The russia-linked Sandworm APT group (aka UAC-0082) has been continuously targeting Ukrainian public systems and critical infrastructure for at least a decade. This group is responsible for massive blackouts throughout the country in 2015-2016 caused by the infamous BlackEnergy malware. That was followed by the NotPetya campaign in 2017, which eventually ended up creating a global cyber crisis with millions of systems infected and billions of dollars in damage. In 2022, just before the full-scale war outbreak, Sandworm targeted Ukrainian power facilities with Industroyer 2 and leveraged multiple data wipers, such as CaddyWiper, HermeticWiper, and Whispergate to attack the Ukrainian government infrastructure.
The intrusions escalated during 2022—2023 as well. According to the latest CERT-UA#5850 alert issued on January 27, 2023, Sandworm APT launched a series of attacks targeting the Ukrainian National Information Agency “Ukrinform” aimed to cripple its information and communication system with at least five different malware samples.
Analyzing the Latest Sandworm APT (UAC-0082) Against Ukrainian National Information Agency “Ukrinform”
In January 2023, CERT-UA tracked a series of cyber attacks aimed at disruption of the informational and communication system of the National Information Agency “Ukrinform.” The inquiry by CERT-UA experts reveals the presence of at least five malicious scripts capable of damaging the integrity and availability of information.
The latest CERT-UA#5850 alert identified that threat actors attempted to cripple users’ computers running different operating systems (Windows, Linux, and FreeBSD) by leveraging CaddyWiper and ZeroWipe destructive scripts, AwfulShred and BidSwipe wipers, as well as a legitimate Windows command line utility, SDelete. Additionally, to proceed with coordinated malware dissemination, hackers created a group policy object (GPO) meant to ensure the initiation of the corresponding malicious tasks. However, the investigation reveals that the attack was partially successful, damaging only several data storage systems.
Also, CERT-UA has discovered an element of the targeted informational and communication system that has been misused to provide unauthorized remote access to the resources of the “Ukrinform” Agency.
Taking into account the results of the investigation, with a high level of confidence, CERT-UA suspects that Sandworm APT, also tracked as UAC-0082, stands behind this malicious operation.
Detecting Sandworm APT Attacks Against Ukraine Covered in the CERT-UA#5850 Alert
Since the outbreak of the global cyber war, there has been a significant increase in destructive attacks targeting Ukraine and its allies linked to the activity of the infamous russia-backed hacking collectives, such as Sandworm APT. To help organizations timely identify malicious activity in their infrastructure, SOC Prime’s Detection as Code platform continuously delivers near real-time detection algorithms against emerging threats, exploits, or adversary TTPs.
Click the Explore Detections button below to instantly reach the comprehensive list of Sigma rules for Sandworm APT activity detection, including rules and queries for the latest cyber attacks covered in the CERT-UA#5850 alert.
All detection algorithms above are enriched with comprehensive cyber threat context and are compatible with the industry-leading SIEM, EDR & XDR platforms, and data lake solutions. To streamline the search for relevant Sigma rules, they are filtered by the custom tag “CERT-UA#5850” based on the CERT-UA alert ID.
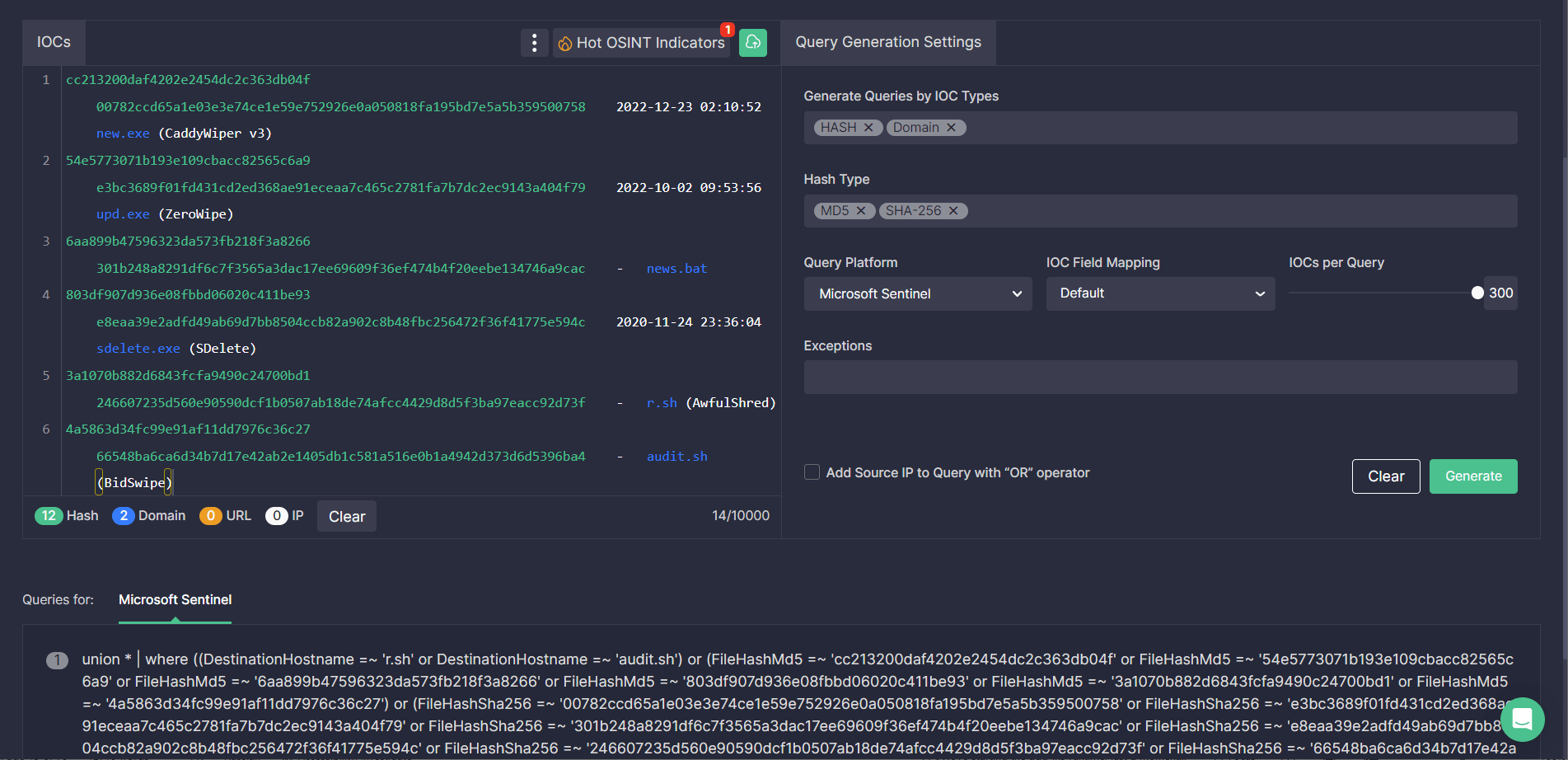
In addition, security engineers can take advantage of the Uncoder CTI tool to instantly generate performance-optimized hunting queries based on the file, host, and network IOCs provided in the CERT-UA#5850 alert and search for relevant threats associated with the Sandworm APT activity in the selected SIEM or XDR environment.
MITRE ATT&CK® Context
To delve into the context of the most recent cyber attacks of Sandworm APT group (aka UAC-0082) targeting Ukraine, all above-mentioned Sigma rules are aligned with the MITRE ATT&CK® framework v12 addressing relevant tactics and techniques:
Tactics | Techniques | Sigma Rule |
Defense Evasion | File and Directory Permissions Modification (T1222) | |
Indicator Removal (T1070) | ||
Hide Artifacts (T1564) | ||
System Binary Proxy Execution (T1218) | ||
Obfuscated Files or Information (T1027) | ||
Deobfuscate/Decode Files or Information (T1140) | ||
Impact | Data Destruction (T1485) | |
Discovery | Network Service Discovery (T1046) | |
Execution | Command and Scripting Interpreter (T1059) |
Striving to proactively defend against russia-linked cyber attacks and boost your cybersecurity posture? Instantly access 500+ Sigma rules against russian nation-backed APT groups along with 50 detection algorithms of your choice as part of our charity-based #Sigma2SaveLives subscription, with 100% of revenue donated to aid Ukraine’s defense. Check out the details at https://my.socprime.com/pricing/




