Hello again! As a follow up to multitude of releases, blog entries and news, we would like to provide more details on the latest BlackEnergy incarnation in Ukraine and how the attacks on Media industry & Electric companies are related, and more over – provide an insight into more indicators of compromise (IOCs). Let us start with saying thanks to all credible cyber experts that investigate the threat and share insights on the attack, some notable names are ESET, CyberX, TrendMicro and iSight. We would focus on ESET’s report as they are providing one of the most comprehensive coverage on BlackEnergy since the days it was first spotted. Now that we have analysis by industry expert on our hands let us take more detailed look at IOC’s and reveal some patterns and perhaps pinpoint a TTP.
Some googling about Ukraine points that BlackEnergy build names may indeed hold some meaning:
- 2015en
- khm10
- khelm
- 2015telsmi – ‘Televisionnye Sredstva Massovoj Informacii’ (as in Television Mass Media)
- 2015ts – Transport System ?
- 2015stb – STB, a Ukrainian TV channel that was under attack in October during elections, part of StarlightMedia a biggest Ukrainian broadcasting group
- kiev_o – perhaps a short for KyivOblenergo, Kyiv power grid
- brd2015
- 11131526kbp – KBP is a IATA code for Boryspil Internation Airport, no attacks were reported
- 02260517ee
- 03150618aaa
- 11131526trk – is a TV Channel ‘Ukraine’, was under attack in October during elections, part of Ukrainian Media Holding
Can we conclude that attacks on Ukrainian Media and Electricity providers are related? This would confirm our previous statement that attack on the Media was a Phase 1 of capabilities test: it did some harm but did not disrupt the broadcast. Phase 2 did however disrupt the electricity and we believe more details will follow on shortly. Let us check the fresh IOC’s from ESET and the ones from attack on the media:

We’ll leave conclusions up to you and continue with a very important part that seems to get past most blog posts and articles – the C&C (C2) addresses. These are the current C2 addresses as reported by ESET that remain active as of this article’s writing time:
5.149.254.114
5.9.32.230
31.210.111.154
88.198.25.92
146.0.74.7
188.40.8.72
If we go back in time to 2014 and see ESET video on BlackEnergy 2 we can find the clues we need for TTP from this screenshot of the video:
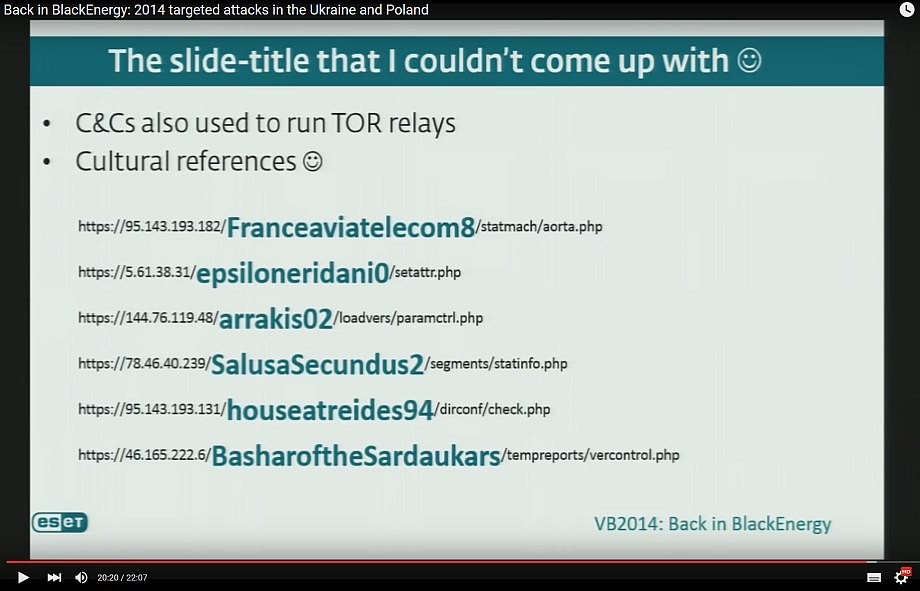
The cultural references decoded from base64 that refer to Dune were the reason that the attack got pinned on group called “Sandworm” by iSight Partners. Do we have enough to put together whole TTP?
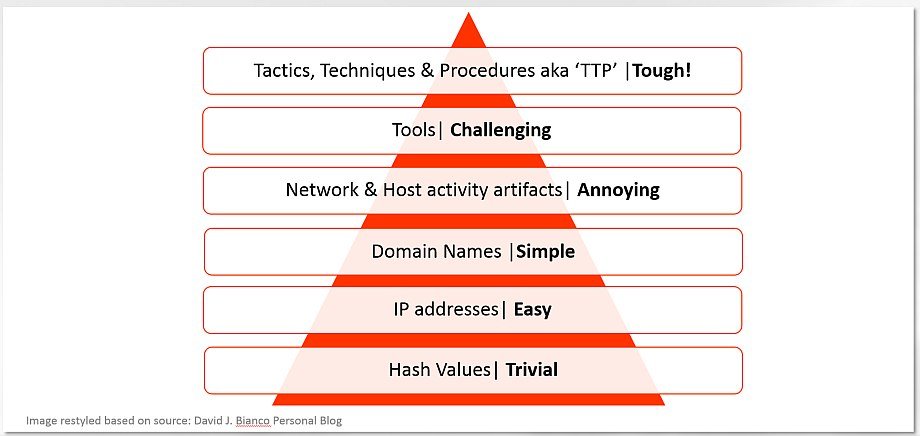
Let us test the model in practice from bottom to the top.
- Hash values are new compared to BlackEnergy 2 (Sandworm).
- Command & Control IP addresses are new compared to BlackEnergy 2 (Sandworm).
- Domain names are not applicable in this case, but we have Tor relays present (again).
- We have no publicly provided host or network artifacts (ones from media attack are here)
- Tool used is new build or edition of BlackEnergy, no doubt about that but we leave the versioning to the experts. The KillDisk plugin is new compared to 2014’s attacks.
We see that current BlackEnergy attacks use 6 IPv4 C2 addresses and there were 6 C2’s in 2014, only addresses themselves were are different. Tor Relays were used back in 2014. A quick lookup of the new C2 IP’s provide us 1 match based on public Tor relay lists. After some research and threat intel analysis we were able to identify that 5 of 6 C2 address had to be related to Tor relays:
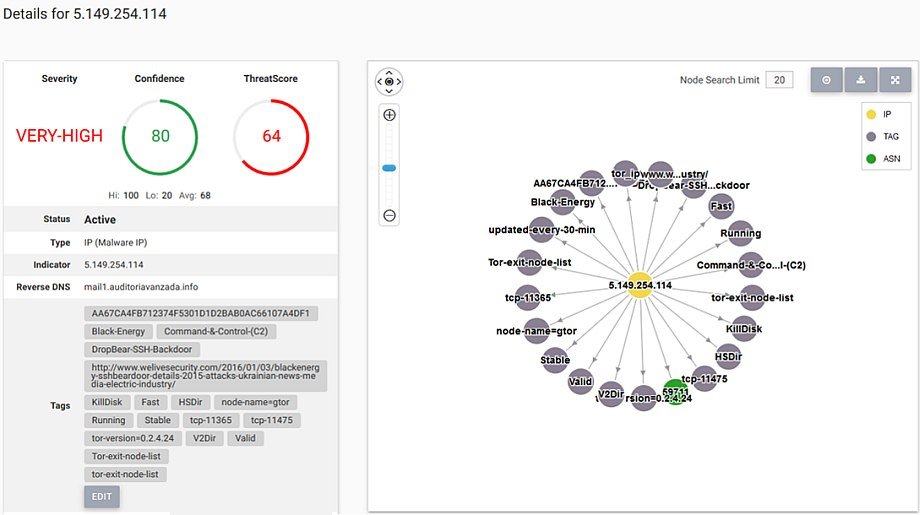
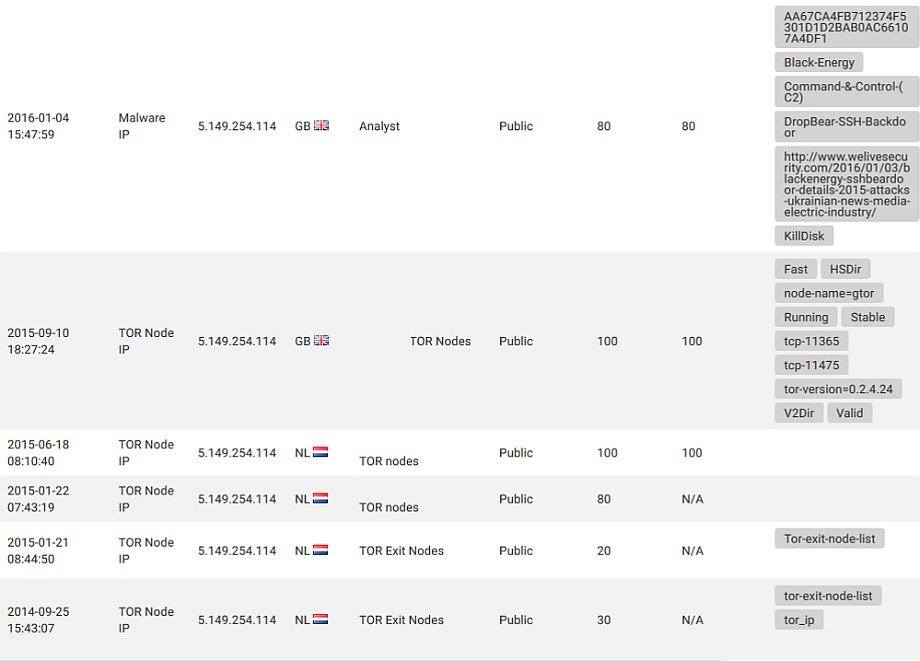
Think about this for a moment. We have same attack tool in use, same amount of C2 IP addresses, Tor is used for APT operations (again) and the same country is attacked, and ICS is attacked (again). One new piece is the KillDisk plugin that has gained some basic AI capabilities: it is able to not just seek & destroy the data it is after but also make decision on the fly, analyzing more than 109 variables and choosing out of 304 functions. We also have new SHA-1 hashes of the drivers different from those ones originally attributed to BlackEnergy 2: are these new builds of same dropper or has it evolved like the plugin? Are we now dealing with APT optimized for FireSale scale attacks to disrupt whole industries? We’d also like to remind that BlackEnergy 3 was mentioned in the past by F-Secure. We leave this question up to the anti-malware specialists with resources and expertise to provide a credible answer. Or perhaps these days BlackEnergy is provided as a packaged Tor-based IaaS available to all who have enough bitcoins to spend ? 😉
Mitigation and proactive detection tips.
Regularly patch your computers and update software, do not open strange email attachments and assure your AV is always up to the date would all seem like a good start. We know for certain that BlackEnergy installs modified drivers that will not load up with modern Windows versions unless it is run in test-mode. Another way of getting those drivers on the system requires a reboot, something that will not fly low under the radar of infosec team. As we already reported BlackEnergy operates based on modified Windows Drivers that are not officially signed, and installation of such drivers requires administrator privileges. Another method of injecting such drivers that was used during the attacks is leveraging a vulnerable version of VirtualBox. As for Proactive detection and timely response we recommend to focus on this:
- Check for any unofficial, self-signed drivers on all Microsoft Windows machines in automated manner. Powershell scripts or tools like OSSEC can be utilized for this. For big and distributed networks scanning for known IOCs may be an option, an example is provided here.
- Do share any suspicious files you discover or malware samples with your AV vendor to receive signatures ASAP. A comment from one of the attack from one of the attack victims “We have shared a BlackEnergy sample with ESET when attack was already in progress and received signature updates in less than 3 hours. This is by no means a promotion of single AV vendor, but a reflection of their capabilities. We express strong faith that many of Endpoint Security manufacturers out there provide same if not better response times, in our case ESET was just one vendor to respond first.”
- Create SIEM content to monitor attack patterns, a new opened port on the host, new service switched to auto-start mode, server restart, Tor connection – all together can give you means to spot APT before it wreaks havoc in your kingdom.
Finally yet importantly monitoring of Tor activity should be on the priority list of CISO of any Enterprise, MSSP or Public organization, but this is a beginning of yet another story…
Stay safe! /SOC Prime team

