Destructive Cyber-Attack Against Ukrainian Government

Table of contents:
Overview, Analysis, and Lessons Learned
On January 13, 2021, a massive data-wiping cyber-attack hit Ukraine, taking down the online assets of the country’s government. As of January 17, 2021, up to 70 websites experienced temporary performance issues due to the intrusion, including the Cabinet, seven ministries, the Treasury, the National Emergency Service, and the state services. Moreover, multiple non-profit organizations and major Ukrainian IT firms have fallen victim to the attack.
In this article, we would like to make an attempt to shed light on what lies behind the infamous attack challenging Ukrainian government organizations that broke out on January 13, 2022. We’re going to analyze all the information we have at hand right now by comparing it with what is already familiar to us and what we have seen before. Let’s take the MITRE ATT&CK® framework to gain more insights into the context surrounding the incident.
Although the exact initial access methods of the attackers are currently unknown, Ukrainian CERT assumes that most likely threat actors leveraged the vulnerability in the October content management system (CMS) to proceed with the intrusion. This software is the core one used across the majority of Ukrainian governmental institutions. Therefore, adversaries possibly used a weak password recovery mechanism for the forgotten password vulnerability (CVE-2021-32648), which remains unpatched since August 2021, to reset the admin account password and proceed with the intrusion. The investigation is still ongoing, and Ukrainian authorities are also inspecting the possibility of a supply chain attack.
What’s Behind WhisperGate: Analysіs of the Cyber-Attack
The investigation by Microsoft Threat Intelligence Center (MSTIC) reveals that upon establishing the initial access, the attack operators have leveraged a novel data-wiping malware dubbed “WhisperGate.” This destructive sample combines the infamous MBRLocker component with custom data-corrupting functionality to deliberately destroy the data stored within the attacked instances.
Microsoft’s discovery of the fake ransomware intended for destructive purposes is a focal point of investigation. Based on ATT&CK techniques, let’s take a closer look at the main features of this two-stage malware as highlighted by MSTIC:
- Stage 1: Overwrite Master Boot Record to display a faked ransom note
Tactic addressed: Impact, Techniques/Sub-technique: Disk Wipe / Disk Structure Wipe, ID: T1561.002, https://attack.mitre.org/techniques/T1561/002/)
- Stage 2: File corrupter malware (based on the hardcoded list of file extensions)
Tactic addressed: Impact, Techniques: Data Destruction, ID: T1485, https://attack.mitre.org/techniques/T1485/)
It looks familiar, doesn’t it? These techniques have already been used in targeted cyber-attacks against Ukrainian critical infrastructure and government assets during 2015 – 2018, including BlackEnergy and NotPetya campaigns.
Leveraging ATT&CK, we can easily come up with a list of threat actors that applied the techniques mentioned above and get the following results:
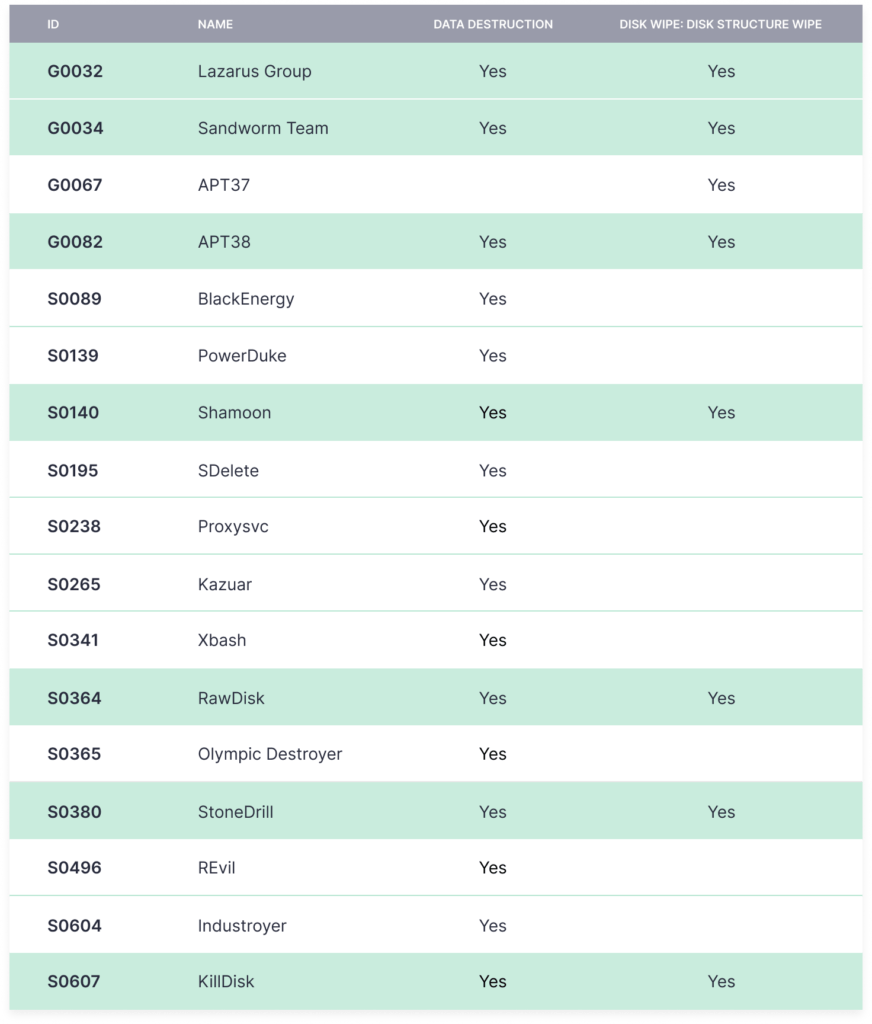
If we make a simple intersection, we can narrow this list to the following groups:
- Sandworm Team (KillDisk)
- APT38 (Lazarus Group)
- StoneDrill
- Shamoon (RawDisk)
All mentioned threat actors are state-sponsored APT groups acting in favor of the Russian, North Korean, and Iranian governments.
While analyzing the most recent attack against the Ukrainian government, MSTIC identified that hackers applied the hardcoded file extension method.
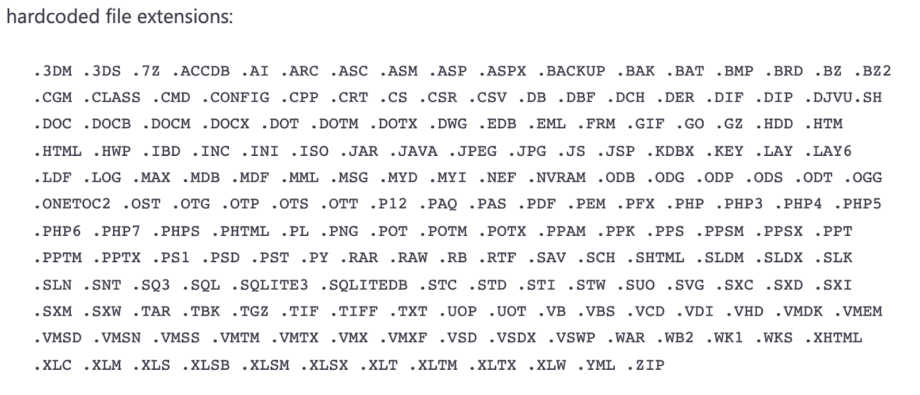
If we go back to the ATT&CK matrix, this method is affiliated only with a single threat actor from the list above, which is the Russian nation-backed group KillDisk (Sandworm Team).
More precise attribution is possible only with an in-depth analysis of the attack samples, however, none of them were shared publicly with the cybersecurity community. All the public information about the attack is limited to IOCs shared within the analysis by Microsoft and multiple suggestions based on this article.
Detecting WhisperGate Wiper Malware
On the basis of the existing public information, the SOC Prime Team has developed a batch of Sigma rules to detect patterns and anomalous behavior pointing to the presence of the WhisperGate wiping malware inside your network. All the detection content is available for free in the SOC Prime’s platform for collaborative cyber defense:
Possible WhisperGate / DEV-0586 Behaviour Activity Patterns (via cmdline)
Possible WhisperGate / DEV-0586 Behaviour Activity Patterns (via file_event)
Possible WhisperGate / DEV-0586 Behaviour Activity Patterns (via powershell)
Possible WhisperGate / DEV-0586 Behaviour Activity Patterns (via proxy)
Possible WhisperGate / DEV-0586 Behaviour Activity Patterns (via dns)
Here’s the link to the entire list of SOC Prime’s hunting queries that look for potential behavior activity patterns of WhisperGate:
https://tdm.socprime.com/expert/?tagsCustom%5B%5D=WhisperGate
Although the attack occurred late at night within the period of January 13-14, 2021, the first samples were uploaded on VirusTotal only on January 17, 2021. Such limited access to information hinders the power of collaborative cyber defense which was already mentioned by multiple security analytics and cybersecurity thought leaders.
If this precious time hadn’t been lost, the worldwide community could have already released cross-tool Sigma-based content ready to use for threat hunting and real-time detection by any team. Considering the experience of previous attacks in Ukraine attributed to Sandworm and TeleBots APT groups, this malware module is not the last one revealed and much more is about to be detected and activated. Only well-orchestrated community collaboration can withstand such critical threats.
Take advantage of prolific collaboration with the global cybersecurity community by joining SOC Prime’s platform to proactively defend against emerging threats and increase the efficiency of your threat detection capabilities. Striving to boost collaboration with your own threat detection content? Apply for the SOC Prime Threat Bounty Program to contribute to the world’s cyber defense while earning recurring rewards for your input.



