Gain insights into the comprehensive Azure Sentinel overview and find out why Microsoft’s platform stands out from other popular SIEMs and how to smoothly get started to boost cyber defense capabilities.
There is a growing trend toward moving from legacy on-premise security solutions to the cloud, which allows organizations to reduce costs on the infrastructure, maintenance, and staffing. CISOs, SOC Managers, and Security Architects are looking for a single solution to the data storage and handling threat detection and response operations, which can be achieved within a cloud environment. According to Gartner1, “The security information and event management (SIEM) market is defined by customers’ need to analyze security event data in real time, which supports the early detection of attacks and breaches.” Azure Sentinel cloud-native SIEM enables timely, effective detection and response to the constantly emerging threats, which makes it a perfect fit for security leaders.
What is Microsoft Azure Sentinel?
Microsoft Azure Sentinel is both a cloud-native security information and event management (SIEM) and a security orchestration automated response (SOAR) tool, enabling real-time security analytics using built-in AI capabilities. As a next-gen AI-powered SIEM, Azure Sentinel adds to all-encompassing cyber defense at cloud scale. Built-in Azure Sentinel’s Data Connectors enable seamless integration of a multitude of log sources and smooth onboarding of various security solutions.
Azure Sentinel cloud-native SIEM can boast its automated User and Entity Behavior Analytics (UEBA) capabilities for in-depth security analysis and timely identification of compromised users and entities. Integrated AI and machine learning allow reducing up to 90% of false positives and alert fatigue, which is a common stumbling block to effective security with legacy SIEMs.
Key milestones that Azure Sentinel can bring to the organization’s SOC:
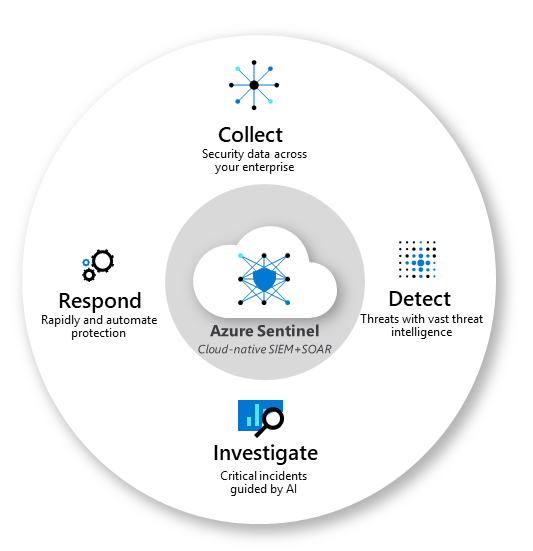
- Collect data from all sources. Azure Sentinel SIEM aggregates data across the entire infrastructure — from any on-premise or cloud environment.
- Detect previously revealed threats while reducing false positives. Microsoft’s Threat Intelligence allows recognizing threats that were detected earlier thus reaching minimum false positives and maximum actionability.
- Investigate threats at cloud speed and scale. Integrated AI-powered capabilities allow identifying and hunting for threats at scale.
- Respond to incidents fast and efficiently. Azure Sentinel enables smart and fast threat detection and prompt response to critical incidents leveraging built-in automation and orchestration tools.
Does Azure Sentinel Compete with On-Premise SIEMs?
What makes Azure Sentinel stand out from other renowned security analytics platforms, like Splunk, Elastic, QRadar, ArcSight, is the platform’s proactive threat hunting capability that allows detecting threats and preventing them before they occur. When it comes to the traditional on-prem SIEMs, their high operational costs and slow scalability enable Azure Sentinel to be second to none in the SIEM market. Azure Sentinel allows analyzing security telemetry across the entire infrastructure using a single cloud-based SIEM solution that offers unparalleled storage and scalability.
Leveraging a security analytics platform, like Splunk on premises, is a reasonable business solution, but when running it in the cloud via AWS or Azure, it can cost a fortune. On the other hand, Azure Sentinel cloud-native SIEM doesn’t need investing in all the servers, storage, networks, engineering, and licensing, which is an indispensable part of the Splunk infrastructure support. This was a core reason why an industry-leading MSSP, Insights Enterprises, chose Azure Sentinel over Splunk.
Handling security operations with the Azure Sentinel SIEM allows reducing up to 48% costs on the infrastructure setup and maintenance as compared to legacy SIEMs and its deployment takes 67% faster.
Is Azure Sentinel PaaS or SaaS?
Azure Sentinel SIEM can be considered as SaaS (Security-as-a-Service) based on its high scalability when meeting the security needs of various organizations. Still, from a high-level perspective, Azure Sentinel can also be considered PaaS (Platform as a service), which involves providing a complete development and deployment environment in the cloud and enabling a full software development lifecycle. Being fully manageable via the Microsoft Azure Portal that enables building, deploying, and managing different applications in a single cloud space allows qualifying Azure Sentinel accordingly.
What is the Difference Between Azure Sentinel and Security Center?
Microsoft possesses its own Azure Security Center (ASC), which is an integrated security management system enabling all-encompassing visibility and security control within hybrid environments in the cloud. Its key goal is keeping a close eye on the entire infrastructure, monitoring the cloud security health, and timely identifying threats. While Microsoft’s Azure Sentinel is both a cloud-native SIEM and a SOAR tool, which goes far beyond log collection and incident prevention by enabling proactive threat hunting, advanced security analytics, and rapid incident response.
What Are Azure Sentinel Top Competitors?
Among top Microsoft’s competitors in the SIEM & XDR market, Google Chronicle can be considered the most relevant one as a cloud-native solution with similar scale and storage capabilities.
As per Gartner Peer Insights, LogRhythm, Splunk, and QRadar are among top Azure Sentinel competitors in the security analytics and SIEM market, while Microsoft’s product is the leader by the “User Overall Rating Score” (4.8 out of 5) and receives the maximum 100% score on the “Willingness to Recommend” scale.
How Do I Deploy Azure Sentinel?
Before deploying content to Microsoft’s cloud-native SIEM, security performers need to enable Azure Sentinel, which requires the following settings:
- An active Azure Sentinel subscription with a free Azure Sentinel account.
2. A Log Analytics workspace with the corresponding contributor or reader permissions to the Azure Sentinel subscription.
3. Connected data sources that may need additional permissions.
After enabling Azure Sentinel in the environment and connecting data sources, you’re all set to start streaming data directly into the SIEM instance and build queries using the Log Analytics functionality by selecting Logs in the Azure Monitor menu.
Where Can I Find Detection Content for Azure Sentinel?
SOC Prime’s core product, Threat Detection Marketplace, possesses the world’s largest content collection of 100,000+ SIEM and EDR algorithms, including the support for 7,000+ SIEM-native analytic rules for Azure Sentinel. Using the Azure Sentinel integration, security performers can seamlessly deploy the latest content from Threat Detection Marketplace to their Azure Sentinel instance. Leveraging the Continuous Content Management (CCM) module enabled by the Azure Sentinel API, content deployment becomes fully automated allowing Microsoft users to stream new and updated detections directly into their SIEM instance and keep always abreast of the emerging threats.
Until the end of 2021, Azure Sentinel users can access the Premium Threat Detection Marketplace content for free using a promo code as part of the joint SOC Prime and Microsoft’s promotion.
Microsoft’s Azure Sentinel Tutorials and Cyber Library
To delve deeper into Azure Sentinel, explore the product documentation allowing smooth onboarding to this cloud-native SIEM and making the most of its cyber defense capabilities.
SOC Prime has also a dedicated space for harnessing threat hunting skills with free and direct access to the cybersecurity knowledge. Join Cyber Library powered by Threat Detection Marketplace to explore how-to guides on Azure Sentinel and learn how to create correlation rules from scratch or deploy Incident Response Playbooks and configure the analytical rule for Playbook triggering.
References:
- https://azurelib.com/what-is-azure-sentinel/
- https://www.linkedin.com/pulse/heres-everything-know-usage-azure-security-center-sentinel-bail
- https://docs.microsoft.com/en-us/azure/sentinel/
- https://socprime.com/blog/creating-microsoft-azure-sentinel-rules-in-your-siem-instance/
- https://socprime.com/news/soc-prime-extends-microsoft-azure-sentinel-promotion/
- https://www.channelfutures.com/mssp-insider/why-insight-chose-microsoft-azure-sentinel-as-core-siem-over-splunk
- https://www.datashieldprotect.com/blog/google-chronicle-vs-microsoft-azure-sentinel
1Gartner, Magic Quadrant for Security Information and Event Management, By Kelly Kavanagh, Toby Bussa, John Collins, 29 June 2021.