SOC Prime Threat Detection Marketplace provides access to 6,000+ Microsoft Azure Sentinel detections, including Queries, Rules, Functions, and Incident Response Playbooks mapped directly to MITRE ATT&CK® to match your organization-specific needs. You can seamlessly find the most relevant detections by applying the Microsoft sorting option and deploy content in a matter of clicks to your Azure Sentinel instance.
To help you deploy the existing content to your environment and create your own rules, we are constantly enriching the collection of online educational resources for various SIEM, EDR, and NTDR solutions available at no charge in our Cyber Library. This article describes the process of Azure Sentinel rule creation to detect threats in your environment. Follow this link and select the Rule tab to reach an even more detailed guide on creating Azure Sentinel rules using your Cyber Library credentials.
There are two types of Azure Sentinel rules that can be created:
- Microsoft incident rules
- Scheduled query rules
Here we’ll focus on the second type of Azure Sentinel correlation rules – Scheduled query rules.
Azure Sentinel Rule Creation: Getting Started
- Select Analytics from the left-hand side menu of your Azure Sentinel instance.
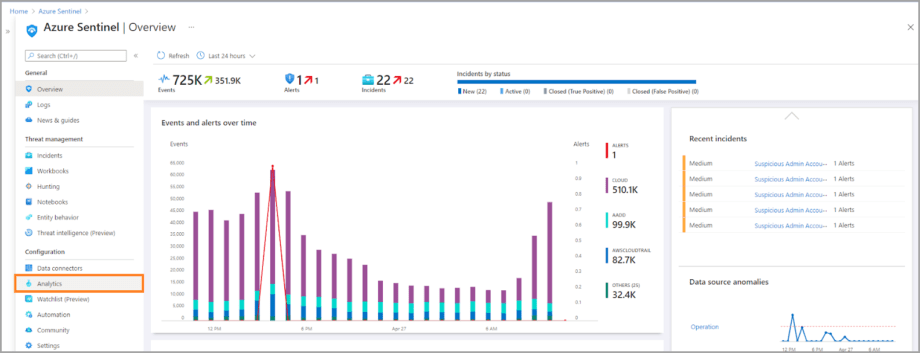
2. Select Create > Scheduled query rule, and the Azure Sentinel rule wizard will open.
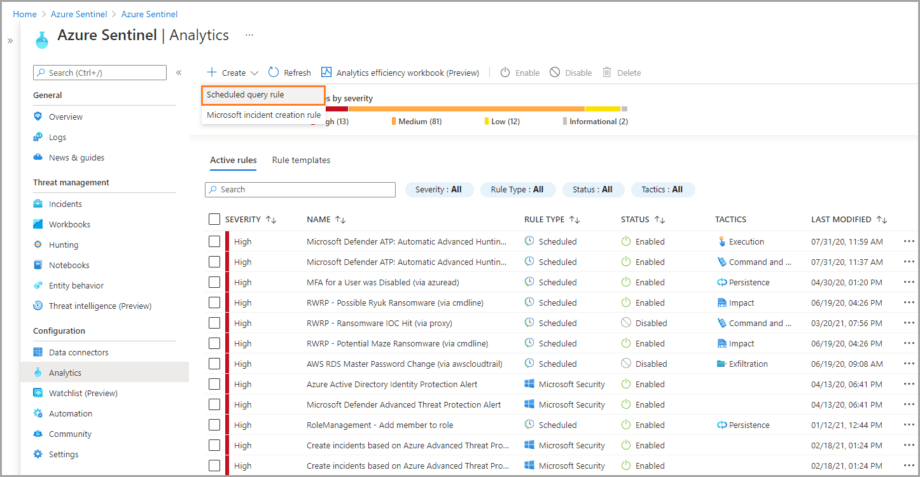
Configuring Azure Sentinel Rule Wizard
The Analytics rule wizard for creating Azure Sentinel rules consists of the following steps:
Each of these steps is a separate tab on the Azure Sentinel rule wizard.
General settings
- On the General tab, fill in the rule name and its description.
- Select the rule severity from the list of predefined options.
- Optionally, you can map the rule to the specific MITRE ATT&CK® Tactics. You can select multiple Tactics at once.
- Specify the rule status. By default, it’s Enabled.
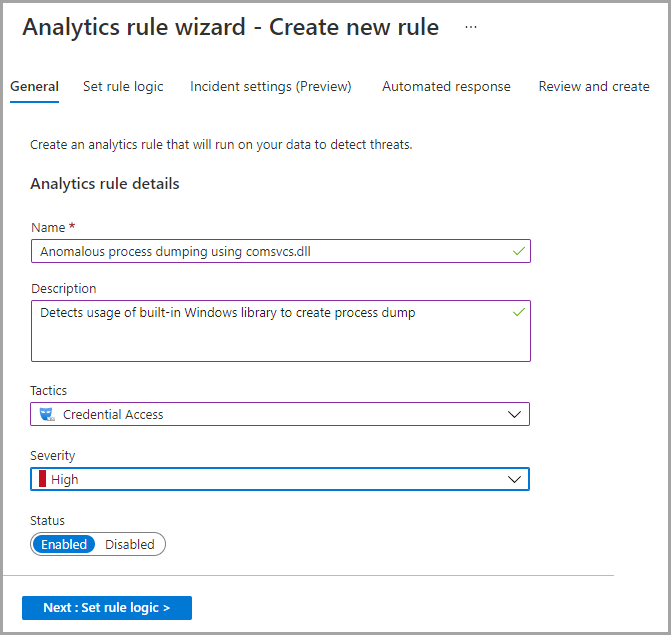
5. Click Next to move to the rule logic settings.
Rule logic settings
The Set rule logic tab defines the rule logic and configures other rule settings, such as:
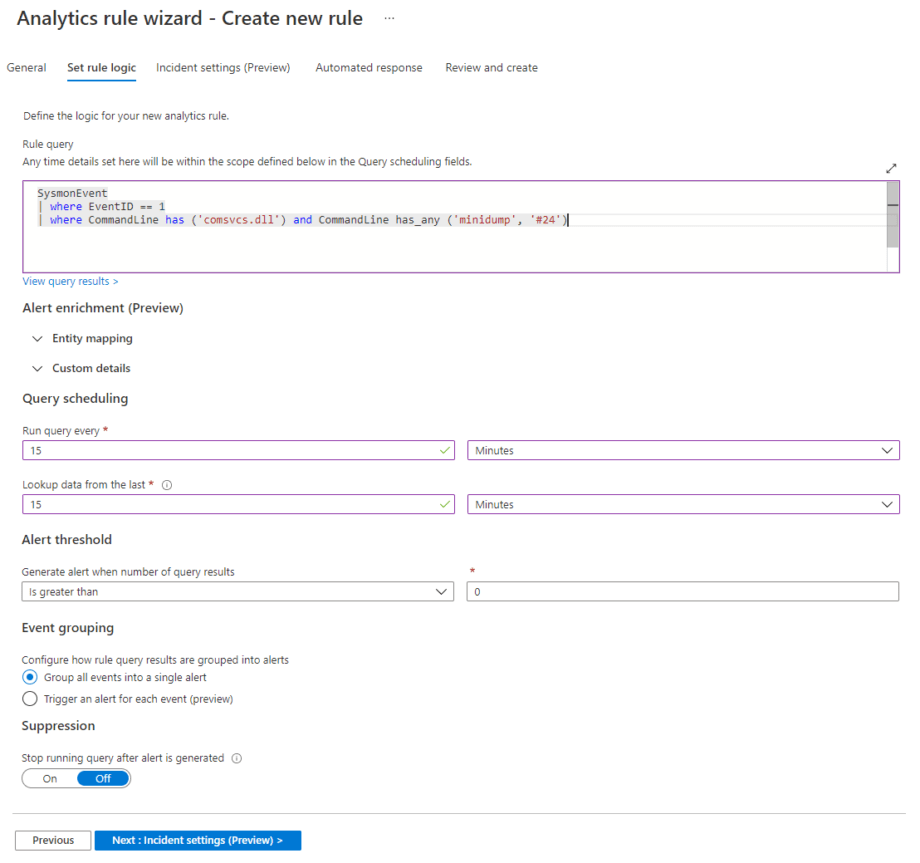
Rule query
Rule query is a query that will be run to discover anomalous behaviors or detect threats. The query shown on the screenshot above will trigger an alert when an attempt is made to dump the process on a host by using the Windows built-in library comsvcs.dll.
Alert enrichment
These rule creation settings consist of the following configurations:
- Entity mapping
- Custom details
The Entity mapping section allows mapping up to five entities recognized by Azure Sentinel (like Account, File, Host, IP, etc.) from the fields which are available in the query results. This enables Azure Sentinel to recognize and classify the data in these fields for further analysis.
The Custom details section allows surfacing event data in the alerts generated from those events. Once configured, these settings enable you to triage, investigate, and respond much faster and more efficiently.
Query scheduling
Here you can set up the schedule for running your newly created analytics rule.
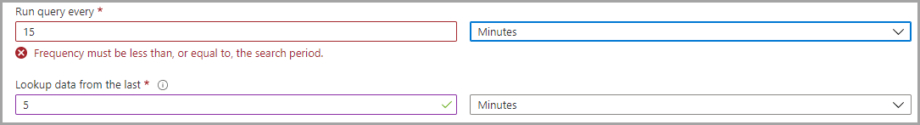
Alert threshold
Setting an alert threshold allows defining the sensitivity level of the created rule. You may want to create an alert only if the query returns a certain number of results.
Event grouping
In this section, you can set up how the rule query results are grouped into alerts.
Suppression
You can stop running a query for a certain amount of time after an alert is generated. This means that if you switch Suppression ON, your rule will be temporarily disabled for the time period you specified (up to 24 hours).
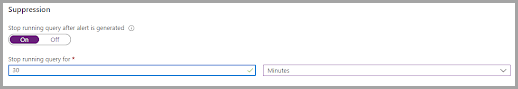
Click Next to move to the Incident settings tab.
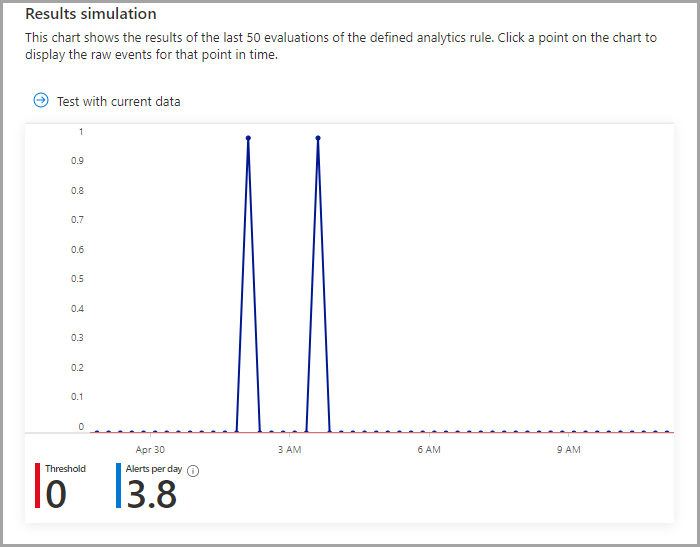
Result simulation
The Result simulation section helps Azure Sentinel users test rules during their development stage before they are deployed to the production environment.
Incident settings
On this tab, you can define how Azure Sentinel turns alerts. The tab includes the following configurations:
- Incident settings
- Alert grouping
You can disable incident creation from alerts or create a single incident from a group of alerts.
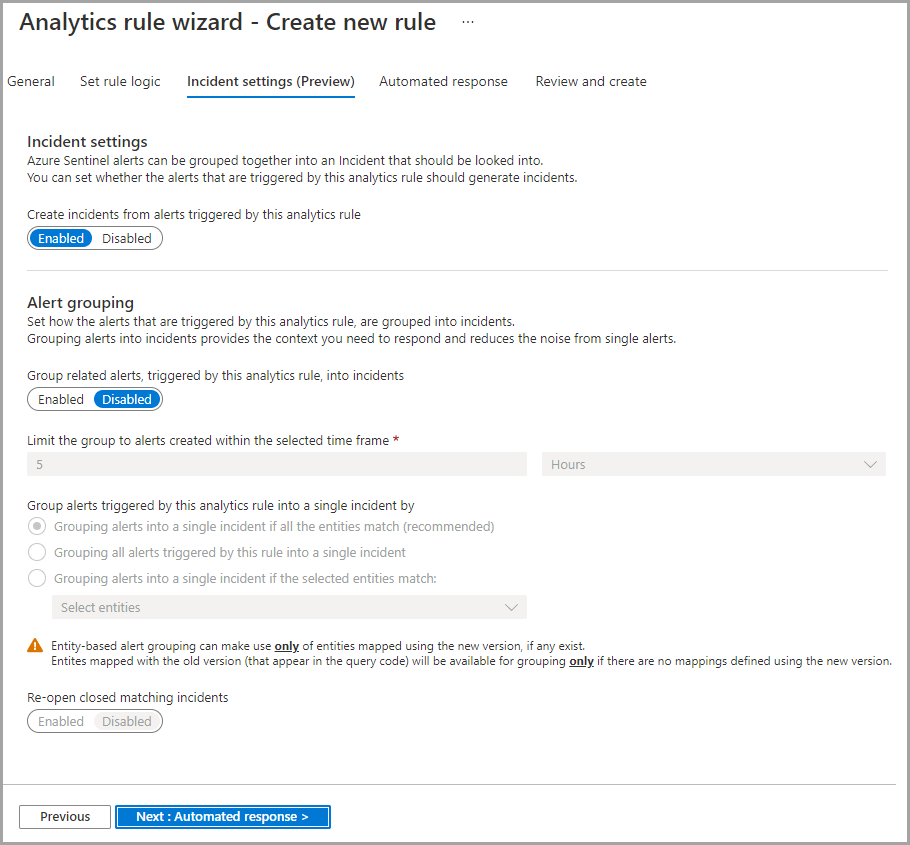
Incident settings
These settings are enabled by default. Once enabled, the separate incident will be created from each Azure Sentinel alert triggered by this rule. You can switch to Disabled when needed.
Alert grouping
When enabled, a single incident will be created from a group of Azure sentinel alerts based on the defined criteria. By default, these settings are disabled.
Other settings here are as follows:
- Limit the group to alerts created within the selected time frame
- Group alerts triggered by this analytics rule into a single incident by
- Re-open closed matching incidents
Click Next to move to the Automated response tab.
Automated response
Here you can select a playbook which will run automatically when an alert is created from the Azure Sentinel analytics rules. You will see only those playbooks available for your selected subscriptions and for which you have permissions.
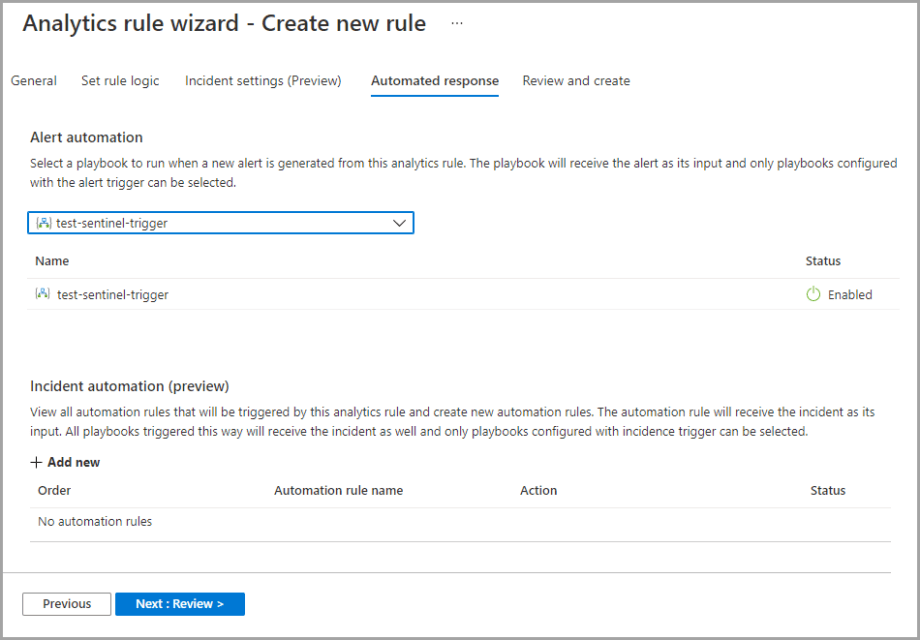
Click Next to proceed to the Review and create tab.
Review and create
This is the final step of the Azure Sentinel rule creation process. The Review and create tab displays a summary of the newly created analytics rule. Also, at this step, the newly created rule goes through validation. You will see the Validation passed message on top of this tab, which means that the rule is properly created and can be deployed.
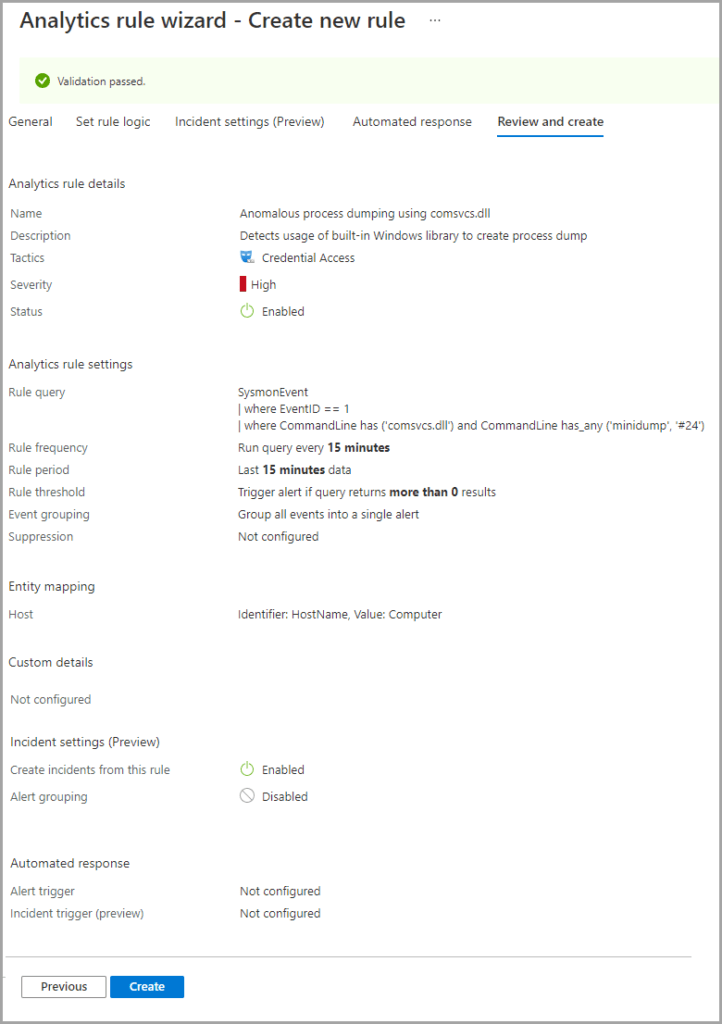
Select the Create button to complete the configuration settings and add a new analytics rule.
You will see your newly added rule in the table under the Active rules tab on the main Analytics screen. Later you can edit, disable, delete, or duplicate this rule by clicking the More ( … ) button.
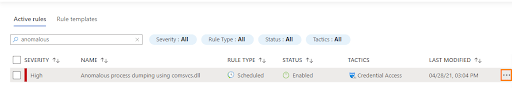
That’s it, now you are ready to create your own Azure Sentinel rules for detecting threats or suspicious activities.
Explore Threat Detection Marketplace to find a broad collection of SOC content tailored to your Microsoft Azure Sentinel environment, including 6,000+ SIEM-native Rules and Queries. Eager to enrich your threat hunting expertise? Sign up for our Cyber Library to hone your SIEM hard skills, explore how-to guides on threat hunting, and watch deep dive cybersecurity webinars.