Hunt at No Cost Through May 25, 2022
Furthering its mission to transform threat detection, SOC Prime has boosted threat hunting velocity by continuing to evolve its Detection as Code platform. Uncoder CTI powered by SOC Prime’s platform allows security researchers to automatically convert IOCs of multiple types into custom queries enabling instant IOC searching for unique customer environments. We are thrilled to announce that Uncoder CTI is now available free of charge through May 25, 2022.
Uncoder CTI currently integrates with nearly 20 industry-leading SIEM & XDR solutions. Also, we’ve recently released integration with AWS OpenSearch and are constantly broadening support for the most widely used technologies.
Please note that no IOC data submitted to Uncoder CTI is stored on our end. Only threat hunters and threat intelligence specialists have access to their IOC data while running a hunting session.
Uncoder CTI Promo Details
All SOC Prime users who have signed up for the SOC Prime’s platform can now gain free access to the extended Uncoder CTI capabilities.
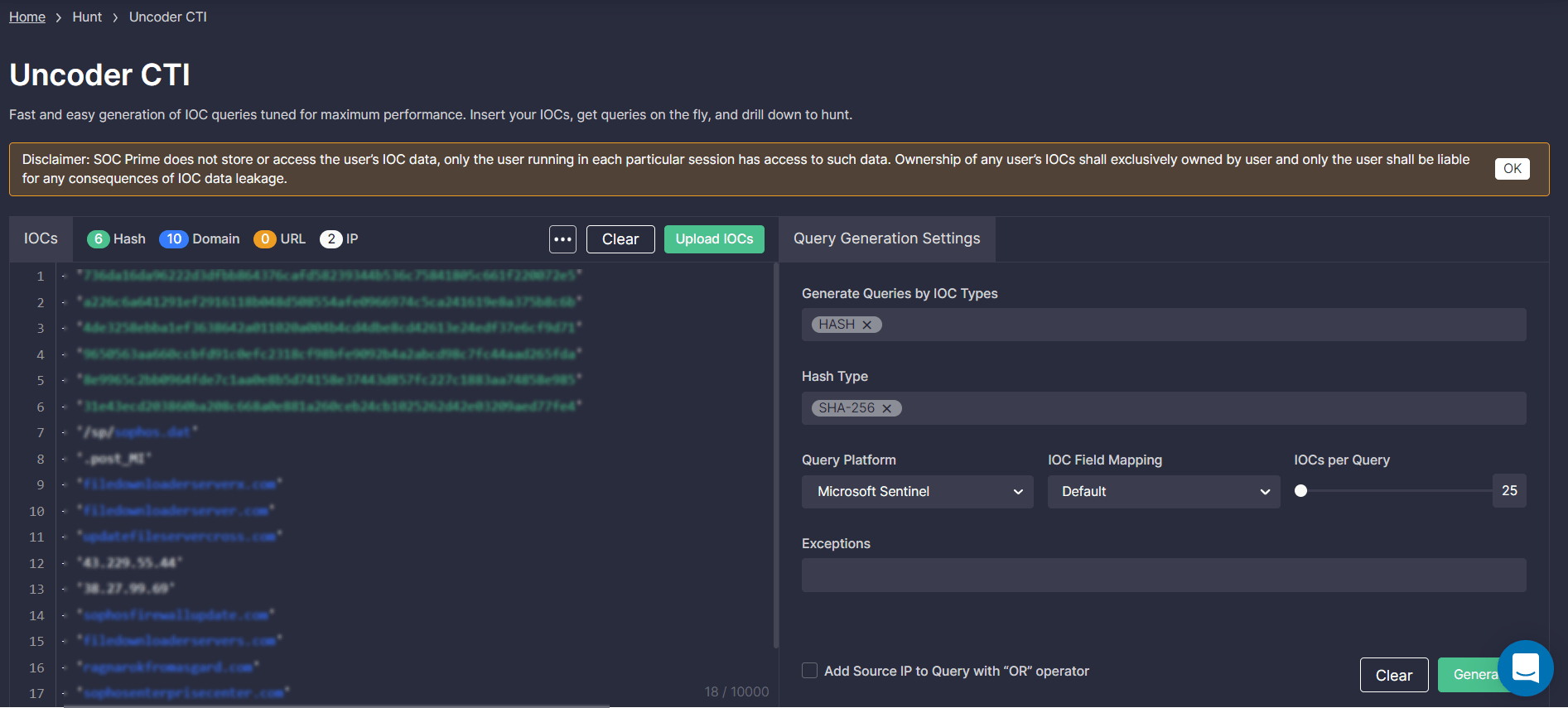
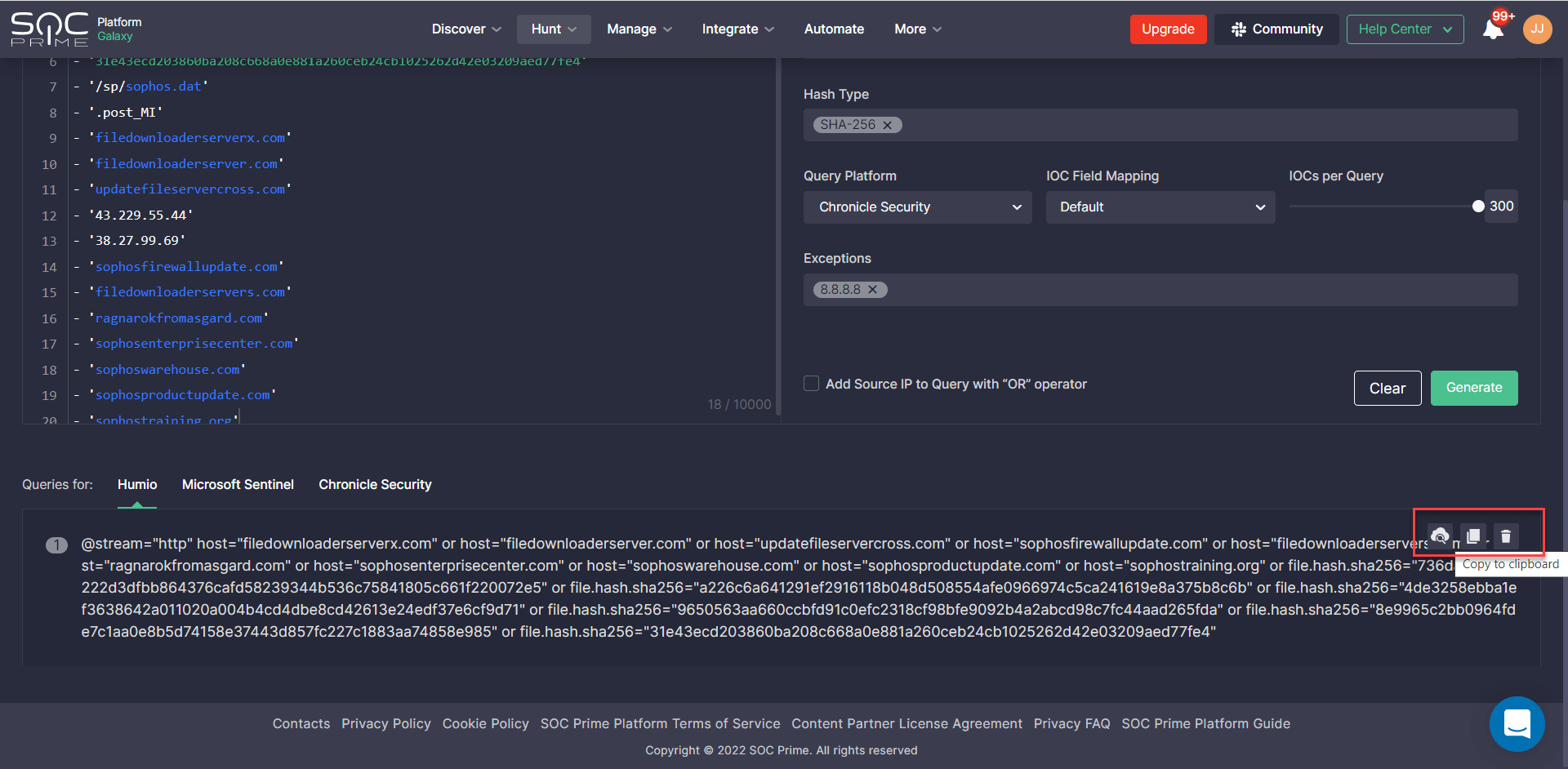
To start hunting with Uncoder CTI, log into the SOC Prime’s Detection as Code platform and select Hunt > Uncoder CTI. On the Uncoder CTI page, take the following steps to add the source file with IOCs and fine-tune your intended query:
- Insert a text file with IOCs or click the Upload IOCs button to import the file from your local disk. Please note that the maximum number of IOCs is 10,000.
- Optionally, you can customize symbols and characters to overcome potential parsing bottlenecks. Click the More button and select predefined options for on-the-fly parsing. Default settings already have the most common replacement options pre-selected.
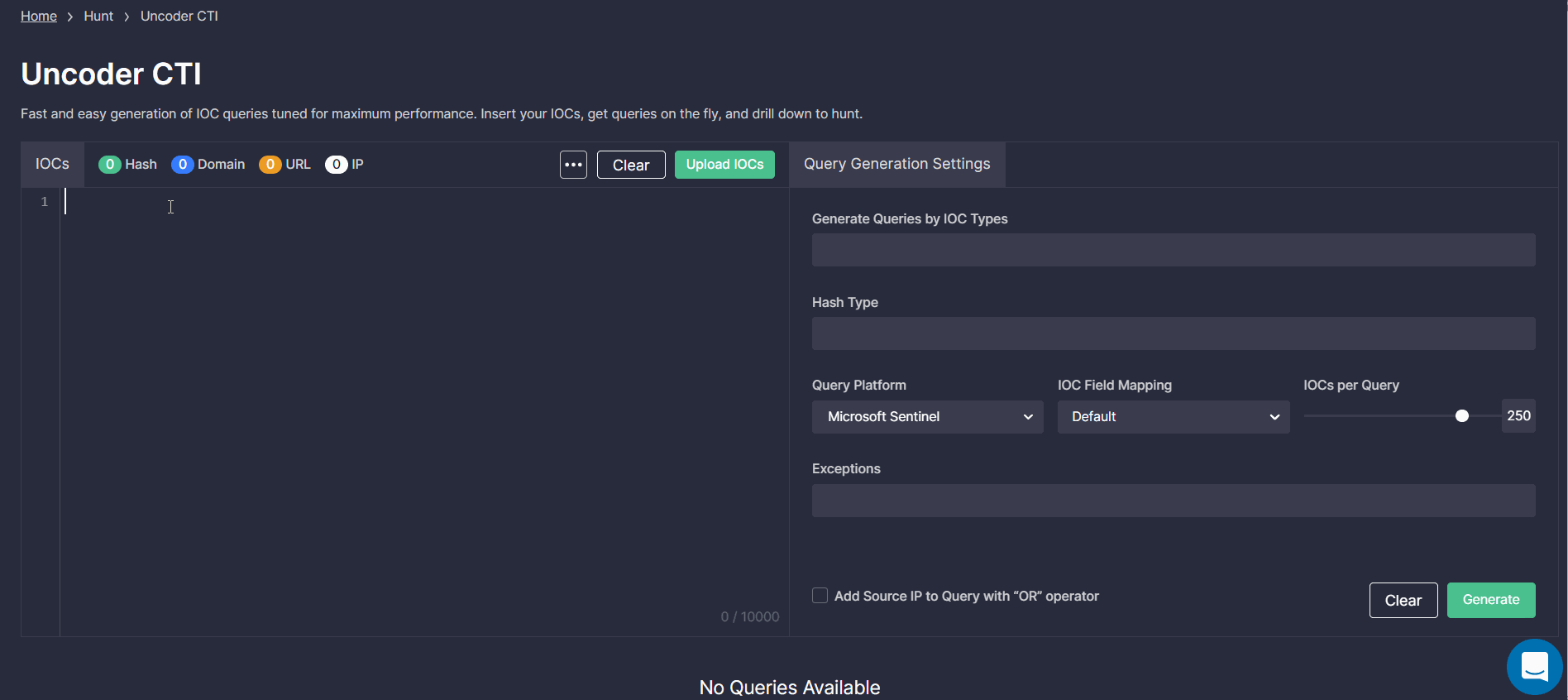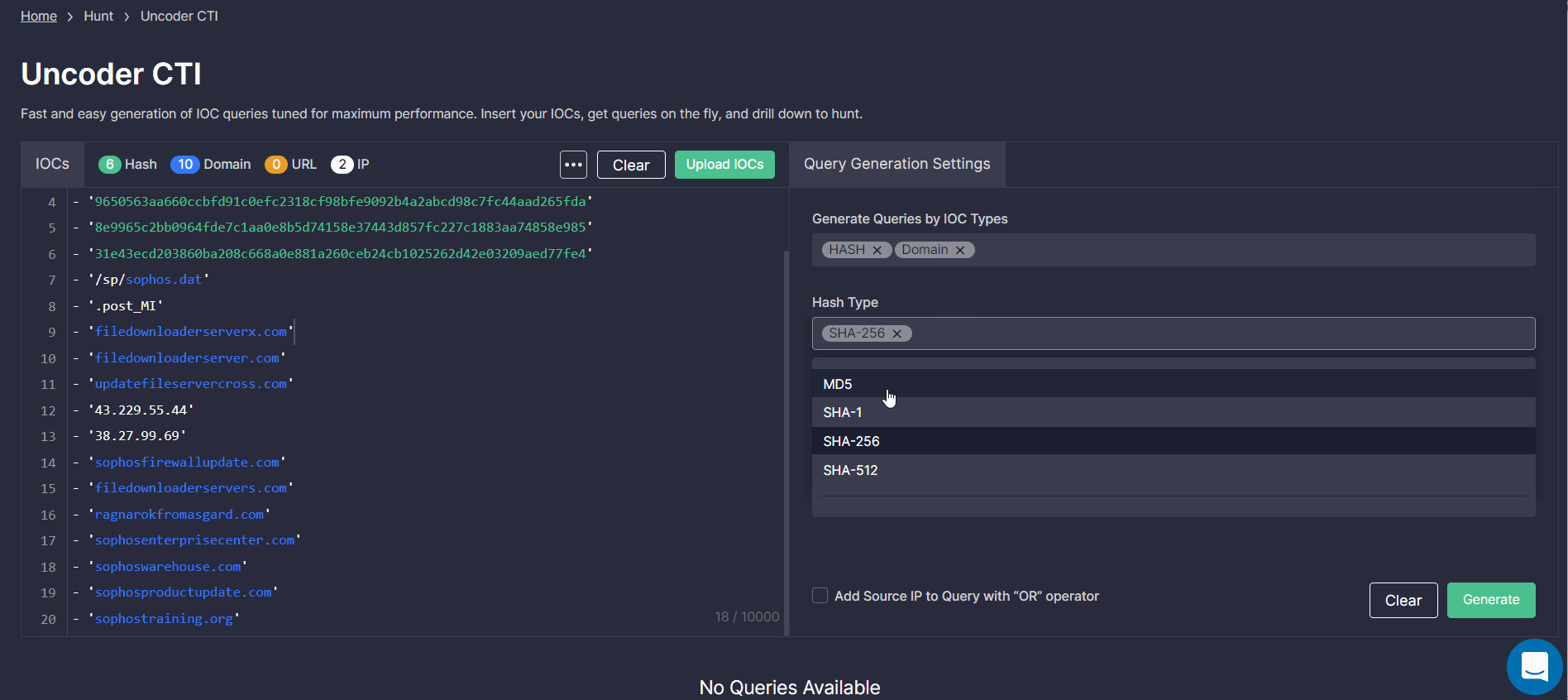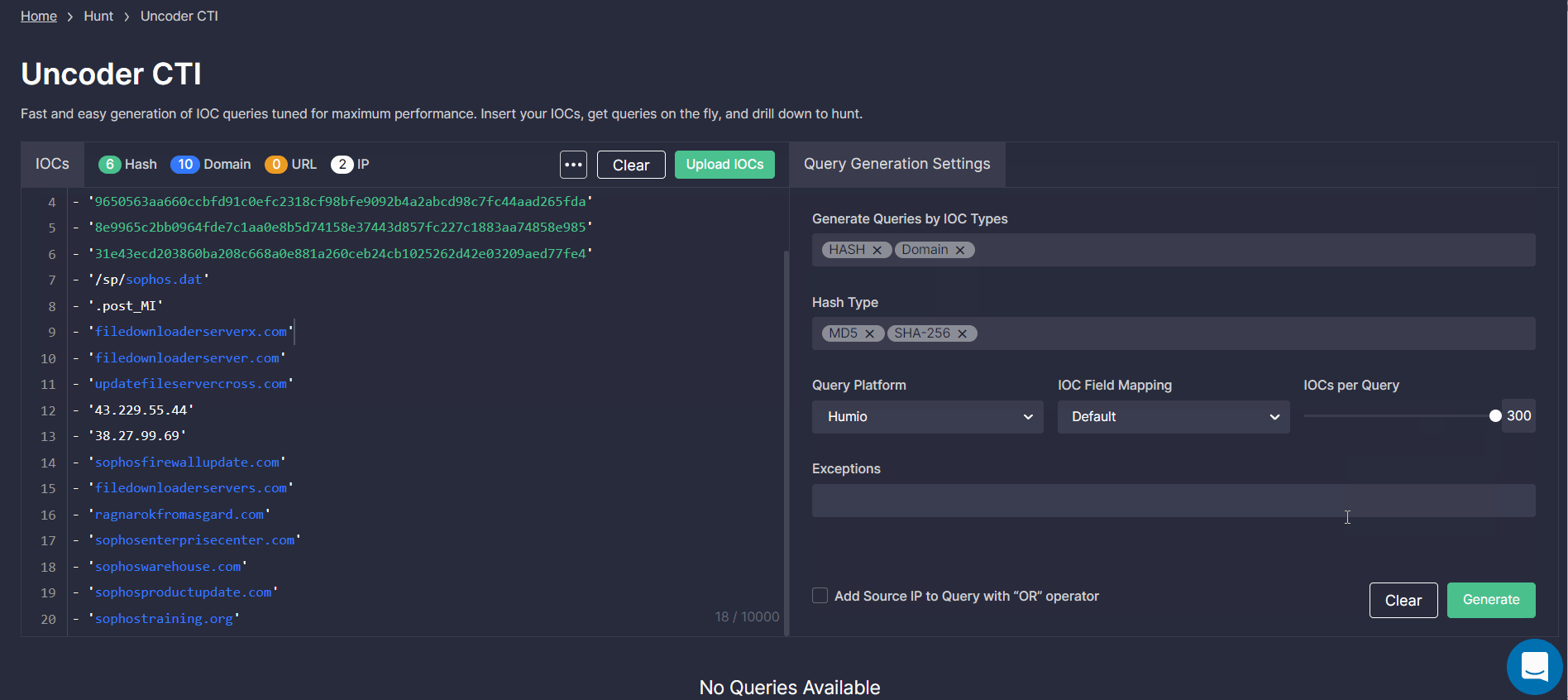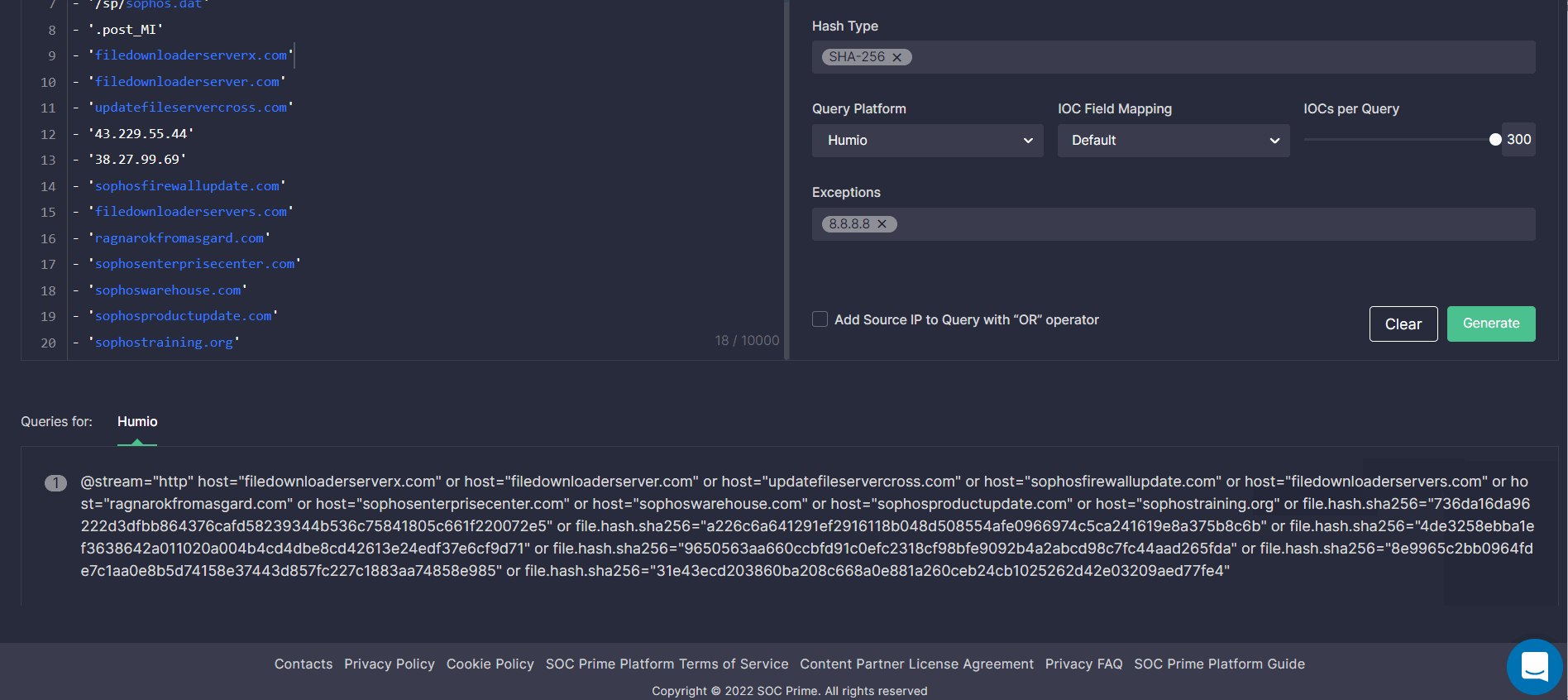
- In the Query Generation Settings, select IOC types for your custom query from the list of predefined options. You can also specify the hash type.
- Select the platform in which you are going to hunt using the query.
- Set up a custom IOC field mapping profile to remap the default parameters of your SIEM or XDR solution to a non-standard data schema that goes beyond vendor specifications. Unless configured, the default profile will be applied.
- Adjust the IOC number within a range from 25 to 300.
- Optionally, you can enter exceptions to cut down on the number of false positives.
- You can also add the source IP in your query with the “OR” operator by selecting the corresponding option in the query settings.
- Click Generate to finish fine-tuning and get the result.
Teams can drill down to hunt with the converted query in two ways:
- Manually copy the IOC query code and then paste it to their environment.
- Automatically submit the query to the configured hunting environment.
Note that to instantly drill down to search with a query in your SIEM or XDR solution, the following conditions should be met:
- You should have your platform integration configured in the Environments settings, including the URL of your web console. The number of environments for which you can set up web-based integrations depends on your active subscription.
- Your SOC Prime account should be linked to a corporate email address.
For more details on how to leverage Uncoder CTI, please refer to this blog article.
In addition to the Uncoder CTI promo, InfoSec practitioners are also welcome to access the extensive collection of FREE Sigma-based detections tagged with #stopwar, #stoprussian, and #stoprussianagression for running instant hunts with the Quick Hunt module. Log into the SOC Prime Platform, follow the link below, and choose queries to instantly search for Russia-linked digital threats using Quick Hunt — again, at no charge:
Drill down to search for Russia-originated threats with Quick Hunt
Join SOC Prime’s Detection as Code platform to evolve your threat detection capabilities and accelerate threat hunting velocity backed by the power of global collaborative expertise. Eager to contribute to crowdsourced threat detection? Submit Sigma and YARA rules to SOC Prime’s platform, wait for detections to get published to the platform after quality control checks and verification, and enjoy recurring rewards for your insightful input.