Threat Detection Marketplace 4.8.0 Is Released
On May 5, 2021, we released Threat Detection Marketplace version 4.8.0 to boost the existing capabilities of our Detection as Code platform and provide customers with a cutting-edge security intelligence experience. This latest upgrade provides significant content quality enhancements, improves the rule page design, introduces a new login/signup page for our customers leveraging Microsoft Azure Sentinel, and broadens support for the FireEye security platform by adding a new content type.
Content Quality Enhancements: SentinelOne, Humio, Elasticsearch, ArcSight, QRadar
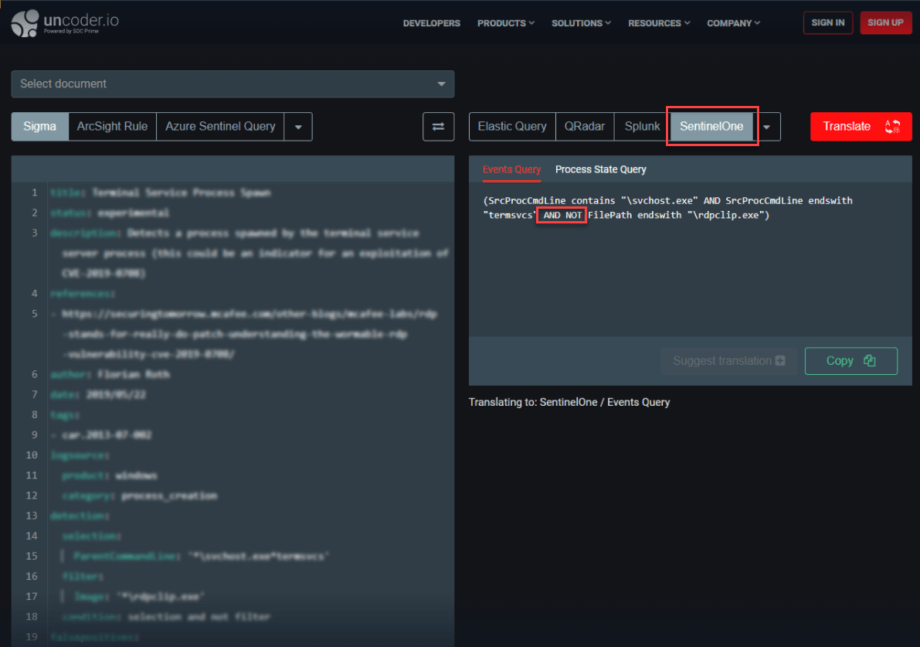
At SOC Prime, we’re striving to improve the content quality when translating behavior-based detections to various SIEM, EDR, and NTDR language formats. With this release, we made major quality enhancements for Sigma rule translations to the SentinelOne platform:
- Fixed the translation of the AND NOT logical operator in the rule source code, which was wrongly converted to the AND operator
Fixed the issue with the duplicate display of the AND operator in the translated content
Also, to ensure an intuitive threat detection experience for Humio users, we’ve made translation enhancements when converting Sigma rules to this cloud-native language format. More specifically, we’ve introduced syntax updates to the Humio regular expressions.
The next platform that received important translation improvements is Elastic Stack. Before the latest update, escape characters, like \ or / were wrongly converted from Sigma to Elasticsearch, which caused a critical translation issue.
Moreover, Threat Detection Marketplace version 4.8.0 provides ArcSight mapping improvements. For a better platform experience of security performers leveraging this security solution, we’ve recently improved custom field mapping for the following content types:
- Rules
- Queries
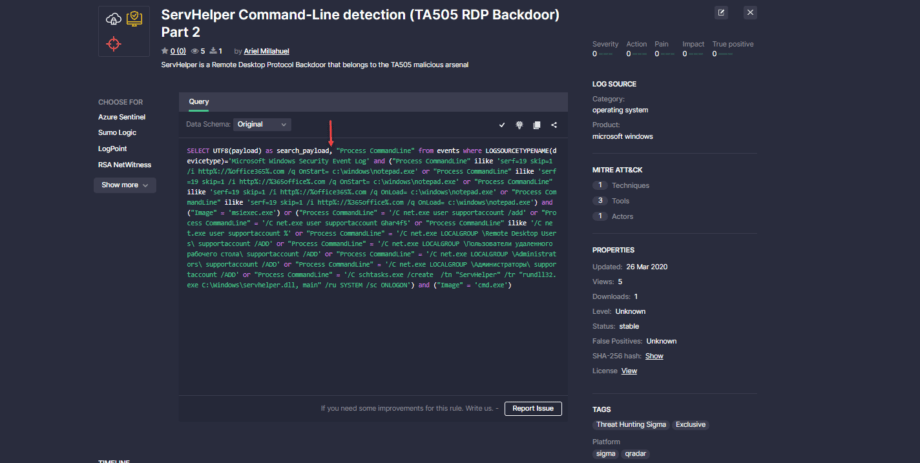
Finally, we’ve improved translations for the QRadar security solution when the original Sigma rule contains specified fields. Security performers can now see that the translation includes a required comma followed by a space after search_payload earlier missing and causing an issue.
Rule Page Redesign
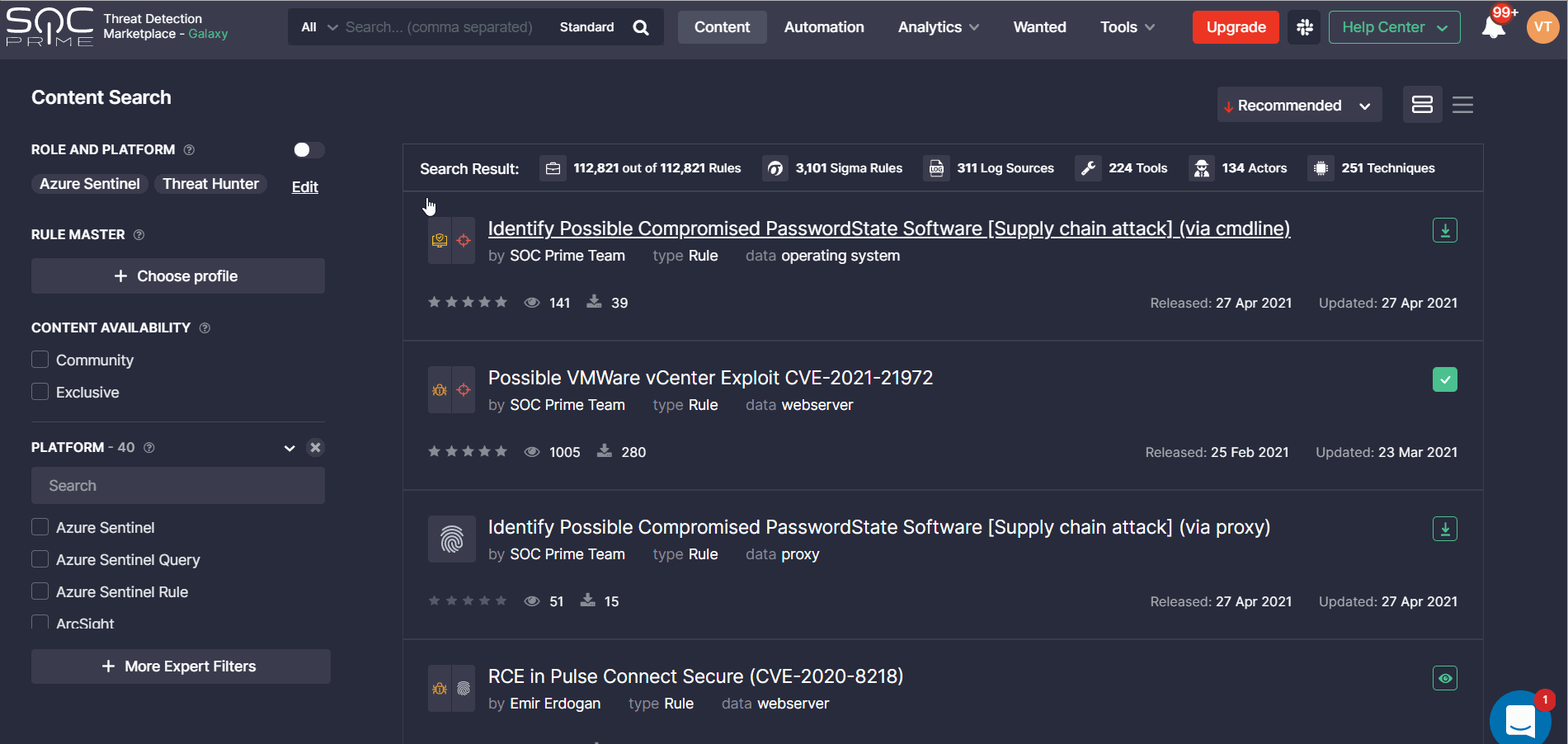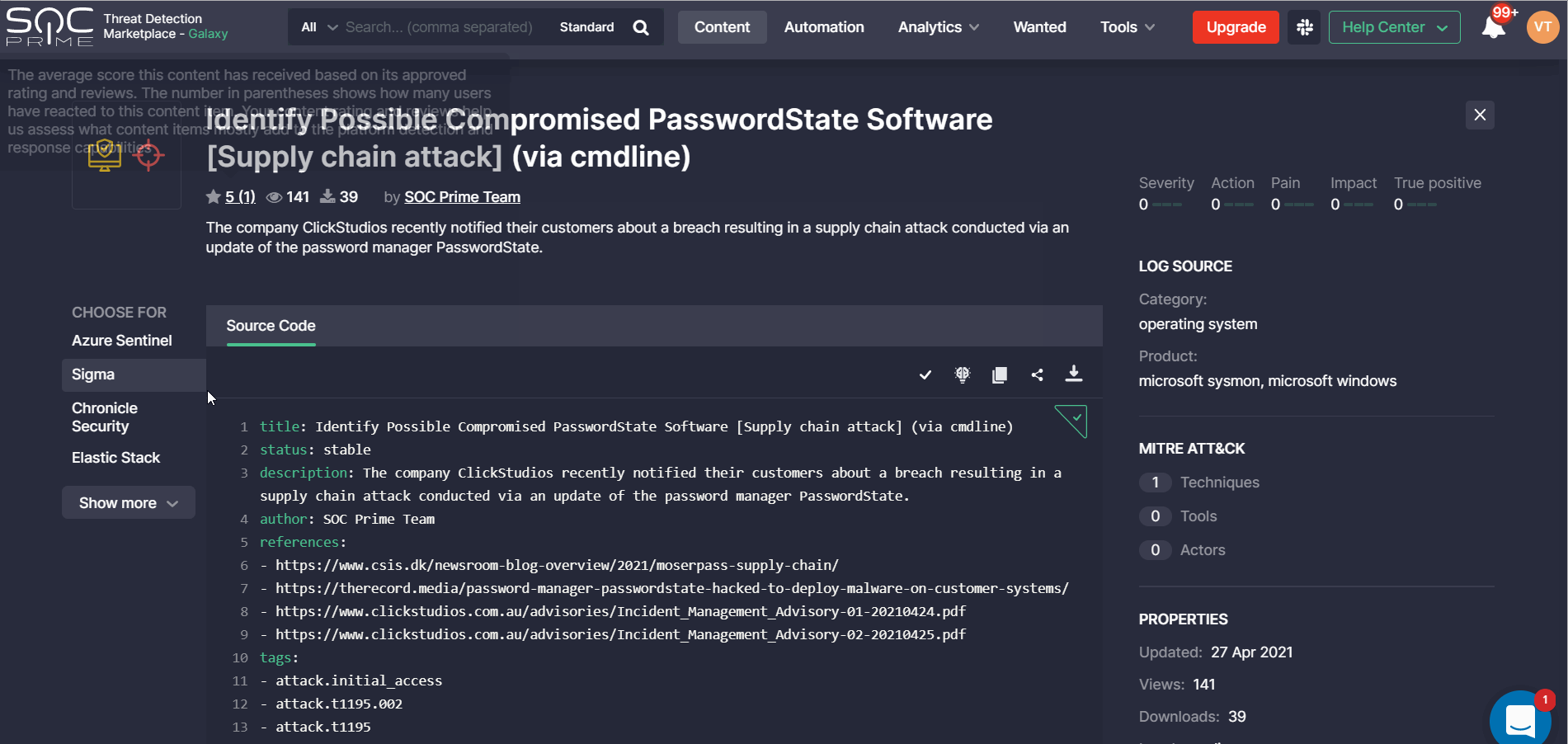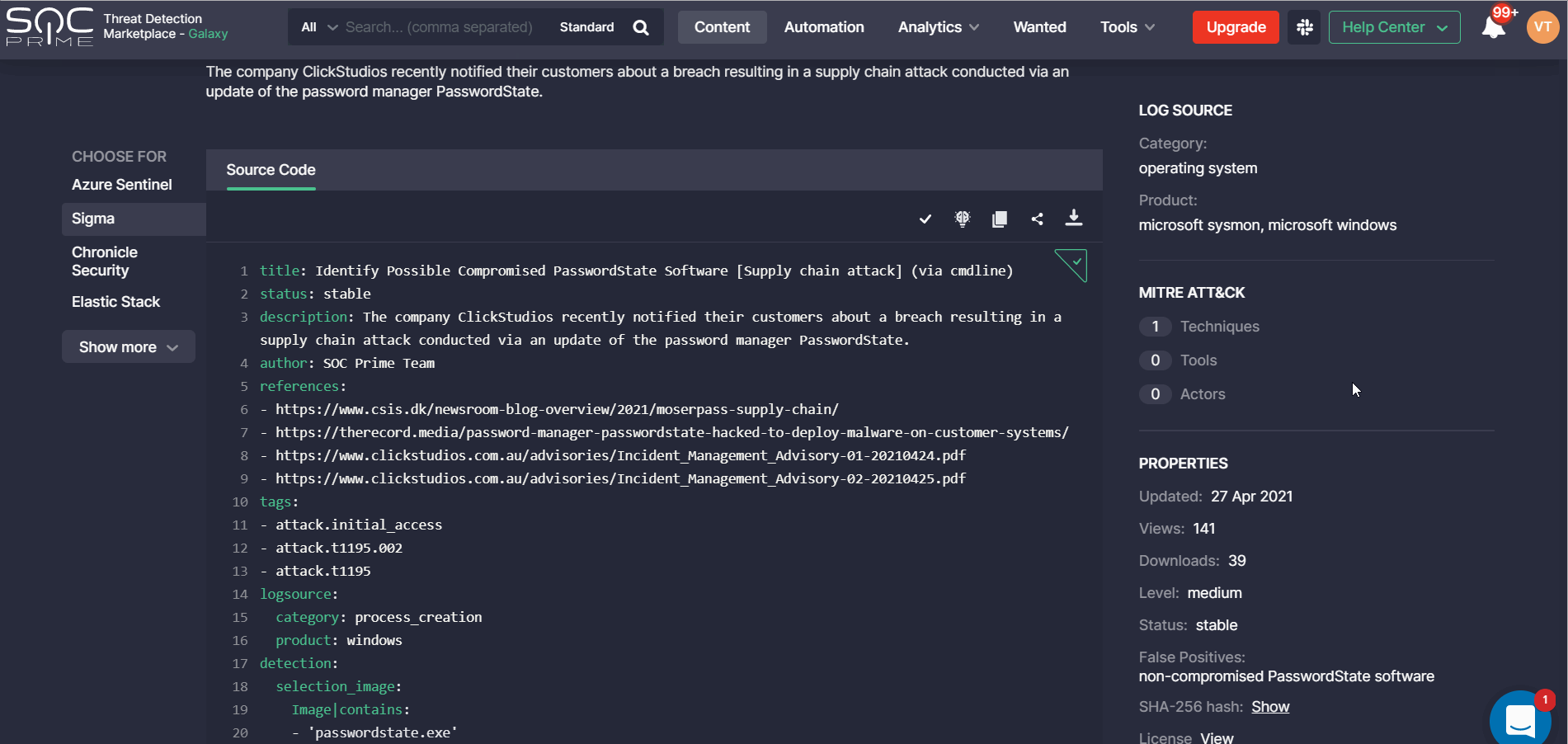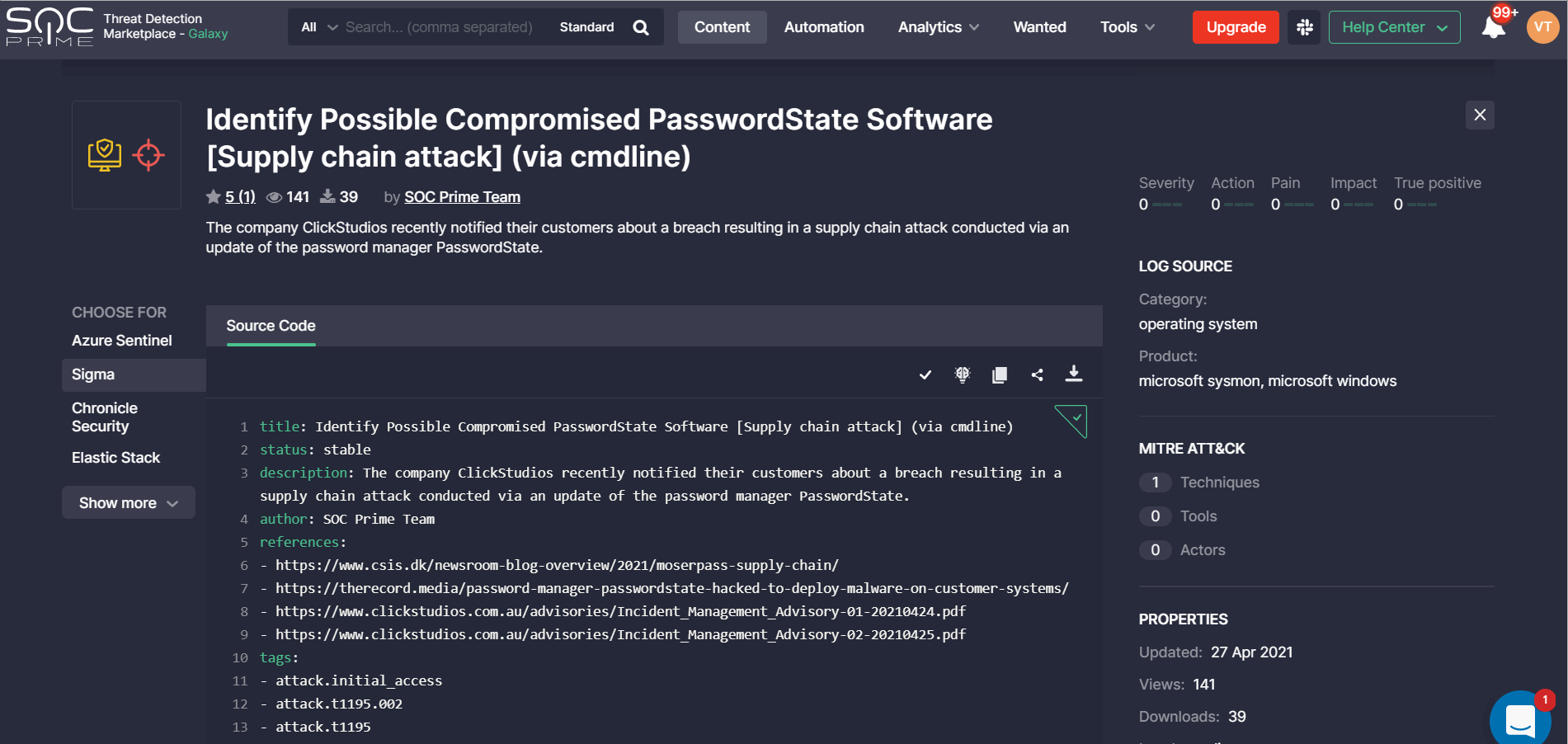
The release of Threat Detection Marketplace version 4.8.0 introduces a brand-new look and feel of the rule page that enables capturing at a glance all the important rule details. Security performers no longer need to switch between tabs to check out the rule context or drill down to the content details — everything is at hand in a single place. The redesigned rule page consists of the following sections:
- General information
- Source code
- Right hand-side panel with log sources, properties, rule metrics, ATT&CK Techniques, Tools, Actors, and related tags
- Rule details, including the timeline, recommended rules, content reviews, and more
General Information
This section of the newly redesigned rule page now displays the use case icon or a set of them if the content item matches multiple categories.
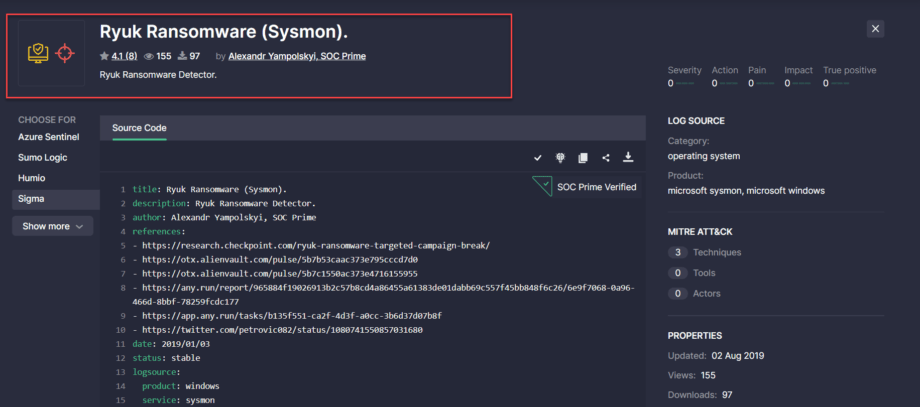
Source Code
We’ve updated the source code section of the rule page in the following way:
- By default, security performers can see four platforms. To see the full platform list, they need to click the Show more button.
The SOC Prime Verified label now appears in this section for rules developed by the corresponding authors. By default, only the checkmark icon is visible, which expands by clicking it to show the full text.
![]()
Right-Hand Side Panel
The following rule-related information moves to the right-hand side panel in the updated rule design, including:
- Log Source
-
- MITRE ATT&CK, which moved from the Context tab in the old design
- Properties, which moved from the Info tab on the old rule page
- Tags
Rule Details
This section at the bottom of the redesigned rule page currently displays the following information related to the specific content item:
- Content Train → Timeline, which was previously displayed on the Context tab
- Recommended Rules that were earlier visible on the Info tab of the old design
Content Reviews, which moved to this section from the Info tab
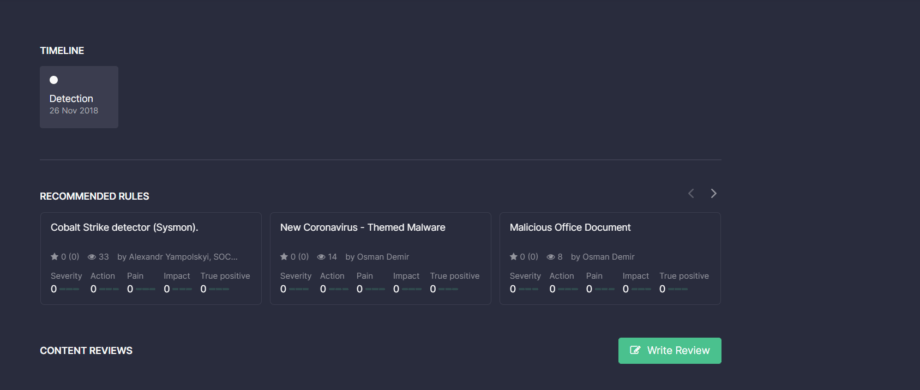
Also, we’ve improved the order of the platform display and removed scrolling from the source code section for an improved user experience.
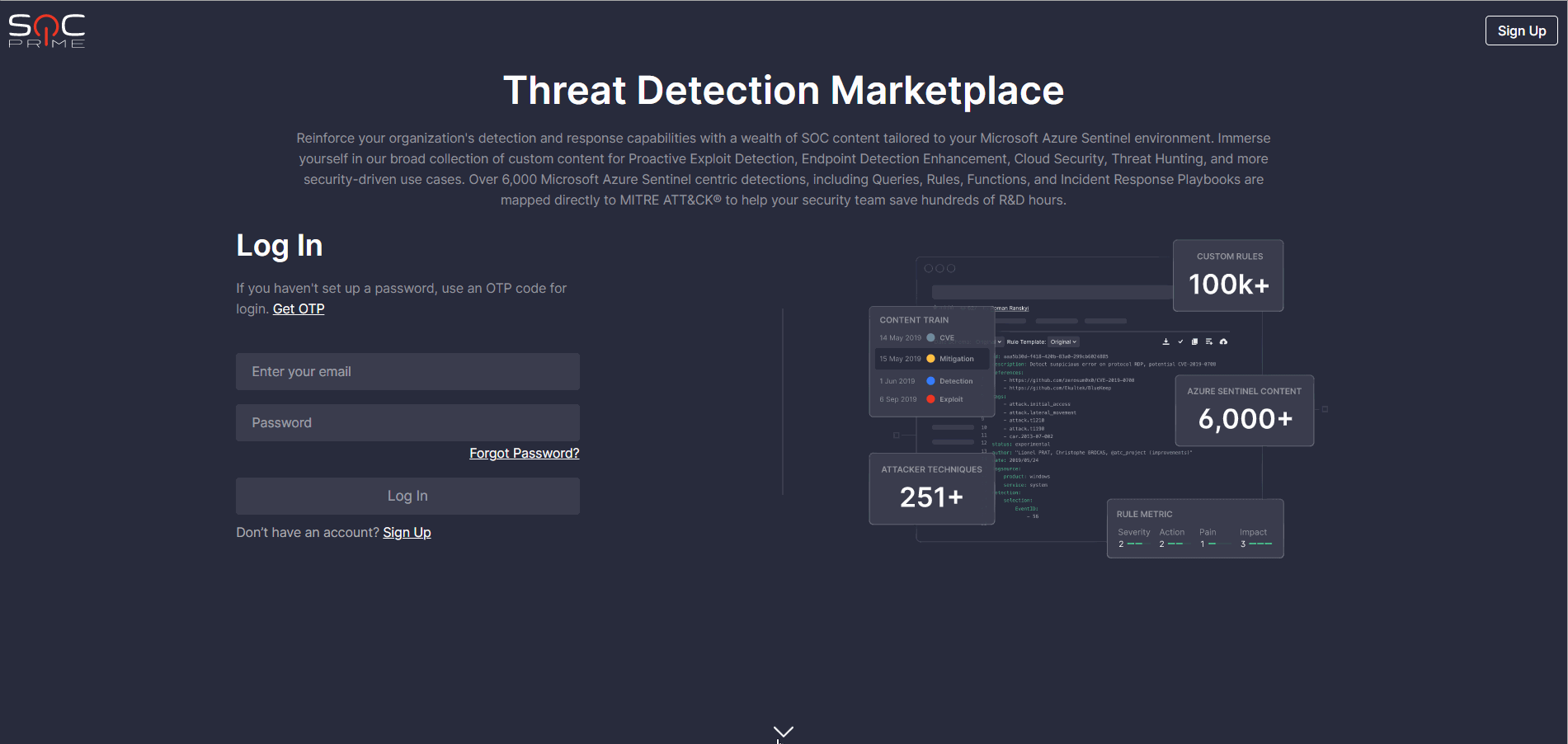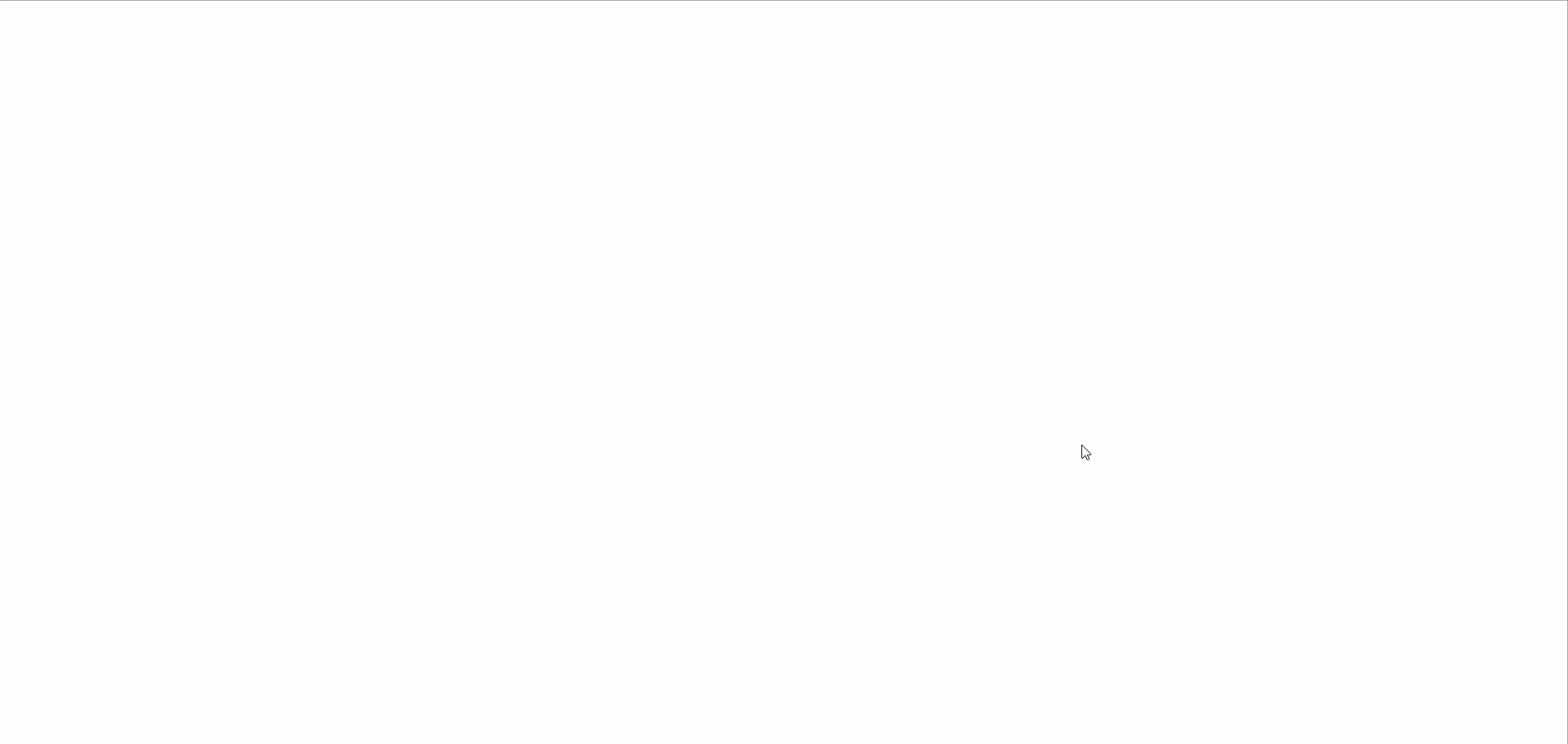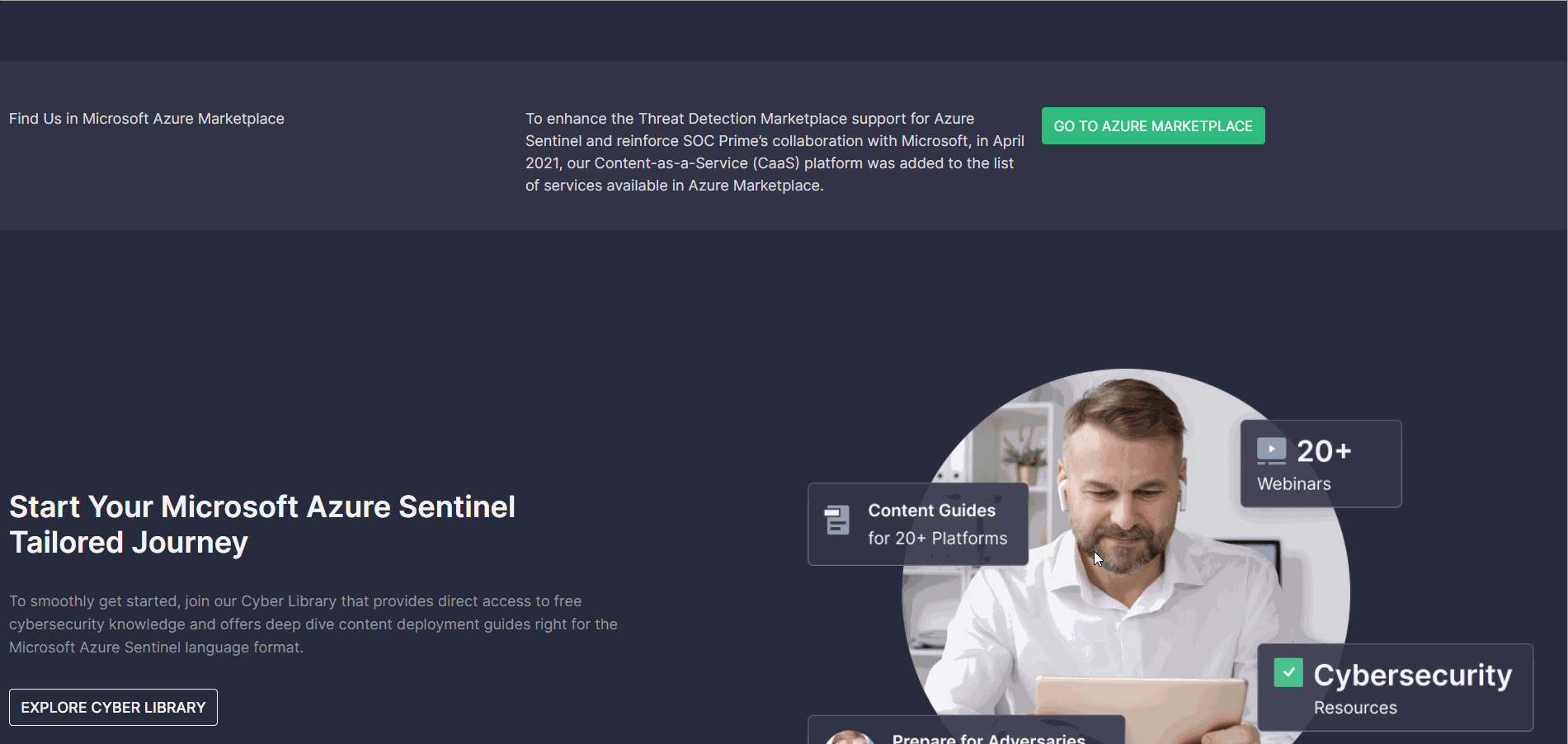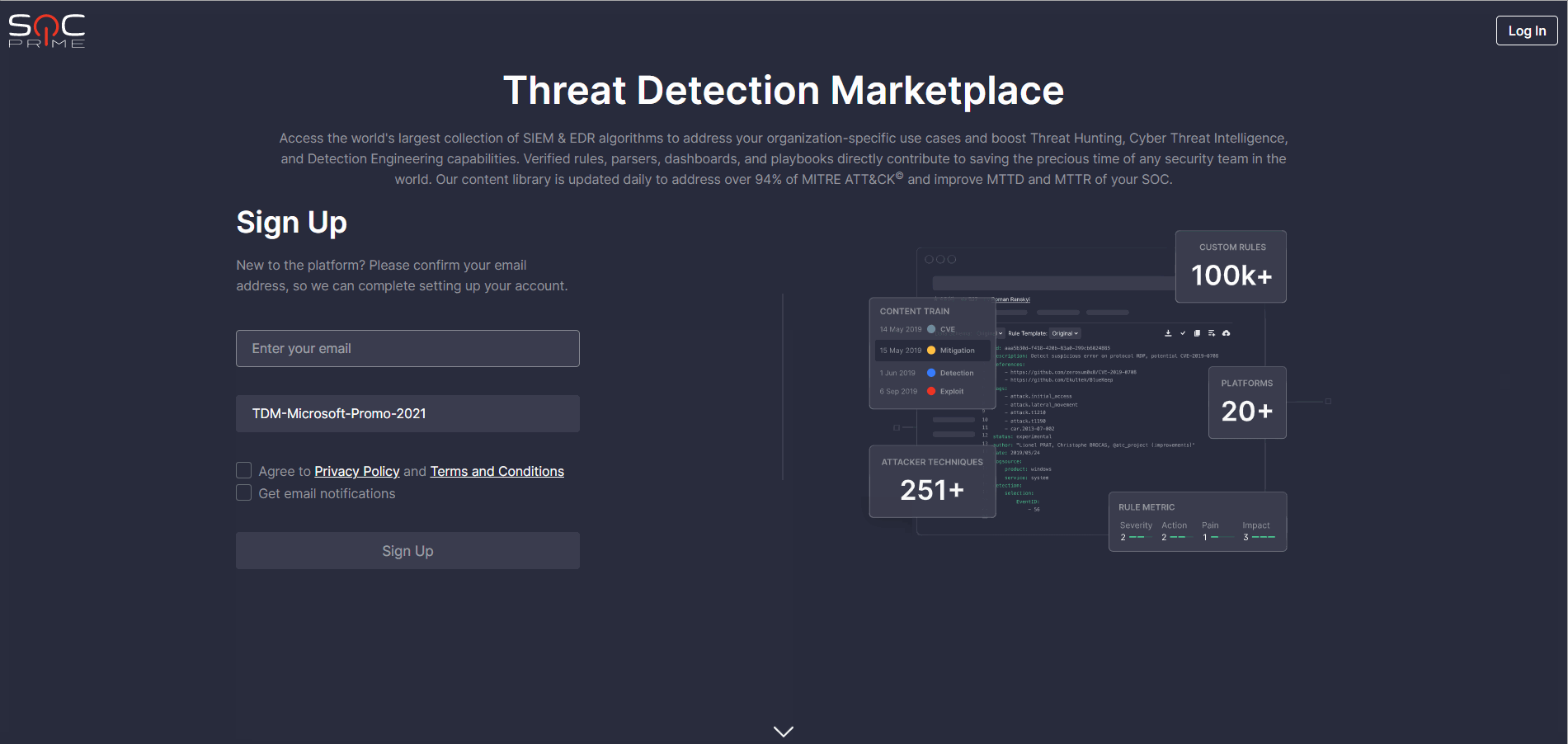
Personalized Login Experience
To deliver the most personalized experience to our Microsoft Azure Sentinel customers, we’ve implemented the Azure-centric login/signup page for Threat Detection Marketplace. Now, security performers who apply the Azure Sentinel solution can see at a glance all the benefits they will gain from leveraging our Detection as Code platform right from this login/signup page. New users can also apply their Microsoft promo codes on the fly upon registration from this freshly released Azure-centric page.
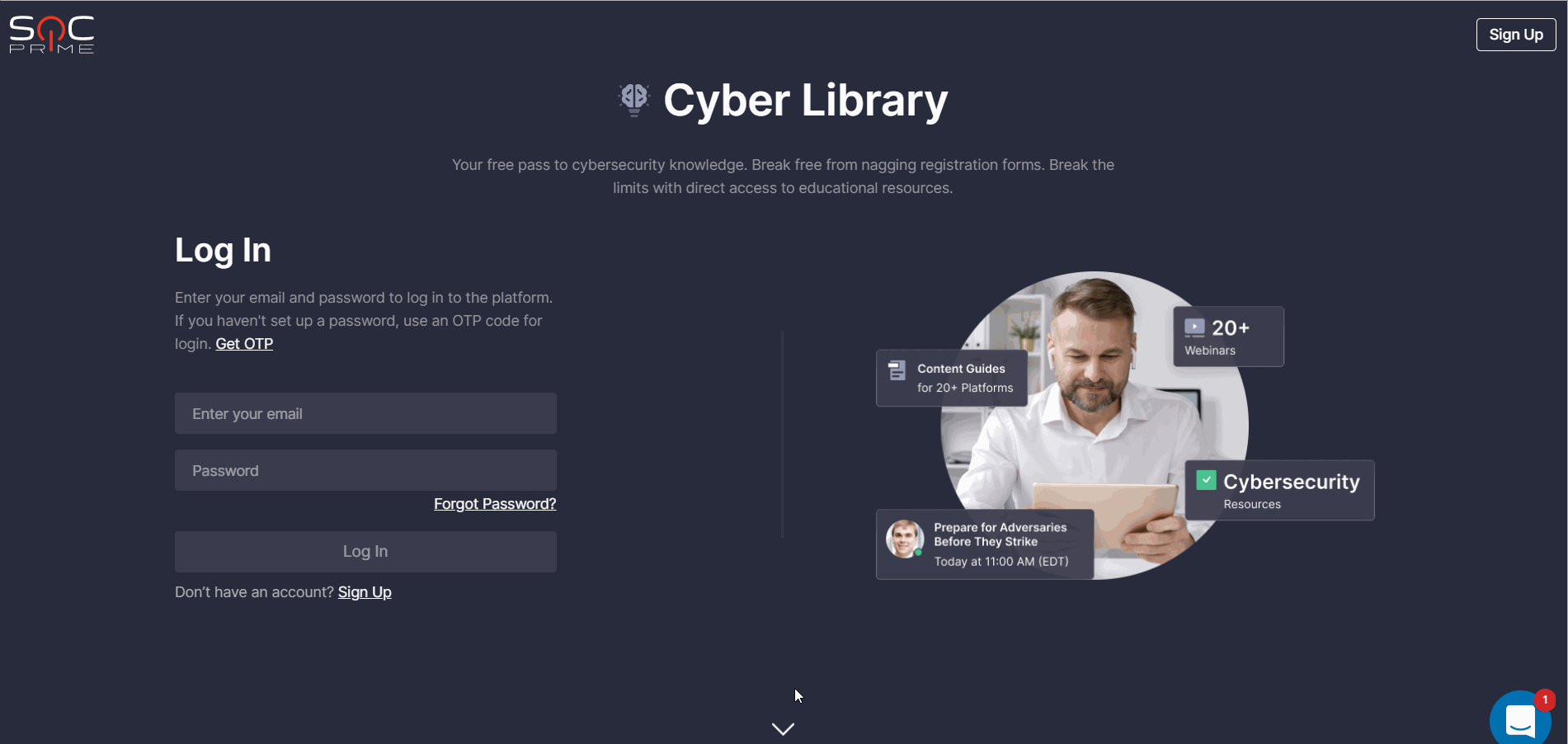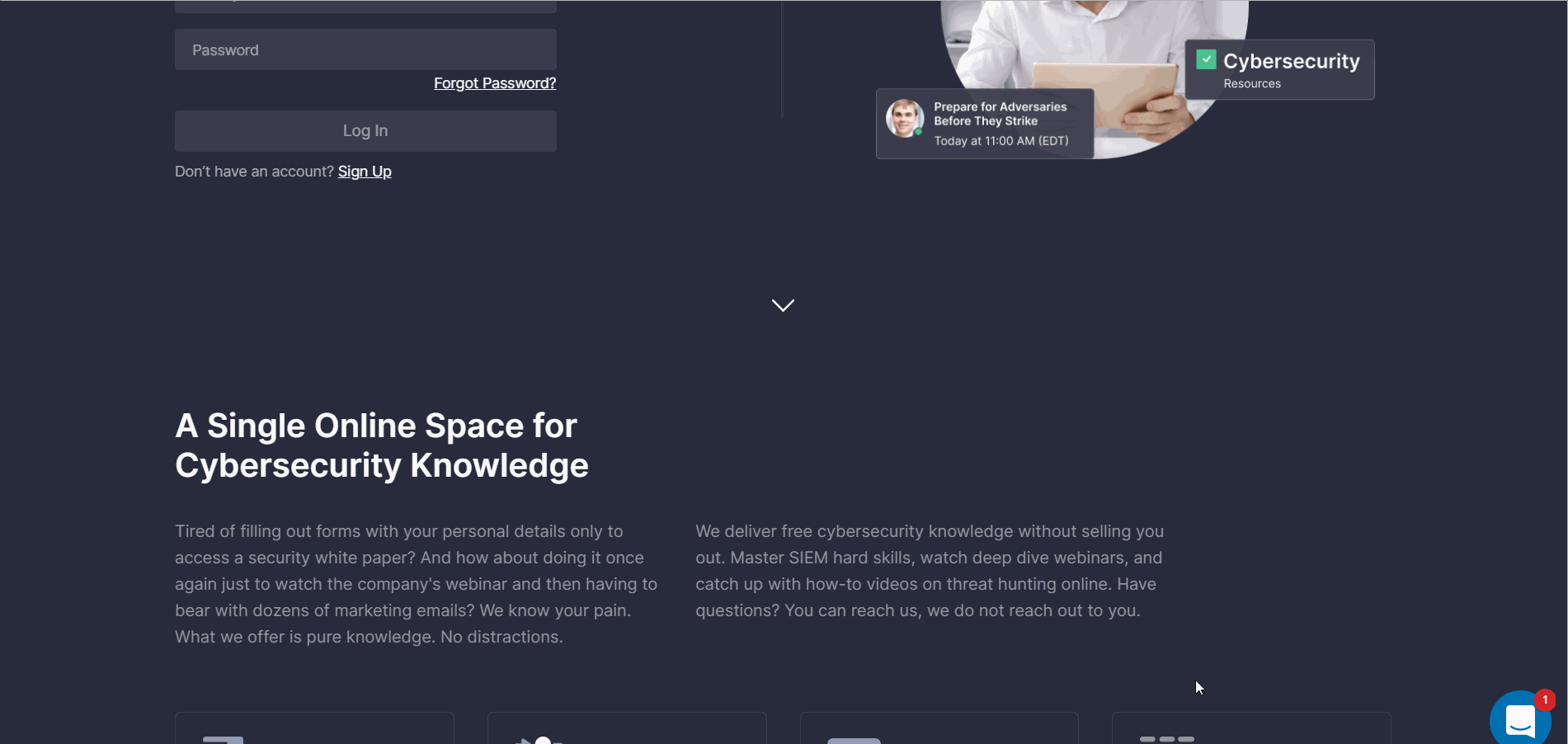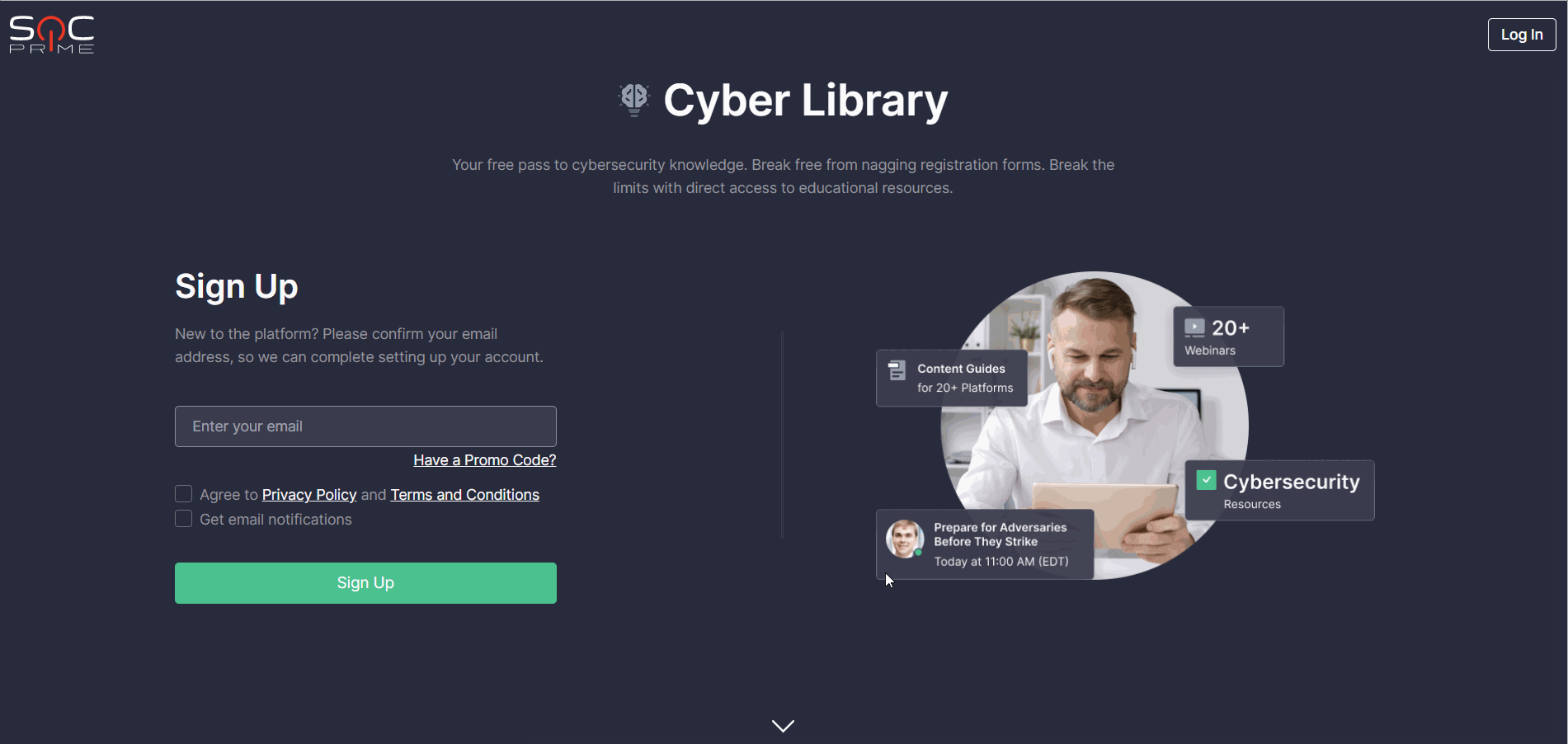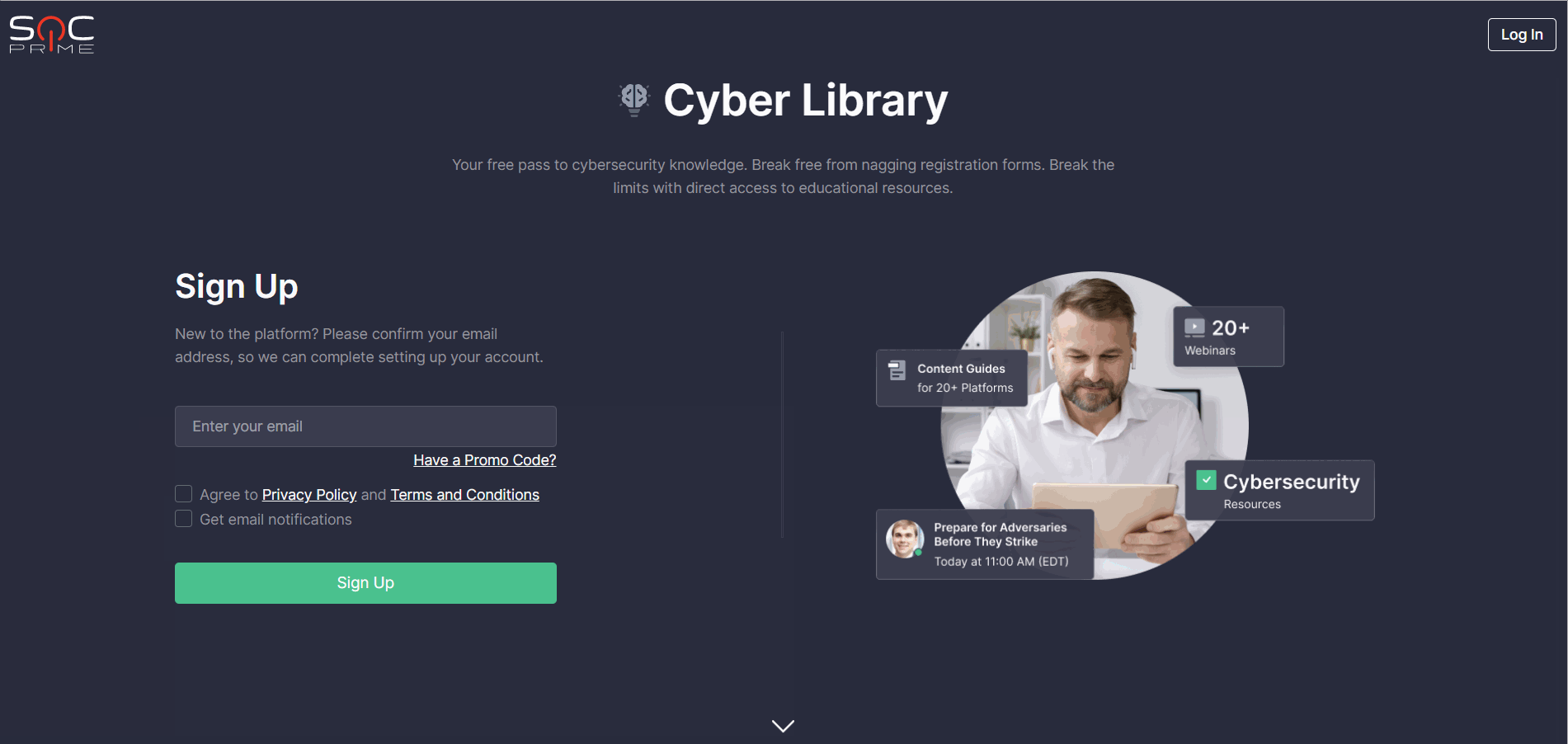
Also, we’ve launched the brand-new look and feel of the Cyber Library login/signup page. The new design enables security enthusiasts to get the gist of the Cyber Library value at a glance. This helps our customers get a brief introduction to the Cyber Library space, understand its core mission, and see all the benefits and capabilities they will gain by joining this free online space for cybersecurity knowledge powered by Threat Detection Marketplace.
FireEye Content Types: OpenIOC Support
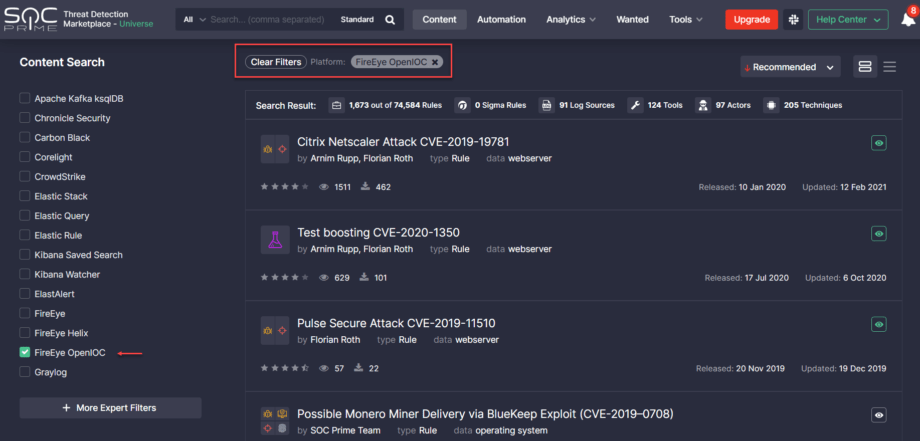
At SOC Prime, we are continuously broadening the support for various SIEM, EDR, and NTDR language formats to make sure our Detection as Code platform delivers cross-tool content tailored to most security solutions. With this latest release, we’ve added the support for the OpenIOC content type in addition to Helix Queries available for the FireEye platform.
Threat Detection Marketplace customers leveraging FireEye can now streamline their search experience by applying OpenIOC from the Platform filter options.
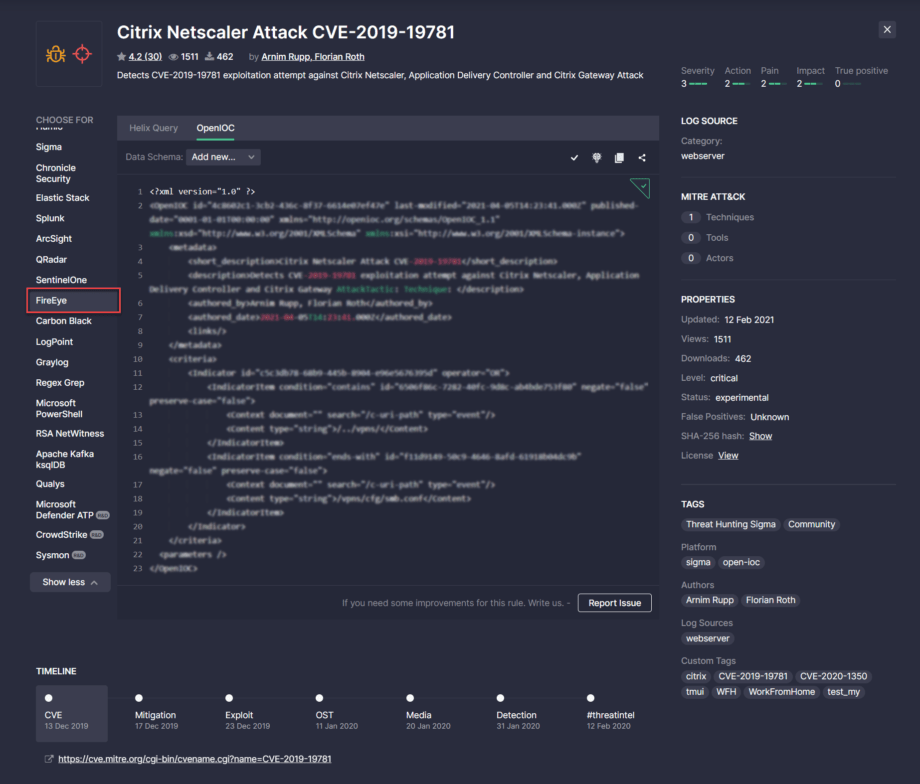
When selecting a certain rule from the filtered list, security performers will see at once the OpenIOC tab with the source code applicable to this language format.
Get a free subscription to Threat Detection Marketplace, an industry-leading Detection as Code platform that provides detection, enrichment, integration, and automation algorithms to support security performers while translating big data, logs, and cloud telemetry into cybersecurity signals. Our SOC content library contains over 100K detection and response rules, parsers, search queries, and other relevant SOC content so you can withstand the growing number of cyber-attacks. Want to craft your own detection content? Join our Threat Bounty Program and get rewarded for your input!


