Sigma Rules Guide for ArcSight

Table of contents:
Introduction to Sigma
Sigma, created by Florian Roth and Thomas Patzke, is an open source project to create a generic signature format for SIEM systems. The common analogy is that Sigma is the log file equivalent of what Snort is to IDS and what YARA is for file based malware detection. However, unlike Snort and Yara, support for Sigma does not have to be built into each application. Sigma acts as the proverbial “rosetta stone” for all platform-specific query languages and enables translation across a myriad of search languages. Below are just a few examples:
Sigma → ArcSight
ArcSight → Sigma → Splunk
Splunk → Sigma → ArcSight
QRadar → Sigma → ArcSight
Conversions are constantly being added to the library with Elasticsearch, Kibana, GrayLog, LogPoint, Splunk, QRadar, ArcSight, and Qualys already supported! This represents a revolutionary new approach to SIEM threat detection that dramatically reduces the overhead associated with traditional development of correlation rules and searches.
https://github.com/Neo23x0/sigma – Visit the Github page for Sigma
SOC Prime and Sigma
As a company founded by security engineers, we always have an eye out for interesting developments in the industry and are constantly looking for ways to give back to the community. SOC Prime does this by both contributing to the development of the Sigma standard and by acting as a bridge between the Sigma authors and community members of our Threat Detection Marketplace which includes over 2200 organizations and over 4000 users. In addition to contributing backend converters to the Sigma project, SOC Prime hosts several resources that are freely available to the public to assist in developing, converting, and consuming Sigma rules.
Development
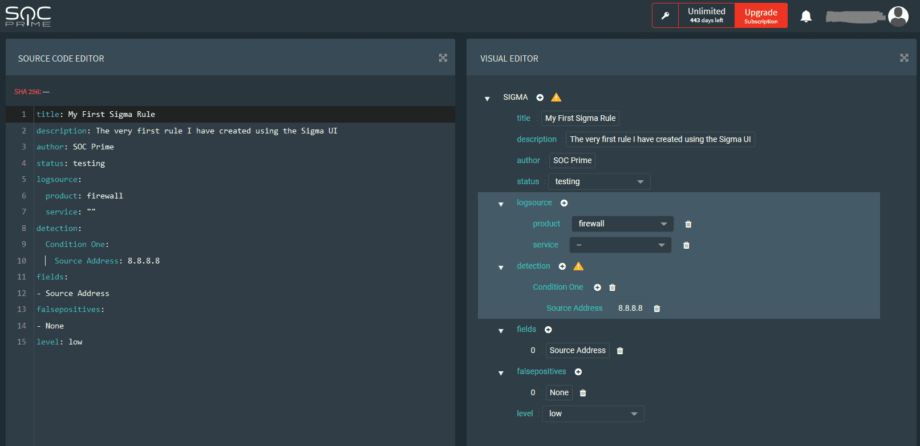
Although the Sigma language is fairly semantic, we acknowledge that some people prefer to work with visual editors when developing. We’ve created the “Sigma UI Editor”; hosted on our Threat Detection Marketplace, where users can leverage our syntax check and export functions for various platforms. We like to say that this is a lite web-based IDE for Sigma development.
Access the Sigma UI Editor here: https://tdm.socprime.com/sigma/
Conversion
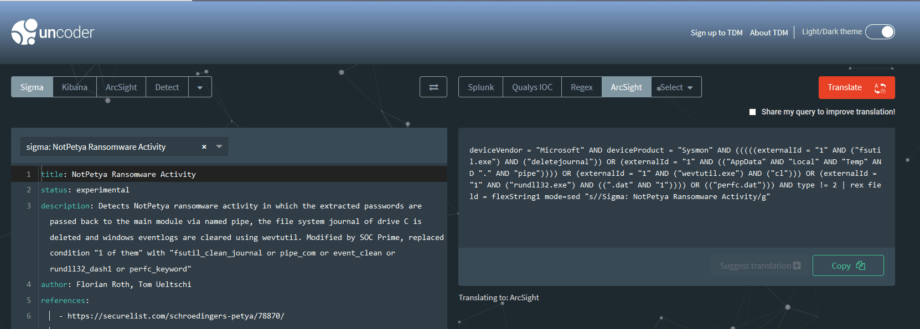
SOC Prime created “Uncoder.io” to assist users in taking search queries from any supported language and converting them into another. The functionality is similar to Google Translate; simply paste one language in, choose an output language, and press translate! We use the Sigma language as a common denominator to even make cross-platform conversion possible. By default, we don’t keep any of the information entered into the translator. However, if you do find errors with a particular conversion, share your query with us so that we can improve the tool.
Access our translation tool here: https://uncoder.io/#
Consumption
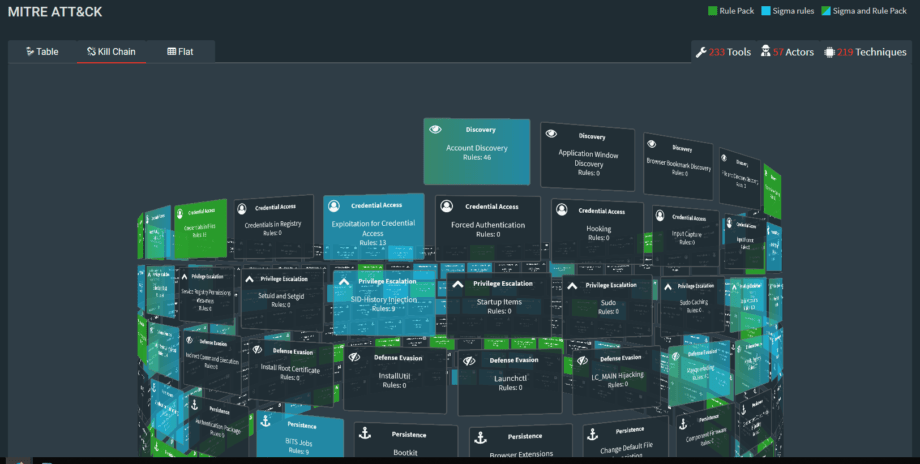
SOC Prime is proud to host Sigma content on our Threat Detection Marketplace. In addition to content made specifically for popular SIEM systems, the TDM hosts over 200 free Sigma rules that come pre-converted. With a community of over 2200 organizations and over 4000 users, we give developers a common space to share and consume detection content. We make it easy to explore rules by tagging each rule with log sources, threat actors, and even TTPs via the MITRE ATT&CK matrix. Sign up is free and over two thirds of our content costs nothing to download!
Sign up for free here: https://tdm.socprime.com
Enthusiastic about creating your own Sigma rules? Explore our Sigma Rules Guide for Beginners.
Leveraging Sigma in ArcSight
Initial Testing & Setup
1. Log in to your ArcSight Command Center or Logger instance.
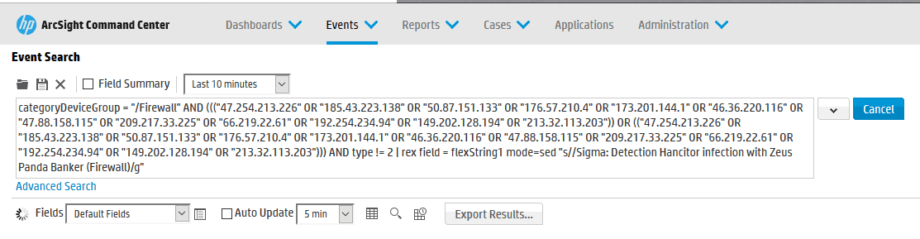
2. Paste your test query into the search field and choose a time frame.
3. Examine Results.
Saved Search & Scheduling
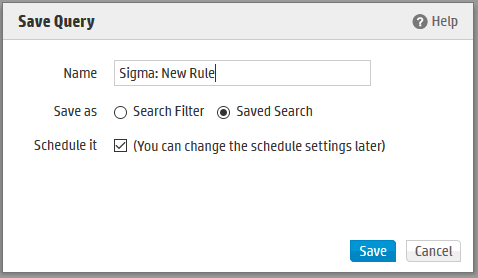
1. Save query as a Saved Search
- Use nomenclature ‘Sigma: RULE NAME’. Where RULE NAME is Sigma Rule Name from TDM.
- Choose option ‘Schedule It’
- Select Save
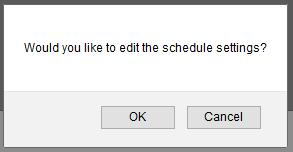
2. A dialogue box asking “Would you like to edit the schedule settings?” will appear. Select OK.
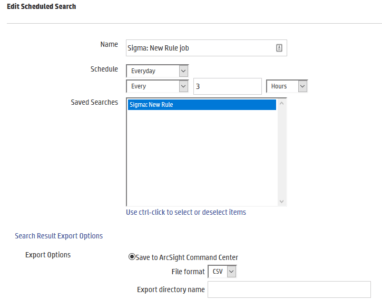
3. Use the following configuration options:
-
- Specify Time Period (This will depend on the user’s environment and preferences)
- Select ‘Save to ArcSight Command Center’
- Leave ‘Export directory name’ empty
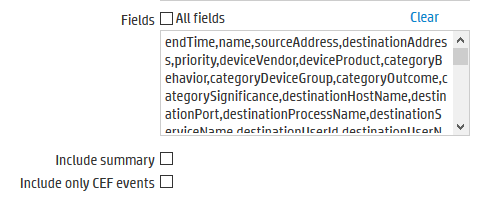
- Uncheck option ‘All Fields’
- Paste the following text into the ‘Fields’ option:
endTime,name,sourceAddress,destinationAddress,priority,deviceVendor,deviceProduct,categoryBehavior,categoryDeviceGroup,categoryOutcome,categorySignificance,destinationHostName,destinationPort,destinationProcessName,destinationServiceName,destinationUserId,destinationUserName,deviceAction,deviceAddress,deviceHostname,deviceProcessName,deviceCustomNumber1,deviceCustomNumber1Label,deviceCustomNumber2,deviceCustomNumber2Label,deviceCustomString1,deviceCustomString1Label,deviceCustomString2,deviceCustomString2Label,deviceCustomString3,deviceCustomString3Label,deviceCustomString4,deviceCustomString4Label,deviceCustomString5,deviceCustomString5Label,deviceCustomString6,deviceCustomString6Label,fileName,filePath,flexString1,flexString1Label,flexString2,flexString2Label,sourceHostName,sourcePort,sourceProcessName,sourceServiceName,sourceUserId,sourceUserName
Leave “Include summary” and “Include only CEF events” unchecked.
4. Access the saved search results:
- Click Administration > Saved Searches and then open the Saved Search Files tab. The files containing the search results are displayed.
- To download and open a file, click a link in the Name column or click the Retrieve icon in the row
5. OR Manually review results in the following directory.
/opt/arcsight/logger/userdata/logger/user/logger/data/savedsearch directory
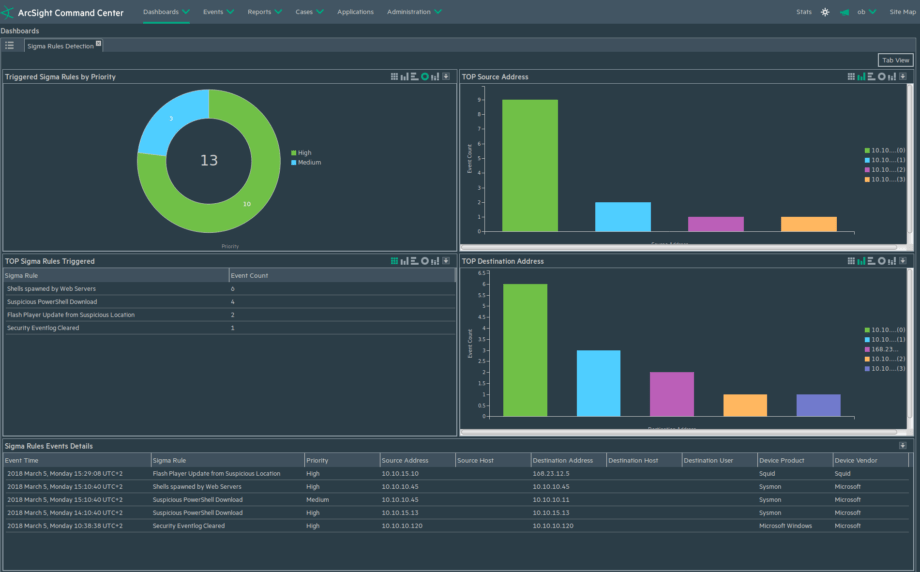
SIGMA Rules Integration Pack
Instead of manually reviewing the saved search results, SOC Prime has developed an entire framework for ArcSight that automatically ingests the search data and produces actionable information in the ESM. This includes a FlexConnector, Filter, Dashboard, and Active Channel designed by our veteran engineers and tested in our own SOC.
This package is free to download through our Threat Detection Marketplace: https://tdm.socprime.com/tdm/info/33/