SOC Prime Unlocks Free Hunting Content to Defend Against Russia-Backed Cyber Threats

On February 24, 2022, Russia ignored international law and long-standing diplomatic agreements to launch a full-scale invasion of Ukraine by land, sea, and air. Disinformation campaigns continue to try and hide the facts that the Russian aggression has abandoned the basic principles of humanity, killing civilians, destroying cities, and creating a massive humanitarian crisis as millions of displaced Ukrainians flee the country seeking refuge from the War.
The full-scale invasion of Ukraine has now lasted three weeks, but the cyberwar against the Ukrainian infrastructure has been ongoing for over seven years. In 2016-2017 Russia launched the BlackEnergy attacks that targeted the country’s power grid. This was followed by the now infamous NotPetya attacks in 2017 and the first-of-its-kind VPNFilter attack targeting the Auly Chlorine Distillation Station in 2018. The Russian military invasion was preceded by a long-running cyber warfare campaign designed to weaken infrastructure and disrupt government operations.
At the turn of 2022, a new surge of more advanced cyber-attacks hit Ukraine. In mid-January, attackers leveraged WhisperGate data-wiping malware to cripple the digital infrastructure of the Ukrainian government. This devastating cyber-attack was attributed to the Russian nation-backed hacking collectives. Likewise, cybersecurity researchers linked subsequent HermeticWiper malware and FoxBlade Trojan attacks to Russian state-sponsored APT groups aiming to undermine the country’s stability on all fronts.
Free Hunting Content to Defend Against Russia-backed Cyber Threats
To help security practitioners detect and prevent cyber-attacks of Russian state-sponsored hacking collectives, SOC Prime has unlocked a large collection of free Sigma rules available in our Detection as Code platform. These rules will identify the malicious activity of Russia-backed APT groups, covering the most common tactics, techniques, and procedures (TTPs) of the affiliated hackers. Also, the detection content available as part of this free offering is designed to detect possible infections of the most recent Russian-sourced malware, including the FoxBlade, WhisperGate, HermeticWiper, and more.
- The detection content is available at no charge for all users of the SOC Prime Platform that have registered with a corporate email address. Those that have registered with personal email addresses may change to corporate addressing to immediately access this detection content to start hunting with tagged content for Russia-backed cyber threats.
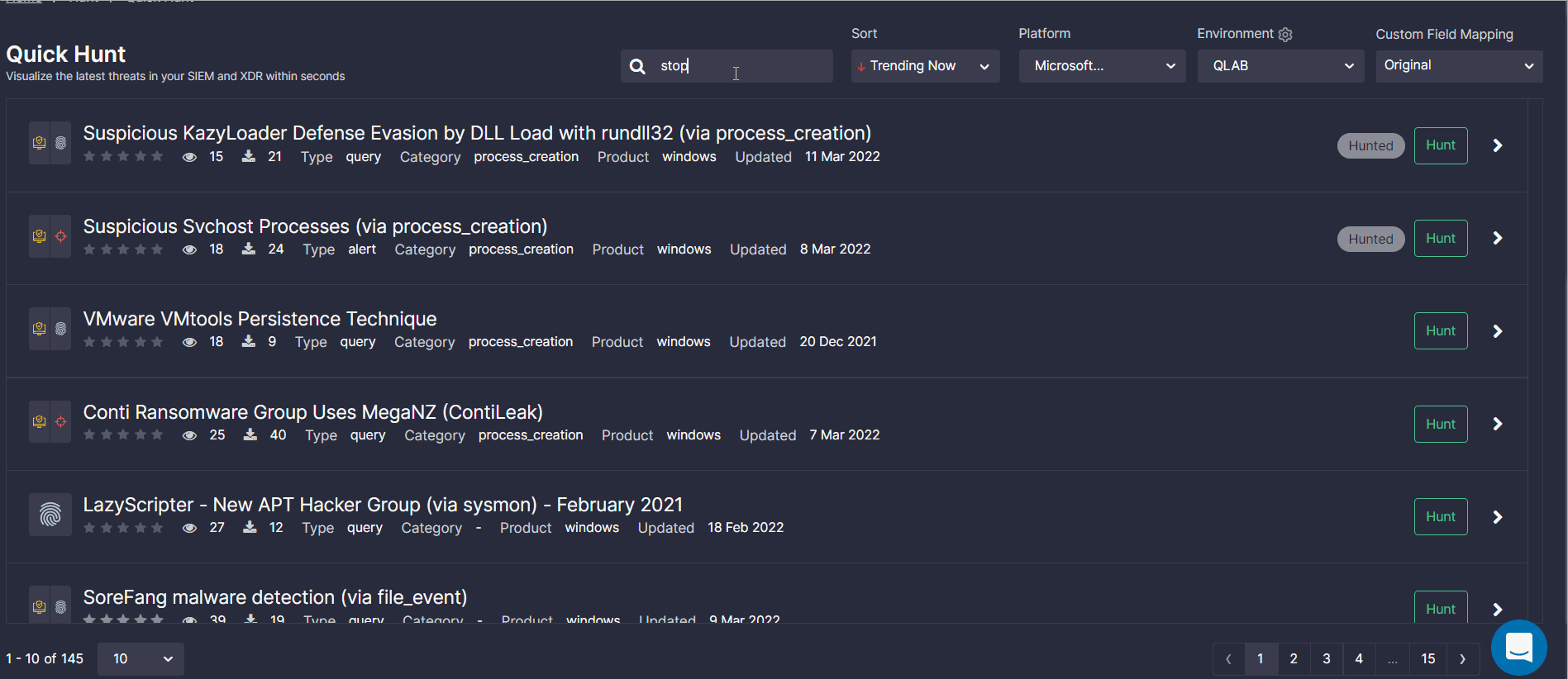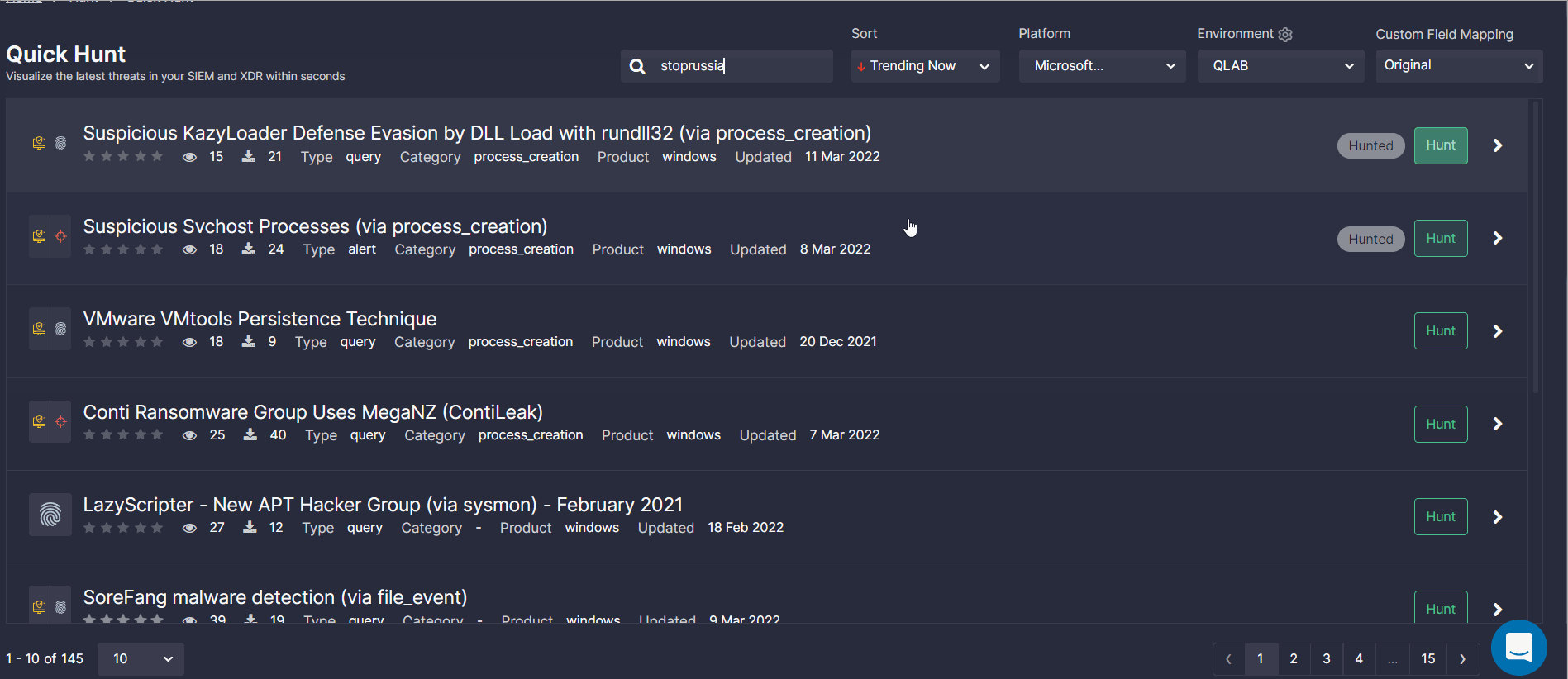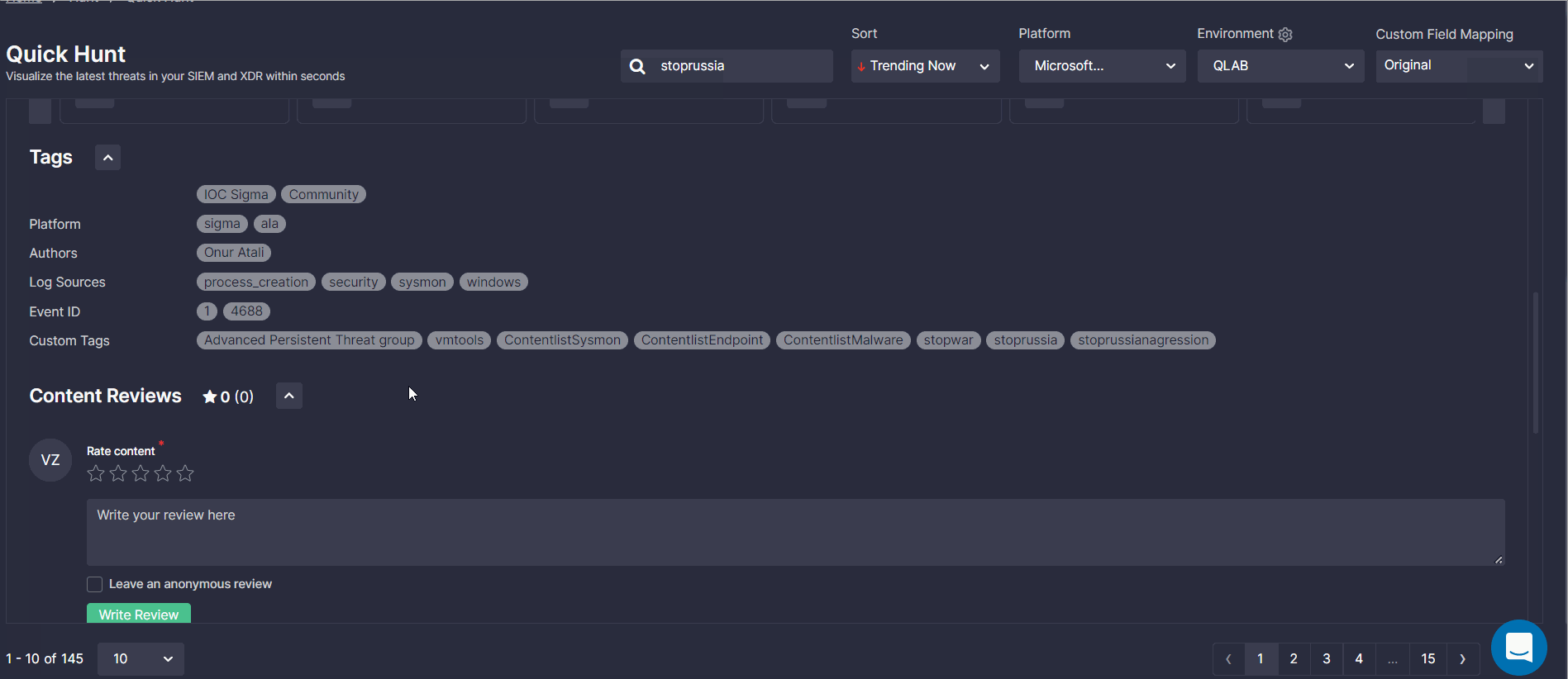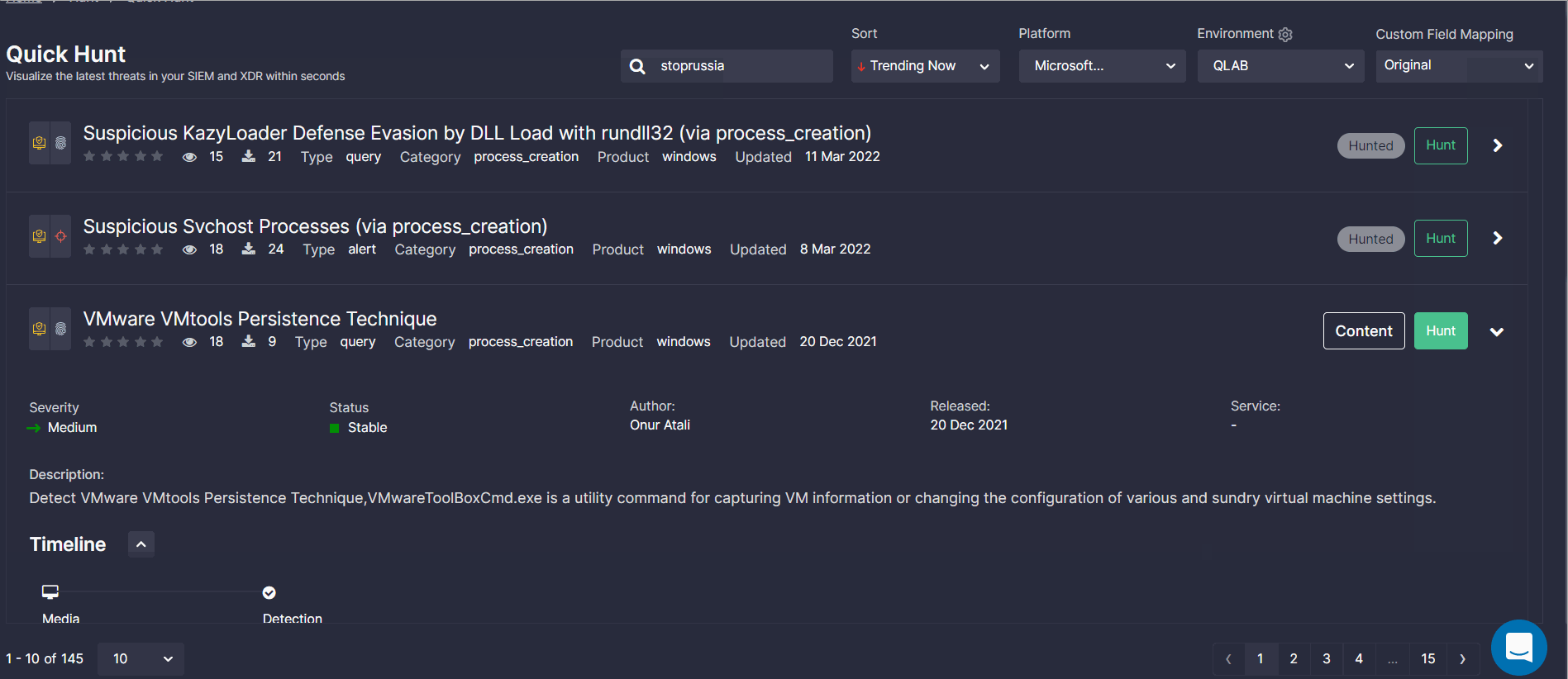
- All detections available as part of this promo are tagged with #stopwar, #stoprussian, and #stoprussianagression tags, to make content searches for Russia-backed cyber threats easier and faster. These tags cover all detections associated with the Russian state-sponsored APT groups and those identified as specific Russia-originated threats.
Please sign up or log in to the SOC Prime Platform here:
Promo content to hunt for Russian-backed cyber-attacks
You’ll land at the Quick Hunt module page displaying the comprehensive list of detections matching the relevant custom tags.
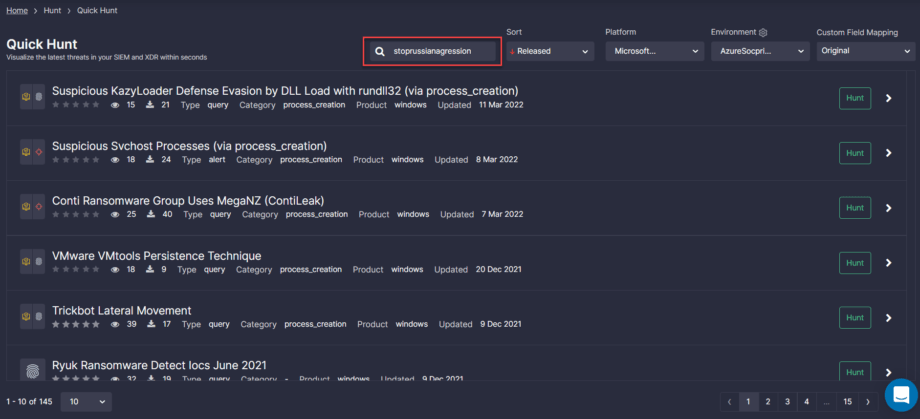
Select the platform and environment and then drill down to search for threats in your SIEM or EDR with a single click.
Please note that the number of hunts per day depends on your current subscription tier.
Teams can also search for dedicated content by entering one of the custom tags, like stoprussia right into the Search field of the Quick Hunt page, and the list of detections will be filtered accordingly.
Gain from collective cybersecurity expertise by joining the world’s largest and most advanced platform for collaborative cyber defense to evolve your threat detection capabilities and boost threat hunting velocity faster and easier you could imagine. Individual threat hunters and researchers can join SOC Prime’s crowdsourcing initiative and contribute their detection content to enrich the collective expertise and help shape the future of cyber defense.


