UAC-0050 Attack Detection: Hackers Are Armed with Remcos RAT, Quasar RAT, and Remote Utilities to Target Ukraine Once Again

Table of contents:
At the end of 2023, the nefarious UAC-0050 group loomed in the cyber threat arena, targeting Ukraine using Remcos RAT, a common malware from the group’s offensive toolkit. In the first decade of January 2024, UAC-0050 reemerges to strike again, exploiting Remcos RAT, Quasar RAT, and Remote Utilities.
UAC-0050 Offensive Activity Overview Based on the Latest CERT-UA Reports
On January 11, 2024, CERT-UA published two security alerts, CERT-UA#8453 and CERT-UA#8494, to notify industry peers of the recently uncovered cyber attacks against Ukraine leveraging phishing lures with the email subjects and file names linked to requests. The hacking collective tracked as UAC-0050 is behind all the incidents covered by the most recent CERT-UA alerts.
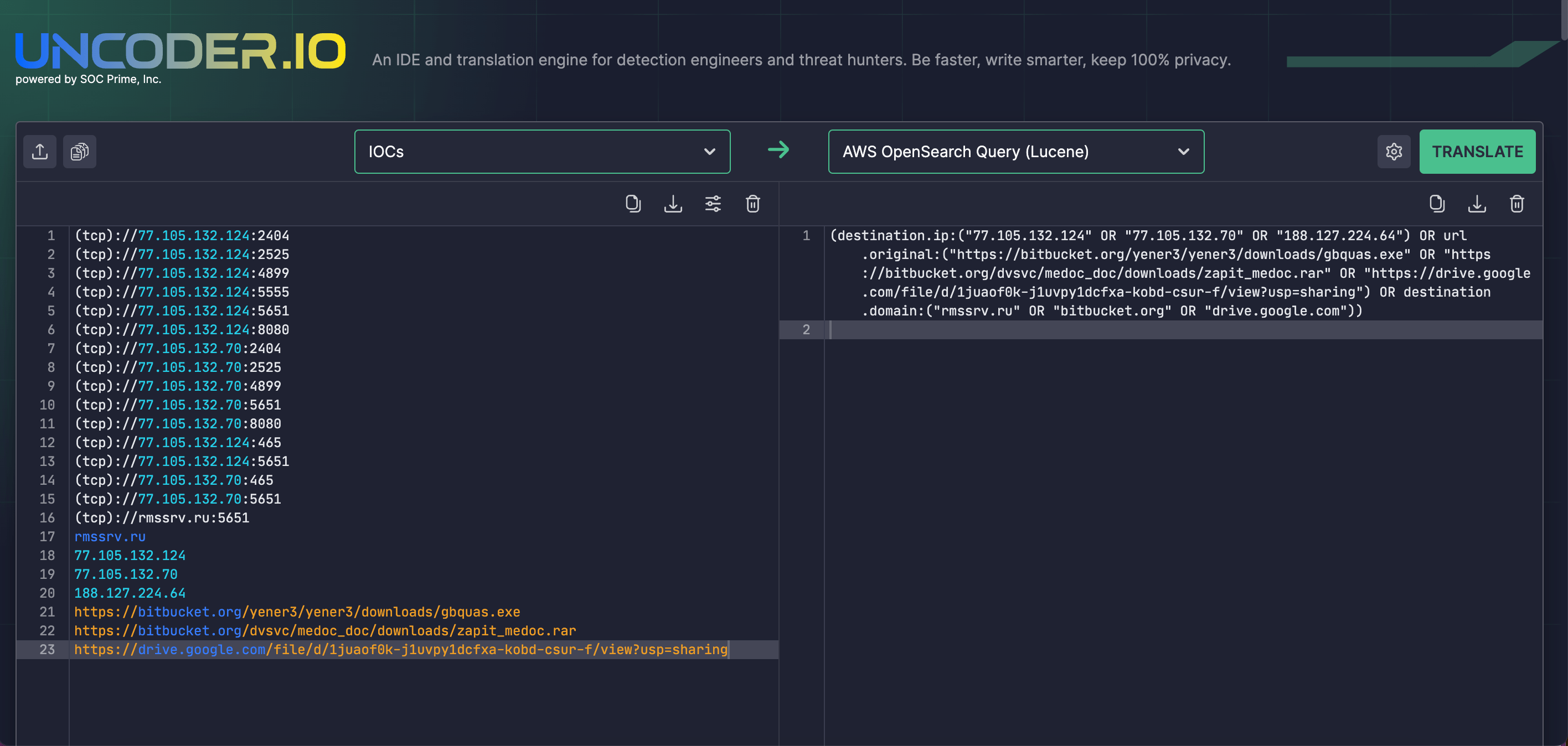
The first identified incident involves mass email distribution with the subjects requesting court documents. The emails include an RAR attachment with a ZIP archive, which contains a protected multi-volume RAR archive and a TXT file with a password for it. The above-referenced archive goes with an executable file designed to create and execute an AutoIt script, which, in turn, facilitates the installation of the Remcos RAT remote administration tool, largely leveraged by the UAC-0050 hackers in their adversary campaigns targeting Ukraine.
In the second incident uncovered by CERT-UA, the archive contains an executable file that applies PowerShell commands to launch and run the malicious Quasar RAT malware downloaded from the legitimate Bitbucket service.
Two days later, after the two detected incidents, CERT-UA unveiled another phishing attack using emails with the subject impersonating the request from the company Medoc. The emails similarly contained a RAR attachment or a link for its download from Bitbucket or Google Drive services. The RAR file contained a password-protected multi-volume archive with a lure file and an executable file. Running the latter leads to installing the remote administration program known as Remote Utilities on the compromised system.
In all cases, UAC-0050 took advantage of the C2 servers located within the AS215939 autonomous system.
Detect UAC-0050 Activity Addressed in the CERT-UA#8453 and CERT-UA#8494 Alerts
In the second half of 2023, there was a notable increase in phishing attacks against Ukrainian organizations associated with the UAC-0050 group. At the turn of 2024, UAC-0050 threat actors hit again, attempting to lure victims into opening phishing emails and compromising the targeted systems. By relying on SOC Prime Platform for collective cyber defense, organizations can effectively preempt cyber attacks and minimize the risks of adversary intrusions. Log into the Platform to reach a set of dedicated detection algorithms mapped to MITRE ATT&CK® and automatically convertible to dozens of cybersecurity languages. All detections are tagged based on the relevant CERT-UA reports for ease of content search.
Sigma rules to detect the UAC-0050 attacks addressed in the CERT-UA#8453 and CERT-UA#8494 alerts
Innovative companies striving to fortifying their defenses and closing all the gaps in detection coverage can employ a comprehensive set of verified rules and queries tailored for UAC-0050 attack detection. Hit Explore Detections to reach dedicated SOC content enriched with threat intel and relevant metadata.
CERT-UA has also provided a list of IOCs to facilitate retrospective hunting. With Uncoder IO, security engineers can streamline IOC matching using the provided threat intel and seamlessly generate custom search queries tailored for multiple SIEM or EDR environments.
MITRE ATT&CK Context
SOC team members can also explore the attack details provided in the CERT-UA#8453 and CERT-UA#8494 heads-ups. Dive into the table below to find the list of all applicable adversary TTPs linked to the above-mentioned Sigma rules for in-depth analysis:
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing (T1556) | |
Phishing: Spearphishing Attachment | ||
Execution | Exploitation for Client Execution (T1203) | |
Scheduled Task / Job (T1053) | ||
Software Deployment Tools (T1072) | ||
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) | ||
Command and Scripting Interpreter: JavaScript (T1059.007) | ||
Persistence | Boot or Logon Autostart Execution (T1547) | |
Defense Evasion | Indicator Removal (T1070) | |
Indicator Removal: File Deletion (T1070.004) | ||
Masquerading (T1036) | ||
Masquerading: Match Legitimate Name or Location (T1036.005) | ||
Masquerading: Double File Extension (T1036.007) | ||
Masquerading: Masquerade File Type (T1036.008) | ||
Visualization / Sandbox Evasion: Time Based Evasion (T1497.003) | ||
System Script Proxy Execution (T1216) | ||
System Binary Proxy Execution (T1218) | ||
Obfuscated Files or Information (T1027) | ||
Subvert Trust Controls (T1553) | ||
Command and Control | Ingress Tool Transfer (T1105) | |
Remote Access Software (T1219) | ||