UAC-0050 Attack Detection: Hackers Launch Another Targeted Campaign Spreading Remcos RAT

Table of contents:
Hard on the heels of the phishing attack impersonating the Security Service of Ukraine and using Remcos RAT, the hacking collective identified as UAC-0050 launched another adversary campaign against Ukraine leveraging the phishing attack vector. In these attacks targeting 15,000+ users hackers massively send emails with a subject and attachment lures related to a summons to court topic aimed to spread Remcos RAT on the impacted systems.
Phishing Attack Analysis Attributed to UAC-0050 and Spreading Remcos RAT
The latest CERT-UA#8150 alert covers another malicious activity by the UAC-0050 threat actors distributing Remcos RAT malware. Adversaries abuse the summons to court topic striving to lure targeted users into opening the malicious email content and an RAR attachment. The latter contains a password-encrypted file with a DOC file and a malicious macro. Once activated, the code macro runs an executable file on the compromised machine via explorer.exe and the SMB protocol. This EXE file is obfuscated using the SmartAssembly .NET-based software designed for decrypting and launching Remcos RAT.
Notably, the latest campaign by UAC-0050 targets at least 15,000 users using legitimate compromised email accounts of one of the Ukrainian judicial authorities. Considering the scope of potential victims, CERT-UA stresses the importance of taking urgent measures to remediate the threat.
Detect the UAC-0050 Campaign Covered in the CERT-UA#8150 Alert
With the increasing number of UAC-0050 attacks against Ukraine, defenders are searching for ways to reinforce their threat detection capabilities and safeguard the infrastructure against adversary intrusions. SOC Prime Platform offers a curated list of detection algorithms to thwart attacks by the UAC-0050 group described in the latest CERT-UA alert. Use the link below to drill down to the list of relevant Sigma rules filtered by the custom tag “CERT-UA#8150” matching the security notice ID:
Detection content for UAC-0050 attacks covered in the CERT-UA#8150 alert
All Sigma rules are aligned with the MITRE ATT&CK® framework, enriched with tailored intelligence, and can leveraged across dozens of SIEM, EDR, XDR, and Data Lake solutions.
Looking for more detection content to withstand existing phishing attacks linked to the UAC-0050 hacking collective? Click Explore Detections to reach the entire collection of SOC content from Threat Detection Marketplace for UAC-0050 attack detection and always stay ahead of adversaries.
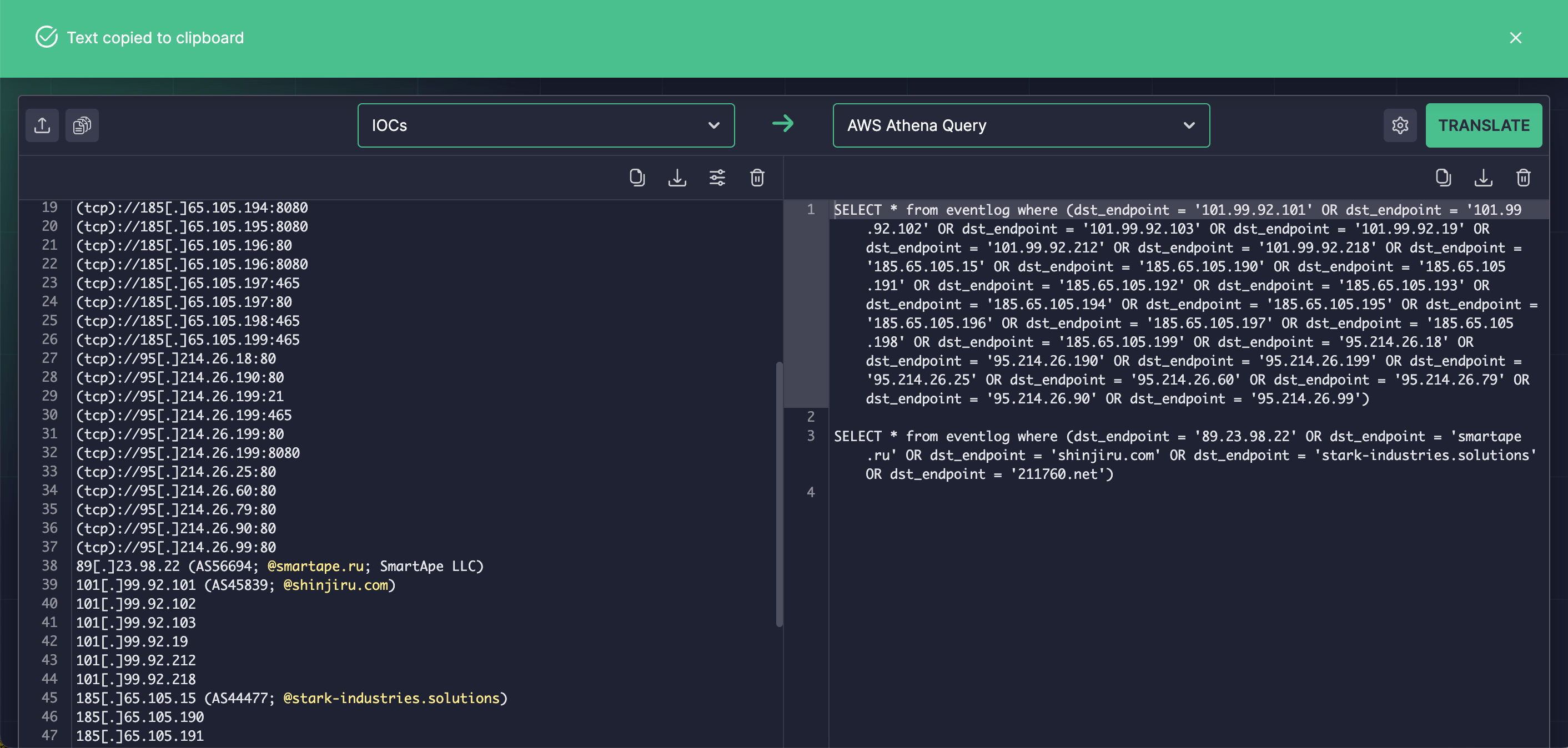
SOC Analysts, Threat Hunters, and CTI experts can also take advantage of automated IOC packaging capabilities offered by the Uncoder IO open-search IDE for detection engineering. Just paste IOCs from the latest CERT-UA heads-up and instantly convert them into custom search queries tailored for the chosen language format to seamlessly hunt for the UAC-0050 malicious activity.
MITRE ATT&CK Context
SOC team members can also explore the attack details provided in the CERT-UA#8150 heads-up. Dive into the table below to find the list of all applicable adversary tactics, techniques, and sub-techniques linked to the above-mentioned Sigma rules for in-depth analysis:
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | Exploitation for Client Execution (T1203) | |
Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | |
| Masquerading (T1036) | |
Masquerading: Double File Extension (T1036.007) | ||
Obfuscated Files or Information (T1027) | ||
Lateral Movement | Remote Services: SMB / Windows Admin Shares (T1021.002) |