The financially motivated group identified as UAC-0006 has been actively launching phishing attacks targeting Ukraine throughout 2023. CERT-UA team reports the reemergence of UAC-0006 in the cyber threat landscape in spring 2024. In the ongoing campaigns, hackers attempt to distribute SMOKELOADER, the common malicious sample from the group’s adversary toolkit.
UAC-0006 Latest Activity Analysis Spreading SMOKELOADER
Throughout 2023, the financially motivated group UAC-0006 massively attacked Ukraine in several offensive phishing campaigns, exploiting financial subject lures and abusing ZIP and RAR attachments to distribute SMOKELOADER.
On May 21, 2024, CERT-UA issued a new heads-up based on the observed significant surge in offensive activity linked to UAC-0006. Hackers have conducted at least two campaigns to distribute the SMOKELOADER malware displaying behavioral patterns similar to those observed in the group’s previous campaigns. The latest offensive operations involve emails containing ZIP archives with images that include executable files along with Microsoft Access files with macros for PowerShell command execution, download, and capable of running other executable files.
After the successful initial access stage, adversaries download the weaponized malware on the infected machines, including TALESHOT and RMS. Currently, the botnet consists of several hundred impacted computers. CERT-UA assumes there might be an increase in fraudulent operations involving remote banking systems in the near future.
Defenders strongly recommend promptly enhancing the security of accountants’ automated workstations and ensuring the implementation of required policies and protection mechanisms to eliminate the risks of infections.
Detect UAC-0006 Attacks Targeting Ukraine
The significant spike in cyber attacks attributed to the UAC-0006 hacking collective exploiting the phishing attack vector requires ultra-responsiveness from defenders. The latest campaigns reported by CERT-UA unveil the group’s ongoing efforts to distribute SMOKELOADER malware, a consistent element in its offensive toolkit. SOC Prime Platform delivers curated and verified detection algorithms to enable defenders to preempt attacks linked to the UAC-0006 adversary activity covered in the latest CERT-UA alert. Hit the Explore Detections button to instantly drill down to the list of relevant detections aligned with the MITRE ATT&CK® framework v14.1 and compatible with industry-leading SIEM, EDR, and Data Lake languages.
Security engineers can also take advantage of the comprehensive collection of SOC content for UAC-0006 attack detection filtered accordingly. Follow this link to reach the dedicated detection stack available in the SOC Prime Platform and contribute to your organization’s proactive defense.
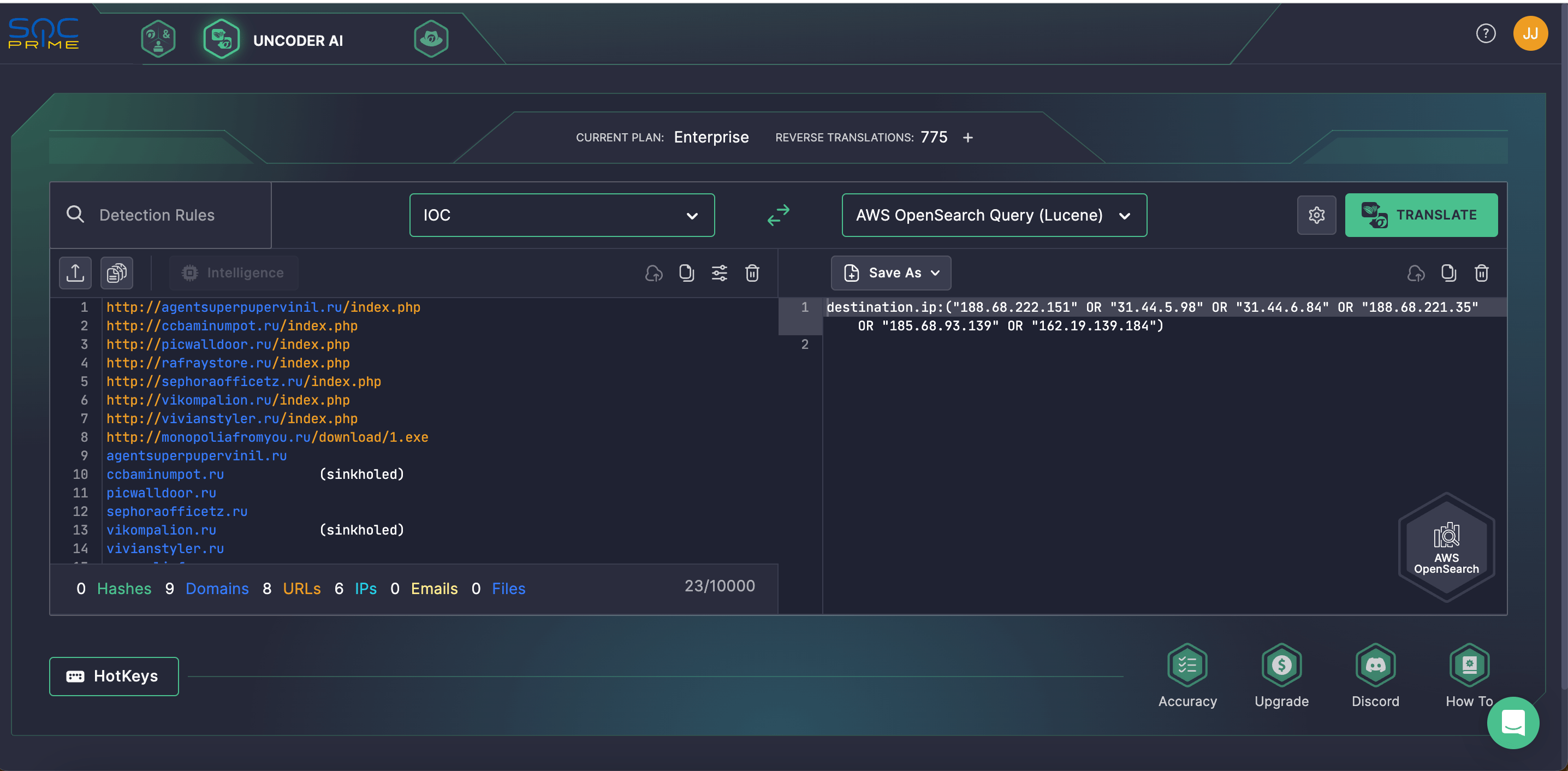
Equip your team with Uncoder AI to seamlessly hunt for IOCs related to the UAC-0006 threats provided by CERT-UA and automatically convert them into custom queries compatible with your SIEM or EDR language format.
MITRE ATT&CK Context
Utilizing MITRE ATT&CK offers detailed insights into the context of offensive operations and TTPs linked to UAC-0006. Check out the table below to view the comprehensive list of specific Sigma rules that correspond to the relevant ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment (T1566.001) Execution User Execution: Malicious File (T1204.002) Scheduled Task / Job: Scheduled Task (T1053.005) Command and Scripting Interpreter: PowerShell (T1059.001) Command and Scripting Interpreter: Windows Command Shell (T1059.003) Persistence Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) Defense Evasion Masquerading (T1036) Masquerading: Double File Extension (T1036.007) BITS Jobs (T1197) Impair Defenses: Disable or Modify System Firewall (T1562.004) Subvert Trust Controls: Mark-of-the-Web Bypass (T1553.005) Command and Control Ingress Tool Transfer (T1105)




