SOC Prime Platform Now Supports the MITRE ATT&CK® Framework v14.1

MITRE ATT&CK acts as a periodic table to categorize and track the methods employed by attackers and enables defenders to profile, identify, and compare threat actors and prioritize threat detection goals. Leveraging ATT&CK, cyber defenders are equipped with a single framework they can rely on to retrospectively document common techniques employed in cyber attacks.
SOC Prime has recently become the MITRE ATT&CK® Benefactor, supporting the evolution of the industry-leading knowledge base to empower research into emerging threats and promote knowledge sharing on a global scale.
In October 2023, MITRE introduced the major framework release v14, introducing enhanced detection guidance for multiple adversary techniques and expanding scope on Enterprise and Mobile, ICS (industrial control systems) assets, and mobile structured detections for more granular insights into adversary TTPs. The ATT&CK v14 provides enhanced Lateral Movement metrics enriched with 75+ BZAR-based analytics, enabling defenders to gain advanced capabilities to identify stealthy movements within the organization’s network in a timely manner and proactively defend against sophisticated APT attacks. BZAR, which stands for Bro/Zeek ATT&CK-based Analytics and Reporting, comprises scripts and tools tailored for the Bro/Zeek Network Security Monitor. Its purpose is to identify offensive activity aligned with the MITRE ATT&CK framework. Moreover, v14 has also introduced a refined relationship between detections, data sources, and mitigations to facilitate an even more seamless and practical implementation of security measures.
SOC Prime has recently added support for the latest framework v14.1 to continuously stay aligned with the most recent updates and improvements introduced in the latest ATT&CK release and strengthen detection coverage through enhanced defensive measures.
What’s New: SOC Prime Platform Support for MITRE ATT&CK v14.1
Through the application of the MITRE ATT&CK, businesses can align detected adversary behaviors with particular techniques, pinpoint security vulnerabilities, prioritize defense strategies, create CTI, and communicate information within the global cybersecurity community. Acting as a foundation for the development of specific threat models and methodologies, the ATT&CK knowledge base fosters collaboration among industry peers, a shared understanding of adversary TTPs, and the exchange of insights on emerging threats and successful defense tactics.
The current MITRE ATT&CK version of SOC Prime Platform fully supports 14 MITRE ATT&CK tactics, 201 techniques, and 424 sub-techniques updated according to the latest MITRE release v14.1.
SOC Prime solutions reflect the corresponding framework updates, including the Sigma Rules Search engine, the MITRE ATT&CK Coverage, Leaderboards, and Dashboard in the SOC Prime Platform, along with content mapping updates to ensure the detection algorithms address relevant tactics, techniques, and sub-techniques as per the ATT&CK v14.1.
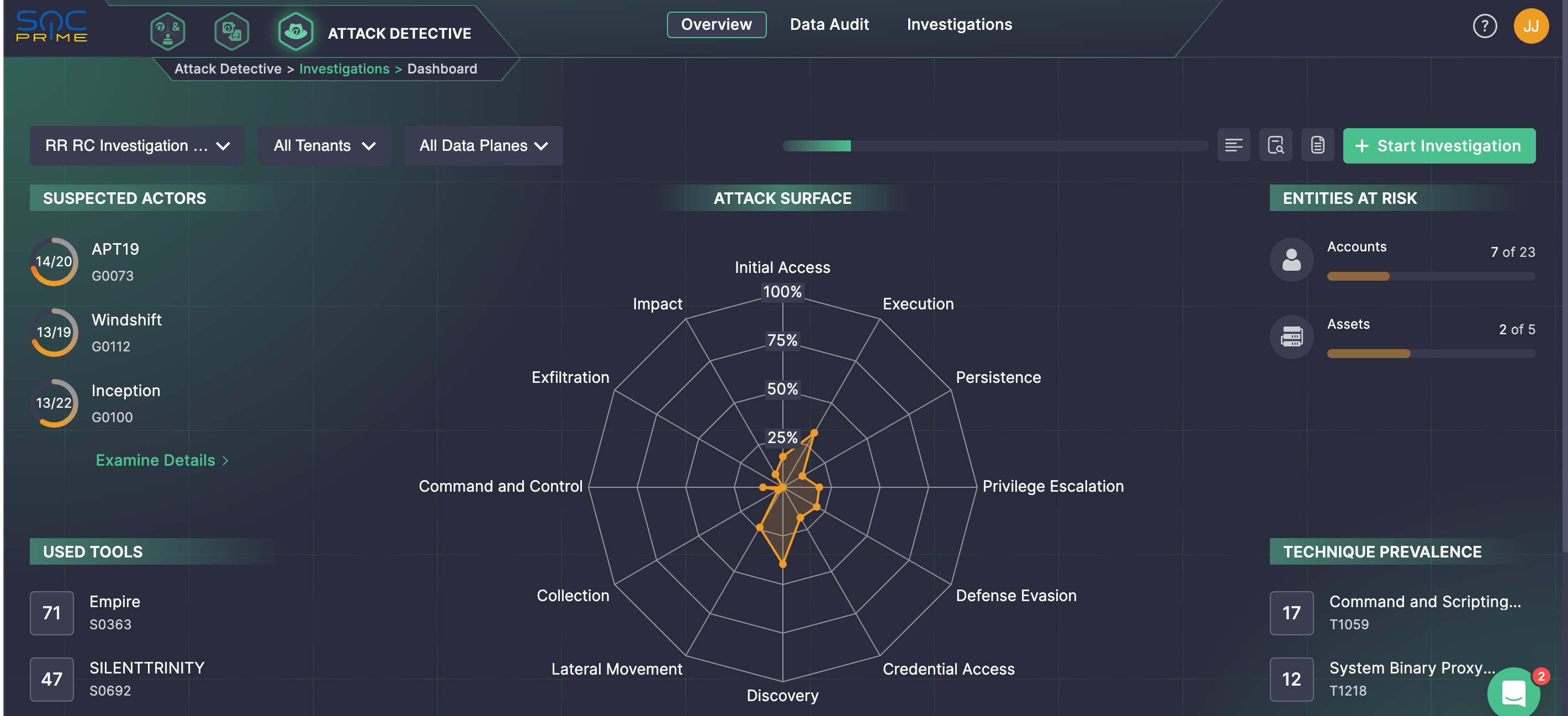
Attack Detective: Unlocking Threat-Informed Defense Backed by MITRE ATT&CK
Global industry collaboration has started with the contribution to MITRE ATT&CK to unlock threat-informed defense, a community-based and proactive approach to cybersecurity that involves a deep understanding of adversary tradecraft and technology to protect against, detect, and mitigate cyber attacks according to MITRE Engenuity. SOC Prime Platform curates the industry-first SaaS for active threat-informed defense that enables automated detection stack validation and threat hunting backed by vendor-agnostic detection algorithms from the Threat Detection Marketplace and MITRE ATT&CK®.
Leveraging the Attack Detective solution, security engineers can validate the entire detection stack in less than 300 seconds with an automatic read-only ATT&CK data audit to find blind spots in the organization’s log source coverage. Attack Detective provides a real-time snapshot of attack coverage using MITRE ATT&CK as a main correlation rule to highlight triggered TTPs and provide a list of prioritized Sigma rules enabling teams to focus on incident investigation rather than analyzing overwhelming volumes of alerts.
Register for SOC Prime Platform to keep up with the latest TTPs used by adversaries in real-world attacks and explore proactive methods to always stay ahead of offensive forces.


