Detect SmokeLoader Malware: UAC-0006 Strikes Again to Target Ukraine in a Series of Phishing Attacks
Table of contents:
Hot on the heels of the massive phishing attacks launched by UAC-0006 at the beginning of May 2023, CERT-UA warns cyber defenders of a new wave of cyber attacks resulting in SmokeLoader infections. The latest investigation indicates that adversaries increasingly spread phishing emails with financial subject lures and use ZIP/RAR attachments to drop malicious samples on the targeted instances.
Analyzing UAC-0006 Phishing Attacks Aimed at SmokeLoader Distribution
On May 29, 2023, CERT-UA experts released a new CERT-UA#6757 alert detailing the ongoing phishing campaign launched by UAC-0006 hacking collective. By leveraging the malicious attachments with a dedicated JavaScript downloader, adversaries deliver SmokeLoader to targeted systems. Specifically, hackers leverage either ZIP or RAR archives containing malicious HTML or VHDX files. In case extracted, the archive triggers JavaScript code, which in turn downloads and launches the executable file that later drops SmokeLoader to spread the infection further.
CERT-UA team identifies a number of prominent updates in the UAC-0006 attack kill chain compared to the similar phishing campaign launched earlier in May 2023. Specifically, experts observe that attackers tend to use multiple infection chains. Also, the SmokeLoader sample used in the latest campaign contains 26 URL links to a server controlling a botnet. Additionally, CERT-UA identified a malicious Cobalt Strike Beacon applied during the intrusions which indicates that UAC-0006 aims to expand its toolset.
Detecting the Latest UAC-0006 Adversary Activity
Just a couple of weeks after massive phishing attacks spreading SmokeLoader, UAC-0006 threat actors responsible for earlier intrusions resurfaced to hit once again. Due to the changes in adversary TTPs and the use of multiple infection chains in the latest offensive operation, organizations can be potentially exposed to more serious risks, which requires urgent attention from cyber defenders. SOC Prime has recently released a set of relevant Sigma rules to timely detect the malicious activity of the UAC-0006 group covered in the latest CERT-UA#6757 alert. All detection content is filtered by the custom tags “CERT-UA#6757” or “UAC-0006” according to the corresponding alert and the group IDs, which enables researchers to streamline content search and threat hunting activities.
Press the Explore Detections button to instantly access the entire collection of Sigma rules for UAC-0006 attack detection mapped to MITRE ATT&CK® and automatically convertible to industry-leading SIEM, EDR, and XDR solutions. To explore relevant metadata, ATT&CK links and CTI references along with other cyber threat context are also available at hand.
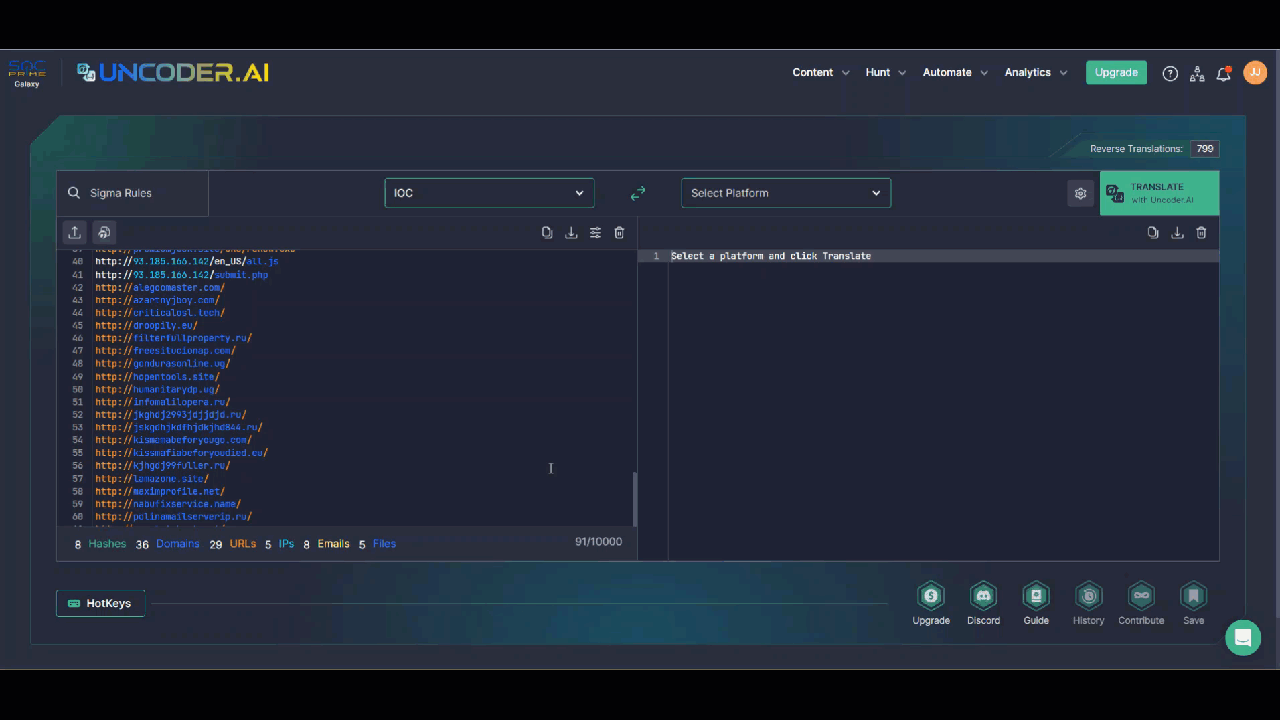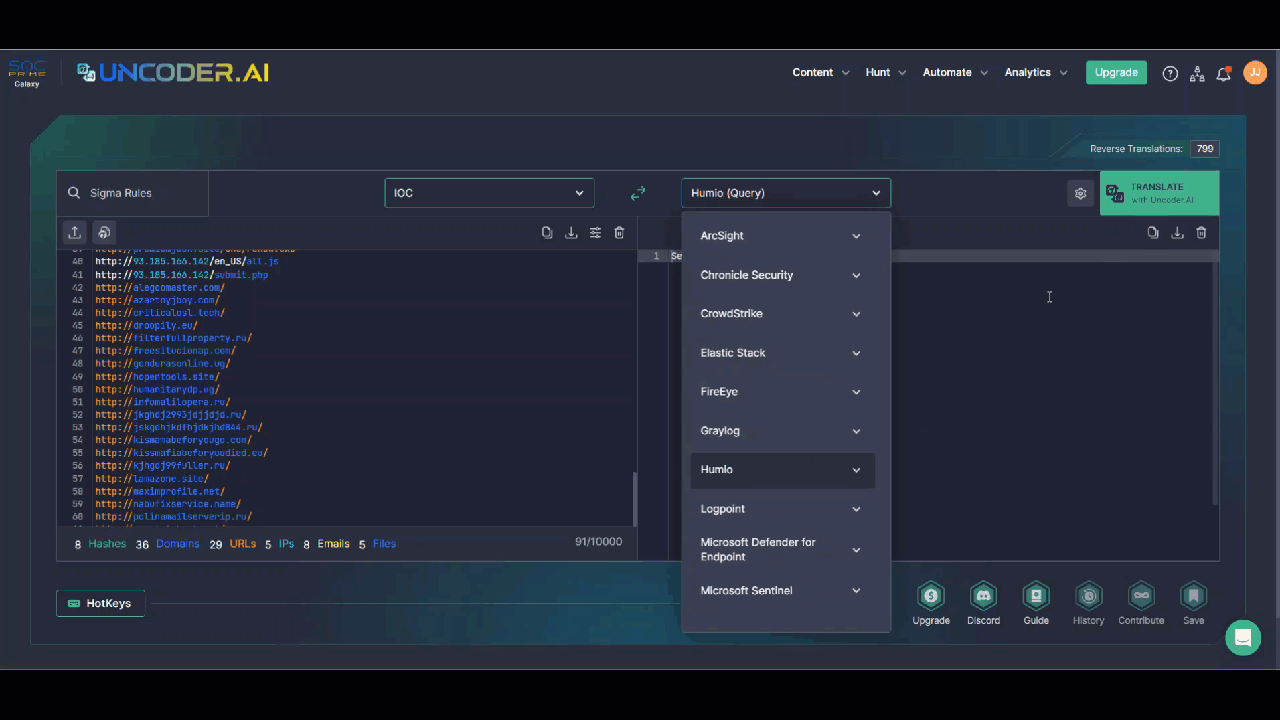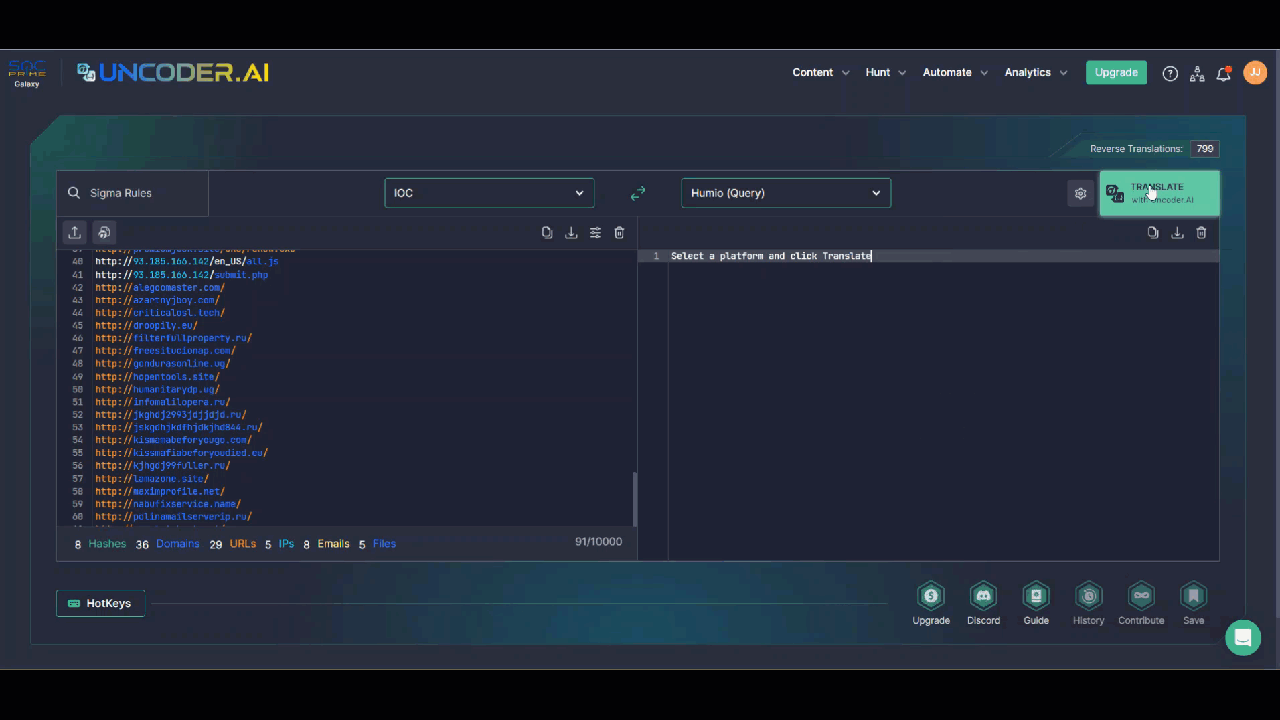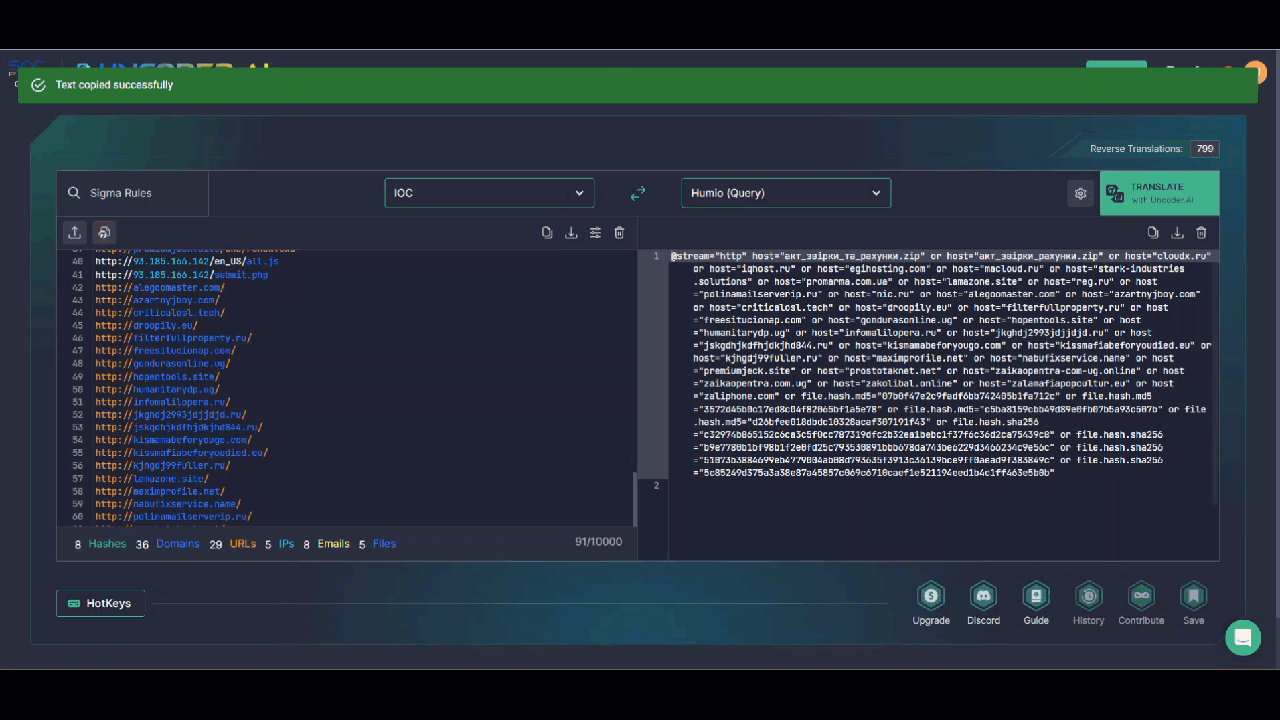
SOC team members are also welcome to hunt for IOCs linked to the UAC-0006 malicious activity leveraging Uncoder AI, an augmented intelligence framework that serves as an ultimate tool for threat hunters and detection engineers and enables converting IOCs to custom IOC queries without limits. Just insert the file, host, or network IOCs provided in the CERT-UA#6757 alert to the tool, select the platform of your choice, apply the query settings customized to your security needs, and be ready to hunt for relevant threats instantly in your SIEM or EDR environment.
MITRE ATT&CK Context
To dive into TTPs leveraged during the most recent attack by the UAC-0006 hacking group spreading SmokeLoader, all the above-mentioned Sigma rules are mapped to ATT&CK and address the corresponding tactics and techniques: