All SOC Prime Team is currently working remotely (hope you do the same) but such conditions didn’t influence our effectiveness and striving to improve Threat Detection Marketplace (TDM) platform.
In this blog we’re thrilled to announce SOC Prime’s 4 new TDM features that come thanks to our 3d party integration with Microsoft Azure Sentinel, which aims to help businesses save their security awareness and reduce implementation time.
Let’s start with the first feature that stands for Integration with sigma integration with Azure Sentinel.
Sigma integration with Azure Sentinel
Uncoder.io, a free SOC Prime’s service and one common language for Cybersecurity will help us to manage that in the most obvious way using Sigma language. With an easy, fast and private UI you can translate the queries from one tool to another without a need to access the SIEM environment and in a matter of just a few seconds.
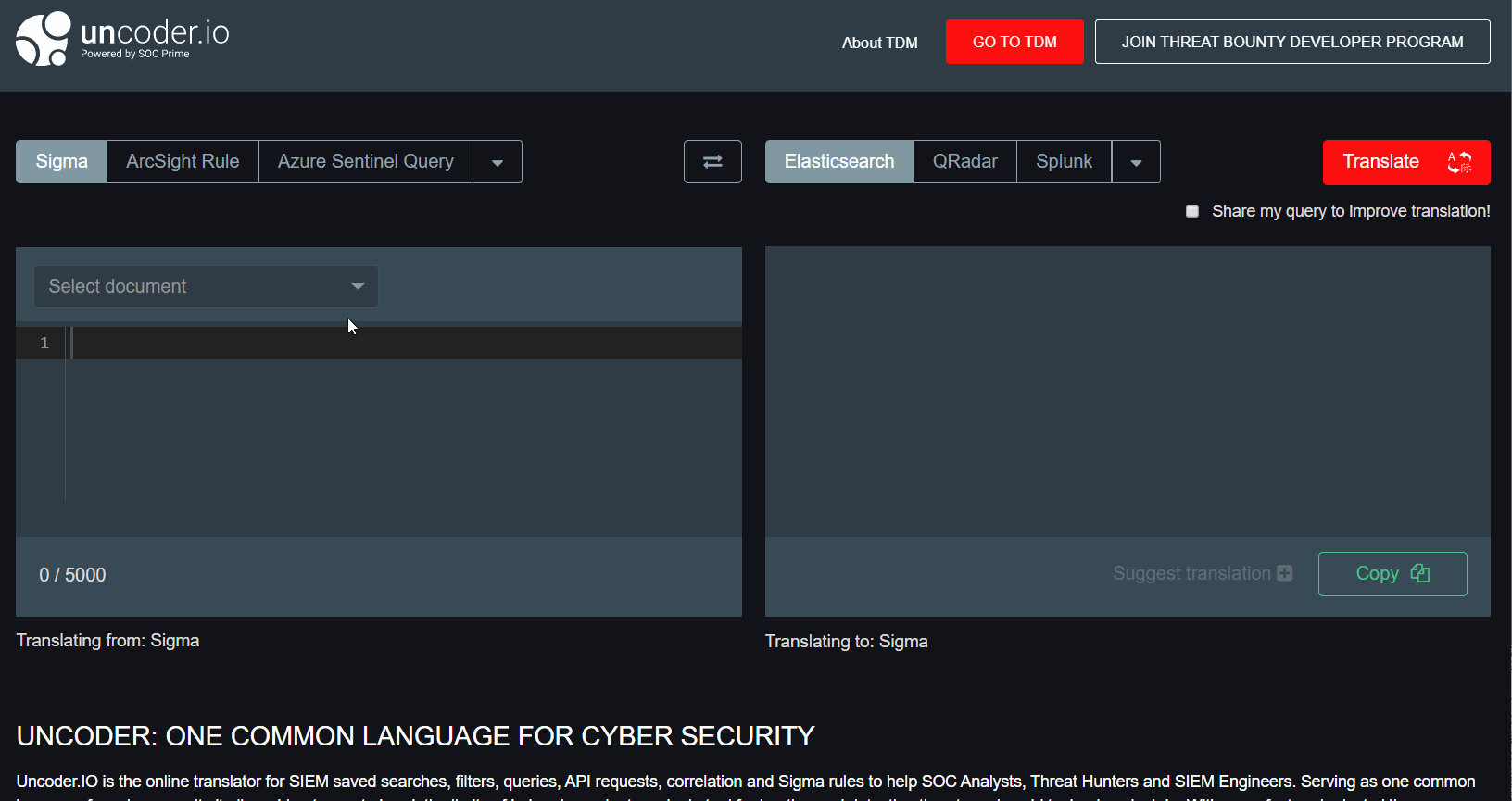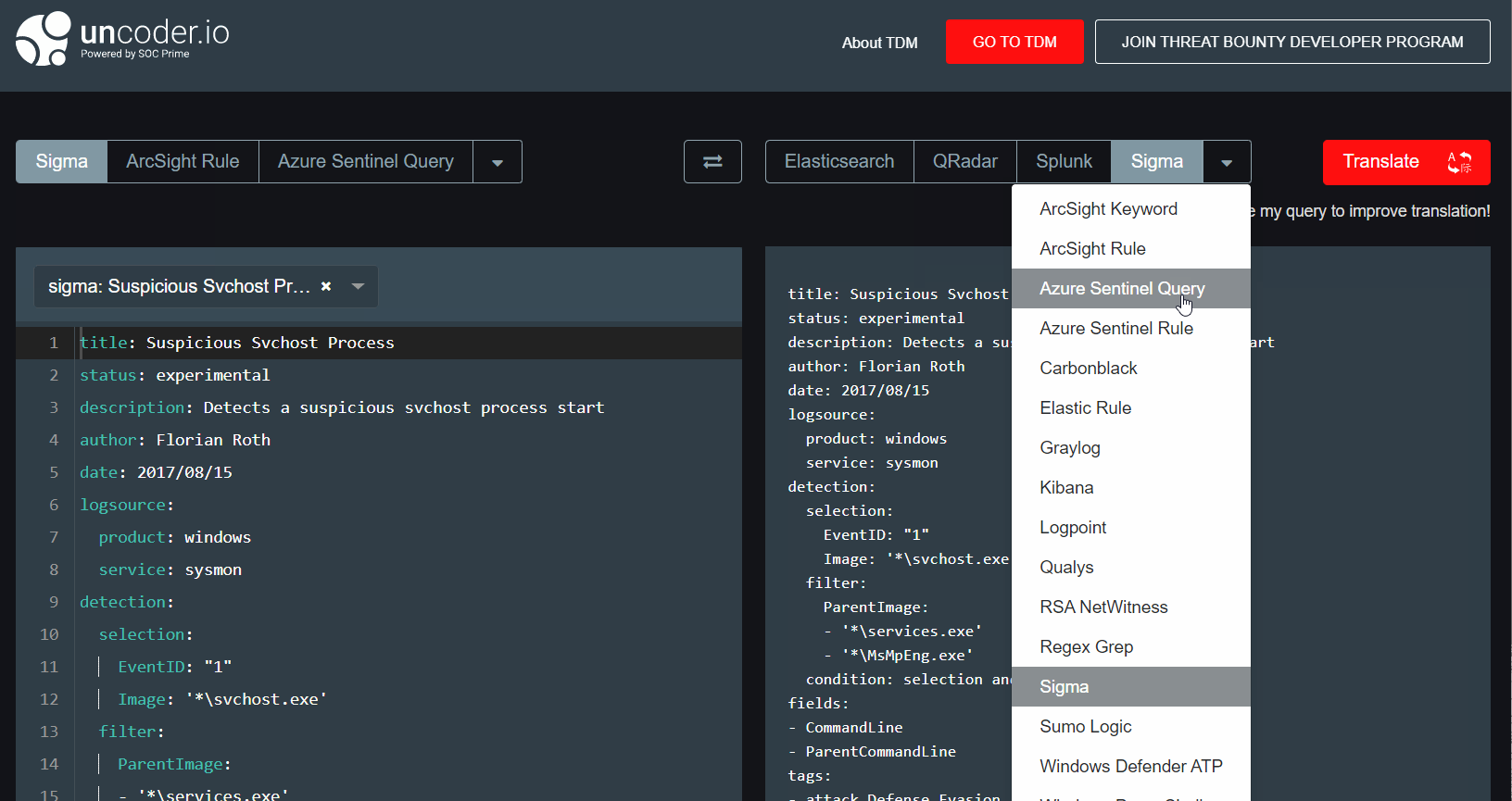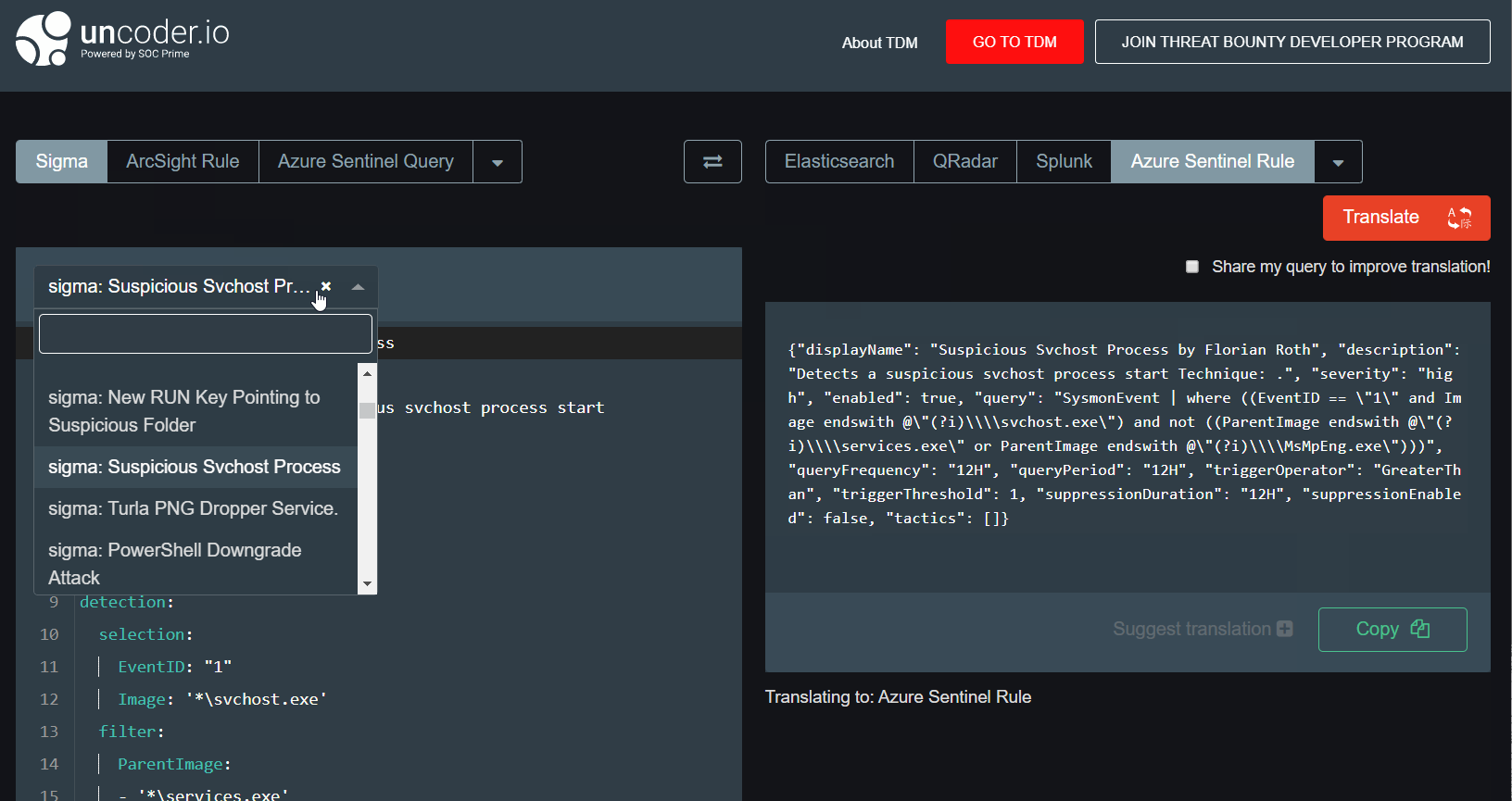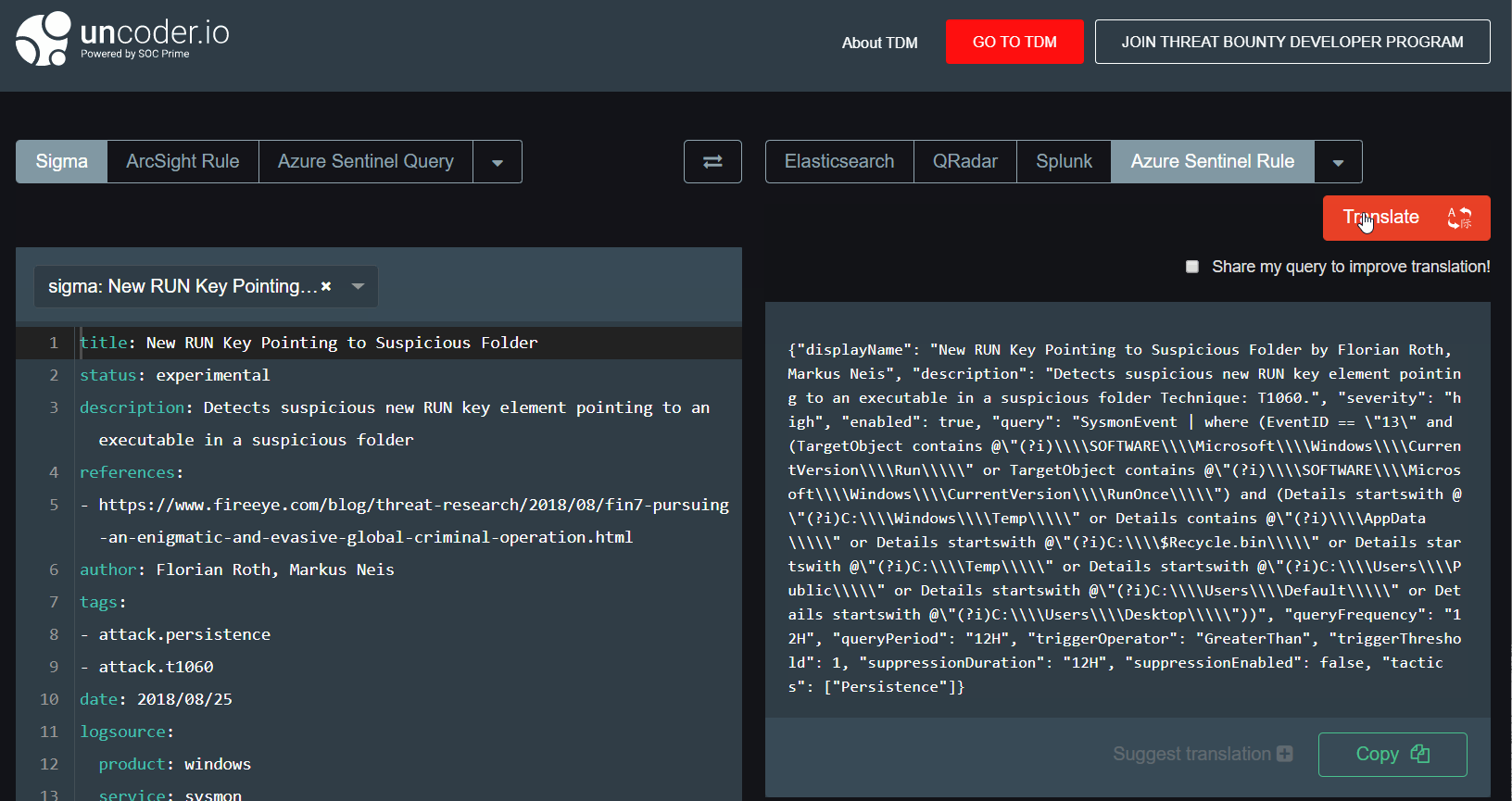
That’s what we can easily do now to convert Sigma rules into functional Azure Sentinel queries & rules.
Easy? We’re pretty sure it’s a nice one feature that will definitely save you some time. Just try it out via Uncoder.io by SOC Prime and let us know what you think 🙂
The second thing we’ve focused on is the automated method of streamlining rules via Azure Sentinel API.
Multi-tenancy hook between TDM and Azure Sentinel API is now available on the TDM.
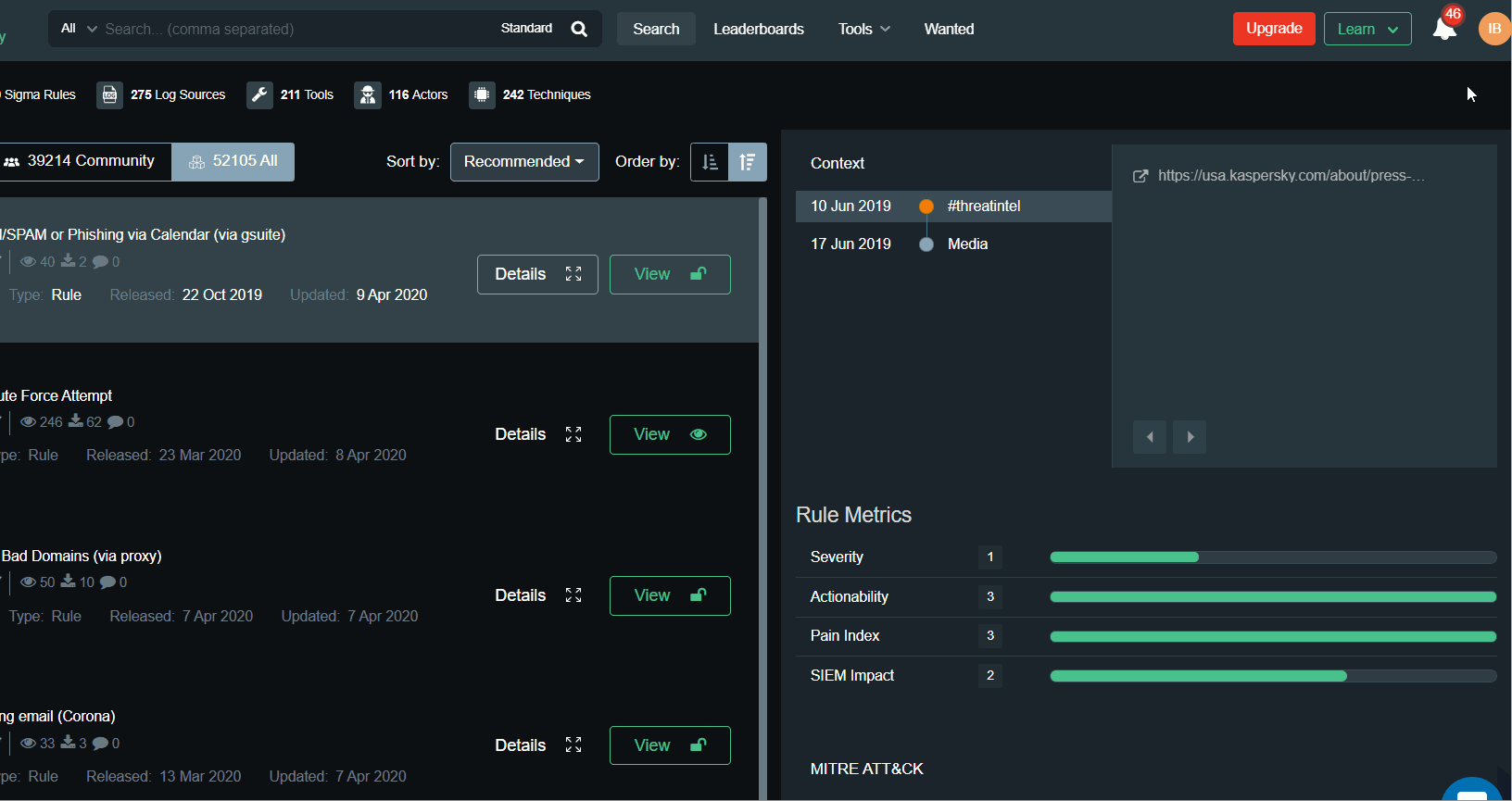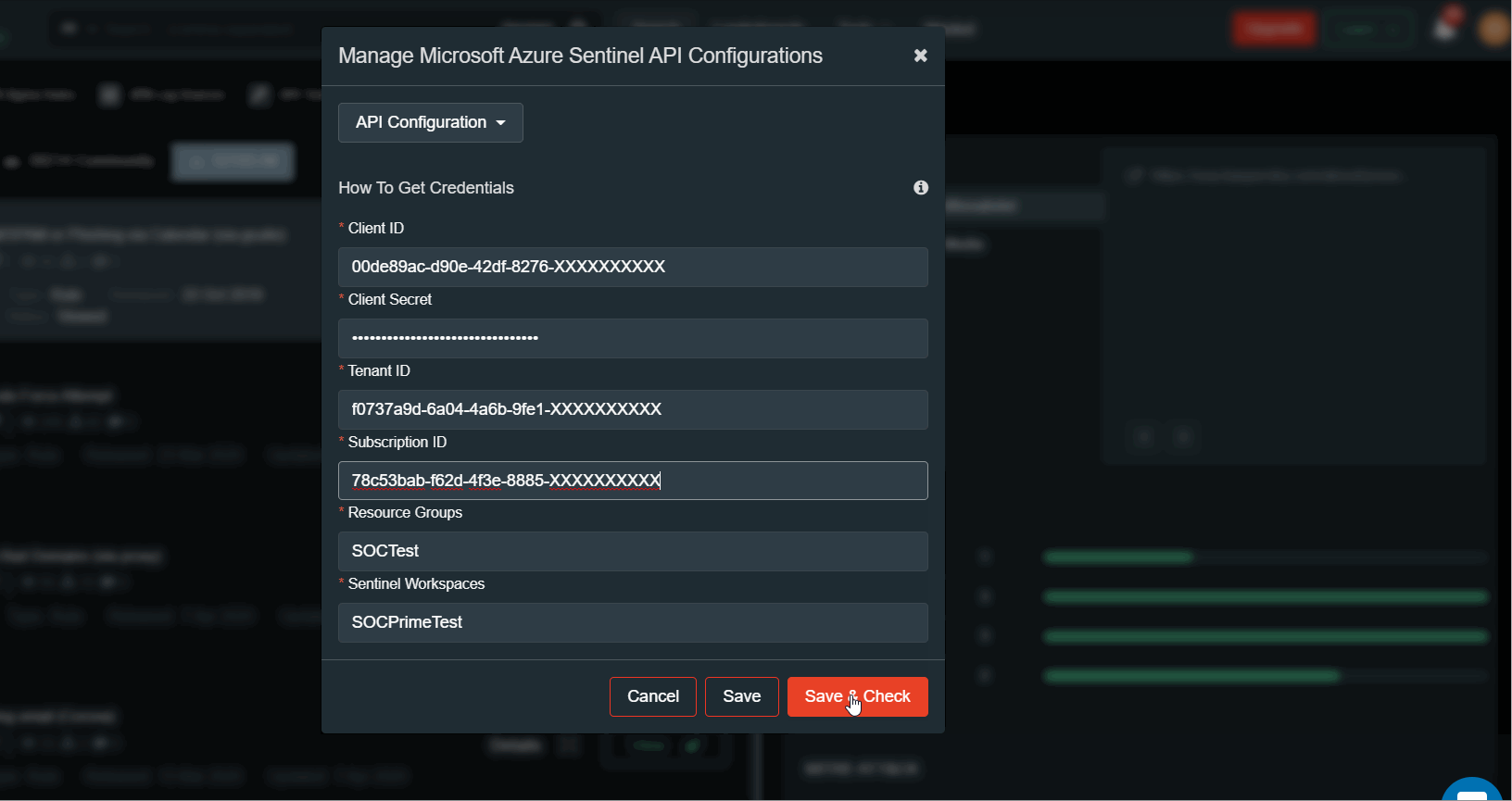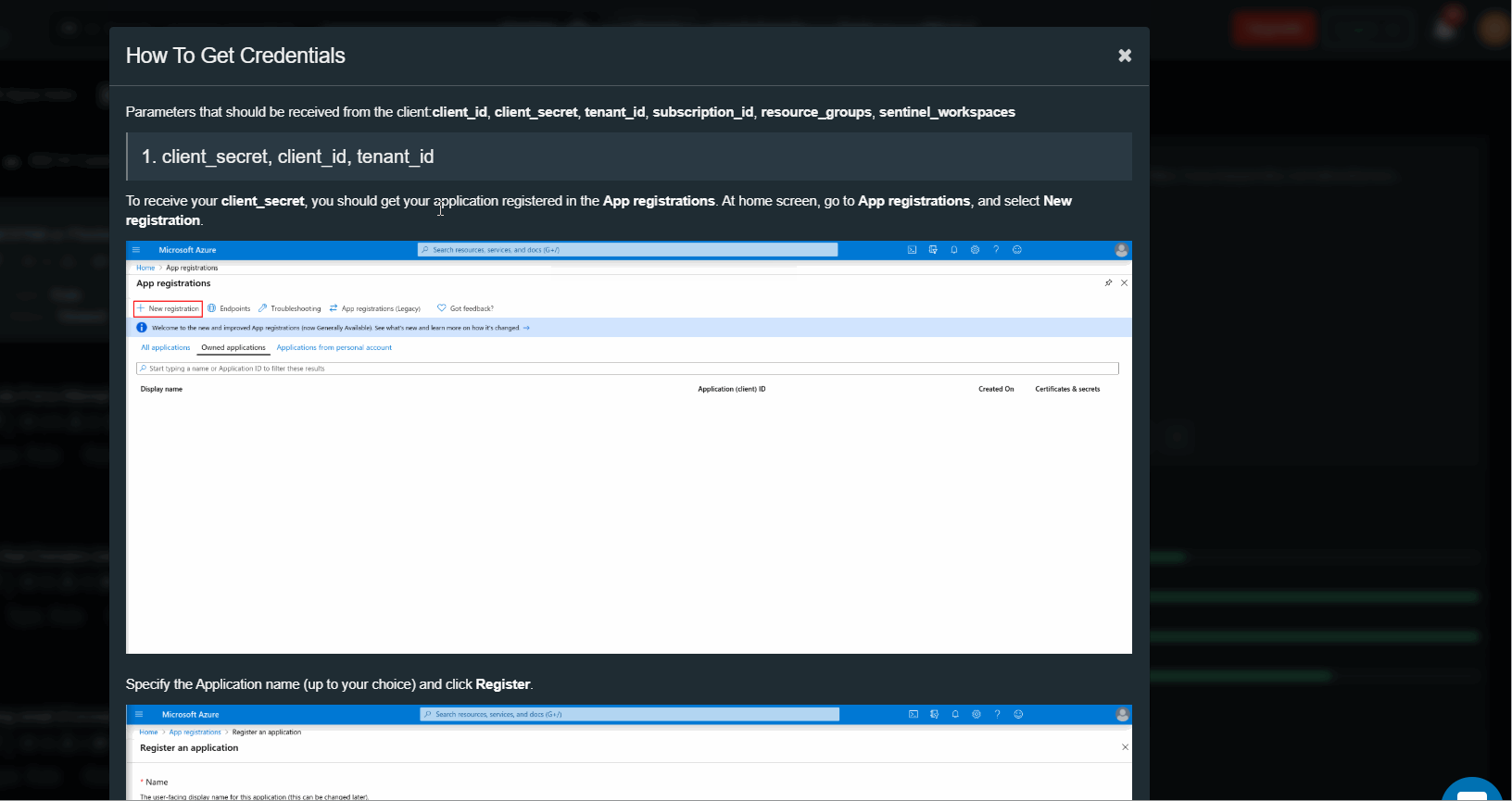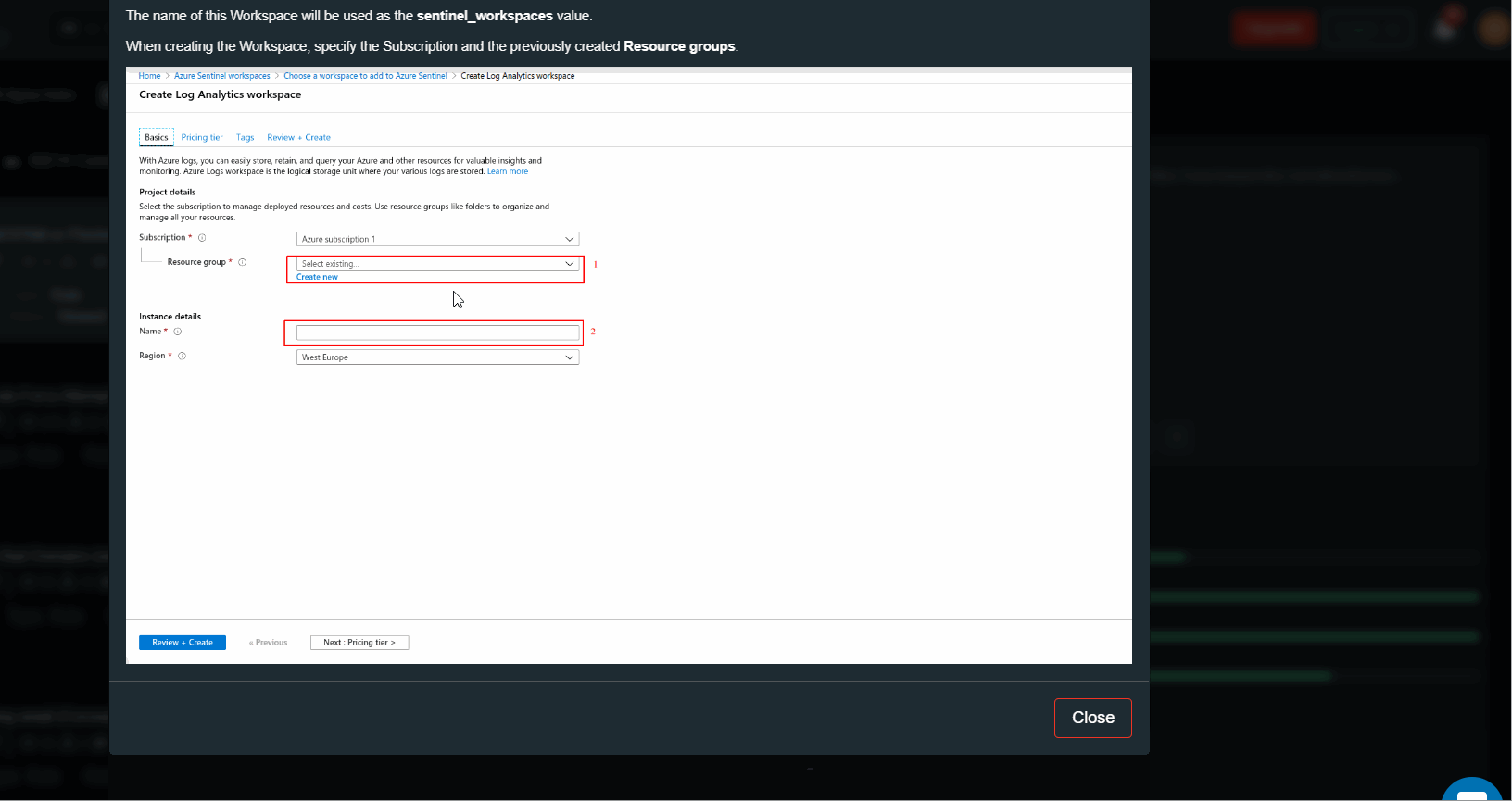
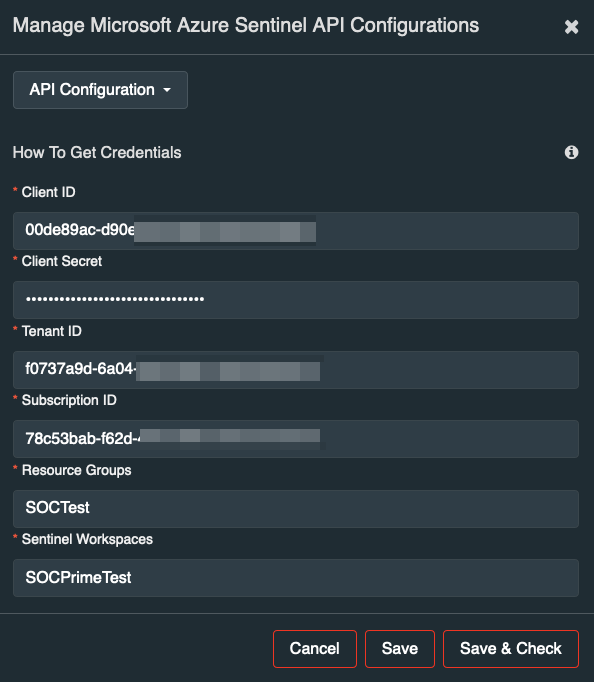
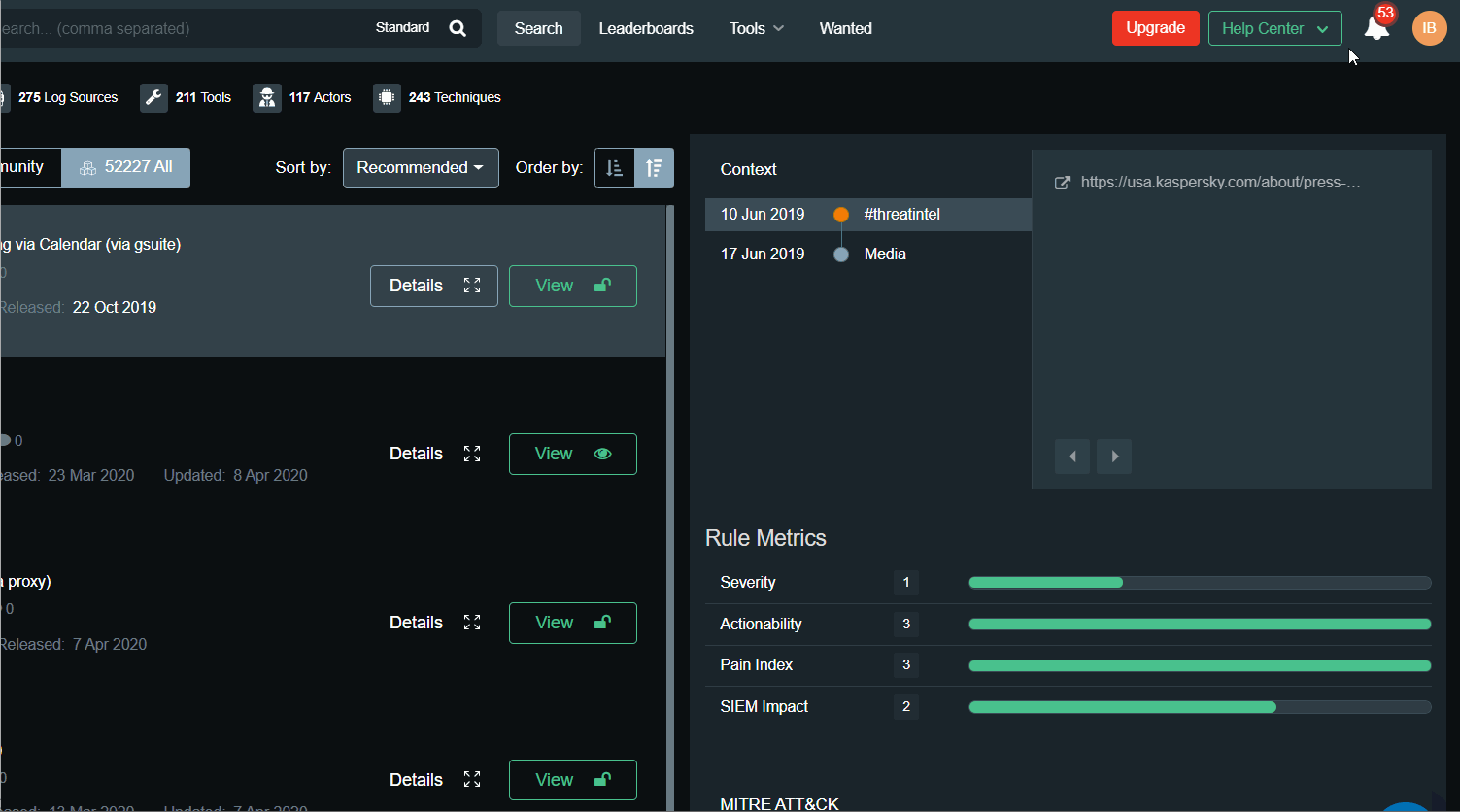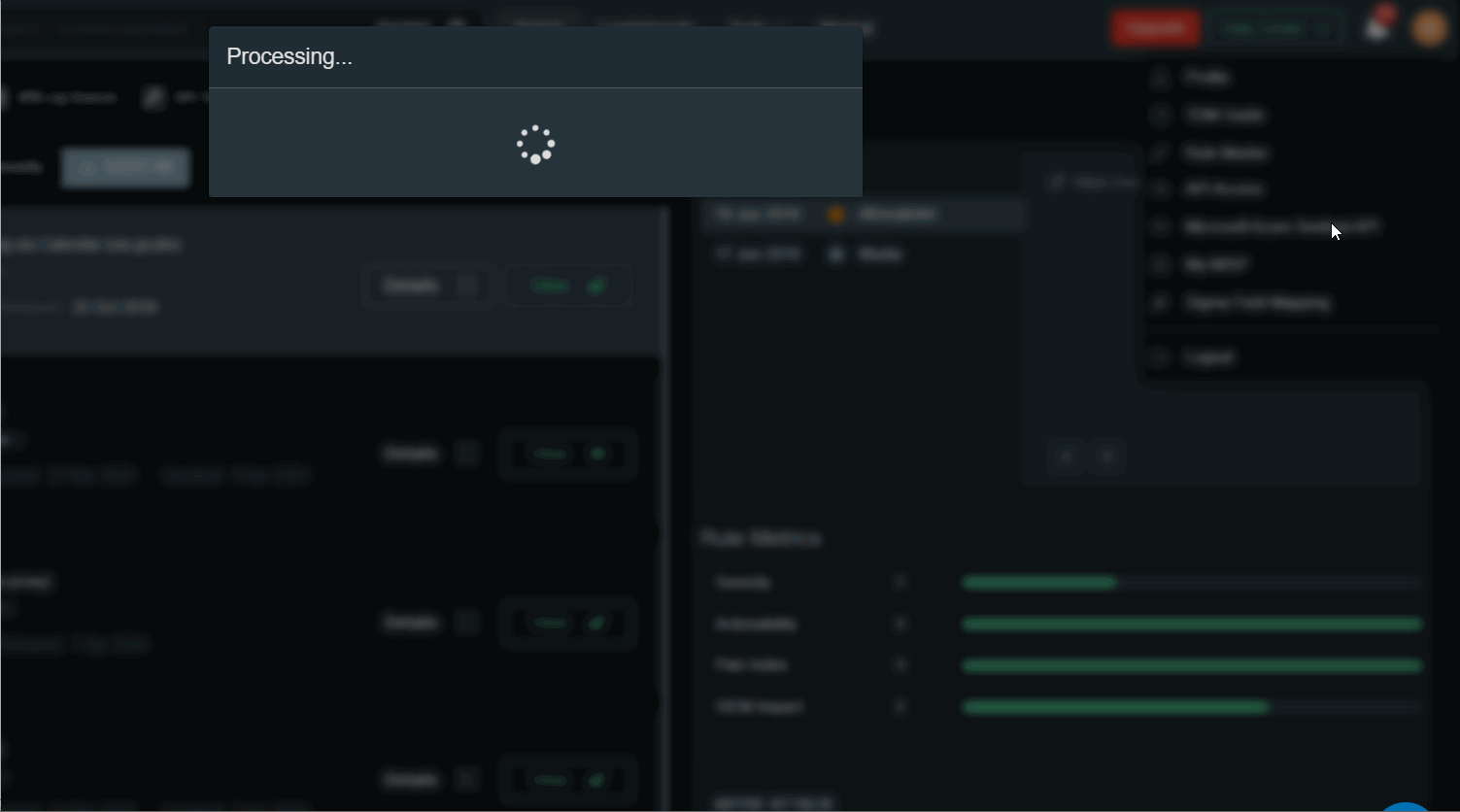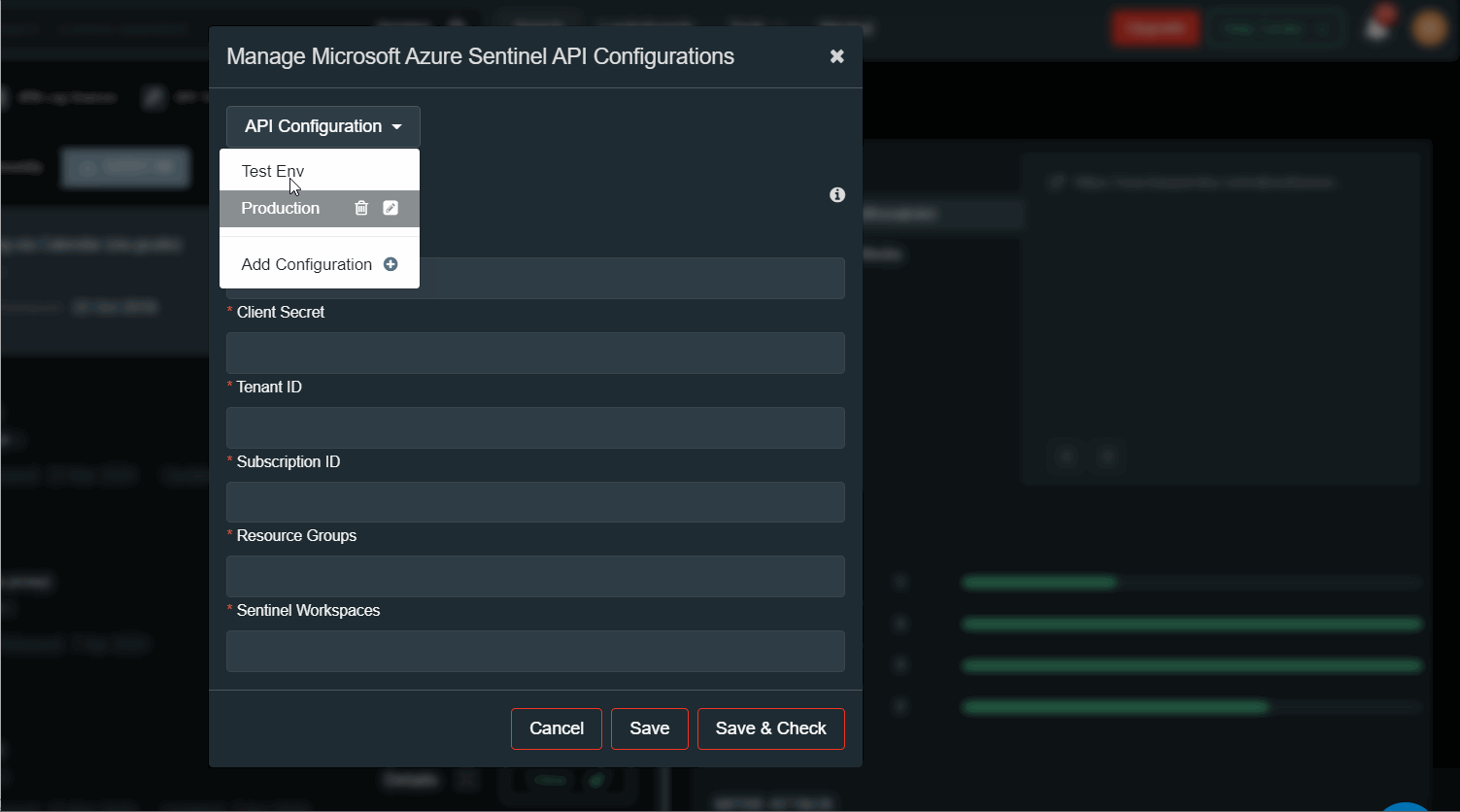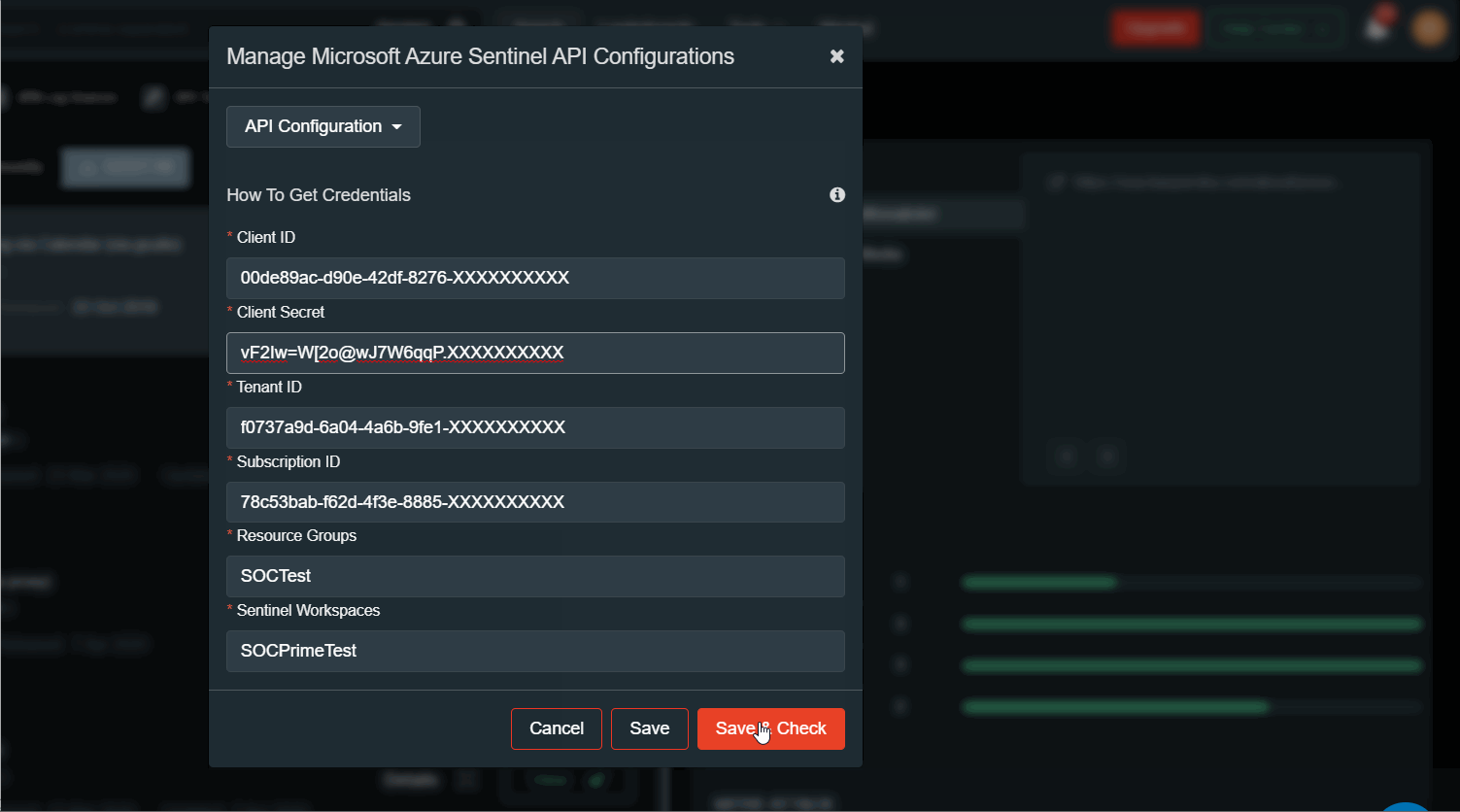
You can now add in the “Microsoft Azure Sentinel API” configuration (available in your TDM profile menu).
When deploying rules choose where exactly you want to deploy them. There is a set of parameters that need to be configured for the Microsoft Azure Sentinel API Configuration:
- Client ID,
- Client Secret,
- Tenant ID,
- Subscription ID,
- Resource Group,
- Sentinel Workspace
Example:
Detailed instructions on how to setup Azure Sentinel API app are in the section ‘How to Get Credentials”, press (i) button.
To add another Azure Sentinel tenant press ‘API Configuration’ button. You can add new configuration, edit or delete existing configuration. For example, a test and production environment.
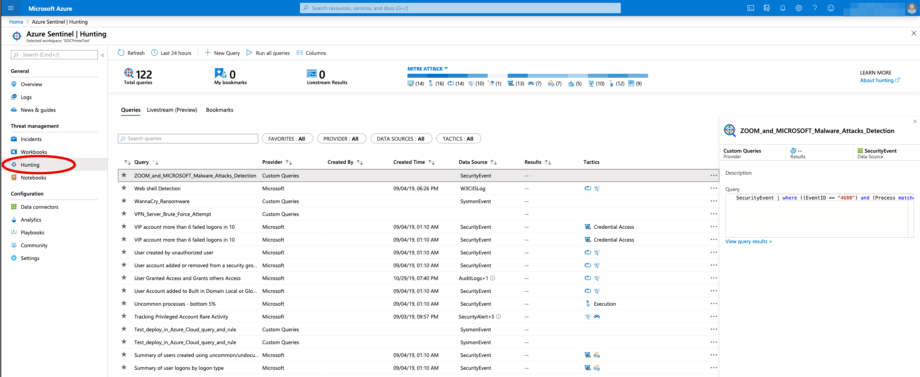
SOC Prime TDM Integration with Azure Sentinel Hunting search queries
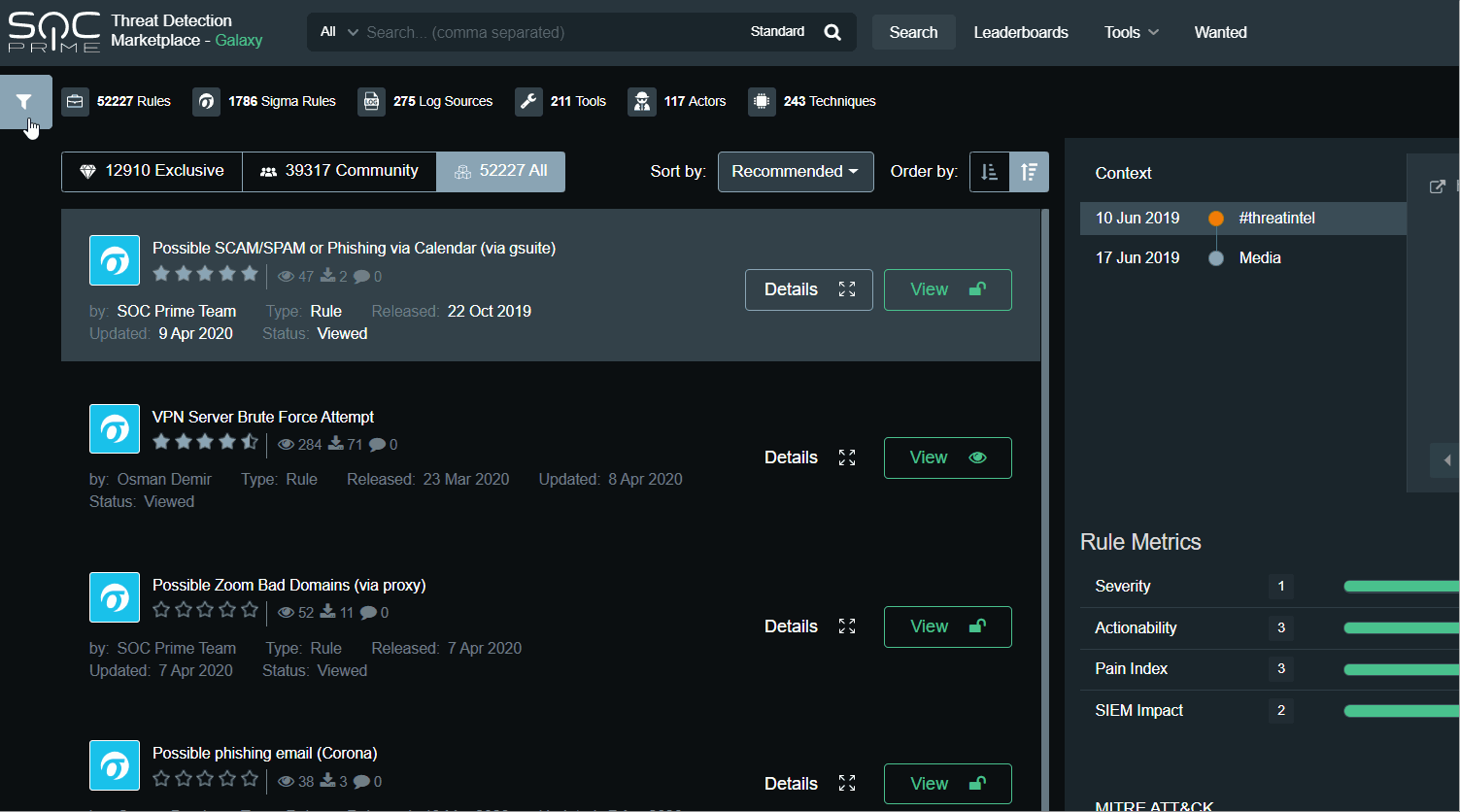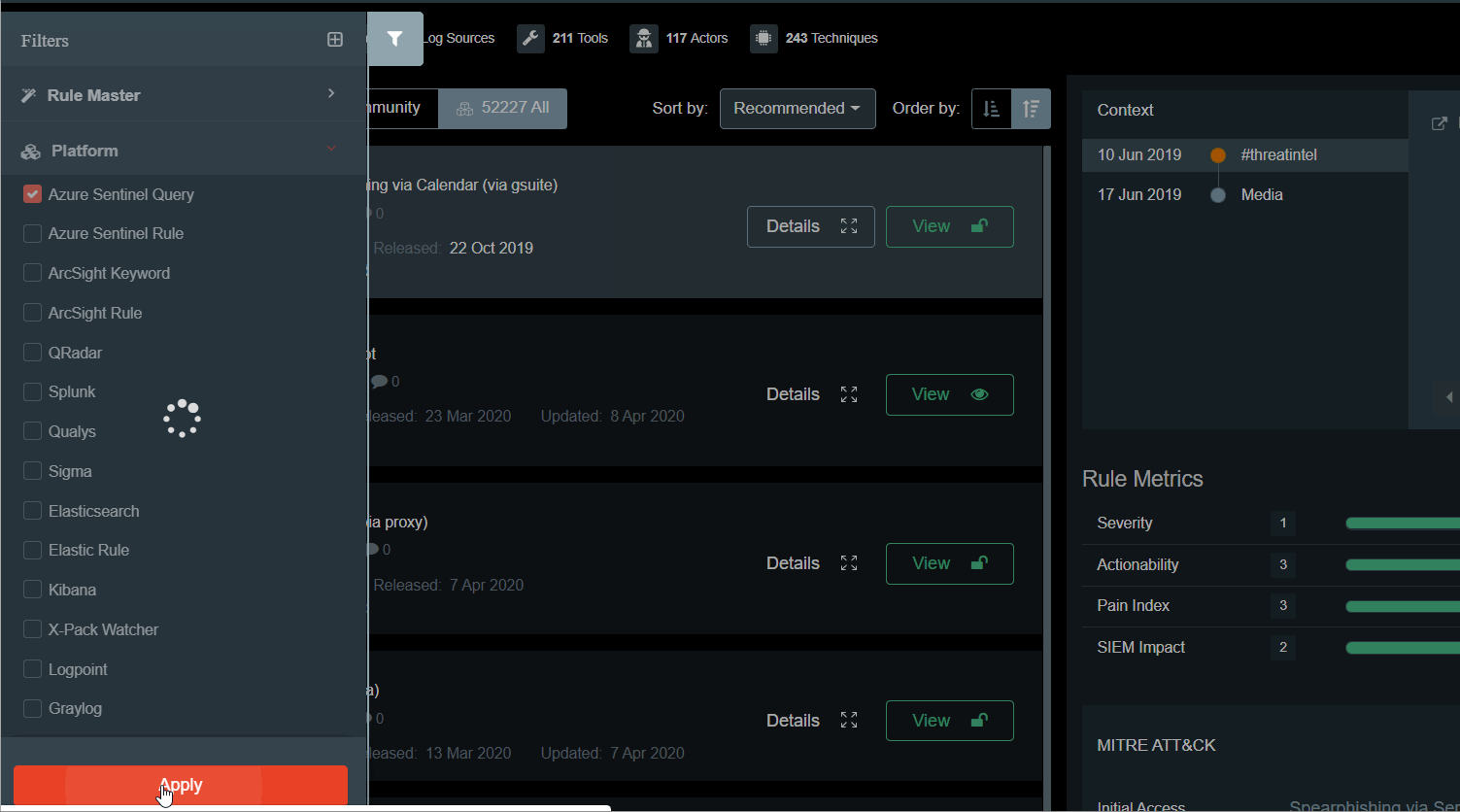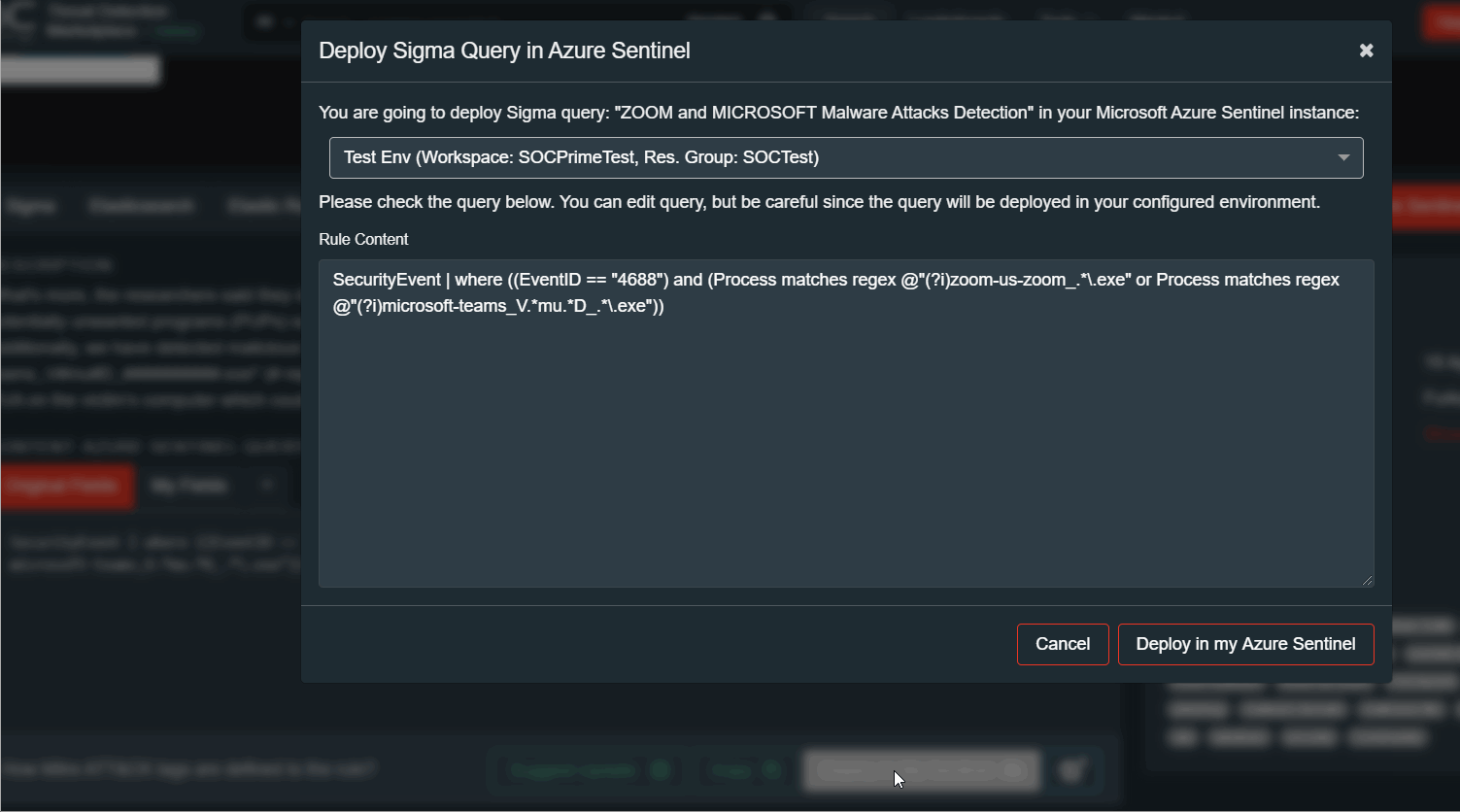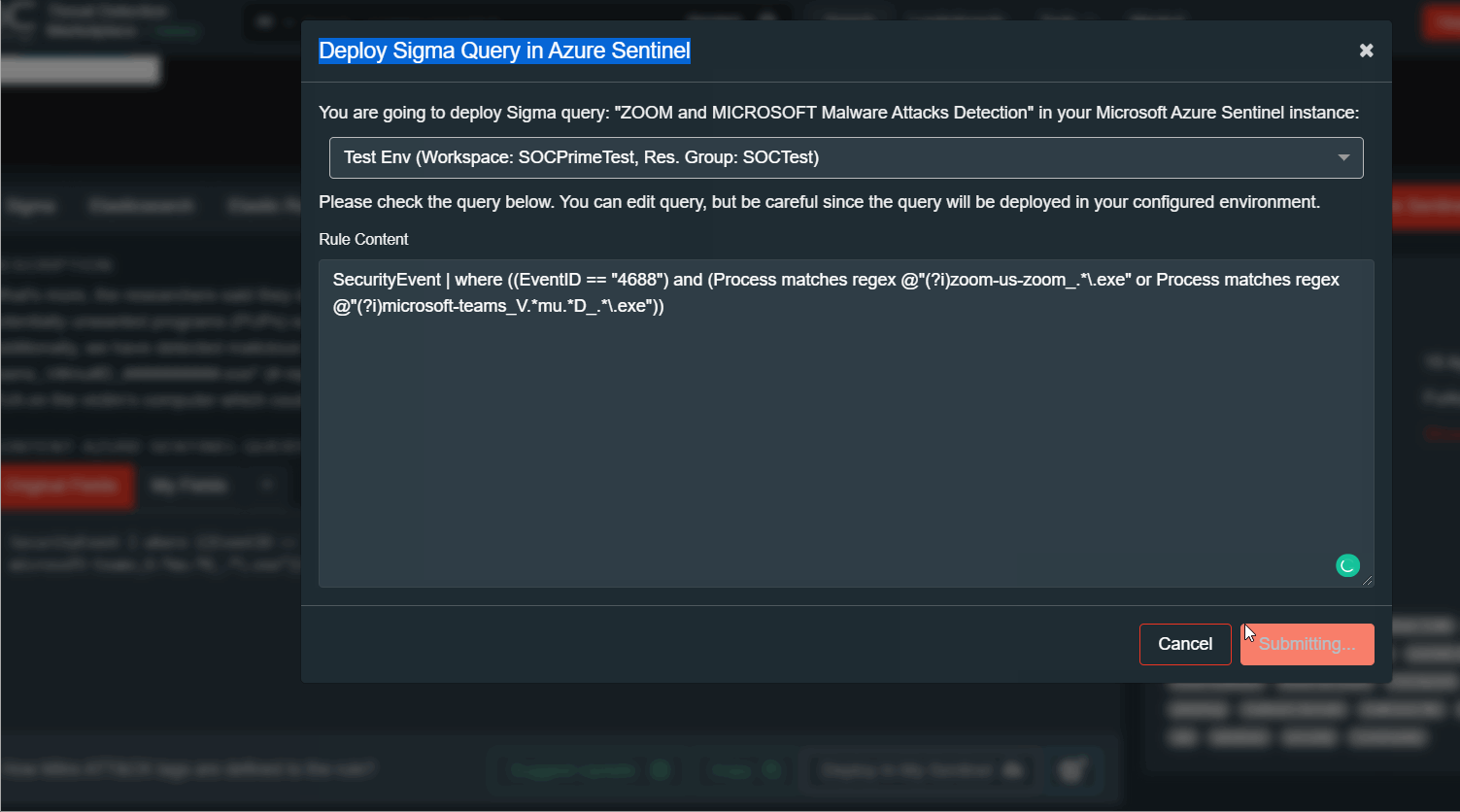
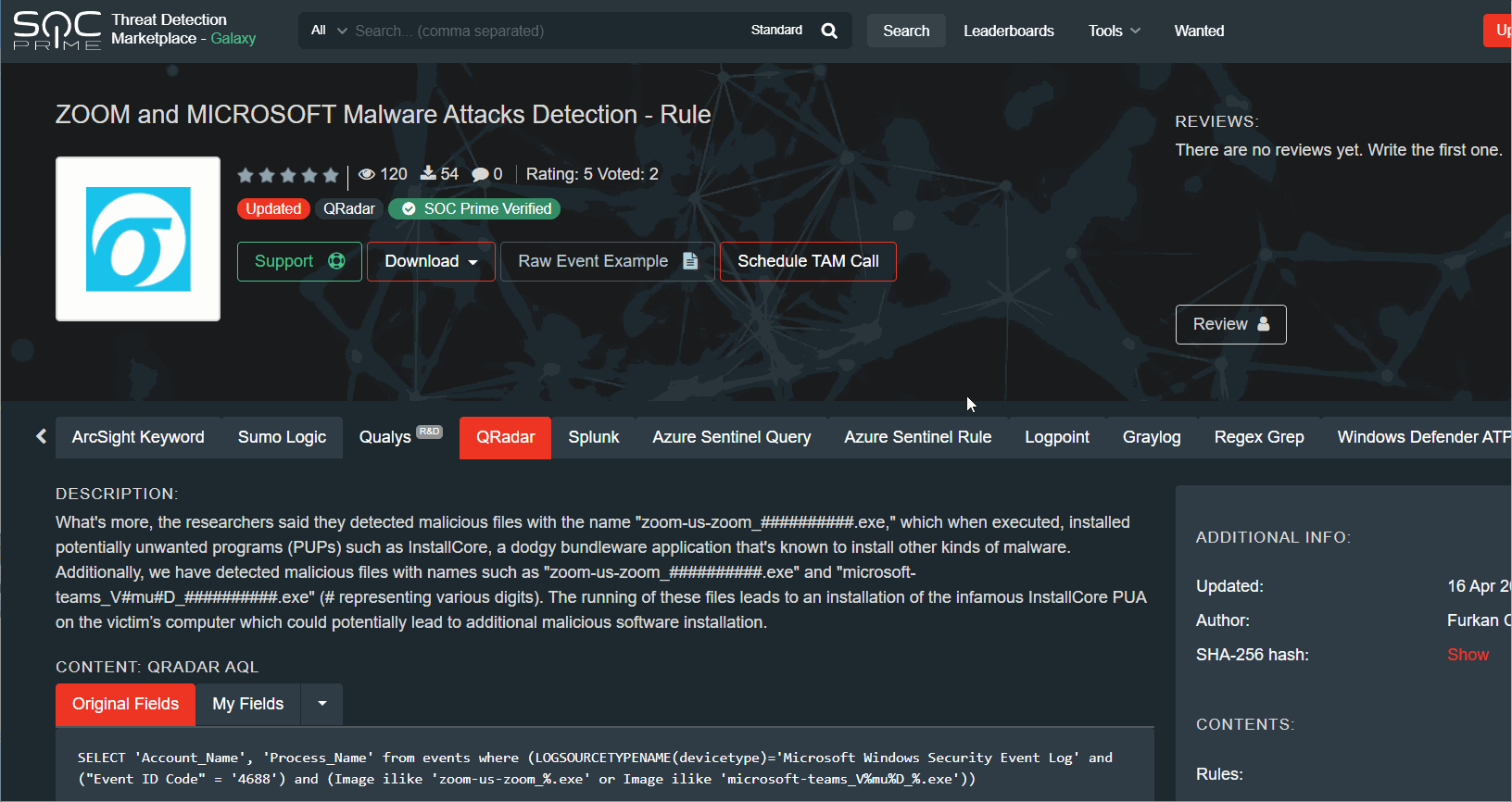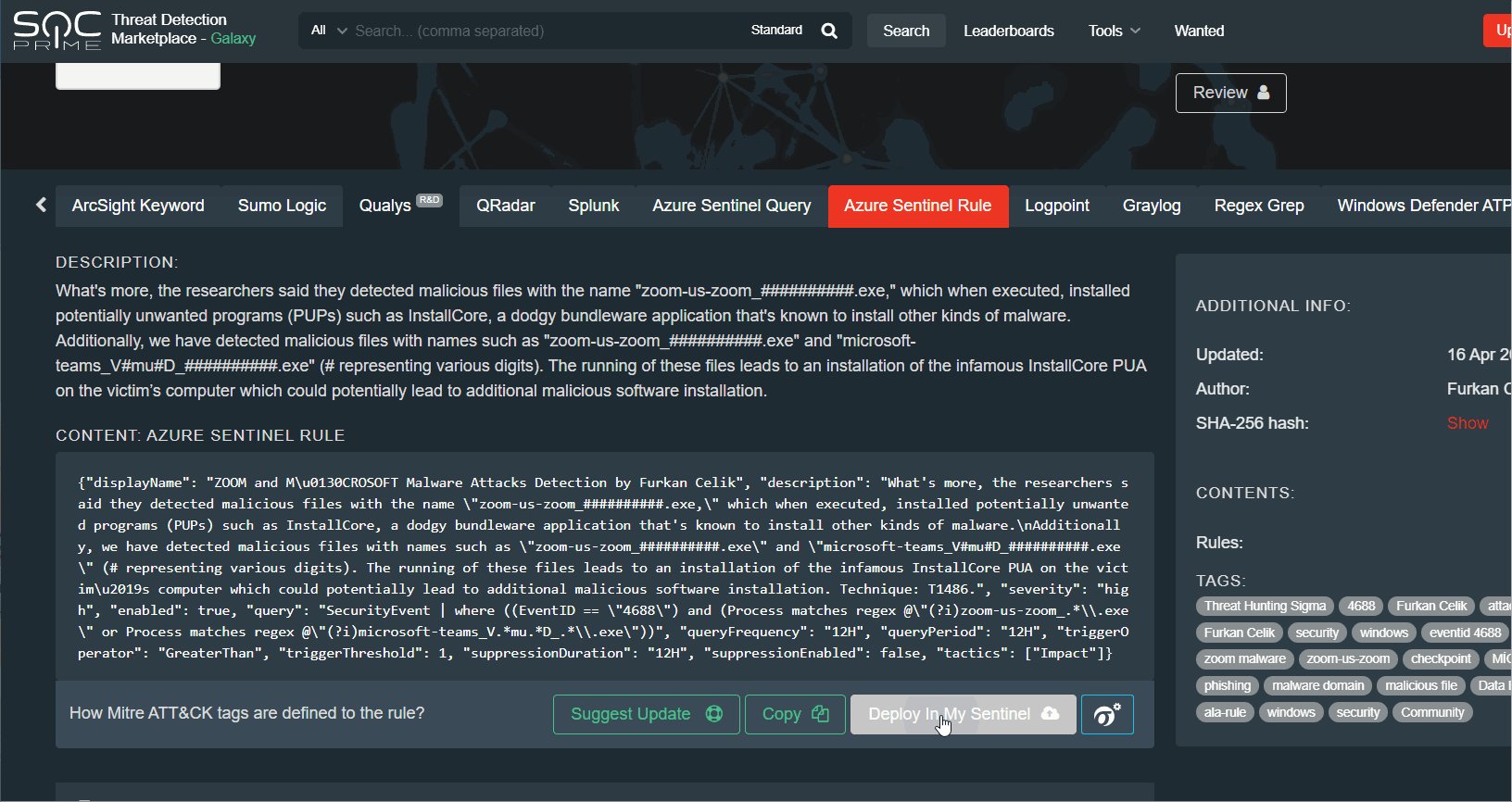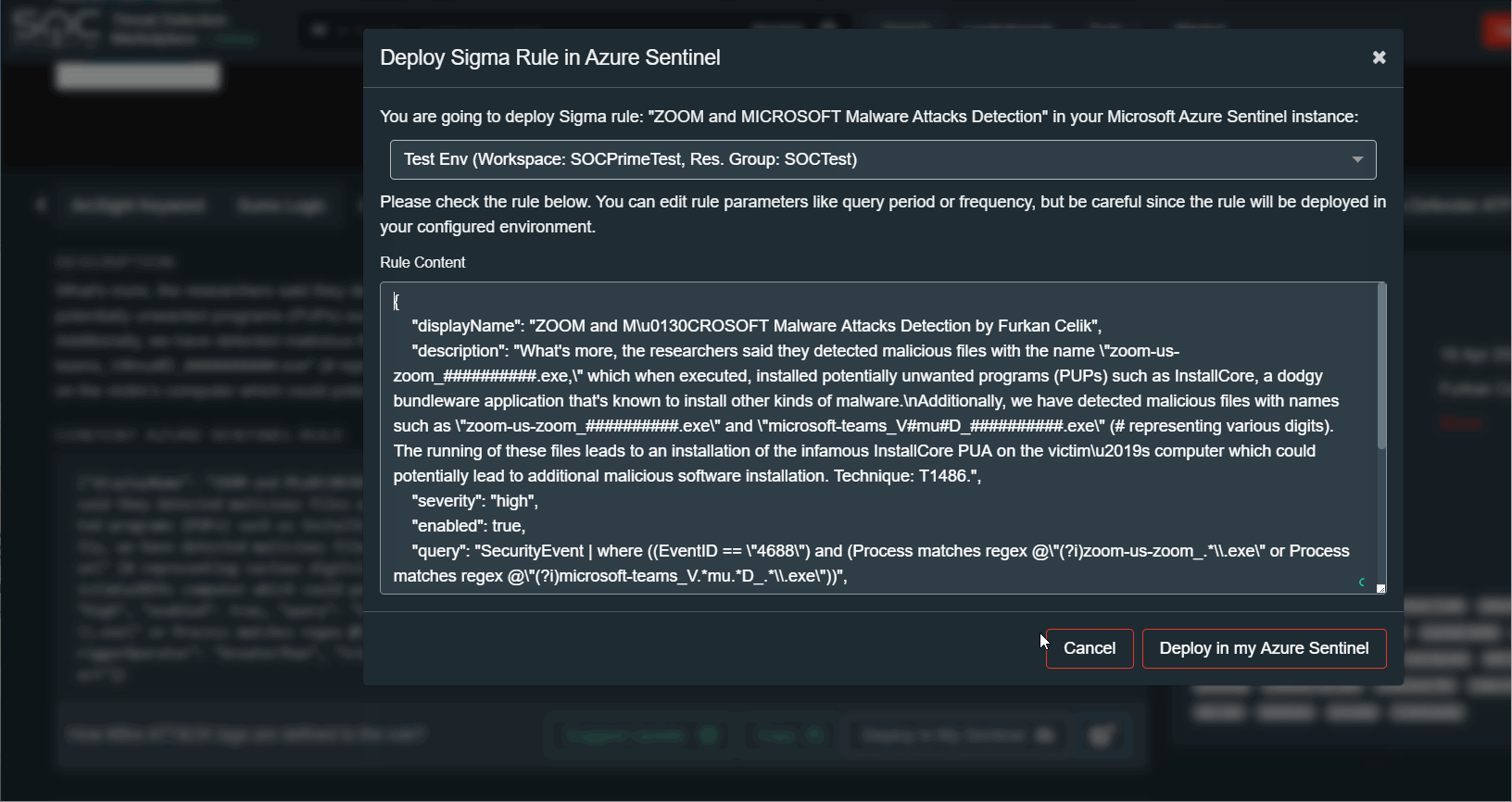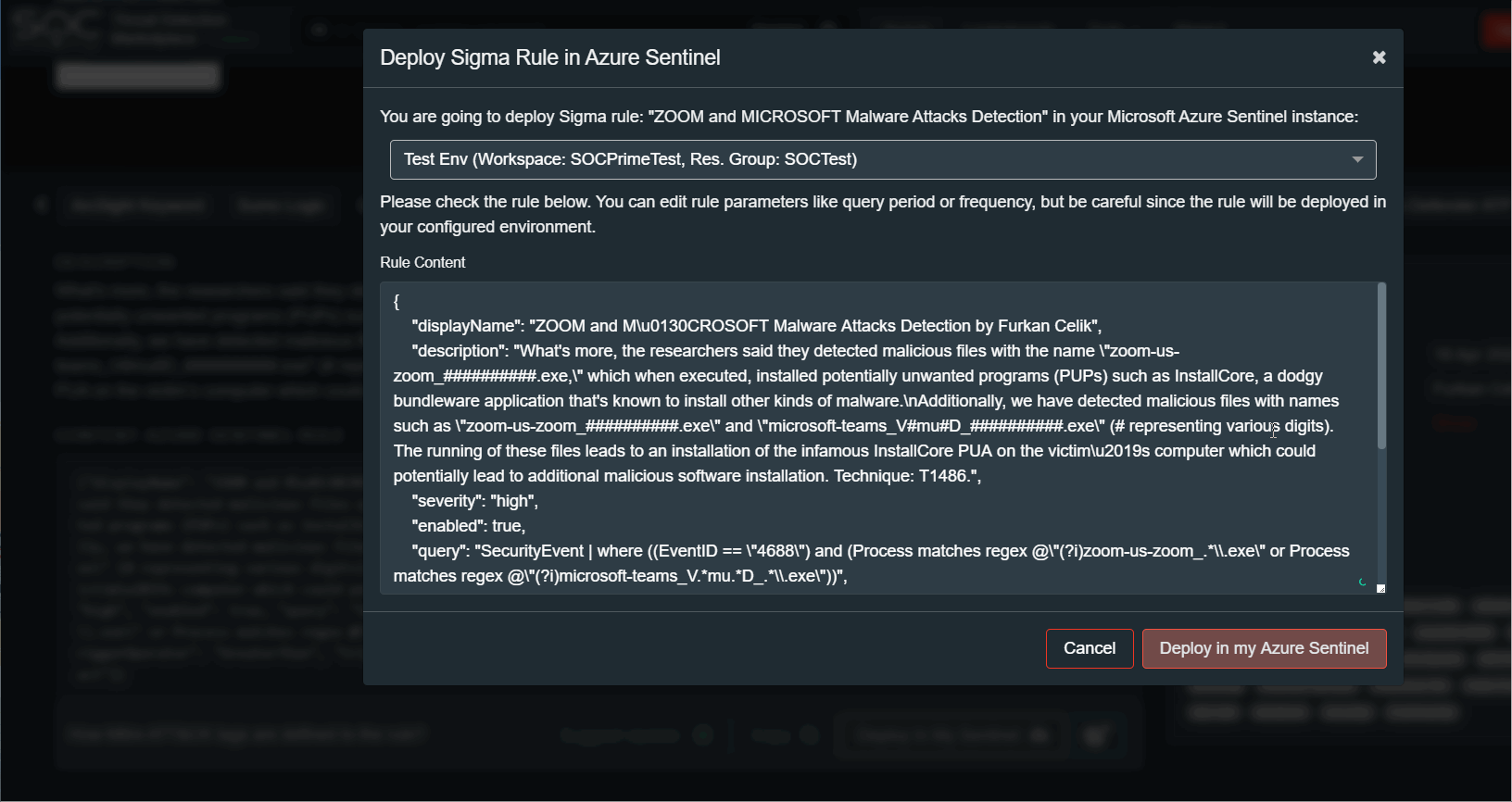
Now you can simply use the “Deploy In My Sentinel” button in your TDM account to deploy queries in the Azure Sentinel.
This button imports query to the Hunting saved search page in the Sentinel. Before deploying you can edit the query manually.
New Hunting queries can be found under the filter PROVIDER: Custom Queries.
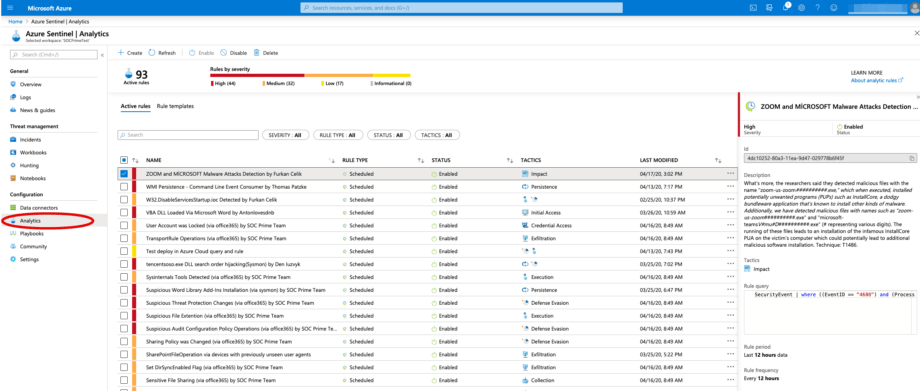
SOC Prime TDM Integration with Azure Sentinel Analytics (Rules)
Also there is a “Deploy In My Sentinel” button in your TDM account to deploy rules in the Azure Sentinel Analytics. This button imports rule to the Analytics page in the Sentinel. Before deploying you can edit the rule parameters manually.
New deployed rule can be found among existing rules in Sentinel Analytics by sorting LAST MODIFIED field.
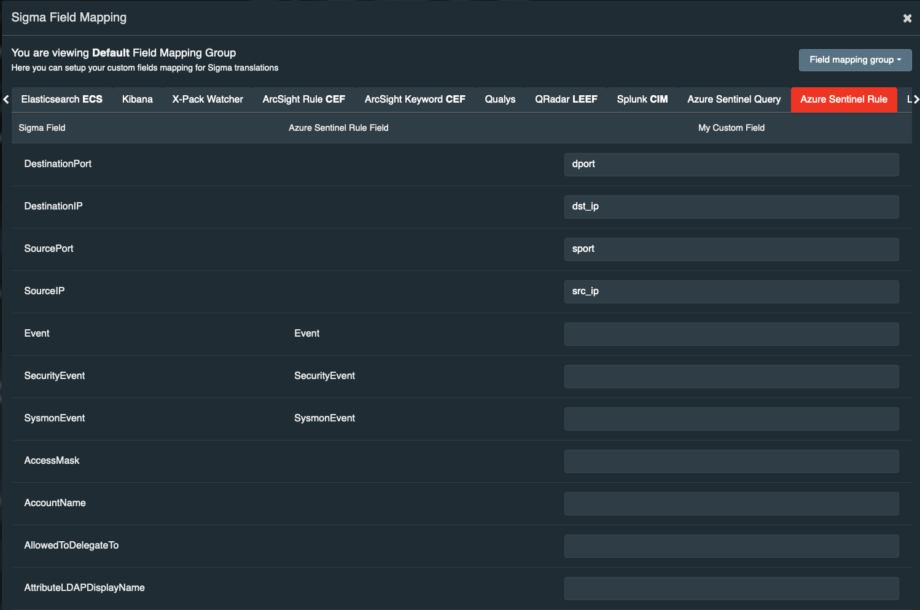
In case you have some mismatch for the field mapping, you can create your own Sigma Field Mapping. Go to Profile -> ‘Sigma Field Mapping’ -> scroll to Azure Sentinel Rule or Query and add there your custom field mappings:
Thanks for reading 🙂
Stay Safe!
Your SOC Prime Team