SOC Prime & Humio Integration: Technical Highlights

Table of contents:
SOC Prime operates the largest and most advanced platform for collaborative cyber defense enabling global organizations to efficiently search for emerging threats at lightning speed. SOC Prime’s Detection as Code platform curates the most up-to-date Sigma-based threat detection content and integrates with more than 25 SIEM, EDR, and XDR platforms. An extensive collection of 180,000+ verified and context-enriched detection and response algorithms is continuously updated and aligned with the MITRE ATT&CK® framework to ensure increased visibility into threats matching the organization’s attack surface.
In this blog article, we’ll cover the most important capabilities of SOC Prime’s platform aimed to simplify and maximize the efficiency of SOC operations for teams using the Humio cloud-based solution.
Tailor SOC Prime’s Platform to Humio Environment
New users of SOC Prime’s platform are prompted to perform a one-time guided setup process using the onboarding wizard designed to tailor the platform experience to the organization-specific environment. This customized setup is designed to boost threat detection capabilities and threat hunting velocity, and drive immediate value from SOC Prime’s solution.
Current SOC Prime subscribers will also be prompted to populate missing settings to customize the platform experience to their security needs and instantly maximize their threat detection and hunting experience. To begin, click Open Wizard from the notification that appears on top of each screen and proceed with the settings.
Throughout the entire setup procedure, Humio customers can watch brief video tutorials in the Tips section on the right designed to simplify the onboarding experience. Alternatively, they can reach out for help in one of the following ways:
- Turn to the Slack Community experts via a Slack channel or submit a Help Request
- Ask for instant support via the Intercom chat and get in touch with SOC Prime experts
For Humio users, the onboarding process involves the following five steps:
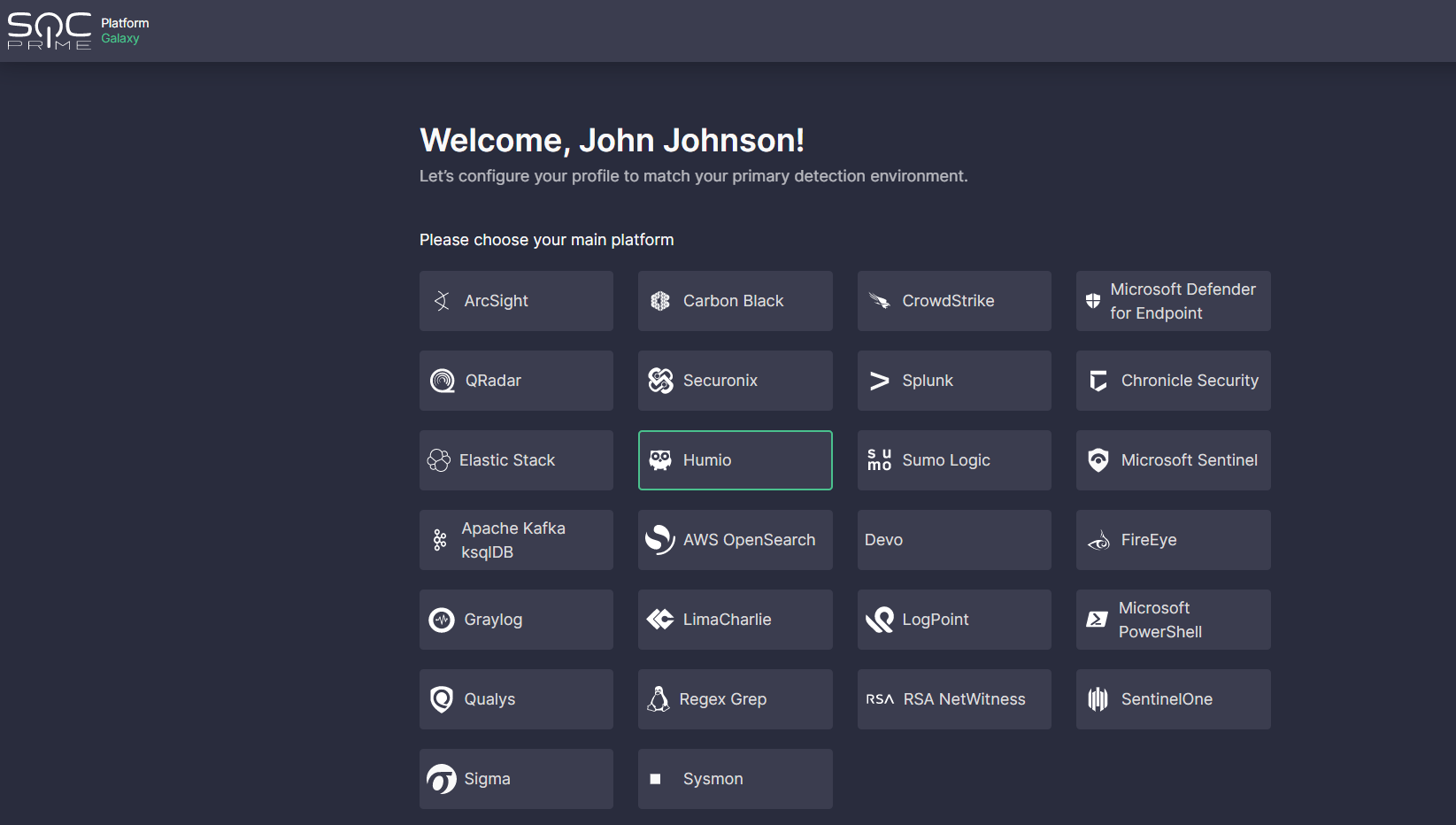
- Select the Humio platform from the list of predefined options.
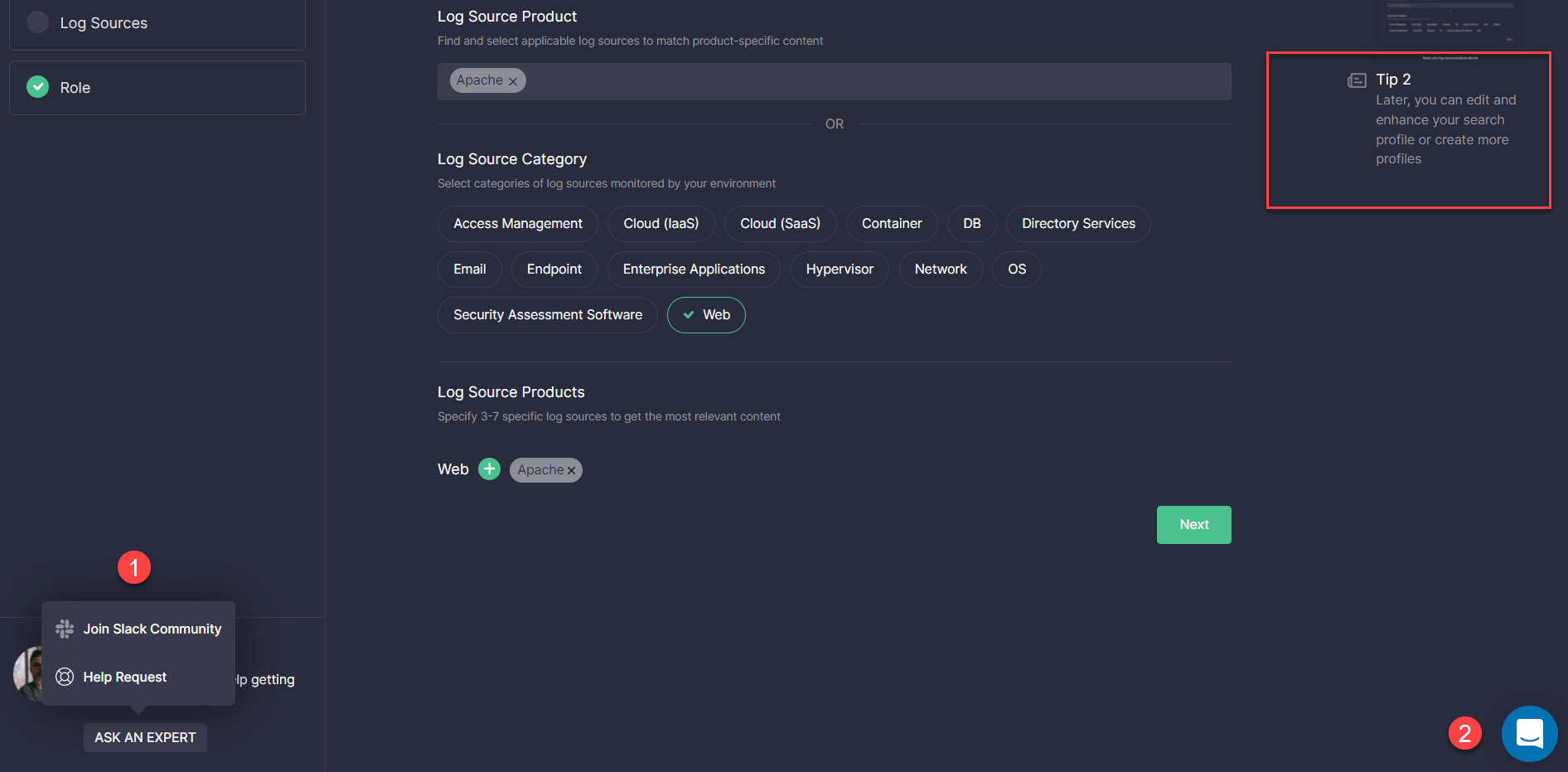
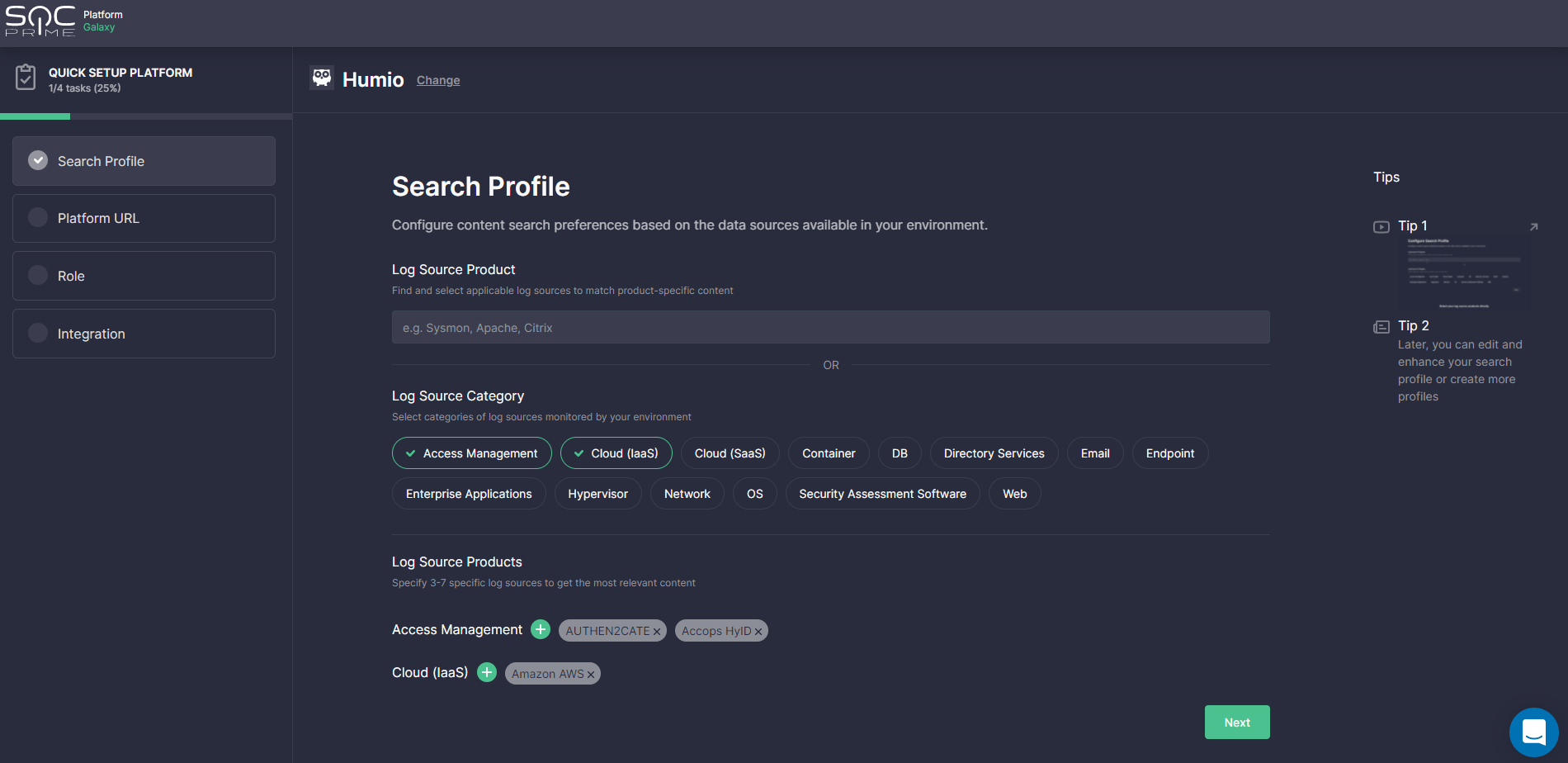
- Set up the Onboarding Search Profile to tailor the detection content search to the data sources relevant to your Humio environment. Here you can select a set of log source products straight away from the list of predefined options or first choose a category and then relevant products tied to it. Click Next as soon as at least one log source product has been provided.
Please note that once set up, this Search Profile can be applied to the Advanced Search page, MITRE ATT&CK® Coverage, and Log Source Coverage dashboards to adjust your content search to actual environment needs.
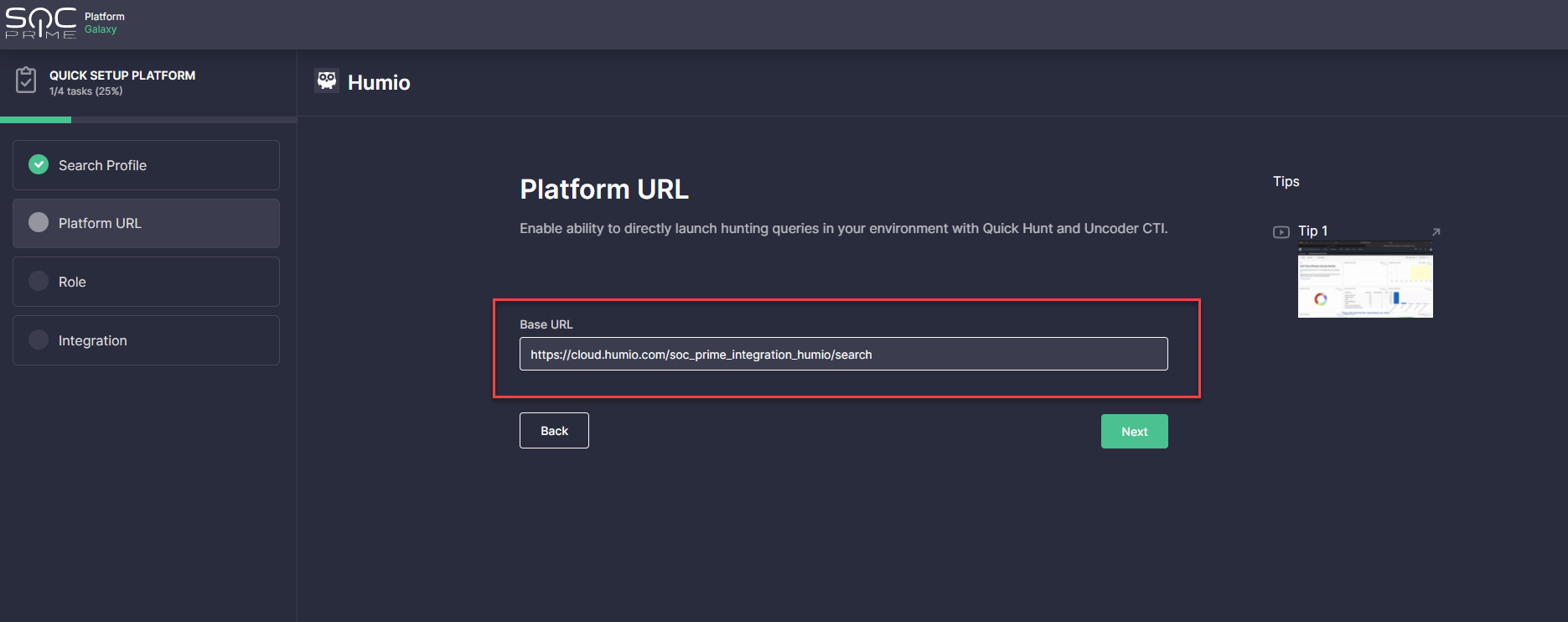
- Provide a Platform URL to set up your hunting environment. These settings are required to enable instantly running hunting queries in your Humio cloud instance with SOC Prime’s Quick Hunt and Uncoder CTI modules. Log into your Humio Cloud instance, copy the link to the repository you want to use for integration, and paste it into the Base URL field of the onboarding wizard.
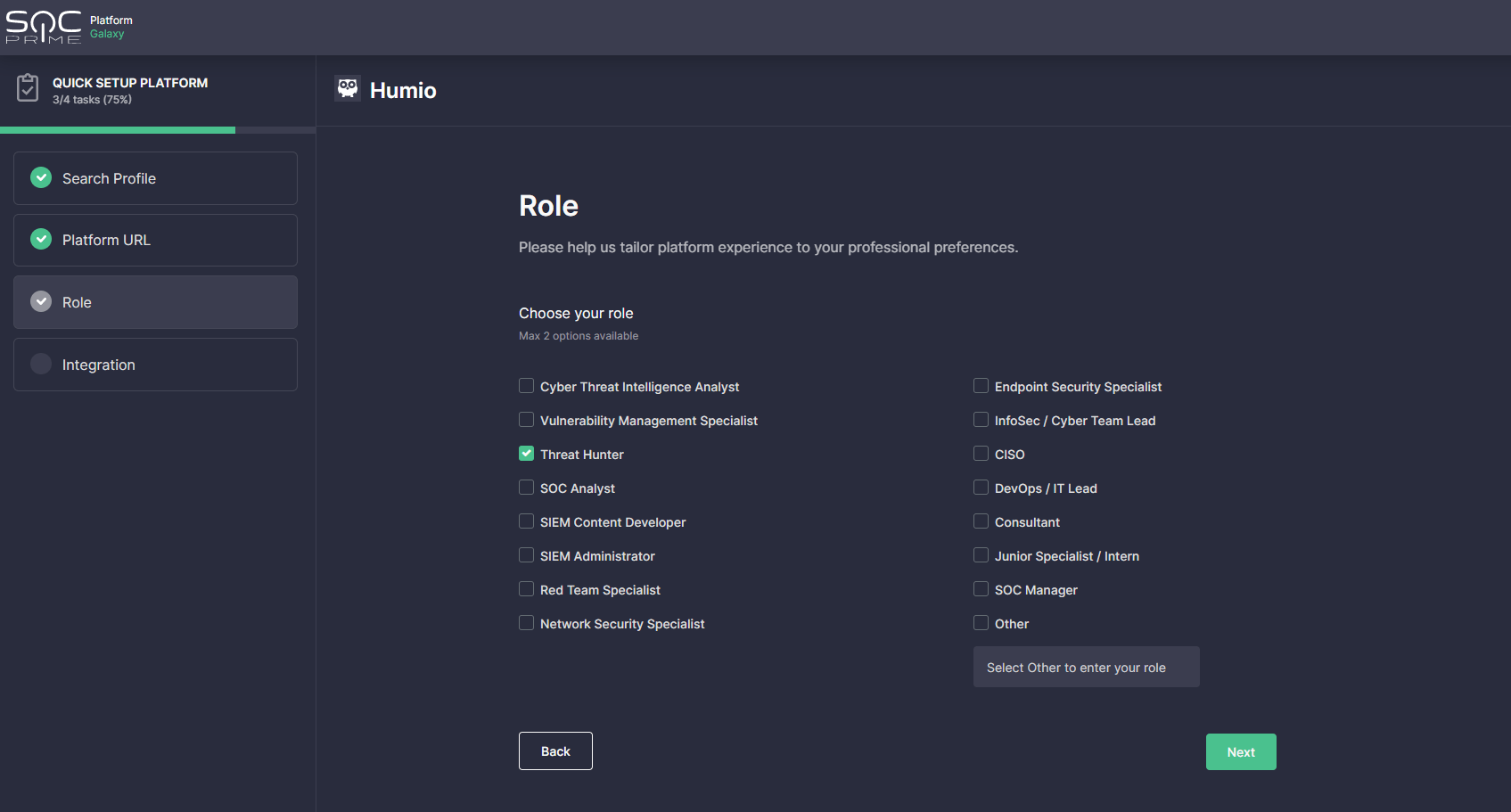
- Optionally, select the professional role to gain the most personalized platform experience. Security practitioners can select two options at most or fill in a different role in the Other field.
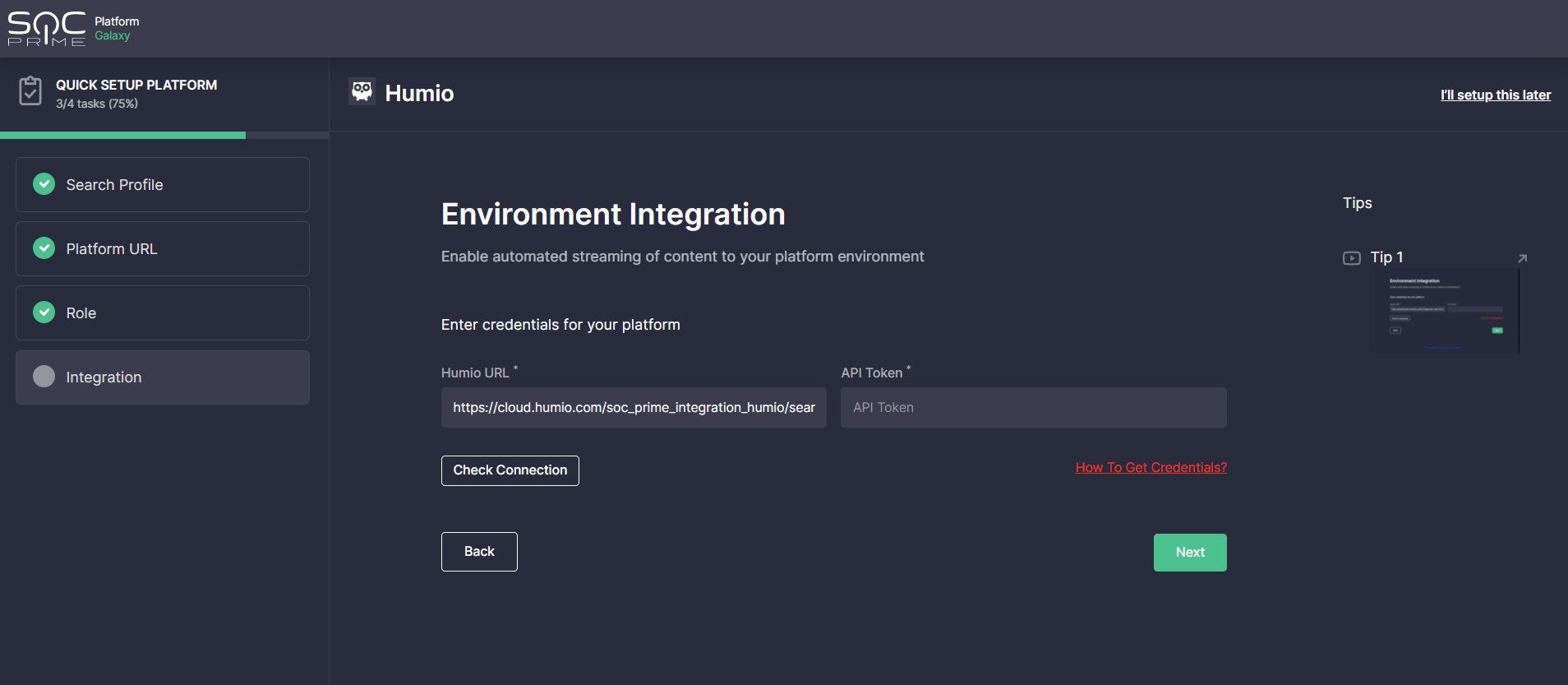
- Set up Environment Integration — the full-fledged API configuration with your target environment to enable automated streaming of detection logic to your Humio cloud instance. After completing the Platform URL settings at step 3, your Humio base URL will be automatically populated in the corresponding field.
To get an API token, go to your Humio Cloud instance and click Manage Your Account linked to the repository you want to use for the integration. Then select API tokens from the Account settings and click the Generate new API token button. On the pop-up that appears, click the Renew token button, copy the newly generated token and then paste it into the API Token field on SOC Prime’s onboarding wizard.
Once configured, click the Check Connection button. If the connection is successful, you’re done with the Humio integration and are all set to unleash the full power of SOC Prime’s platform.
Search for Threats and Deploy Detections to Your Humio Instance With a Single Click
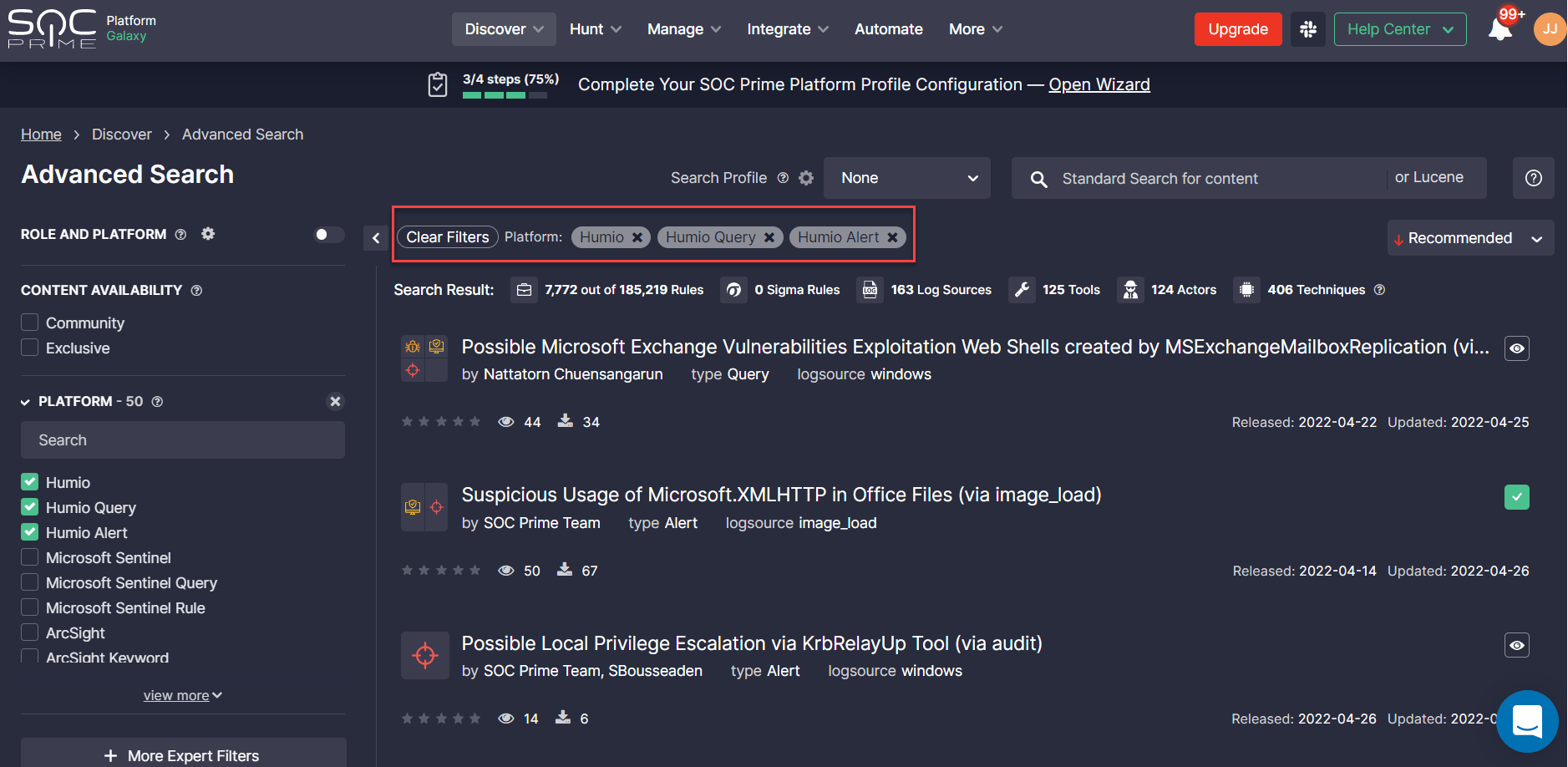
To reach the entire collection of Humio detection rules, select Discover > Advanced Search after logging into SOC Prime’s platform. Security practitioners can filter content by the Humio platform or by Humio-specific content types — Alerts or Queries. Once applied, drill down to the content item page to reach the detection source code convertible to the Humio cloud-native language format.
Please note that after setting up the onboarding wizard for your Humio environment, the content item page will automatically display the rule source code in the corresponding platform format. There is no need to filter content by the Humio platform beforehand.
Depending on the selected content type, you can choose one of the following automated detection capabilities tailored to your Humio environment*:
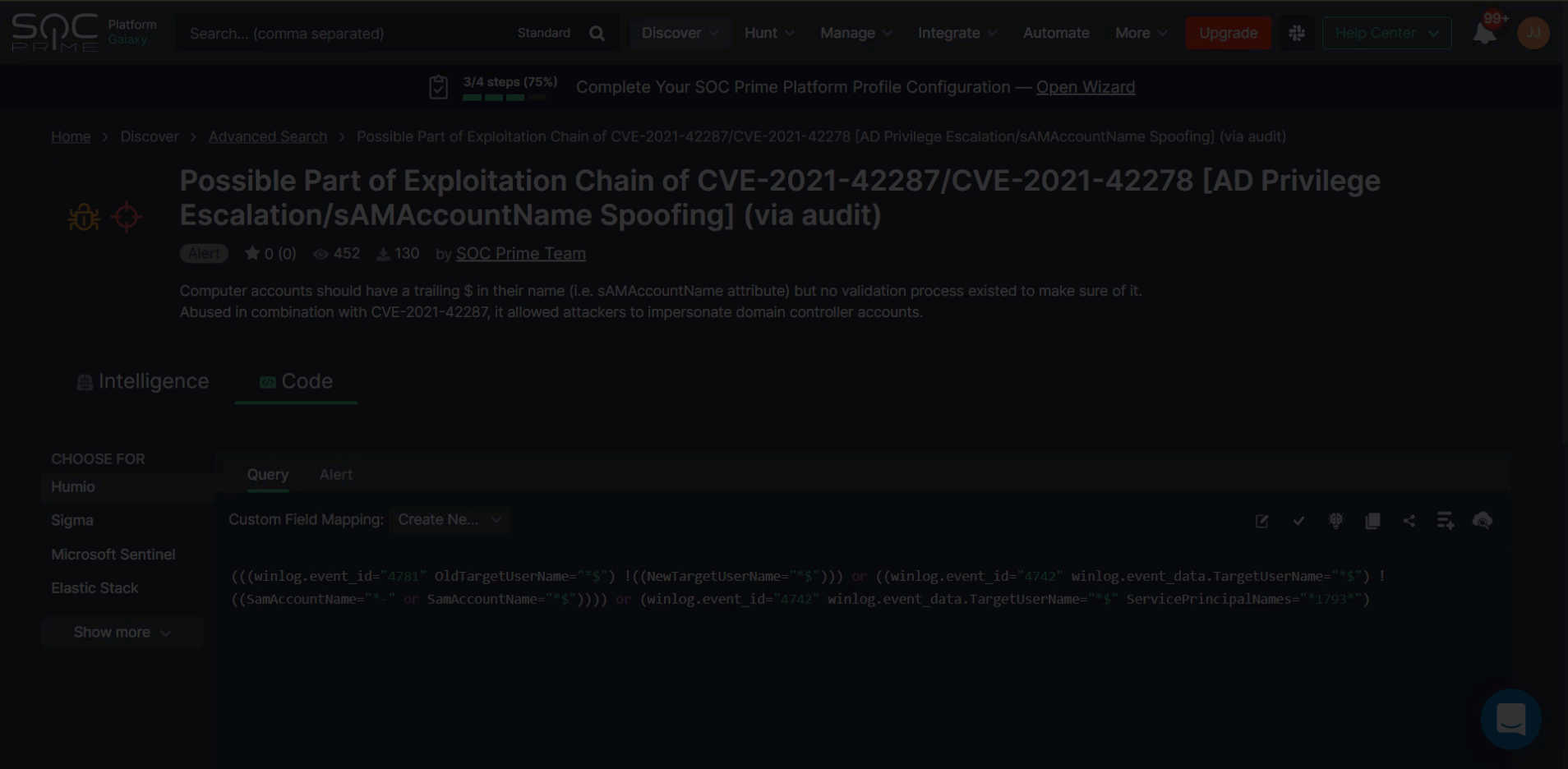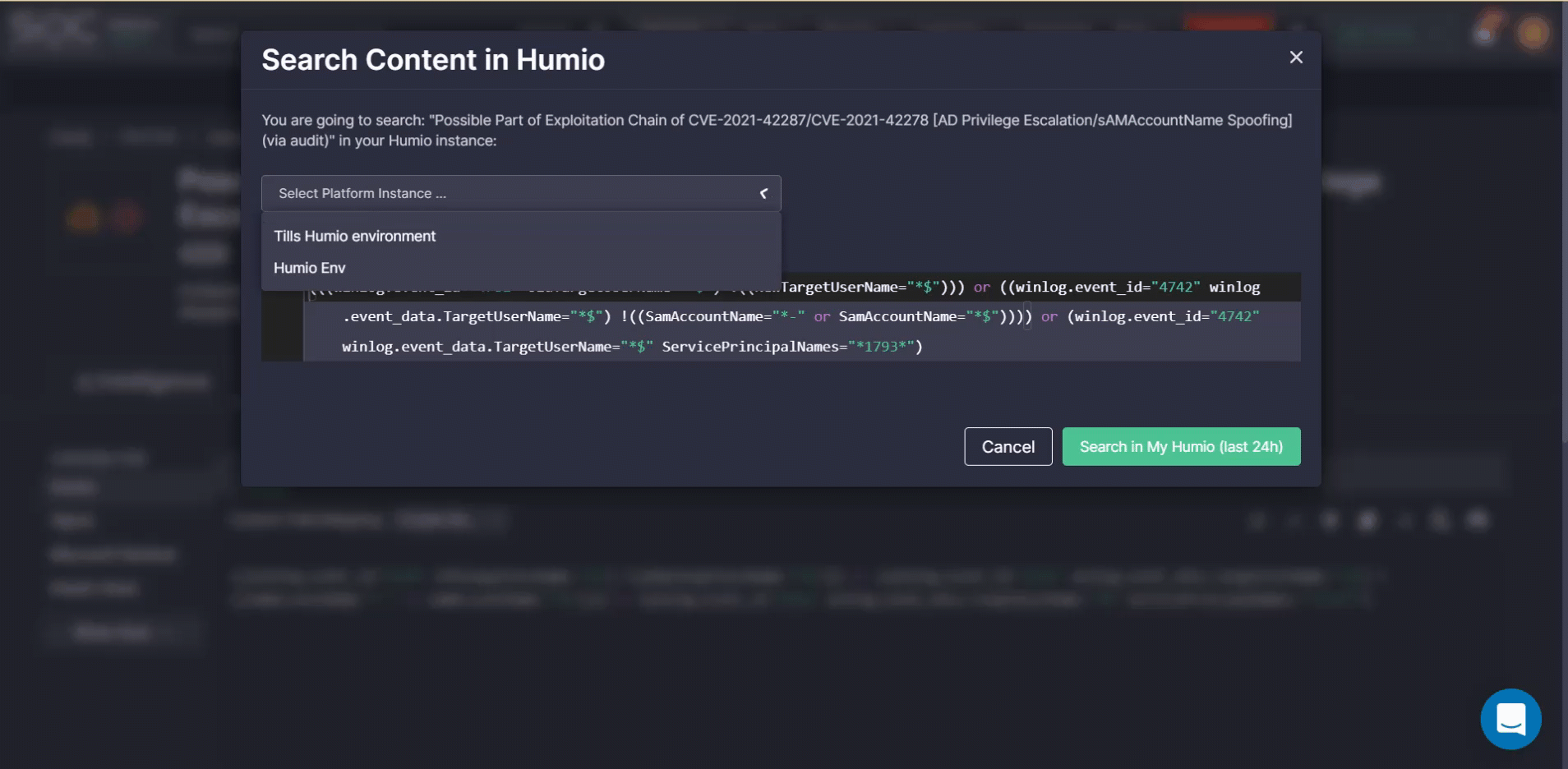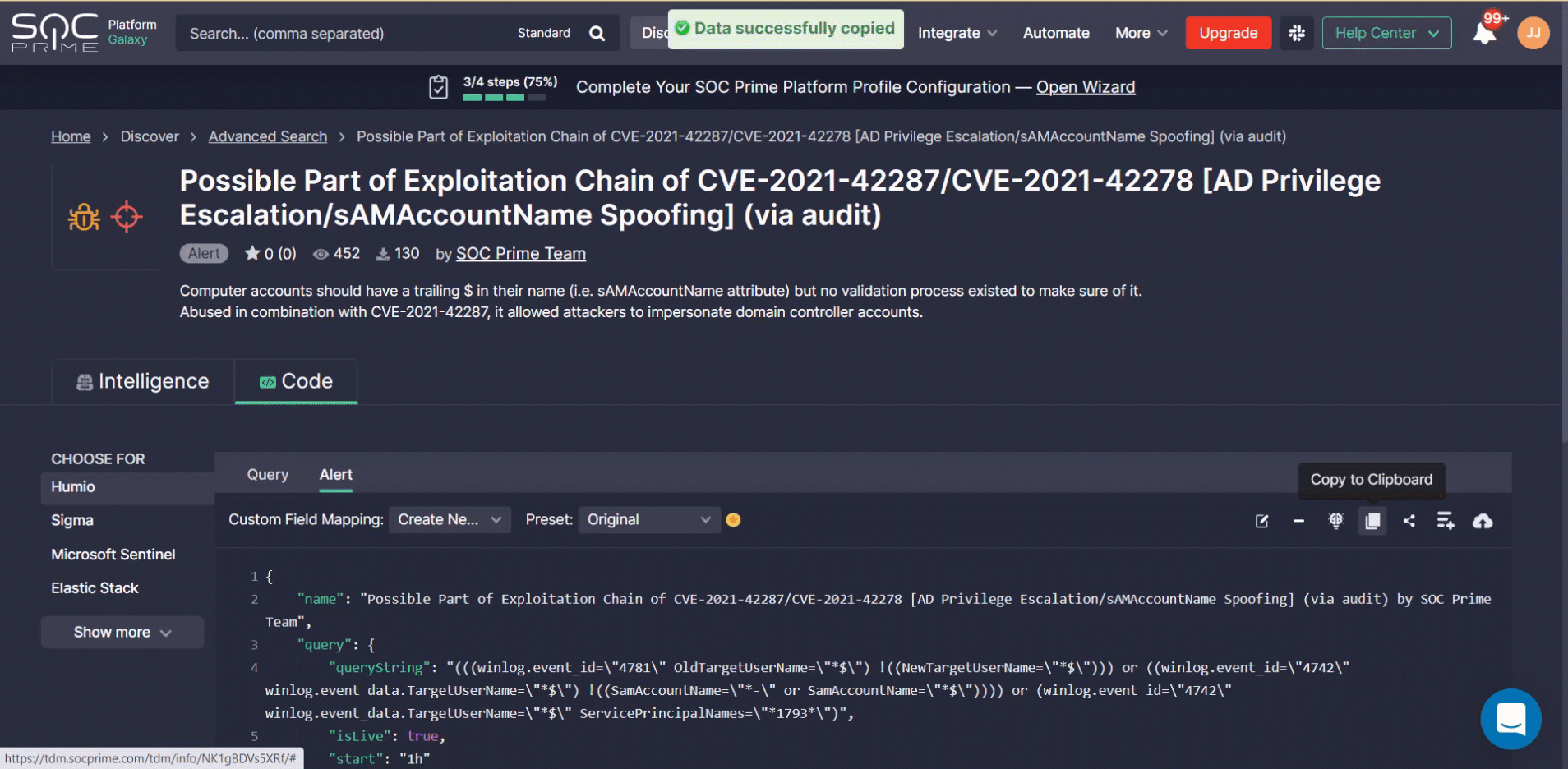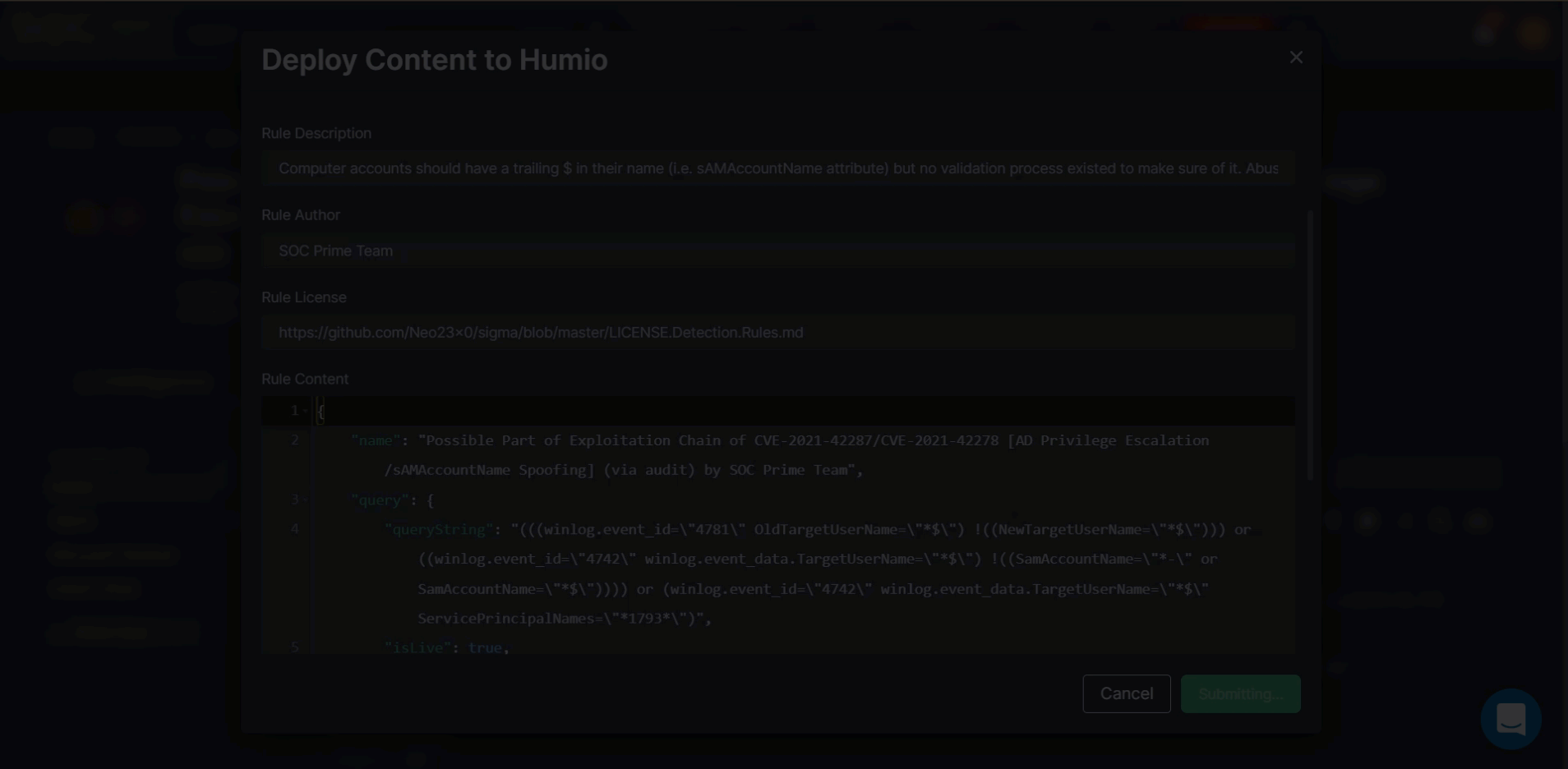
- Instantly search for threats with Humio Queries by clicking the Search in Humio button.
- Automatically deploy Humio Alerts via the Deploy to Humio button.
*These actions are available after completing the Environment Integration setup at step 5 of the onboarding wizard. For both automated search and deployment actions, you need to select one of the pre-configured environments.
Alternatively, you can manually copy the source code via the Copy to Clickboard button and then instantly paste the Humio Query or Alert to your cloud environment and run the detection rule.
Continuously Stream Real-Time Detection Algorithms Directly to Your Humio Instance
Teams can automatically stream Humio Alerts directly into their cloud-native environment via the Continuous Content Management (CCM) module available under the Automate category of SOC Prime’s platform. Powered by Humio’s API, this functionality allows organizations to stay on top of both emerging threats and strategic detection objectives without having to manually search for or download content from SOC Prime’s platform.
Please note that before leveraging the CCM module, Humio customers should have enabled API access to their Humio subscription, which can be pre-configured at step 5 of the onboarding wizard.
SOC Prime users can leverage the following CCM capabilities:
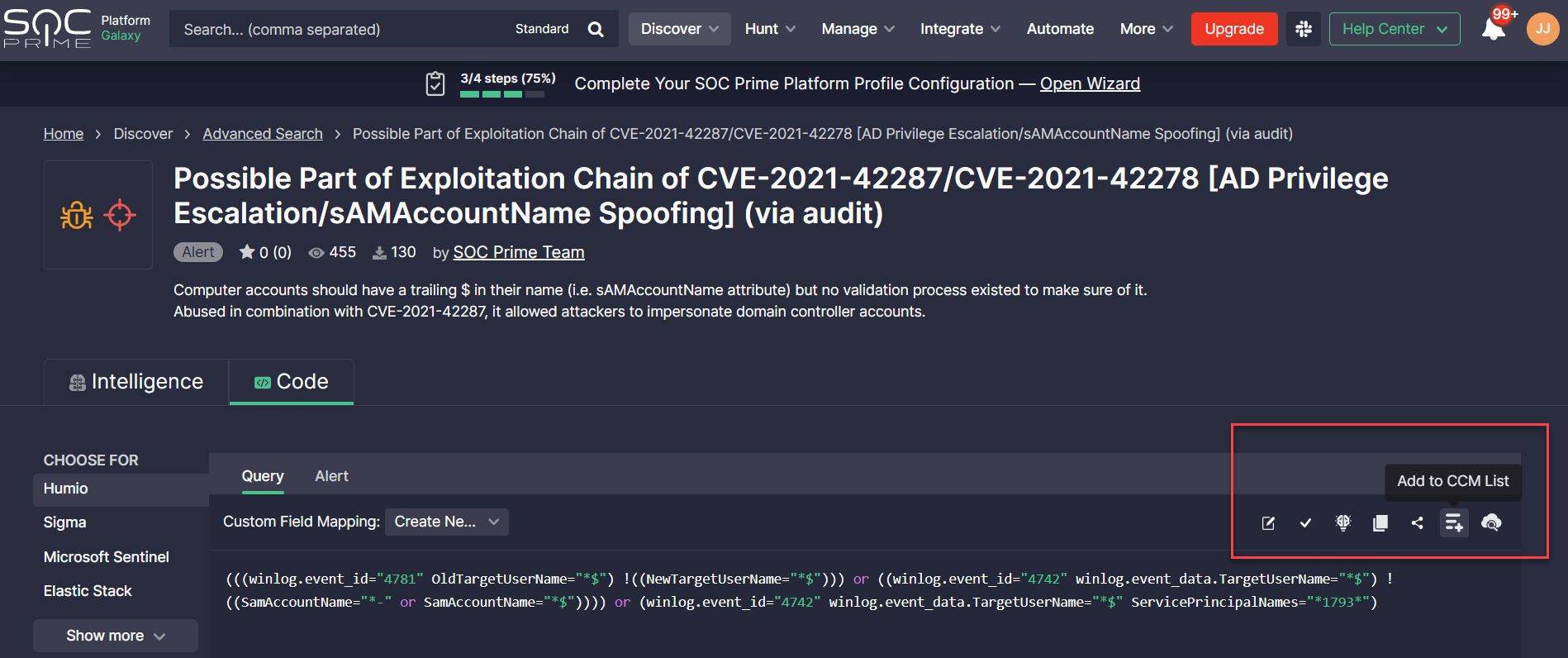
- Create and manage content lists on the fly to pull Humio Alerts from these lists to the cloud instance in use:
- Static lists with hand-picked content. Selected content items can be manually added to specific lists by clicking the Add to CCM List button from the Code tab.
- Dynamic lists to automatically populate the latest and recently updated Humio Alerts mapped to the pre-configured filter conditions. To tailor the dynamic content list to the Humio format, on the list configuration form, click Advanced Filters > Content Platform, and select Humio Alert from the list of predefined options.
- Inventory lists to modify and deploy custom content versions across multiple Humio instances.
- Static lists with hand-picked content. Selected content items can be manually added to specific lists by clicking the Add to CCM List button from the Code tab.
- Run flexibly scheduled jobs to automatically pull detection algorithms from specific content lists tied to the pre-configured Humio environment. By default, jobs will apply the default Custom Field Mapping profile based on the pre-configured log source applicable for such deployments. Here you find the details on how to set up the log source-based Custom Field Mapping profile.
- Manage all detection content inventory from a single place with the ability to update rules on the fly and then deploy the changes directly into the Humio environment. On the Inventory page, teams can also track the deployment status, content author and source, deployment date, and other details of detection deployments.
- Browse the entire logging history of automated and manual content deployments along with inventory modifications. On the History page, security engineers can also delve into the deployment issues for all Humio Alerts for better visibility.
- Customize deployments to tailor detection logic to your environment and processes and avoid large volumes of false positives via Presets and Filters.
To gain more insights into the automated content management capabilities, please refer to the dedicated blog article.
Simplify Threat Hunting Operations
After configuring the hunting environment at step 3 of the onboarding process, Humio customers can leverage SOC Prime’s hunting tools to search for threats faster and simpler than ever before.
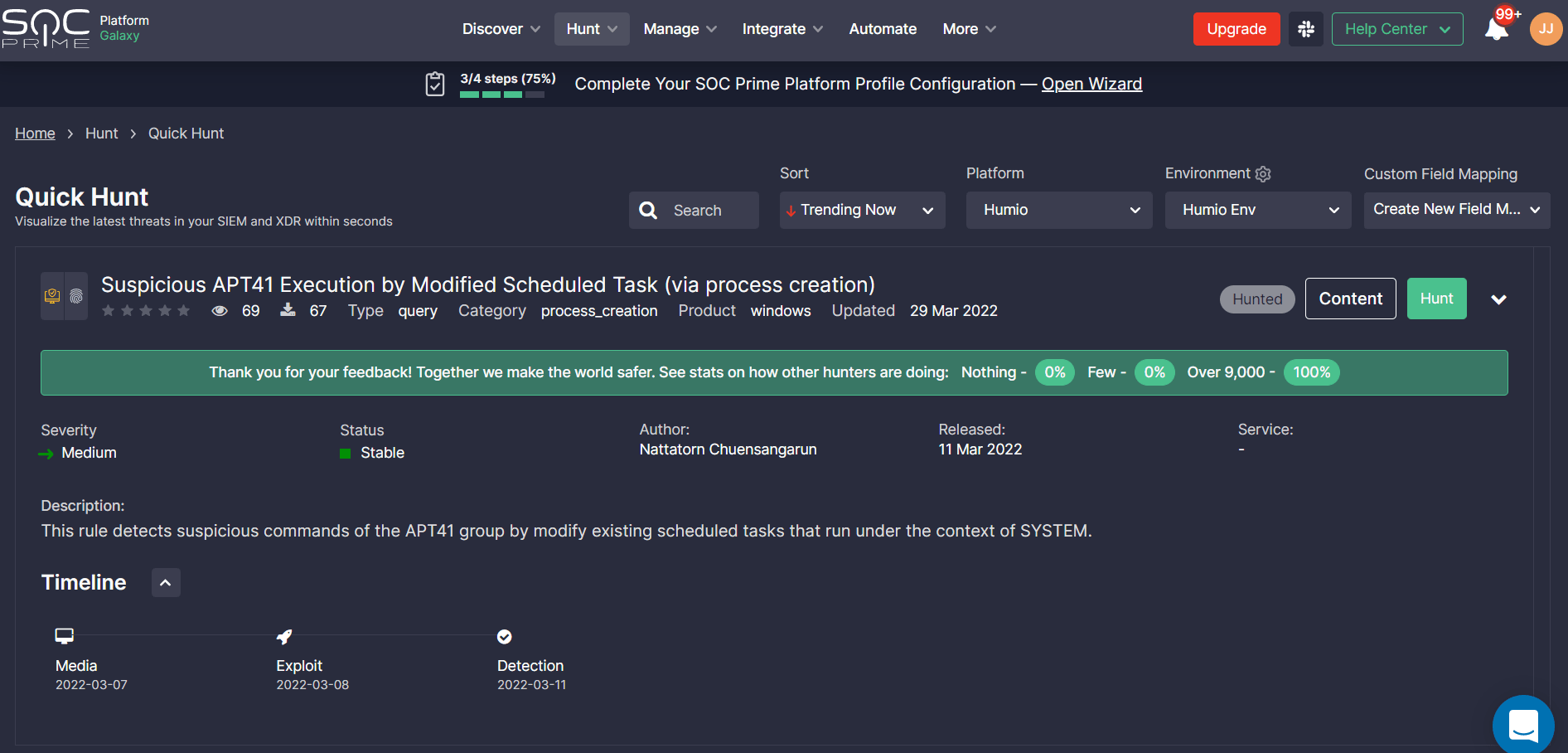
Quick Hunt allows teams to easily hunt without an expert background in the field. To get started, select Hunt > Quick Hunt and browse the query list sorted by top trending detections by default. Your Humio platform will be pre-selected at once along with the pre-configured environment according to the onboarding settings. In addition, you can also select an existing Custom Field Mapping profile or set up a new one for hunting on non-standard log data. Please refer to the dedicated article section on how to configure the log source-based Custom Field Mapping profile.
Make sure you are logged into Humio Cloud before running a Quick Hunt Session.
Click Hunt to run a selected query directly in your Humio environment and then share feedback with your peers on your hunting experience. Providing feedback contributes to the collective global expertise enabled by SOC Prime’s platform and helps make hunting more efficient while continuously enhancing detection content quality and volume.
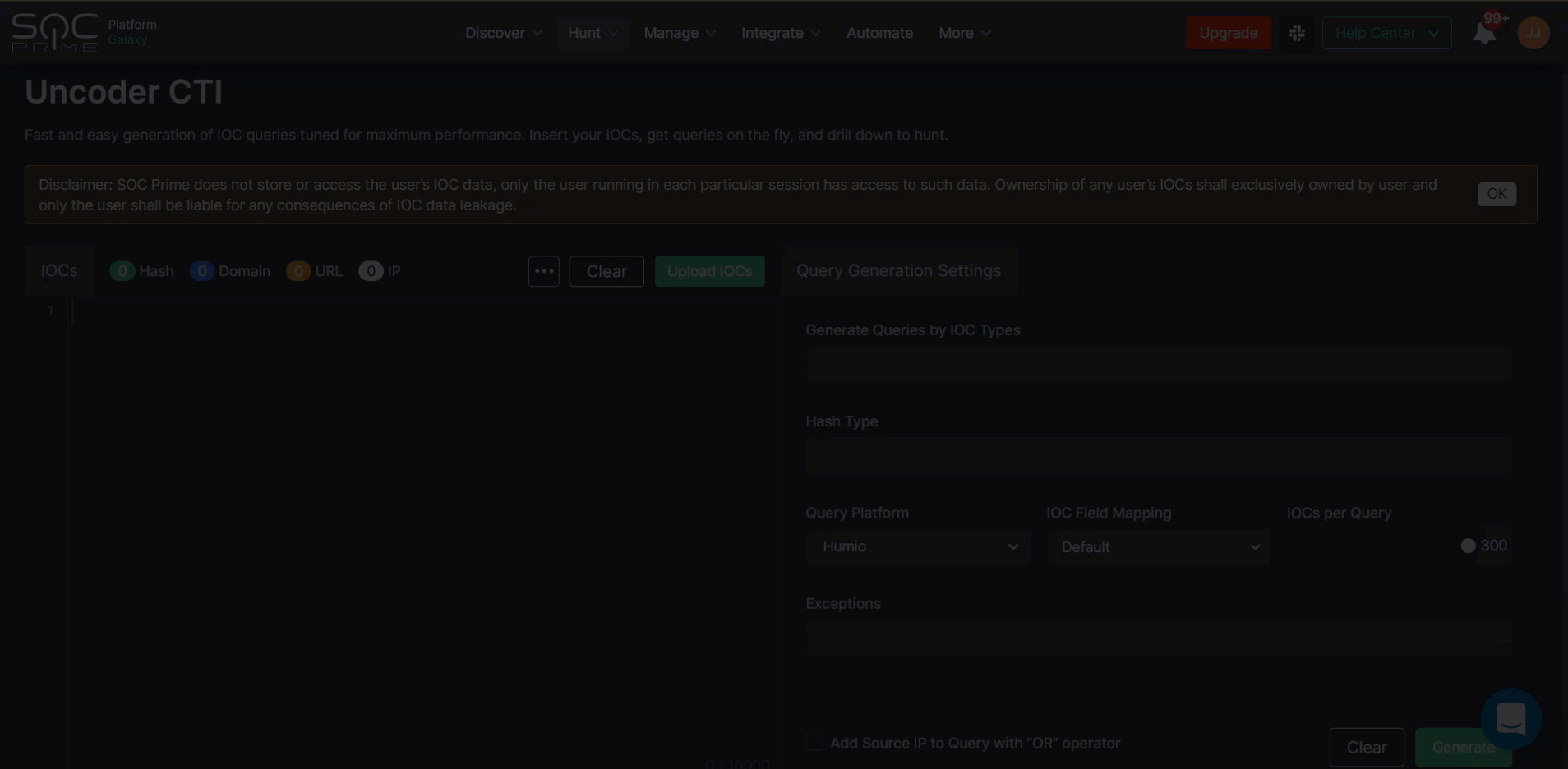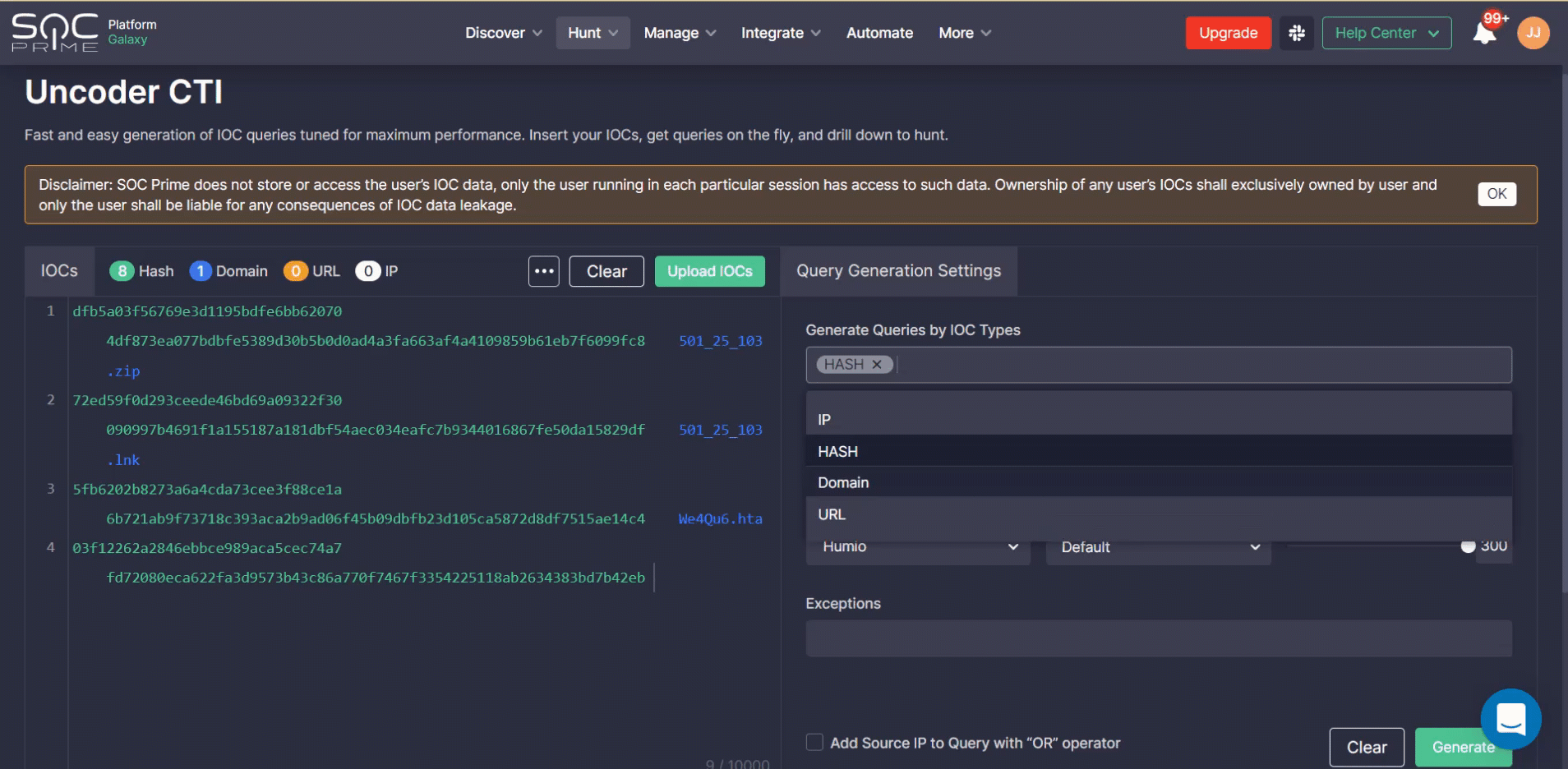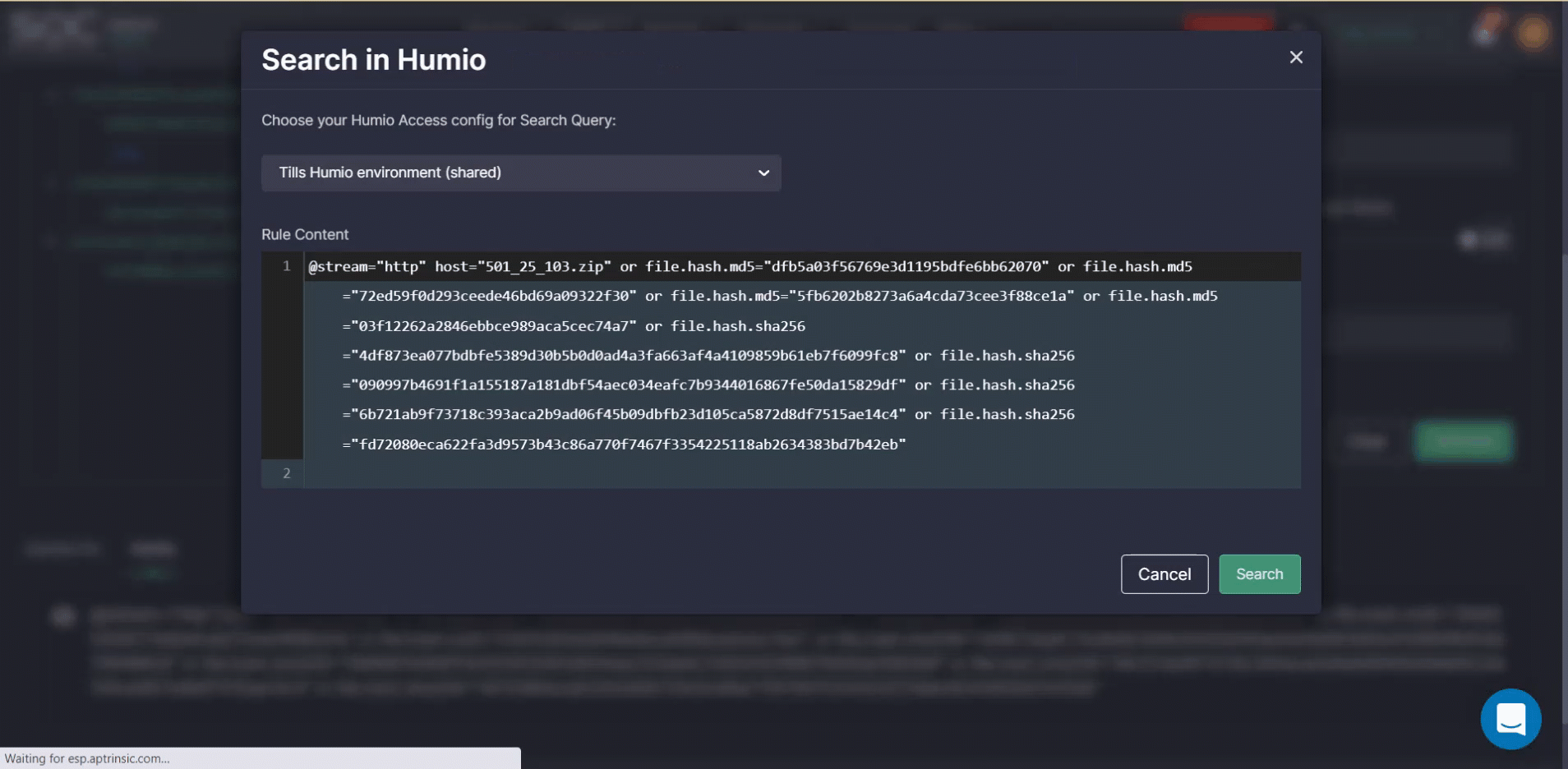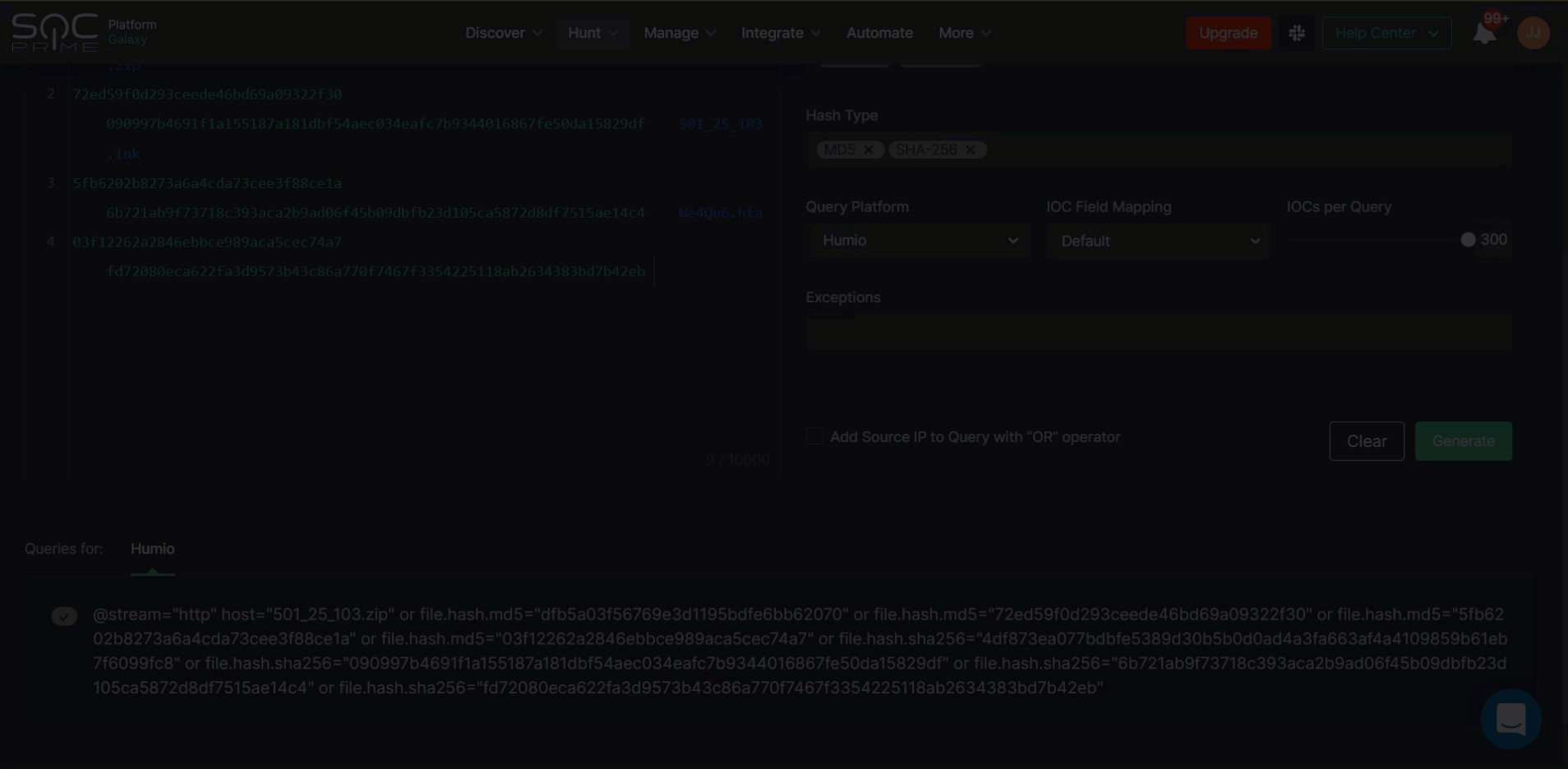
Uncoder CTI is designed to accelerate IOC-based threat hunting and allows instantly generating IOC queries fine-tuned for organization-specific environment needs.
Please note that after configuring the platform-dependent onboarding wizard, Humio will be automatically set as a hunting environment for Uncoder CTI sessions.
Humio users can hunt with Uncoder CTI in just a matter of clicks:
- Insert IOCs directly into the left hand-side panel or import the corresponding CSV, JSON, or TXT file.
- Customize the query to be generated: select IOCs, specify the IOC field mapping profile other than the default one (if needed), set the number of IOCs per query, and add exceptions. Hash types will be automatically populated based on the provided IOCs.
- Click the Generate button to obtain a custom IOC query.
- Choose to copy the query and then paste it into your environment or click the Hunt in your environment button to automatically run the generated query in Humio.
Notably, SOC Prime users can make the most of Uncoder CTI free of charge through May, 25, 2022.
Convert Sigma Rules to Humio Alert and Queries via Uncoder.IO
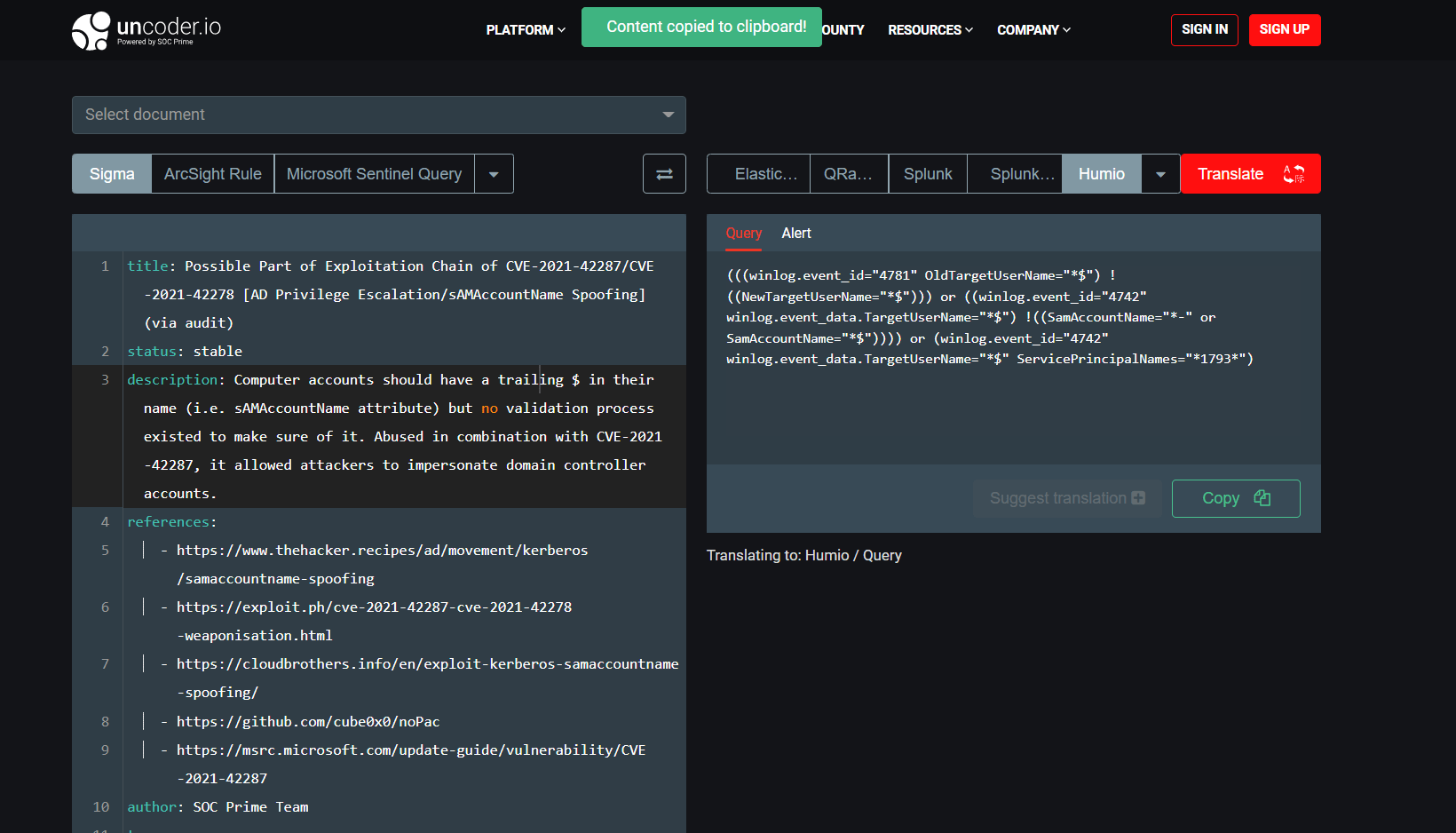
Uncoder.IO is an online translation engine intended to dissolve the boundaries of a single tool for hunting and detecting threats that enables converting Sigma-based detections to 25+ SIEM, EDR, and XDR formats. To automatically translate Sigma rules to the Humio format, take the following steps:
- Select Sigma as an input query language in the left hand-side panel.
- Insert the Sigma rule source code or select the relevant document from the drop-down list.
- Select Humio as a target language in the right hand-side panel.
- Select the target Humio format — Alert or Query.
- Click the Translate button.
- Click the Copy button and paste the detection code into your Humio environment.
Join SOC Prime’s Detection as Code platform to tap into the power of global industry collaboration enabling teams to keep up with the ever-increasing attack volume and proactively defend against complex and continuously growing digital threats. By harnessing the collective expertise of the world’s largest and constantly enriched detection content library, organizations can solve the challenge of creating a continuous volume of customized content suited for their unique SOC deployment environment. Individual researchers are also encouraged to join the ranks of collaborative cyber defense by sharing their detection content and being compensated for their contributions.