SOC Prime Provides a Smoking Guns Sigma Rules List to Give Organizations a Competitive Advantage in Cyber War

On July 6, 2022, SOC Prime introduced a Smoking Guns Sigma Rules list enabling the organization of any scale to proactively detect cyber-attacks, perform Threat Hunting for the latest adversarial TTPs, and get a tactical defense advantage for their business during the global cyber war. SOC Prime’s Detection as Code platform users are now equipped with the top-quality threat detection content against the most common behaviors and tools used in current and future destructive cyber-attacks.
Enabling Individual Defenders and SOC Teams to Stay Ahead of Attackers
The ever-growing attack surface and increasing complexity of the cyber threat landscape have put cyber defenders in a condition of never-ending threat chasing where adversaries are always one step ahead. For example, the NVD database holds more than 12,000 vulnerabilities published in 2022 so far. Hundreds of CVEs are reported each week and dozens of malicious approaches pop up daily. Such a trend creates absolutely enormous workload for security teams flooded with huge amounts of data to analyze combined with large volumes of false-positive alerts. Information overload, cybersecurity silos, and critical personnel burnout substantiate a high demand for proper prioritization and high-fidelity alerts that will help security teams to align their efforts.
Driving threat detection evolution and connecting security practitioners for collaborative cyber defense, SOC Prime has pioneered the Detection as Code approach, which has become a widely accepted trend and significantly contributed to the Sigma rules recognition as a de-facto industry-standard language for writing and sharing detection code. Since the invention of the Sigma language in 2016, SOC Prime has been a pioneer supporter and the biggest commercial Sigmac backends contributor to this generic detection content format, which has been recommended by industry-leading organizations, including U.S. federal agencies like CISA and FBI, founders of the leading threat intelligence platform of the EU, MISP, and the SANS Institute. For over 7 years, the SOC Prime team, together with the Sigma community and Threat Bounty Program members, have encountered and resolved thousands of quality issues of leveraging Sigma rules in production for over 25 SIEM, EDR, and XDR products. Sigma rules use cases have evolved drastically from a hobby project launched by Florian Roth and Thomas Patzke, who serve on SOC Prime Advisory Board. In 2018, SOC Prime launched Uncoder.IO to demonstrate the power of one unified language for Threat Hunting and pioneered the concept of tagging Sigma rules with MITRE ATT&CK®. 2019 was the year when the crowdsourcing initiative was born, with hundreds of security researchers from different parts of the world joining SOC Prime’s Threat Bounty Program and starting their contributions to Sigma rules on daily basis. This has launched the content creation process into a hyperscale direction. Today, 8,000+ сurated Sigma rules are available through SOC Prime’s platform, and 400+ new behavior-based detections are published monthly. A global collaboration effect has taken place, where 600+ SOC Analysts, Threat Hunters, and Detection Engineers contribute to our Threat Detection Marketplace world’s largest detection content repository, while over 28,000 users who perform the same duties as contributors for enterprise, SME, MSSP/MDR, and government organizations leverage Sigma rule translations daily to enhance their productivity and increase the efficacy of the SIEM and EDR stack in place. As a result, over 8,000 organizations provide feedback on how Sigma rules operate in their environment, highlighting their challenges and suggestions for improvements back to SOC Prime and content Authors on a daily basis.
The combination of the above-mentioned effects allows SOC Prime in conjunction with the global cybersecurity community to address the next challenge in cyber threat detection: content selection. This issue was not so significant before content went hyperscale. The majority of SOC Analysts today are still overloaded with unceasing “security noise.” To concentrate on relevant threats and combat them efficiently, security experts should get a holistic view and set priorities across large volumes of attacks. To reach edge detection, SecOps practitioners require the source of enriched, verified, highly accurate, and low false-positive behavioral detection indicators accompanied by proper threat context for relevant prioritization.
Sigma Rules That Anyone Should Have for Their SOC & Threat Hunting Operations
To address these challenges, SOC Prime has long been working on improvements for the recommendation algorithm harnessing the power of global industry collaboration. We have aggregated the collective feedback and expertise into a comprehensive list of Sigma rules that enables any organization regardless of its size and cybersecurity maturity to apply in their SIEM, EDR, or XDR environment.
We’ve analyzed the content priorities of cybersecurity practitioners determined by their professional roles. High-fidelity Sigma rules are mainly needed by SOC Analysts, while threat hunting queries are a perfect fit for hunting purposes. The Smoking Guns Sigma Rules list serves as a universal solution for a wide cybersecurity audience both offering high-fidelity alerts to identify critical security gaps and providing an immense collection of threat hunting content for deep-dive threat investigation.
Get Smoking Guns Sigma List with High-Quality Content Recommended by Industry Peers
Cybersecurity practitioners can instantly apply the Smoking Guns Sigma Rules list powered by SOC Prime’s recommendation engine from the Advanced Search page after logging in or signing up for the Detection as Code platform:
- Go to Discover > Advanced Search.
- Select the Smoking Guns option from the sorting drop-down.
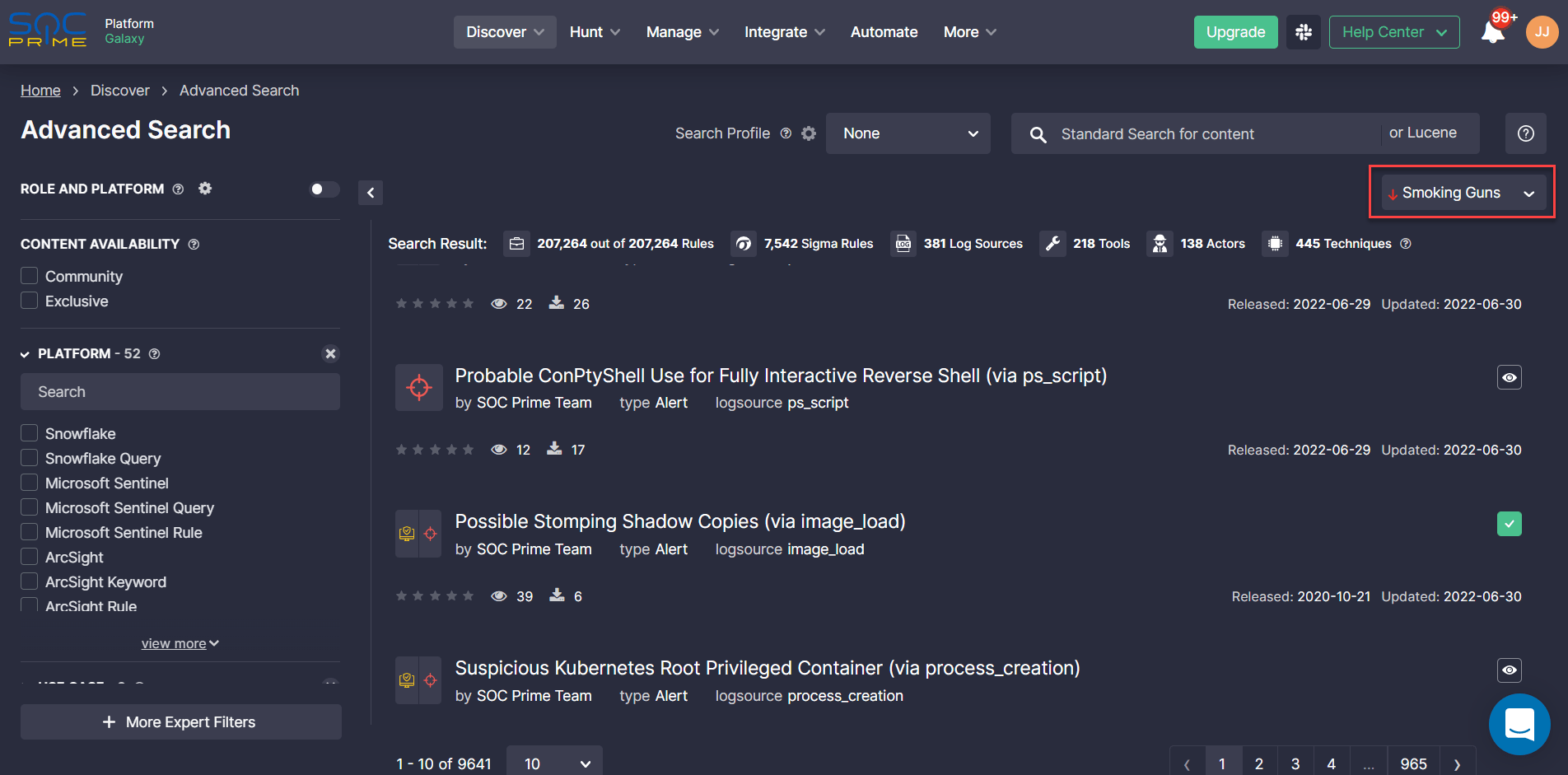
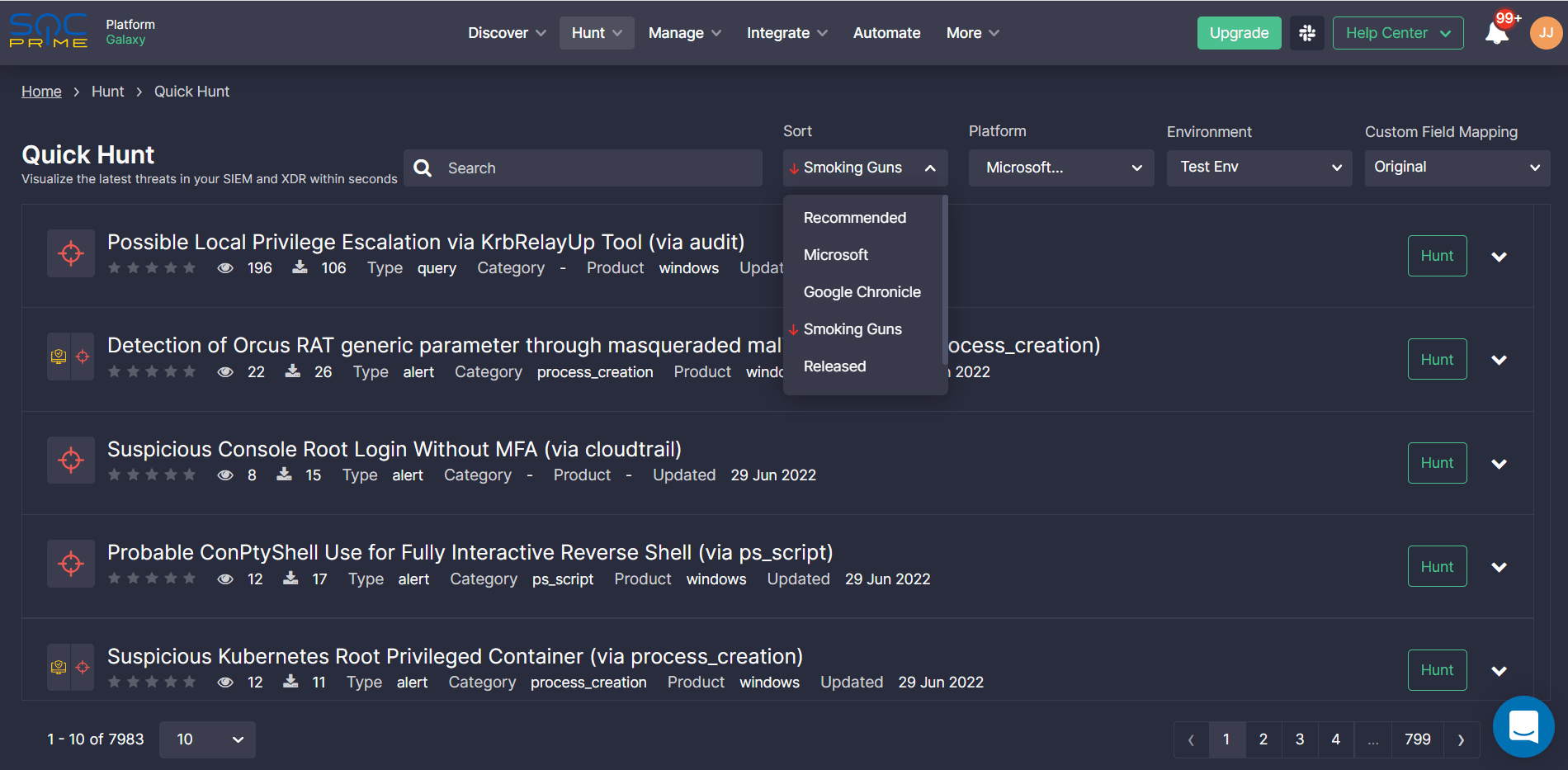
Alternatively, SOC Prime users can access dedicated Sigma rules for streamlined Threat Hunting operations from the Quick Hunt module UI. By selecting the Smoking Guns option from the Sort drop-down, the recommendation engine will display relevant hunting queries at the top of the list.
Automatically Stream Top Quality Sigma Rules From the Curated Content List Directly Into Your Environment
Most mature security teams who defend the largest enterprise and government organizations and hold the cyber frontline at MSSP and MDR companies are on a rising trend to leverage CI/CD pipelines to automatically stream Sigma rule translations directly into their SIEM and EDR stack. SOC Prime’s platform enables security practitioners to stream detection logic from the curated Smoking Guns Sigma Rules content list created by the SOC Prime team leveraging the automated capabilities of the Continuous Content Management (CCM) module. Any team with access to the CCM module can configure the automated deployment of this content list directly into the SIEM or EDR instance in use. Explore this article to find out how to enable SOC Prime’s automation module and tailor it to your environment needs.
Please note that organizations will be able to access the scope of detection content from this list according to their active subscription plan.
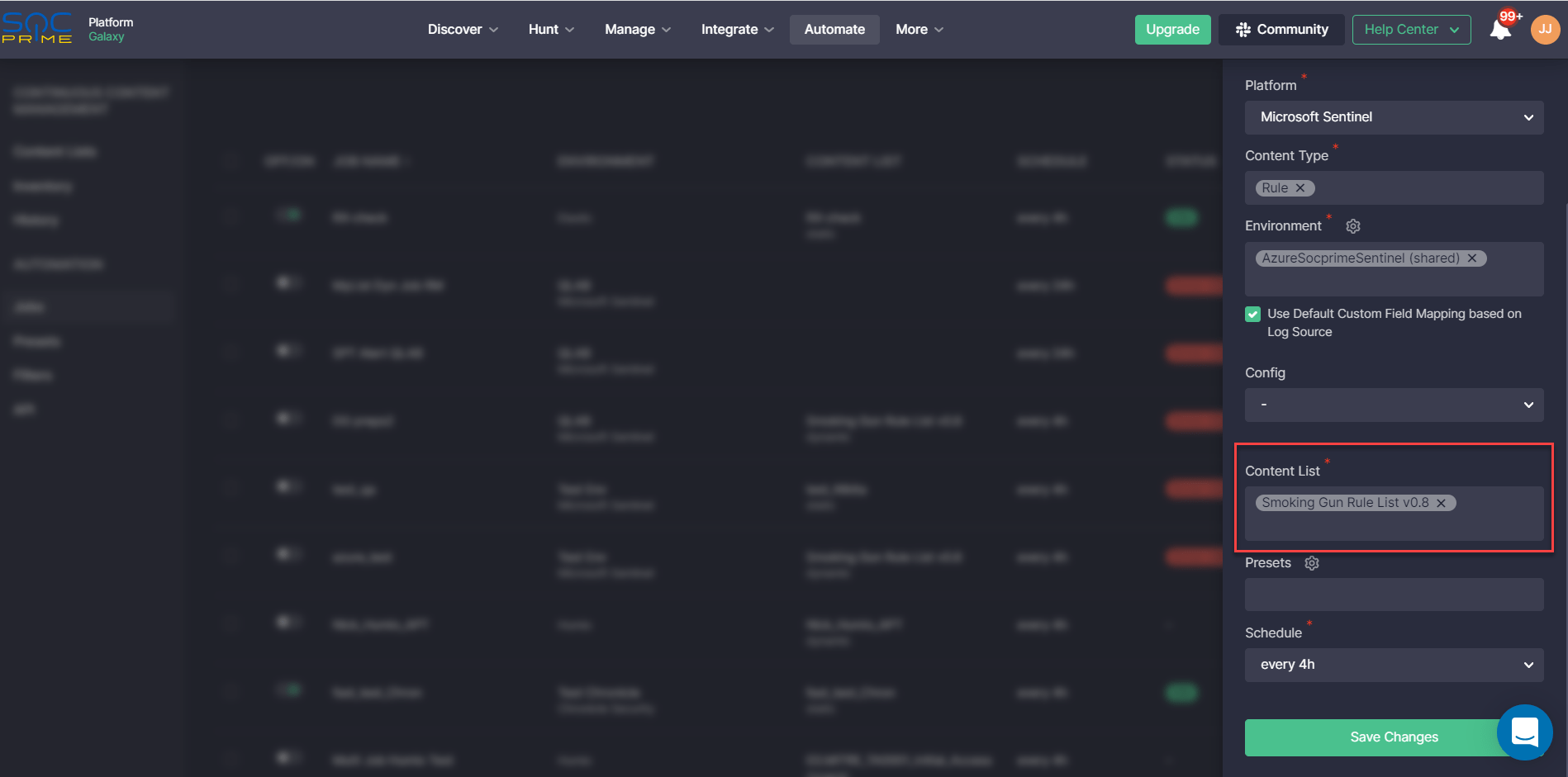
To create a Job linked to the dedicated content list that will be scheduled to run and automatically stream Sigma rule translations into the selected SIEM or EDR instance, take the following steps:
- Select Automate > Jobs.
- Click Create to configure a new Job.
- Provide a Job name.
- Select a platform to which you want to deploy detections, content type, and the specific environment.
- Select the Smoking Gun Rule List from the list of Content List options.
- Customize a deployment schedule if needed.
- For non-standard content deployments, you can select a Custom Field Mapping profile of your choice. By default, a standard profile will be applied based on log source products the corresponding detection content is intended for. Also, you can set up an alternative translation configuration by selecting one of the available options from the Config drop-down. For more details on how to configure and make the most of content customization capabilities, please refer to this blog article.
- Optionally, you can apply additional customization options, such as a rule name prefix/postfix or filters by linking a specific preset to this Job.
- Click Save Changes.
Join SOC Prime’s platform to reinforce cyber defense capabilities and constantly stay ahead of emerging threats with access to an immense collection of Sigma rules that can be used across 25+ SIEM, EDR, and XDR solutions. Cybersecurity experts can also instantly discover comprehensive contextual information on cyber threats accompanied by relevant Sigma rules using the industry-first search engine for Threat Hunting, Threat Detection, and Cyber Threat Intelligence.


