SOC Prime Platform Now Supports the MITRE ATT&CK® Framework v12

MITRE ATT&CK is a globally-accessible knowledge base leveraged by all cyber defenders no matter their role in cybersecurity and the technology stack in use. Acting as a periodic table, the MITRE ATT&CK framework enables cybersecurity experts to profile, identify, and compare threat actors, while setting priorities for threat detection goals. Leveraging MITRE ATT&CK, the global cyber defender community can retrospectively describe any common method used in cyber attacks.
To keep in sync with the latest framework updates and enhancements, SOC Prime has recently added support for the latest framework version — v12.
Collective Cyber Defense Powered by Sigma and MITRE ATT&CK
SOC Prime pioneered tagging Sigma rules with ATT&CK to enable teams to always get clear answers on what exactly to detect in their organization’s environment. By fusing ATT&CK and Sigma, SOC Prime has created a knowledge base of detection content enriched with comprehensive cyber threat context to enable cyber defenders to constantly stay in the know on emerging threats and obtain relevant detection algorithms against any TTP that was or will be used in a cyber attack.
Based on this latest ATT&CK release, we’ve added support for all new techniques and sub-techniques and made the corresponding updates to the existing Sigma rules according to the framework changes. All existing detection content available in the SOC Prime Platform is currently mapped to ATT&CK tactics, techniques, and sub-techniques reflecting the current changes introduced in v12.
According to the updates covered by the latest ATT&CK release, certain techniques have seen minor changes for more efficient threat investigation. For instance, the Enterprise Technique “Indicator Removal on Host” has been renamed to Indicator Removal (T1070) to better describe the malicious behavior in the cloud environments.
Due to an ever-increasing cyber threat landscape and the escalating threats of high-profile ransomware attacks, organizations are looking for new ways to proactively defend against impactful cyber incidents while strengthening the cybersecurity posture and enhancing the use of CTI. The use of MITRE ATT&CK as the common framework for all cyber defenders, which allows teams to break down adversary TTPs, can be considered one of the most actionable CTI tools. This latest framework release introduces detections for Industrial Control Systems (ICS), enabling industrial security practitioners to detect and remediate related threats more effectively and efficiently than ever before.
Insights Into SOC Prime Platform Updates Based on MITRE ATT&CK v12 Release
The current MITRE ATT&CK version of SOC Prime Platform fully supports 12 out of 14* MITRE ATT&CK tactics, 193 techniques, and 401 sub-techniques updated according to the latest MITRE release v12.
SOC Prime solutions reflect the corresponding framework updates, including the Sigma Rules Search engine, the MITRE ATT&CK view and Analytics dashboards in the SOC Prime Platform, and content mapping updates.
*The Reconnaissance tactic is also partly addressed in terms of threat detection by logs, therefore threat coverage in the SOC Prime Platform can be considered to involve up to 13 MITRE ATT&CK tactics.
Sigma Rules Search Engine: MITRE ATT&CK Visualization
The industry-first Sigma Rules Search Engine provides ideas for Threat Hunting, guidance for Detection Engineering, and CTI links along with MITRE ATT&CK mapping for enhanced threat reference and threat detection application. The MITRE ATT&CK visualization allows instantly viewing search results aligned with ATT&CK and drilling down to particular tactics and techniques most relevant to the organization’s threat profile. Cyber defenders can also choose to import or export the pre-configured ATT&CK Navigator file to customize their search for the most relevant adversary TTPs.

Content Search Based on MITRE ATT&CK in the SOC Prime Platform
The MITRE ATT&CK page accessible from the Content drop-down in the SOC Prime Platform breaks down the detection content search by adversary tactics, techniques, and sub-techniques. In addition to searching by content name, Threat Hunters, Detection Engineers, and SOC Analysts can sort the list of all detection algorithms mapped to the particular ATT&CK sub-technique by the content type (like Rule, Rule Pack, Config, etc.) or the detection content author.
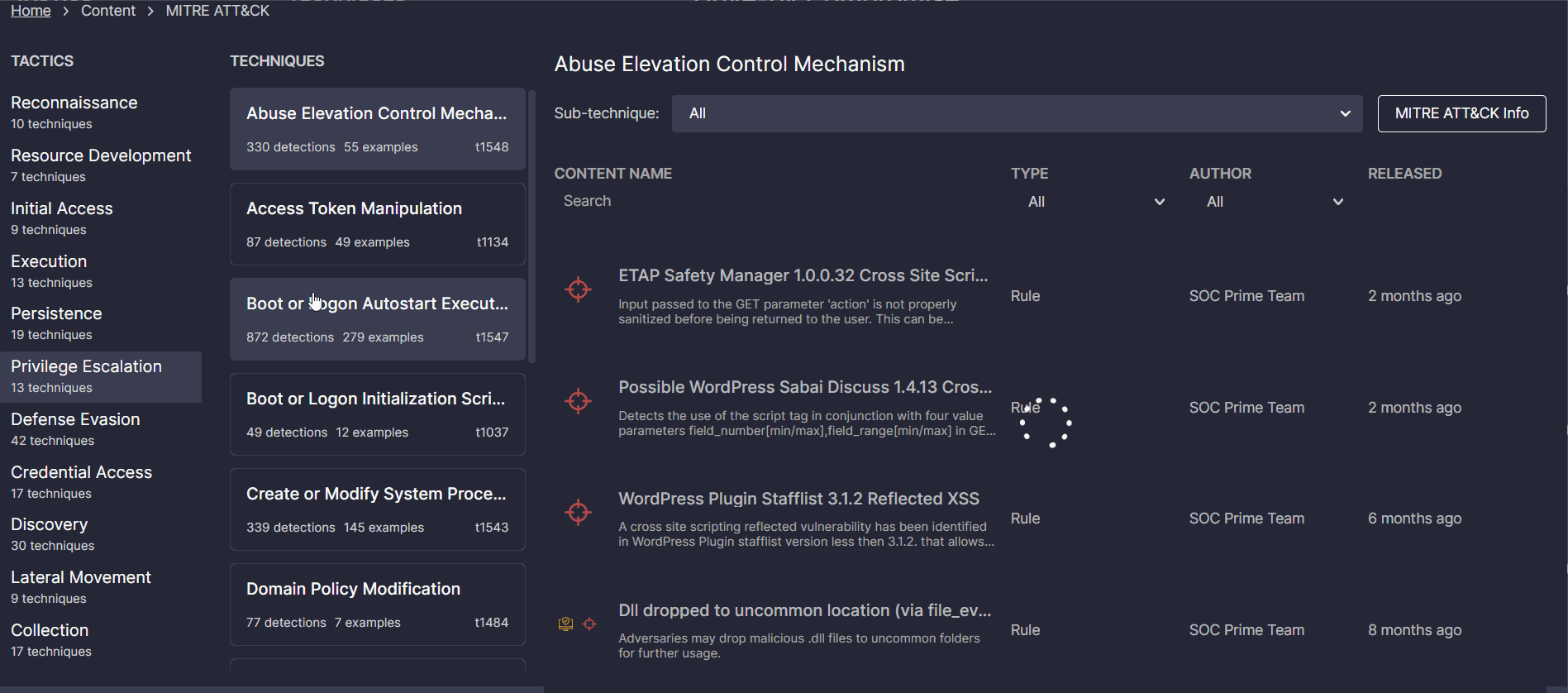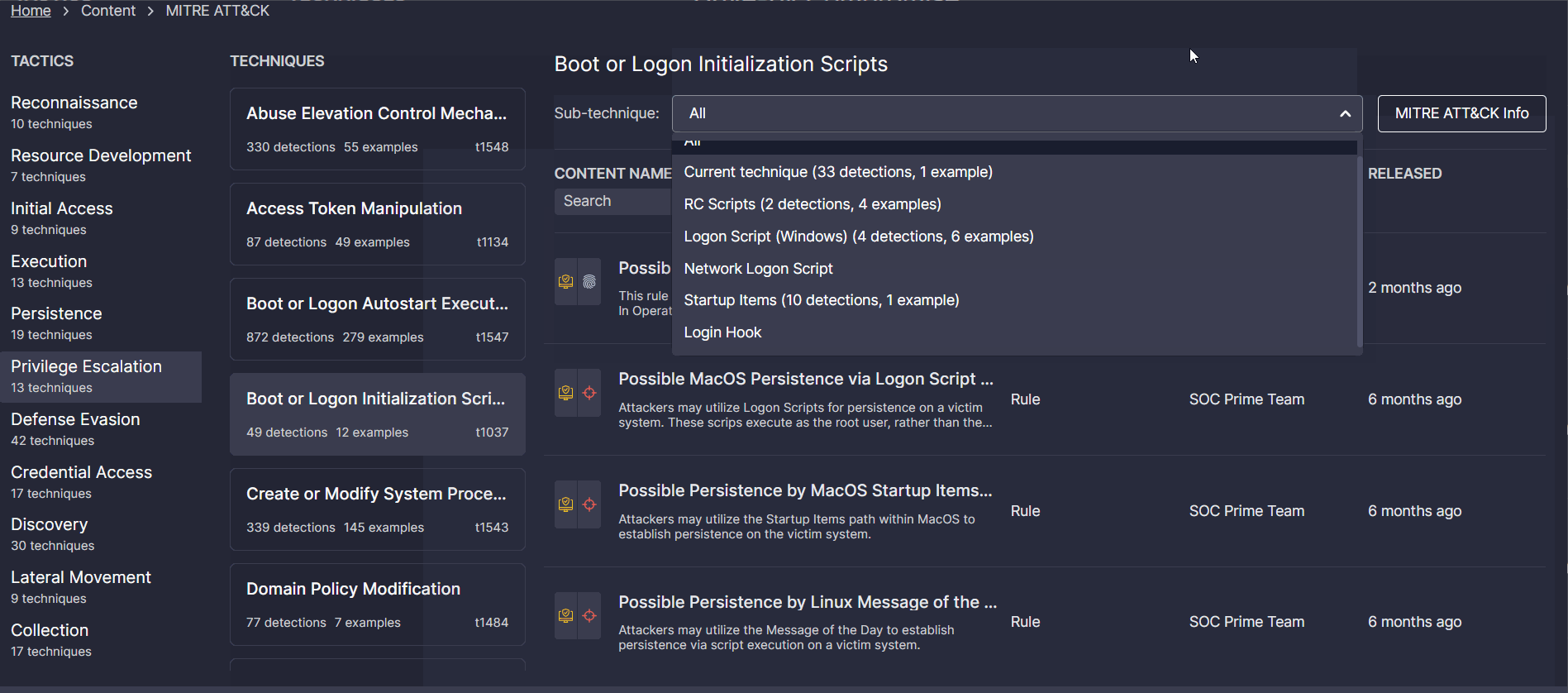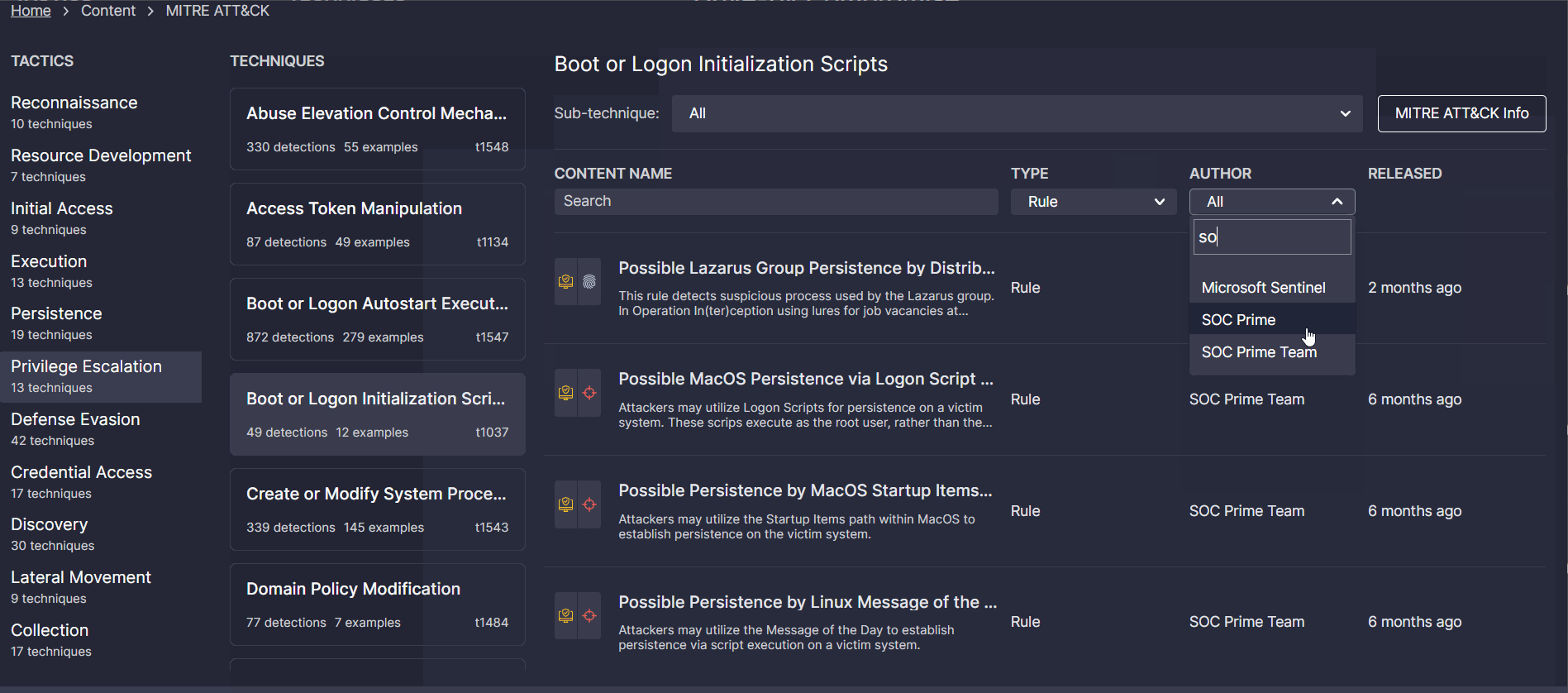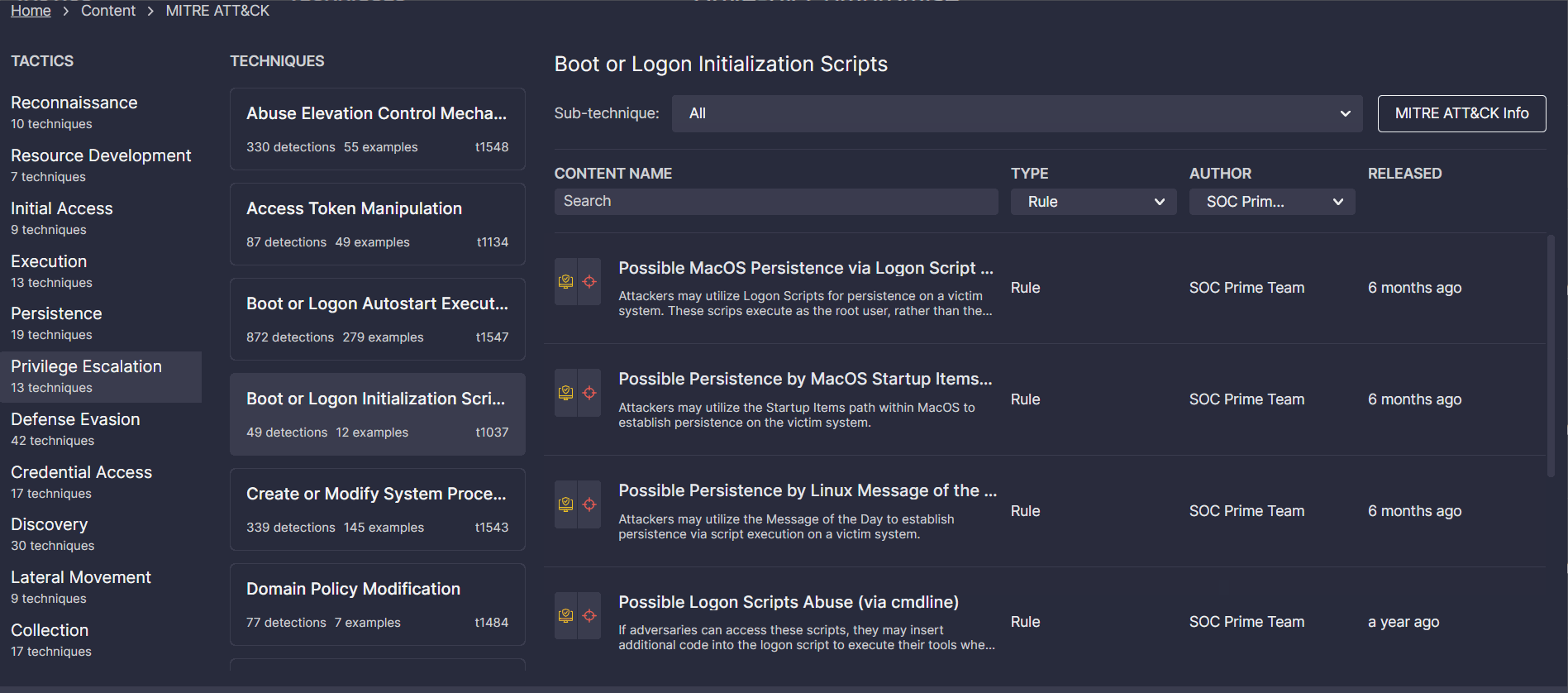
Analytics Dashboards
The MITRE ATT&CK Coverage dashboard, which displays the dynamics of threat coverage broken down by tactics, techniques, and sub-techniques, is currently updated to introduce all the framework changes in v12.
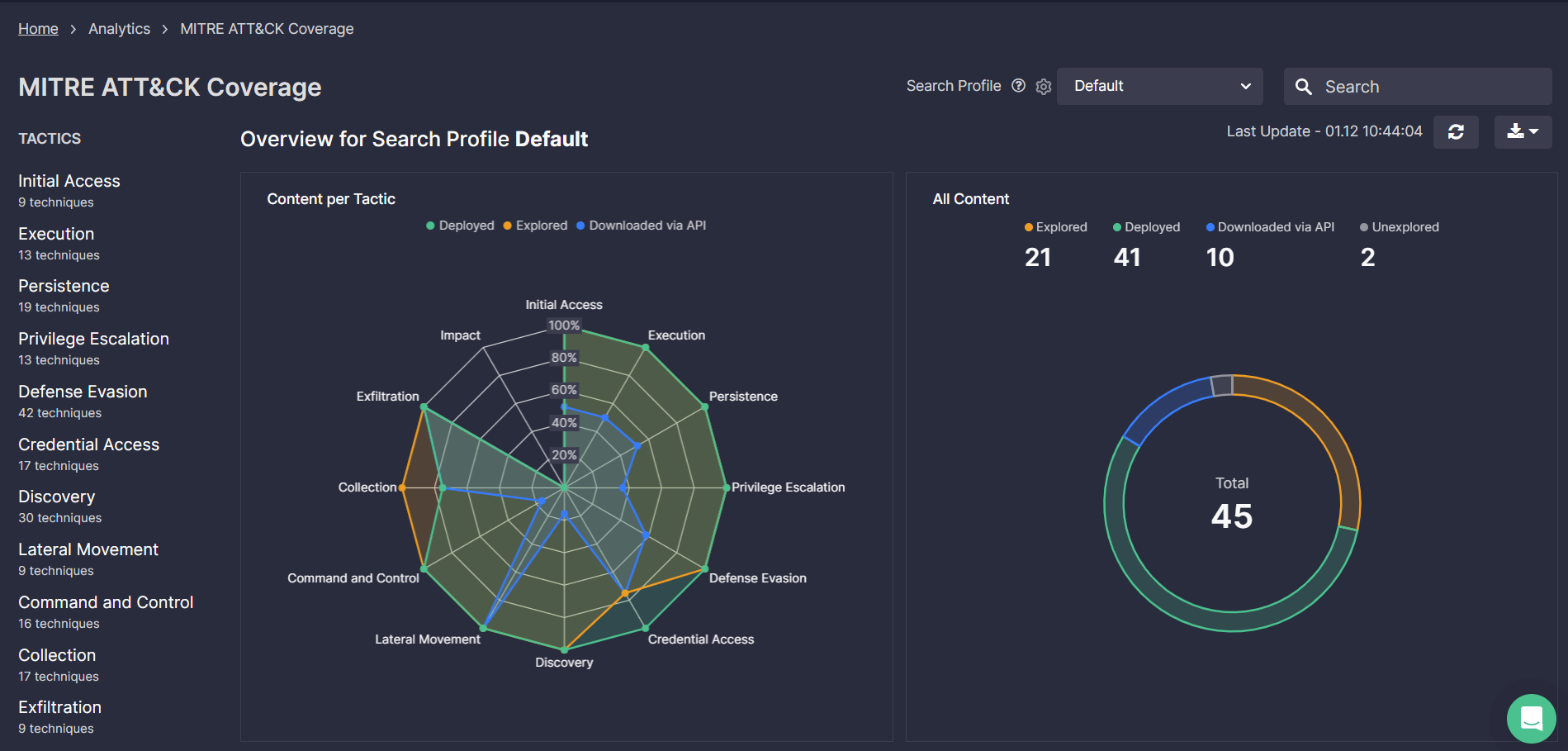
The Dashboard functionality displays the number of ATT&CK techniques, tools, and actors addressed over time based on detection content tagging enabling CISOs and SOC / IR Managers to assess the progress of threat detection and hunting capabilities benchmarked against industry peers.
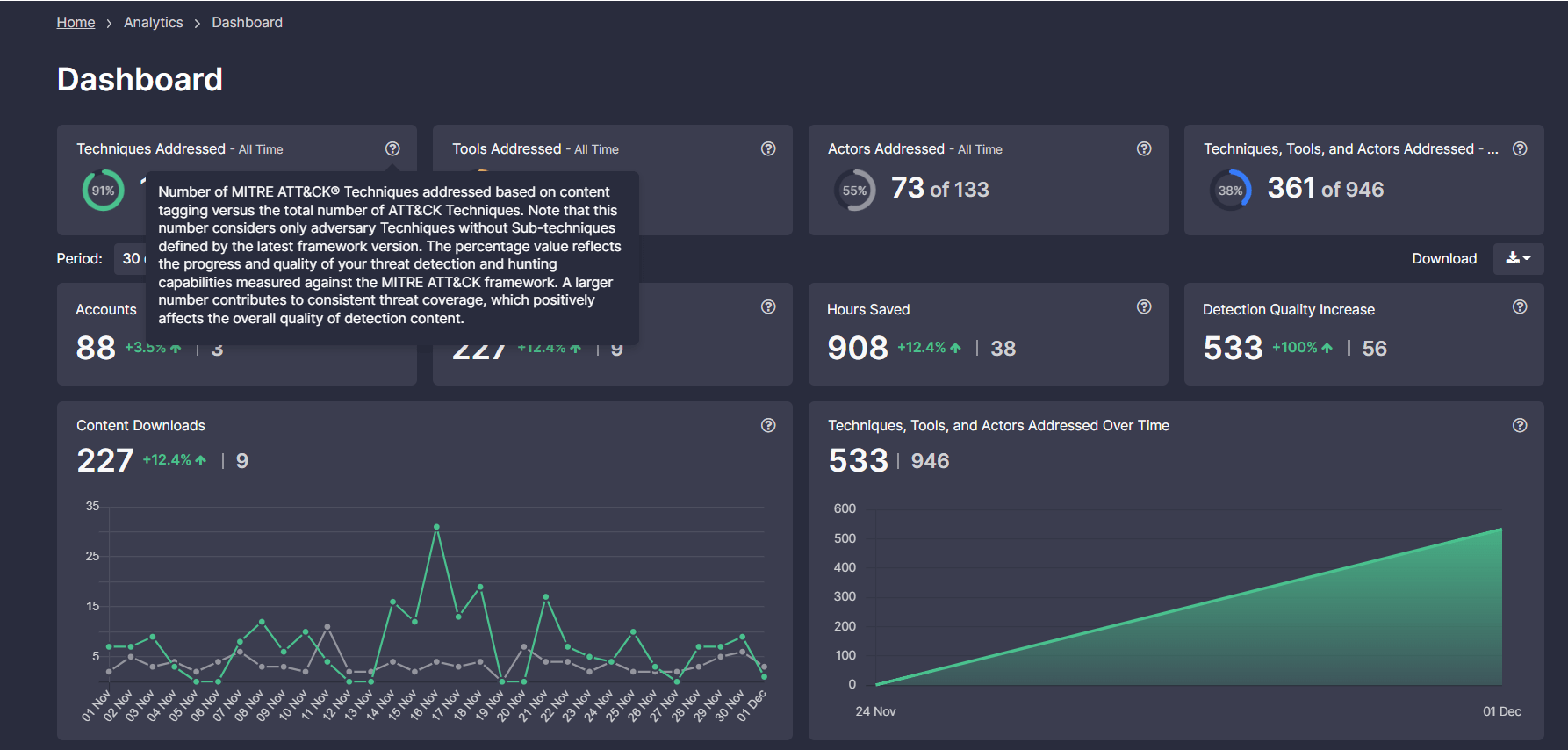
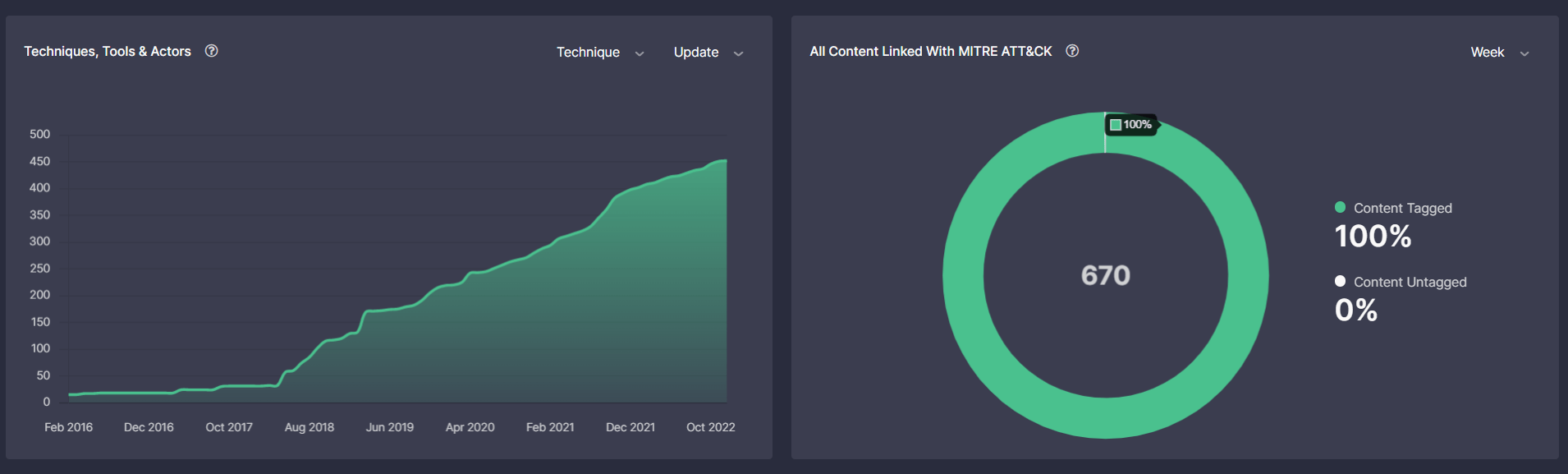
Leaderboards illustrate the growing trend of ATT&CK techniques in conjunction with sub-techniques, tools, and actors addressed over time based on the newly released MITRE ATT&CK v12. Also, here, cybersecurity professionals can view the total amount of detection content, including Sigma rules and their translations to 25+ SIEM, EDR, BDP, and XDR platforms mapped to the latest ATT&CK version as compared to unmapped content. The rising trend enables CISOs and Heads of SOC teams to assess the progress of improved threat coverage, which contributes to the overall detection content quality and helps boost the organization’s cybersecurity posture.
Threat Bounty Program: Detection Content Mapping Updates
SOC Prime’s Threat Bounty Program connects threat researchers globally to help the cybersecurity community proactively defend against emerging threats. Over 600 Program members contribute their curated Sigma rules to SOC Prime’s Threat Detection Marketplace on a daily basis while earning recurring rewards for making the world a safer place. With the latest platform updates introducing the latest MITRE ATT&CK release, all detection content submitted by Threat Bounty developers is mapped to v12 to ensure the highest content quality standards.
Looking for detection content addressing MITRE ATT&CK tactics, techniques, or tools that matter most? Explore 800 unique detections for Initial Access with 100 items available for free at https://socprime.com or reach the entire detection stack with On-Demand access.


