MITRE ATT&CK® is a framework for threat-informed cybersecurity defense and public knowledge base of adversarial tactics, techniques, and procedures (TTPs) based on real examples observed in the wild. It also includes a wealth of metadata such as possible detections, mitigations, data sources, platforms, system requirements, associated groups, references, and more. The ATT&CK content is published online and is usually updated 2 to 3 times a year.
Cybersecurity practitioners use a methodology of mapping certain pieces of information (code, intel, research) to the MITRE ATT&CK TTPs to facilitate threat analysis, detection, and response. It is possible to do that with the help of free tools that are available on GitHub. Getting acquainted with ATT&CK helps to strengthen an organization’s cybersecurity posture. For example, you might implement new device sensors, gaining greater visibility because otherwise, you won’t be able to track most TTPs at all.
ATT&CK also promotes the concept of collaborative cyber defense. Why is collaboration important? Let’s go back in time a little bit. Robert C. Martin described a “very strange behavior” of Log4j in his book “Clean Code.” That was in 2008! Imagine we had MITRE ATT&CK 14 years ago. Would we have all the Log4j drama in 2022?
MITRE ATT&CK and Behavioral Threat Detection
When it comes to security operations, behavioral threat detection became a game changer. ATT&CK is like a database of different adversary behaviors that is “good to know” to detect certain attacks. For example, if malware comes with a packer, it can re-encrypt itself hundreds of times, so looking for one particular hash is less than reasonable. Instead, if we see behavior like executing a command for adding a logon script as a registry value, we can find this behavior in the logs by creating a custom search query. Something like:
(index=__your_sysmon_index__ EventCode=1 Image=”C:\\Windows\\System32\\reg.exe” CommandLine=”*add*\\Environment*UserInitMprLogonScript”) OR (index=__your_sysmon_index__ (EventCode=12 OR EventCode=14 OR EventCode=13) TargetObject=”*\\Environment*UserInitMprLogonScript”)
(Source: CAR)
Using a behavioral approach gives SOC Analysts more flexibility and precision. As long as they can find the behavior, it doesn’t matter in which file it happens and if it is a file at all (e.g., API call).
What is MITRE?
While ATT&CK itself is a trademark, MITRE is a non-profit organization based in the US, with a subsidiary non-profit MITRE Engenuity.
With a preceding history of interesting Air Force projects, MITRE currently manages federally funded R&D centers. In addition to the ATT&CK framework, they have launched several helpful initiatives in the cybersecurity domain:
- MITRE Engenuity foundation and its Center for Threat-Informed Defense (23 ‘big player’ members)
- MITRE Cyber Analytics Repository
- National Cybersecurity Federally Funded Research and Development Center (NCF) sponsored by NIST
- CVE® Program
- CWE™ List
Now that we figured out what MITRE ATT&CK framework is, let’s review its building blocks and how to use them.
What is in the ATT&CK Matrix?
MITRE ATT&CK has a few matrices. A matrix is a visual representation of tactics and techniques that apply to a specific technical architecture. Below you will see a full list of matrices (at the time of publishing) with links to their respective online versions. Note that matrices continuously develop and update:
Every matrix can be edited locally by using a MITRE Navigator tool. SOC teams use it for mapping detections and mitigations to TTPs for the purposes of analysis, security operations, and management.
MITRE ATT&CK matrix gives an instant look at all TTPs that have been observed in a particular tech domain. So, instead of going for a long and tedious process of searching what attacks have been leveraged in the Cloud, just open a Cloud matrix and see them on a single screen. It’s not like TTPs not shown on the particular matrix will never happen on the given platform. For example, the whole Reconnaissance tactic belongs to the PRE matrix (pre-compromise), but it can occur on different kinds of software, firmware, and hardware.
ATT&CK vs. Cyber Kill Chain
When it comes to MITRE ATT&CK alternatives, another widely discussed framework is the Cyber Kill Chain® by Lockheed Martin.
Lockheed Martin is a global corporation that specializes in defense and space manufacturing. They also handle the development and deployment of software and DevSecOps infrastructures in government agencies.
Cyber Kill Chain is a sequence of steps that adversaries need to take to perform a successful cyber-attack. This framework is part of the Intelligence Driven Defense® (IDD) model designed for managing threat prevention, detection, and response.
Cyber Kill Chain looks like this:
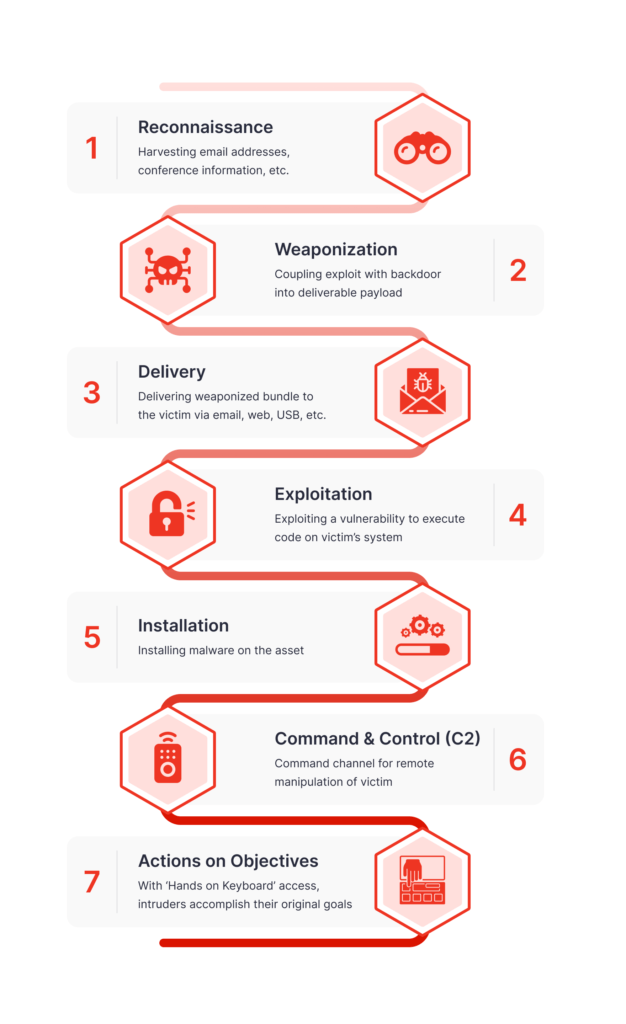
However, the Cyber Kill Chain model has been criticized for being malware- and perimeter-based. Plus, it implies a linear tactic where an attacker goes straight from A to Z. In real life, most attacks aren’t necessarily linear. That’s why Paul Pols developed a Unified Kill Chain with 18 Tactics. All in all, it looks like an “ATT&CK meets CKC” threat model:
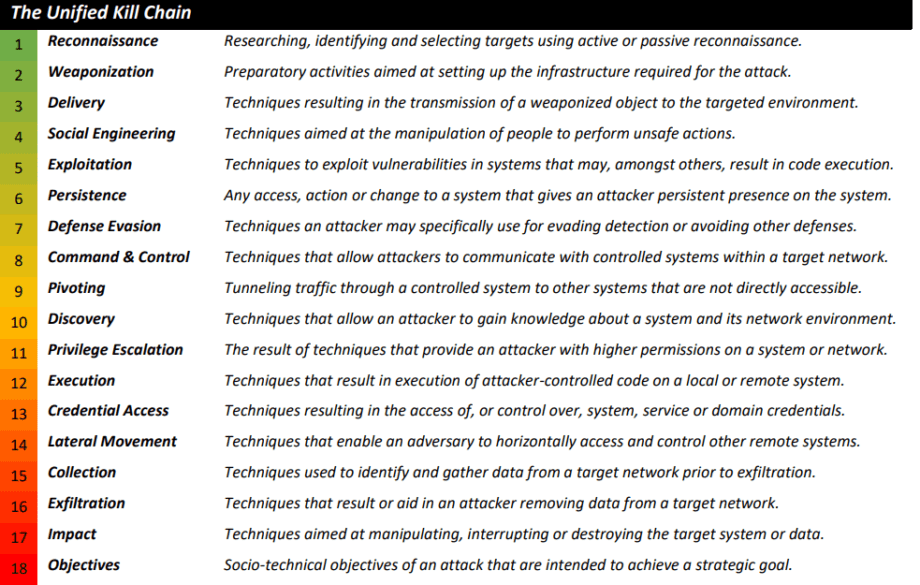
So which one to choose?
Lockheed Martin proposed an interesting approach of offense by defense, which suggest how to tactically defend at each stage of the kill chain. Meanwhile, MITRE made its framework a “living,” tangible tool that can be integrated into cybersecurity workflow. They do aggregate some vague technical Detections and Mitigations, but they don’t take the liberty of suggesting the overall defense approach.
Furthermore, while ATT&CK provides very thorough explanations of technical details, the Unified Cyber Kill Chain makes an attempt to embrace a strategic overview of the socio-technical objectives of adversaries.
As for the 18 Tactics against 14, it seems like most of them overlap. For example, Social Engineering in the form of Spearphishing is covered in ATT&CK’s Reconnaissance Tactic. And Pivoting is covered in T1572, Protocol Tunneling.
Perhaps, it would be best to follow the updates of both frameworks to be able to cover the widest possible range of cyber threats. Ideally, a SOC team should aim to cover three levels of defense: operational, tactical, and strategic.
What Are MITRE ATT&CK Tactics?
Tactics are the highest-level categories of the MITRE ATT&CK framework that represent the goals of cyber attackers and answer the question “why.” At the time of writing this article, the newest edition is vol. 11 (issued in April 2022), which includes 14 tactics in 3 domains: Enterprise, Mobile, and ICS.
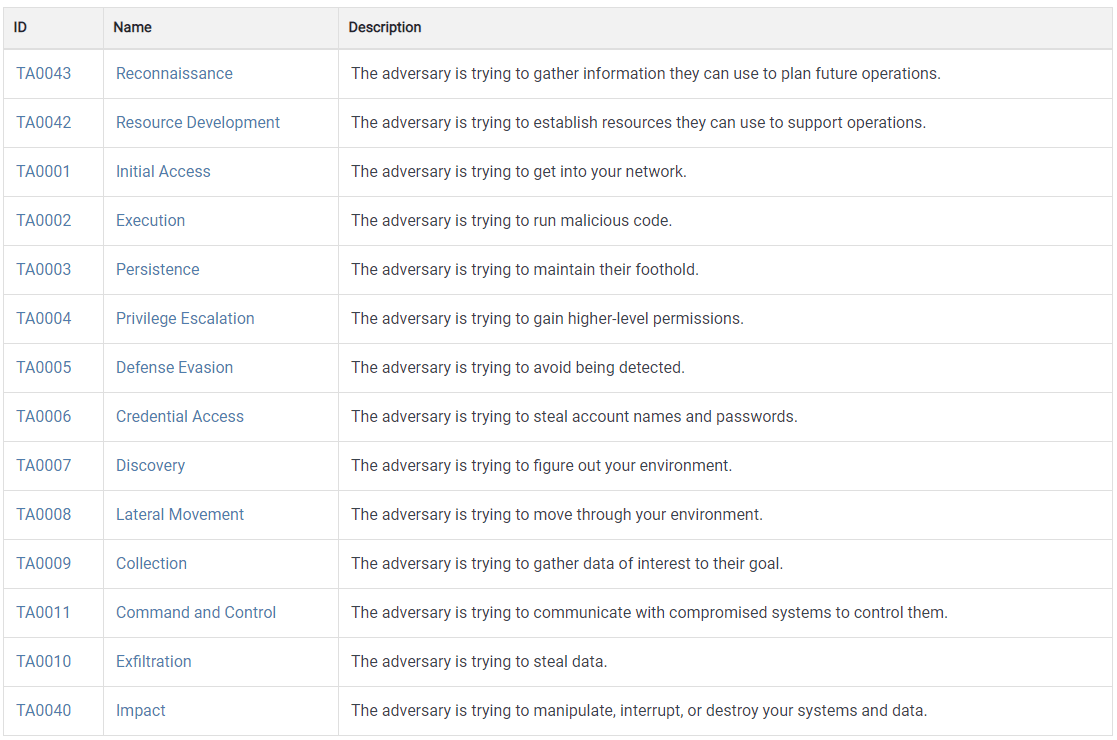
What Are MITRE ATT&CK Techniques, and How Many Are There?
Every Tactic consists of multiple Techniques. The current ATT&CK version comprises 191 Techniques that answer the question of “how” to achieve the tactical goal. These are particular actions like Access Token Manipulation, Hide Artifacts, etc. One Technique can belong to more than one Tactic. For example, Domain Policy Modification Technique may refer to both Defense Evasion and Privilege Escalation Tactics. You will see these relationships in an upper right window on a Technique page. Also, you’ll see there a lot of useful metadata, such as permissions required, defense bypassed, version history, contributor, mitigations, detections, and references.
What Are MITRE ATT&CK Sub-Techniques?
Sub-Techniques (385 in v.11) are smaller parts of Techniques that describe different ways of performing those Techniques. They are even more precise than Techniques and include low-level technical details. Sub-Techniques are enumerated as sub-categories of Techniques with direct dependencies. For example, a Sub-Technique T1548.003 Sudo and Sudo Catching is part of Technique T1548, Abuse Elevation Control Mechanism.
What Are MITRE ATT&CK Procedures?
On the Sub-Technique pages, you’ll see Procedures Examples with references to malware types and cybercriminal groups. Note that malware types and cyber-attack groups are enumerated, and each of them has its own ID, while Procedures don’t have their IDs.
Procedures describe particular cases of Sub-Techniques’ implementations that were observed in real attacks. Each Procedure may belong to more than one Sub-Technique/Technique since it’s a specific case of malware execution in the wild.
How To Use ATT&CK?
MITRE ATT&CK can be used by a SOC team in quite a few instances:
- Technical Controls
- Cyber Threat Intelligence
- Security Monitoring
- Threat Hunting
- Penetration Testing
- Threat Detection
- Malware Analysis
- Software Composition Analysis
- Administrative Controls
- GRC
- Budgeting
- Continuous Improvement
The threat-informed approach, leveraged by ATT&CK, gives a much-needed context to events that are happening on the enterprise’s network. Put simply, it’s useful in all three major stages: before the attack (proactive defense, risk management), during the attack (detection & response), and after the attack (recovery, reporting). Of course, here you might disagree: what if our organization has never been attacked before? Is it necessary to implement ATT&CK on all those levels?
The truth is, even if all the necessary multi-layer defense is in place, there is always a residual risk. So risk assessment and policy should go first and define a range of relevant cybersecurity controls. Good news is that ATT&CK seamlessly integrates into various types of enterprise-level cyber software so that SOC teams can integrate a few points from the above list within one solution.
Here’s the list of helpful tools for ATT&CK and beyond, created by MITRE:
- ATT&CK Navigator
- ATT&CK Python Tools
- ATT&CK Workbench
- CALDERA™ Adversary Emulation Platform
- CASCADE server
- GitHub repos:
Explore SOC Prime’s Cyber Threats Search Engine to instantly find in-depth cyber threat information, including CTI context and comprehensive MITRE ATT&CK references. Click the Explore Threat Context button below to reach the search results for trending CVEs, APTs, and exploits enriched with contextual metadata and accompanied by relevant Sigma rules.
On a strategic level, frameworks like ATT&CK help to move towards achieving a more resilient cybersecurity posture while organizations are trying to withstand the growing pressure of APT attacks and their malicious socio-economic objectives. Structured analysis and threat-informed approach provide valuable information for a continuous improvement or realignment of cyber-defense strategies.
MITRE Engenuity Initiatives
MITRE ATT&CK is an ever-growing framework. So, how do they evolve? With MITRE Engenuity nonprofit foundation, the ATT&CK evolution goes beyond a passive study of publicly open threat research. Engenuity works with the private sector and already has 23 high-profile enterprise members.
About two years ago, the foundation launched a Center for Threat-Informed Defense, which hosts a regular series of purple-team sprints called ATT&CK Evaluations. The project provides free downloadable emulation plans on GitHub. Each organization performs its own emulation and analysis of a given threat (MITRE Engenuity doesn’t rank the results in any way). The research results of each participant are published on this website.
The thing is, every Technique can be executed by attackers in multiple Procedures, and in turn, every Procedure can employ a custom mix of Techniques. Each actor may also alter their procedures as a response to new detections. That’s why different vendors who perform the same research in their own environments bring tons of valuable information.
Another interesting initiative of MITRE Engenuity is the MITRE ATT&CK Defender™ (MAD) training and certification program. There is only one fee that unlocks a year of full access to a MAD Skills Hub. MAD encourages Security Practitioners to continuously update their skills to fight emerging threats. That’s why their on-demand and live training regularly present new learning opportunities. Consequently, if you earned a badge once, you’ll need to renew it as soon as the threat landscape changes.
FAQ: The ATT&CK Framework and SOC Prime’s Detection as Code Platform
Let’s quickly cover a few questions on using the ATT&CK with the SOC Prime platform.
Why Should I Use ATT&CK TTPs in SOC Prime Detection as Code Platform?
Mapping cybersecurity efforts to ATT&CK helps to cover the widest range of possible threats within the shortest timeframe. And it’s no secret that both blue team and red team members have a lot on their plates. Mapping to ATT&CK and analyzing the results becomes much more straightforward if doing it on SOC Prime’s Detection as Code platform.
It is possible to use ATT&CK on our platform in quite a few ways:
- Detection content search
Use Cases: reducing MTTD, preventive controls
- Exploration and analysis of threat context
Use Case: performing Threat Hunting
- Performance analysis
Use Case: assessing the effectiveness of the SOC team
- Tools & services assessment
Use Case: excluding an open-source tool from a supply chain because it would take too much time & effort to secure (number of SOC Prime rules + TTPs to cover)
- Vendor migration or product overlap
Use Case: providing threat coverage across software solutions that the company currently uses. For example, Splunk + Crowdstrike + Securonix
- Risk management
Use Cases: providing threat profile analysis & updates, gap analysis, etc.
- SOC ROI assessment
Use Case: evaluating the work done and comparing it to the time and money spent
- Internal security audit
Use Cases: managing regulation compliance, mergers & acquisitions, etc.
How to Use MITRE ATT&CK Framework in the SOC Prime’s Detection as Code Platform?
Use the following paths once logged into the SOC Prime’s Detection as Code platform:
Analytics > Advanced Search or Detection Engineering
- Use filters to search for detection rules and queries mapped to specific tactics, techniques, sub-techniques, actors, tools, data sources, or data components.
Analytics > MITRE ATT&CK Coverage
- Analyze TTPs covered by SOC Prime’s detection content that your team has explored, deployed, or downloaded via API.
- Click Export to export the TTPs coverage defined by a current Search Profile into MITRE Navigator. You can also click Import when creating a Search Profile to import a Navigator layer that you have already been using.
Automate > Search Profiles > Create > Technique
- Easily manage lists of TTPs along with other parameters in a Search Profile
Content > MITRE ATT&CK
- Search detection rules, configs, and content packs by TTPs.
Content > Advanced Search > [Rule Name] > Intelligence > MITRE ATT&CK
- Explore TTPs covered in a particular content piece.
It is possible to review not only your own analytical efforts but also those of your team. Configuring automation and reporting might take some time at first, but once it’s done, using ATT&CK-mapped detections will be much easier and faster.
Can SOC Prime Users Gain Insights Into MITRE ATT&CK Context Without Registration?
Yes.
Go to SOC Prime’s Cyber Threats Search Engine and search for detection content of your interest. You can search by typing TTPs, CVEs, threat actors, log sources, names of malware strains, software products, and much more. Once you see search engine results, you can narrow them down by using filters on the left side of the screen and at the top.
Switch on the MITRE ATT&CK® view toggle to sort the results by TTPs. In the top right corner of the screen, you will see two icons – Export and Import of JSON files to and from the ATT&CK Navigator. Using them is super easy! One click – and you’re on Navigator, exploring the detection content search results on a MITRE ATT&CK matrix. Two clicks – and you’ve imported the TTPs from your Navigator layer and see all the detections relevant to your selection. However, the actual use of those detections in your SOC environment is only possible if you’re registered at the SOC Prime’s Detection as Code platform.
Conclusion
MITRE ATT&CK is many things. It’s a beauty of perfectly ordered data. It’s about enhanced abilities to collaborate. Strategic moves. Even more so, it’s about a philosophy of clean architecture, often used in coding, where the business logic doesn’t depend on particular tools. In a cybersecurity context, the logic of a single detection is transferable across a variety of different security layers as well as horizontally equal solutions, tools, and formats.
By making the Adversary Tactics, Techniques, & Common Knowledge (ATT&CK) free and open, MITRE Corp. facilitates a collaborative threat defense approach, bringing together communities, the private sector, and the government. Enumeration and explanation of every cyber-attack move give an opportunity to implement new methodologies and threat models, automate processes and effectively analyze threats.
Improve your threat detection coverage with on-demand Detection-as-Code content mapped to MITRE ATT&CK. Choose the On-Demand subscription plan and obtain customized detection content aligned to your cyber defense to proactively defend against emerging threats.




