SOC Prime Cyber Threats Search Engine Now Includes Comprehensive MITRE ATT&CK® Visualization

Table of contents:
Instantly Explore the Latest Trends and Adjust Search Results to Illustrate ATT&CK Tactics and Techniques Most Relevant to Your Threat Profile
SOC Prime recently released the industry-first search engine for Threat Hunting, Threat Detection, and Cyber Threat Intelligence allowing InfoSec professionals to discover comprehensive cyber threat information including relevant Sigma rules instantly convertible to 25+ SIEM, EDR, and XDR solutions. The free tool provides in-depth cyber threat information and relevant context with sub-second search performance.The tool has been enhanced to include comprehensive MITRE ATT&CK mapping to enhance threat reference and threat detection application. SOC Prime pioneered the tagging of Sigma rules with MITRE ATT&CK reference to originally attribute detection content for NotPetya ransomware for the infamous Sandworm APT. SOC Prime significantly contributed to evolving this initiative into a powerful open-source tool to assist security professionals with proactive Threat Hunting.
SOC Prime’s search engine, used in conjunction with its Detection as Code platform, streamlines threat detection operations by serving as an instant source of Sigma rules and relevant contextual information, including MITRE ATT&CK references, attack trends visualization, and threat intelligence insights.
Getting Informed on the Latest Threats
SOC Prime harnesses the power of global industry collaboration by aggregating threat detection content from SOC Prime Team, the open-source Sigma community, and crowdsourced Threat Bounty Program developers. Leveraging this extensive pool of knowledge and capability, progressive organizations can boost threat detection and hunting velocity.
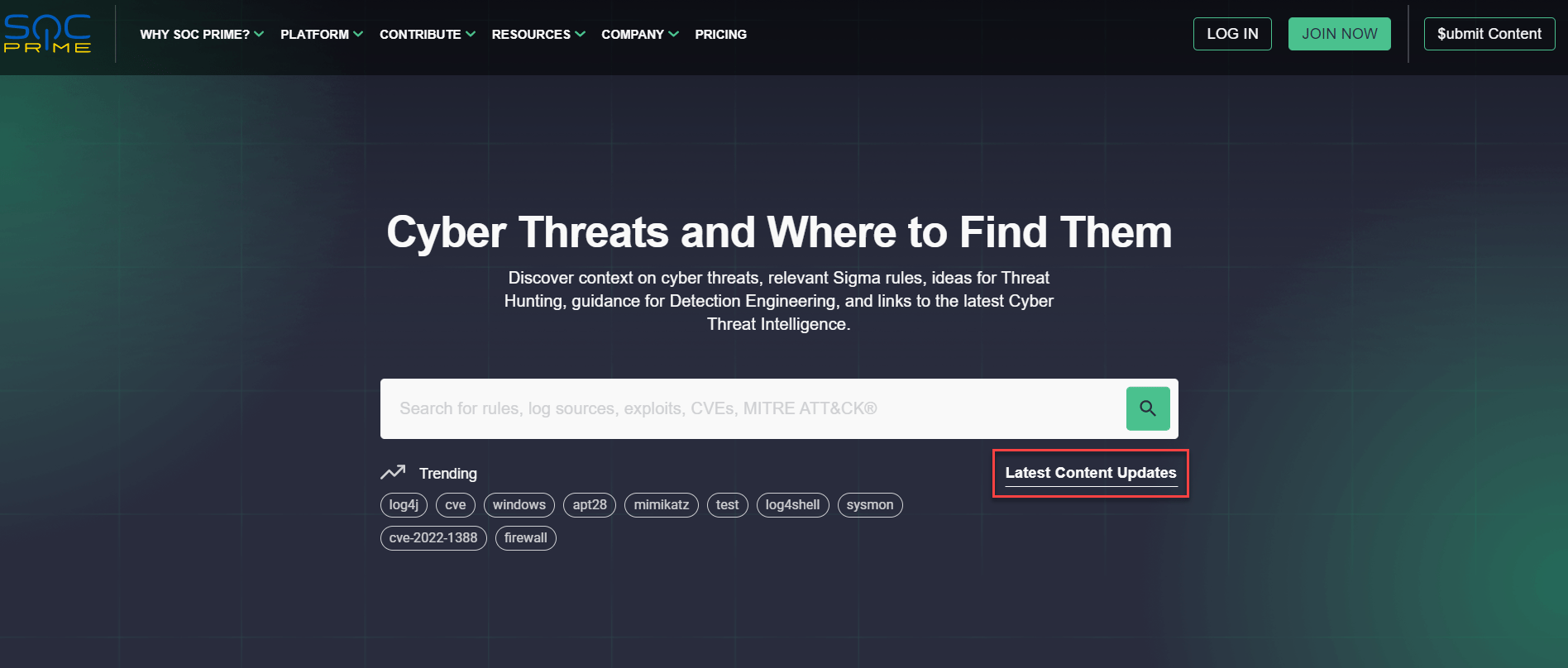
To keep track of the dynamically changing attack surface, the cyber threats search engine includes recommendations intended to ensure cybersecurity experts have instant access and information on recent threats.
The search engine by default displays trending results for CVEs, exploits, APT, or other threats that are currently in the spotlight in the cyber threat arena. To drill down to the search results based on the corresponding trend, select this item from the recommended list of options below Trending. By clicking the Latest Content Updates, security practitioners can instantly reach the most recent detection content released over the last month enabling them to proactively defend against emerging threats.
MITRE ATT&CK Insights
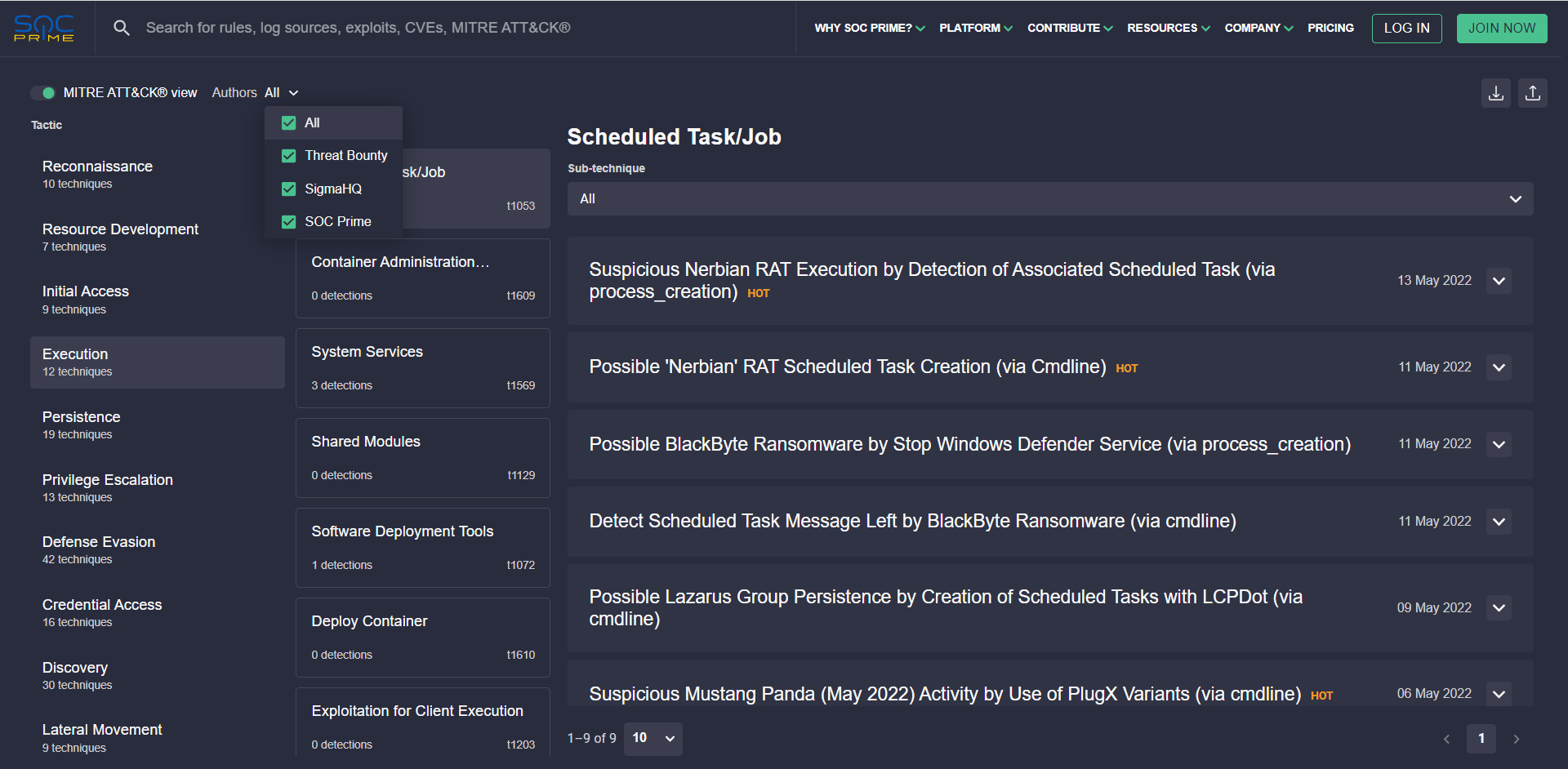
Security practitioners can also switch to the MITRE ATT&CK view to see search results aligned with the MITRE ATT&CK framework and drill down to the tactics and techniques relevant to their organization’s threat profile. In addition, the search engine allows filtering of relevant Sigma rules matching the applied ATT&CK parameters by the corresponding content authors:
- Threat Bounty — crowdsourced detections developed by the Threat Bounty content contributors
- SOC Prime — rules crafted by the SOC Prime Team
- SigmaHQ — content from the open-source Sigma rules repository
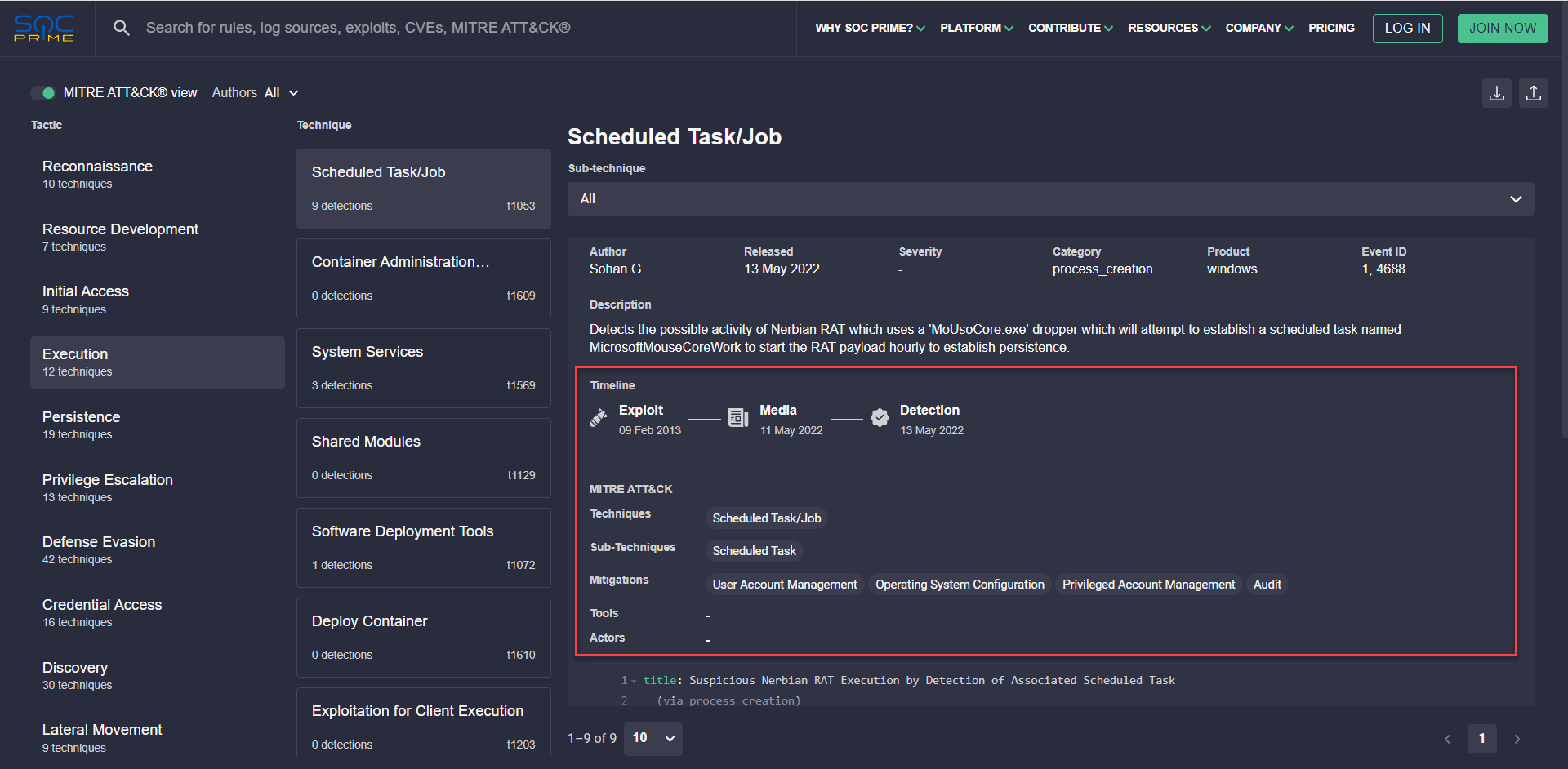
Similar to the threat context that accompanies a Sigma rule, the search engine also provides the timeline covering the MITRE ATT&CK context, including:
- The exploitation of the selected technique
- CVE references
- Available Threat Intelligence
- Media links and more relevant metadata
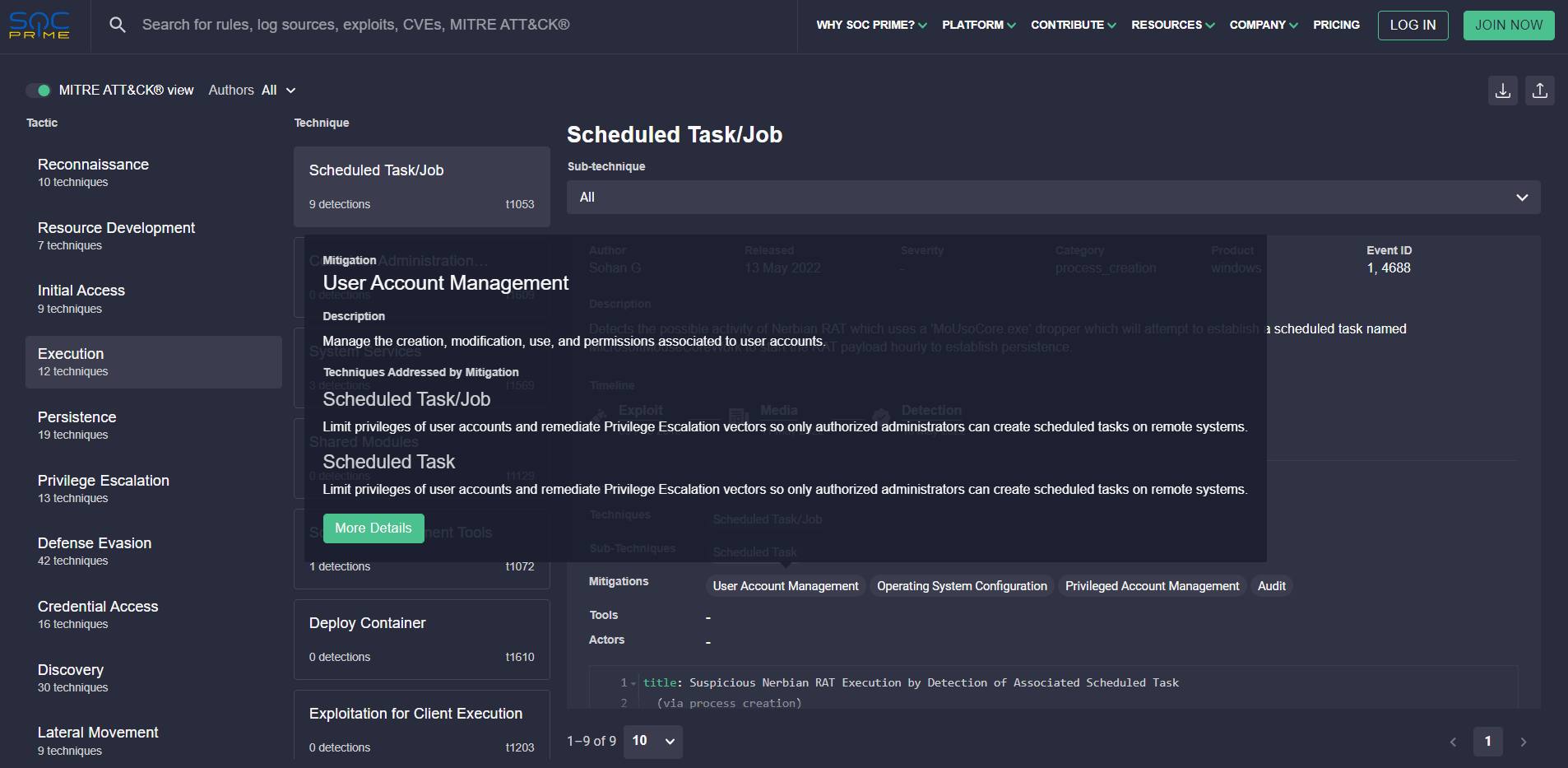
Threat Hunters, Cyber Threat Intelligence experts, and Detection Engineers can also instantly drill down into details to thoroughly explore the suggested technique Mitigation and the corresponding ATT&CK reference.
Drilldown to ATT&CK Navigator Tool with a Single Click for at-a-Glance Filtering
Teams can also filter the search engine results using the selected tactics and techniques from the corresponding ATT&CK Navigator JSON file. Security practitioners can drill down to the ATT&CK Navigator tool with a single click to view the addressed techniques and sub-techniques, as well as instantly export and import the pre-configured JSON file.
SOC Prime’s search engine enables streamlined threat discovery along with comprehensive details and filters to retrieve relevant metadata on curated Detection-as-Code content from SOC Prime’s platform enriched with MITRE ATT&CK reference to instantly receive curated Sigma rules appropriate for any organization’s unique security needs.