The popularity of cryptocurrencies doesn’t only attract investors but also makes them a true honeypot for hackers. While crypto has seen some better times in the market, cryptojacking is on the rise. With a variety of terms emerging, it is easy to get lost. So, let’s dive into the specifics of crypto malware, crypto ransomware, and cryptojacking.
Crypto malware definition comes down to a specific type of malicious software aimed to perform illegal mining (cryptojacking). Other names for crypto malware are cryptojackers or mining malware. If you are new to these concepts, feel free to check the glossary of the related terms:
Glossary:
- Cryptocurrency is a digital currency powered by blockchain technology.
- Cryptomining (aka cryptocurrency mining) is a process of creating new coins and validating new transactions. It is conducted by solving complex equations using highly powerful machines.
- Cryprojacking is criminal crypto mining, defined as unauthorized access to and usage of crypto mining resources.
Crypto malware was first discovered when a member of the Harvard community started mining dogecoins using the ‘Odyssey cluster’ in 2014. Since then, cryptojackers made a long way to become one of the most significant cybersecurity concerns. You might treat cryptojacking as another buzzword, but statistics show an 86% increase in illegal crypto mining incidents – 15.02 million per month in 2022 compared to 8.09 million per month in 2021.
How Does Cryptojacking Malware Work?
Even though crypto malware forms a separate group of malicious software, it still acts similarly to most other malware types. The primary infection vector is malware distribution through botnets, mobile apps, web pages, social media, or phishing. When the victim’s machine opens a malicious file, codes are executed via Macros or JavaScript to install the crypto malware.
How is Crypto Malware Different From Other Malware Types?
The main distinction is that instead of corrupting data directly, crypto malware uses the GPUs and other resources of the victim’s machine for mining while running inconspicuously in the background.
Crypto Malware vs. Crypto Ransomware
Firstly, remember that these terms aren’t related, even though they have a ‘crypto’ part in common. Crypto malware is related to cryptojacking (illegal mining of cryptocurrencies), while crypto ransomware has nothing to do with cryptocurrencies. Crypto ransomware is one of the ransomware types. The most popular ransomware varieties are:
- Locker Ransomware blocks basic functions of the victim’s device, such as a partially disabled mouse or keyboard and denied access to a desktop.
- Crypto Ransomware is the one that encrypts files leaving you without access to them. This type of ransomware is the most common because it is generally associated with more damage.
What unites all ransomware variants is the ransom adversaries demand to recover access to either files or devices. So, as you see, crypto malware’s primary mission is to use the victim’s computer resources for as long as possible without being noticed. In contrast, ransomware (including crypto ransomware) has a different purpose – money paid as a ransom.
How to Detect Crypto Malware
Even though the volume of crypto malware attacks is getting higher, you can still ensure timely detection if you follow these recommendations:
Know Your Infrastructure
Aim to find the vulnerabilities in your systems before adversaries do. Besides that, you should also understand what performance is normal for your infrastructure. This way, if you start receiving help desk tickets about slow performance or overheating, you will know that those are red flags to investigate.
Monitor Your Network
To be aware of what’s happening in your infrastructure, you should constantly collect quality logs and analyze them properly. An excellent start would be learning more about data sources and data analysis. Here you can find detailed explanations with real-world examples.
Have Your Coverage in Place
Collecting logs is important but what’s even more important is what logs you are collecting. You can’t cover all the possible attack vectors, but if you know how the kill chain works, you will have a clearer understanding of what to look for. Start by understanding the MITRE ATT&CK® framework to improve your threat analysis, detection, and response.
Leverage Threat Hunting
While Threat Hunting might seem overwhelming at first, it is one of the most effective ways to search for traces of stealthy threats, such as crypto malware itself. A proactive approach in terms of threat detection is what can save you money, time, and reputation. If you don’t know where to begin, check our guide on Threat Hunting basics.
Opt for Behavior-Based Detections
While IOC-based detections can be helpful in some cases, they are generally considered ineffective at detecting unknown malware. At the same time, behavior-based detections proved to be much more practical as they search for patterns that can be reused in different attacks. You can significantly improve your SOC operations by implementing proactive defense against cyber threats with context-enriched detections.
If you want to learn more about crypto malware and its detection, check the following studies:
- Caprolu, M., Raponi, S., Oligeri, G. and Di Pietro, R. (2021). Cryptomining makes noise: Detecting cryptojacking via machine learning. Computer Communications. Available at: https://doi.org/10.1016/j.comcom.2021.02.016
- Zheng, R., Wang, Q., He, J., Fu, J., Suri, G. and Jiang, Z. (2022). Cryptocurrency Mining Malware Detection Based on Behavior Pattern and Graph Neural Network. Security and Communication Networks, 2022. Available at: https://doi.org/10.1155/2022/9453797
- Bursztein, E., Petrov, I. and Invernizzi, L. (2020). CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks. Google Research. Available at: https://research.google/pubs/pub49278/
- cybersecurity.att.com. (n.d.). Crypto miners’ latest techniques. Available at: https://cybersecurity.att.com/blogs/labs-research/crypto-miners-latest-techniques
- Hernandez-Suarez, A., Sanchez-Perez, G., Toscano-Medina, L.K., Olivares-Mercado, J., Portillo-Portilo, J., Avalos, J.-G. and García Villalba, L.J. (2022). Detecting Cryptojacking Web Threats: An Approach with Autoencoders and Deep Dense Neural Networks. Applied Sciences, 12(7). Available at: https://doi.org/10.3390/app12073234
- Eskandari, S., Leoutsarakos, A., Mursch, T. and Clark, J. (2018). A First Look at Browser-Based Cryptojacking. 2018 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). Available at: http://dx.doi.org/10.1109/EuroSPW.2018.00014
What is the Impact of Crypto Malware Attacks?
Depending on each case, the impact of a cryptojacking attack can be different. Still, the most typical consequences to the affected devices and networks are:
- Slower network and system performance due to the usage of CPU and bandwidth resources by illegal crypto mining activity
- High power consumption, any physical damage, or system crashes because of the hardware overheating
- Unordinary disruptions of routine operations
- Financial losses related to increased power consumption and the downtimes caused by any of the previously mentioned damages. Additionally, there can be a cost of recovering files and systems
- Reputational and compliance risks due to unauthorized access to the network
What are the Most Severe Crypto Malware Examples?
In the past years, there have been numerous cryptojacking attacks, giving endless opportunities to analyze relevant cases and prepare to prevent future attacks. Let’s dive deeper into some of the most notable cases.
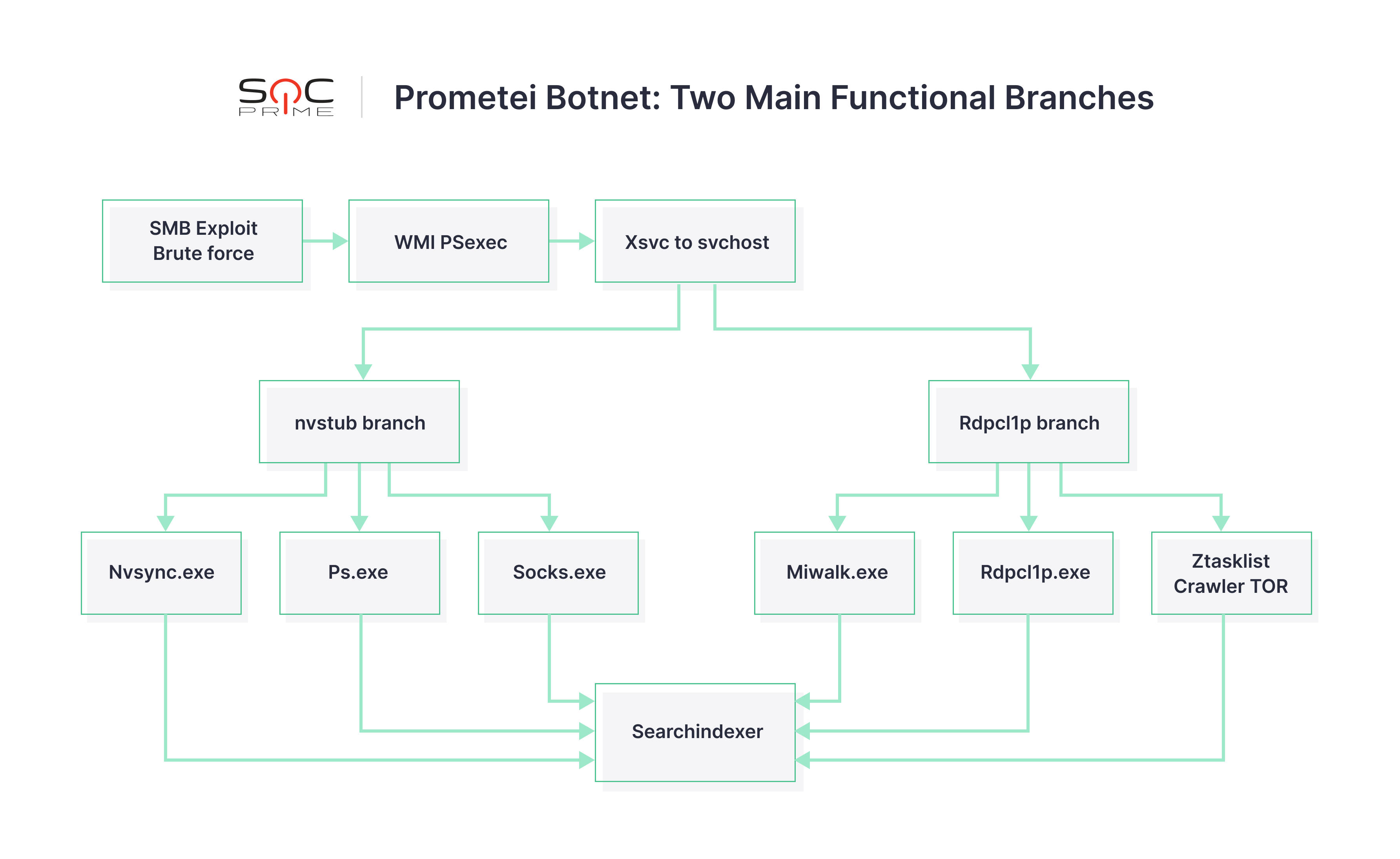
Prometei Botnet
Prometei is a multi-stage crypto malware botnet discovered in 2020, targeting both Windows and Linux systems. Prometei uses various techniques and tools to spread across the network achieving the ultimate goal of mining Monero coins.
The infection begins when the primary botnet file is copied from an infected system via Server Message Block (SMB), with the usage of passwords retrieved by a modified Mimikatz module and well-known exploits such as BlueKeep and Eternal Blue.
Researchers followed the activity of the Prometei botnet for over two months and found that the malware has more than 15 executable modules arranged in two main operational branches that can perform rather independently. Below you can see the graphical representation of how the modules are organized. For a more detailed technical overview, check this analysis.
As for the MITRE ATT&CK framework techniques, adversaries actively used the following:
- T1562.001 (Impair Defenses: Disable or Modify Tools)
- T1105 (Ingress Tool Transfer)
- T1027 (Obfuscated Files or Information)
- T1059.001 (Command and Scripting Interpreter: PowerShell)
- T1569.002 (System Services: Service Execution)
- T1036 (Masquerading)
- T0884 (Connection Proxy)
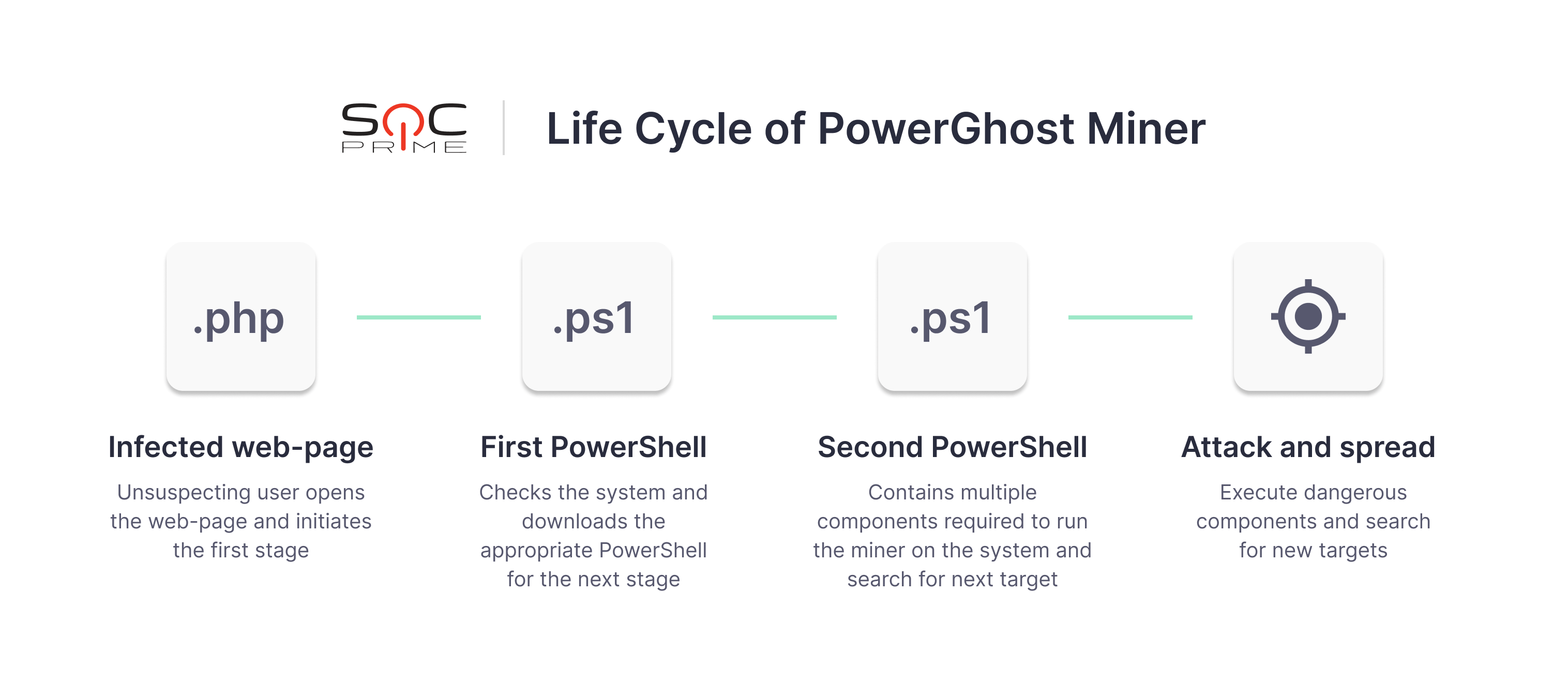
PowerGhost
PowerGhost miner is a fileless malware that uses multiple techniques to remain undetected by antivirus solutions. This malicious software owes its name to the silent behavior of embedding and spreading across the network. Without creating new files on the system and writing them into the hard drive, the Powershell script runs out of sight, infecting systems with a combination of Powershell and EternalBlue.
To gain access to remote accounts, PowerGhost leverages mimikatz, EternalBlue, or legitimate software tools, such as Windows Management Instrumentation (WMI). Essentially, PowerGhost malware is an obfuscated PowerShell script with the following structure:
- Core code
- Add-on modules:
- Actual miner
mimikatz- Libraries that are required for the miner’s operation, such as
msvcp120.dllandmsvcr120.dll - Module for reflective Portable Executable (PE) Injection
- Shellcode for the EternalBlue exploit
The life cycle of the PowerGhost miner can be divided into four stages:
Conclusion
Crypto malware definitely has some peculiarities, but it won’t catch you off-guard if you have an effective cybersecurity strategy. You can always boost your SOC team efforts by registering at SOC Prime Detection as Code platform. This will give you access to the world’s biggest collection of Sigma-based detections seamlessly integrated with 26+ SIEMs, EDRs, and XDRs.