Threat Hunting Techniques, Tactics, and Methodologies: Your Step-by-Step Introduction

Table of contents:
We could start this article with a bold statement saying that Threat Hunting is easier than you think, and by reading our blog post, you will instantly become a pro. Unfortunately or luckily, that’s not the case. However, we understand that starting out as a Cyber Threat Hunter is tough. That’s why we are introducing a series of guides on Threat Hunting Basics.
Preventive measures are not a panacea for an impenetrable defense. That’s where threat hunting comes into play. However, where do you start? In this blog, we’ll take a closer look at threat hunting methodologies, particularly threat hunting techniques and threat hunting tactics.
Threat Hunting Tactics
Threat hunting tactics refer to the fundamental approach a Cyber Threat Hunter leverages for both reactive and proactive threat hunting.
Target-Driven Threat Hunting
Target-driven threat hunting works well for initial data collection while focusing on a particular threat you try to find in your environment, such as:
- Advanced persistent threat (APTs) groups, including their tactics, techniques, and procedures (TTPs)
- Specific attack vector based on the MITRE ATT&CK® Framework or alternatively, Cyber Kill Chain, NIST CSF, and the frameworks by SANS Institute and ISACA. If you don’t know where to start, check our MITRE ATT&CK guide for self-advancement.
- Indicators of Compromise (IOCs) obtained either from your intel team’s internal research or from the world-class threat intel organizations.
Data-Driven Threat Hunting
A data-driven approach turns the target-driven hunting on its head. You collect data, analyze it, and define what to hunt for, depending on the items of interest and available data. A data set that allows detection of one or more threats may be a good starting point.
Data-driven threat hunting allows organizations to focus on what they have today. In contrast, target-driven threat hunting typically identifies gaps in data that may require additional resources to capture. The best threat hunting teams tend to use both tactics.
Threat Hunting Techniques and Methodologies
Generally, adversaries take the path of least resistance to obtain their goals. Like any human, they make mistakes, leave evidence, and recycle techniques. And you can use it to your advantage. With that said, let’s dive into the basic threat hunting methodology for effective hunts.
Step 1: Know Your Infrastructure
While this step might seem obvious, you’ll be surprised to know how many organizations aren’t even aware of the exact number of their endpoints. Before getting into the threat hunting techniques, you should ask yourself the following questions:
- What is the scope of my environment?
- How will adversaries try to target the environment?
- How are my employees actually utilizing the environment?
- What are my gaps in visibility, ability to triage, and ability to respond?
Step 2: Data Sources
The fundamental part of any threat hunt is data. Data sources can be active or passive:
- Active data refers to the events that were already determined as malicious by some sort of solution. You get this data from IDSs, IPSs, antivirus, etc. As an example, an antivirus solution will create an event when it quarantines a file it recognizes as
mimikatz. - Passive data is the whole scope of events, whether they are malicious or not. They can be provided by Windows event logs, sysmon, cloud logs, firewall logs, zeek, etc. For instance, most systems deliver all authentication events, including both successful and unsuccessful events. Passive data has no bias; it is simply a record of an event.
Both types of data have value. However, for a Cyber Threat Hunter, passive data sources are more useful because they provide complete visibility without relying on someone else’s research and detection logic (their bias).
Another challenge is managing the cost of data collection, which might be a real pain. Applying a ‘greedy’ approach might leave you without the required logs. And yes, you also need historical events. General advice is to keep at least a year of logs. However, it depends on the compliance, industry specifics, and your organization’s strategy. Note that passive data sources will be more expensive to collect than active sources.
Example data source: process creation
Perhaps one of the most important passive data sources to collect is process creation. Process creation events can help cover detection for more than two-thirds of the existing MITRE ATT&CK techniques. Some might argue that gathering process creation events lead to password leakages. However, you lose more by not collecting these logs, and there are workarounds to avoid a possible exposure of sensitive data. Process creation is also supported out of the box from Windows and Linux systems. In addition, enriched logs from EDR sources or Microsoft’s sysmon are very common.
Step 3: Think like an Adversary
Every cyber attack is a process, and it is far from being random. That’s why the concept of a kill chain exists. Kill chain refers to the steps adversaries take to achieve their goals. If you’re new to threat hunting, relying on your intuition and think-like-an-adversary approach might not be the best idea. However, trying to analyze attack vectors and different APTs is a great place to start.
Adversaries can’t snap their fingers to ‘own’ your systems. Generally, they must take a series of actions towards reaching their objective(s). Most of the time, this involves steps like gaining a foothold, establishing persistence, elevating permissions, lateral movement, etc.
There are certain types of attack that may allow an adversary to skirt some or even all of these measures. For instance:
- If an adversary just wants to take your main website offline, they can probably pay a denial-of-service (DoS) company to do that for them.
- Attacks like SQL injection or finding exposed cloud storage may allow adversaries to steal sensitive data without ever obtaining a foothold.
Ensure you have your coverage in place
First, check one of the frameworks (MITRE ATT&CK, Cyber Kill Chain, etc.) and take a deeper look at it to understand what might be behind an attack. Of course, there is no universal matrix that can be applied to every case, but every framework has a similar approach to the attack vectors description.
When you are familiar with the kill chain, think of what techniques and sub-techniques you should cover in the first place. Trying to cover all of the techniques might be your first intention, but, most likely, this won’t work because it is pricey, time-consuming, and still doesn’t protect your system completely.
To avoid the unnecessary fuss, keep in mind the following ideas:
- Learn what vectors adversaries can take
- Every attack doesn’t come down only to a framework
- Keep an eye on newly-emerging techniques
- Know what APTs might target your industry and what’s their style
- If your threat intel is out of place, avoid relying on the historical data on threat actors
- Check reliable reports to keep on track with the industry trends
Step 4: Data Analysis
When you’ve collected your logs, it’s time to analyze them. As a Cyber Threat Hunter, you shouldn’t only be good at code writing because working with data is essential. Practice makes perfect but what matters is who you learn from. Based on our Threat Hunters’ experience, we’ve collected the following tips for you.
Tips for successful log analysis
The following suggestions can significantly improve your threat hunting process:
- One alert means nothing but the same pattern in multiple alerts or a chain of suspicious events is what you are looking for. To track it, do the following:
- Gather all the relevant events (e.g.,
process creation) in one report - Select the most interesting ones. Remember that the most common things are the least suspicious. You can choose them manually or using Jupyter Notebook or an Excel table. Alternatively, you could write a Python script for some advanced filtering. Mostly, you have to check the command line details.
- When you select the most relevant events, make a shortened report (it might include around 100,000 events out of a million or two), export a
.csv, and give it to your analysts or analyze it yourself.
You might feel like trying to find your way through 2 million alerts is too much. However, it won’t usually take more than a few hours, even with a couple of millions of alerts.
- Gather all the relevant events (e.g.,
-
Process creation auditing is your best way to go, even for zero days and supply chain attacks. As we’ve mentioned before, only gathering these events will cover most of the techniques.
-
Remember that not every behavior is cataloged on MITRE ATT&CK. For example, keep in mind the short file names (e.g.,
1.pst) or suspicious paths, such asC:\windows\temp. According to Florian Roth, you should also pay attention to the following anomalies:- Renamed system file (
certutil.exeas%temp%\cu.exe) - Office application spawning a shell (
cmd.exe,powershell.exe) - Renamed well-known tools (
PsExec.exeasC:\p.exe) - Execution from uncommon paths (
C:\Users\Public,C:\Perflogs, etc.) - File anomalies (UPX packed file with Microsoft Copyright)
- File download from suspicious TLD (
.dlldownload from.oniondomain)
- Renamed system file (
- If your company allows, share your observations because collaborative cyber defense is way more effective than ‘fighting’ on your own.
Step 5: Threat Hunting Process
When the preparation is over (you know your infrastructure well, you have the data you need, and you’ve analyzed it), you can start the hunt. Detecting advanced attacks might seem complicated, but it gets much easier with the right telemetry. Remember that even advanced adversaries rely on recycled tactics, techniques, and procedures (TTPs).
Still doubting? Then, here is a representative example of the Solarwinds supply chain attack that remained undiscovered for around a year.
Almost every attack has more plausible and more difficult things to detect. In the Solorigate example, you can see some advanced and novel techniques that are complicated (not impossible, though) to hunt against, such as:
- Golden SAML
- Memory-only malware
- Steganography
- IP Address Masquerading
- Encrypted Files
- DGA
- Encrypted / Novel HTTP C2
On the other hand, there are more trivial techniques and methods to hunt for:
- Powershell Usage
- Process Creation / LOLBAS Usage
- Scheduled Task Creation
- Unusual Account Activity
The following script didn’t necessarily have to be malicious. However, if you see rundll32.exe running the vbscript:"\, you should pay attention to this and at least check if it has run before in your environment. Even though the adversaries did some extremely advanced stuff, they still used a well-known LOLBAS “Rundll32“.
Rundll32.exe vbscript:"\..\mshtml,RunHTMLApplication "+Execute (CreateObject("Wscript.Shell").RegRead("HKLM\SOFTWARE\MICROSOFT\Windo ws\CurrentVersion\sibot\")) (window.close)
What do we see here?
- Process Creation
- Well-known LOLBAS “
Rundll32” Rundll32run with known LOLBAS arguments
Again, this could easily be detected if you had the right telemetry. Not to mention that before the attack disclosure, we had a rule in the SOC Prime Platform that would generate an alert based on the Rundll32.exe and RunHTMLApplication.
For more examples, you can watch a webinar prepared by our Threat Hunting Engineering Lead Adam Swan, where he analyzes multiple attacks and the detections that could have been used.
IOCs- vs. behavioral-based rules
Are IOC-based rules effective? Yes, but not always. The issue with them is that IOC-report releases often take longer than the cybersecurity reality allows. In addition, most likely, IPs, hashes, domains, and tools won’t be reused. Whereas a threat hunting query built to identify unusual rundll32 activity may be useful for decades instead of days/weeks/months. So, opt for behavior-based rules for a more long-lasting effect.
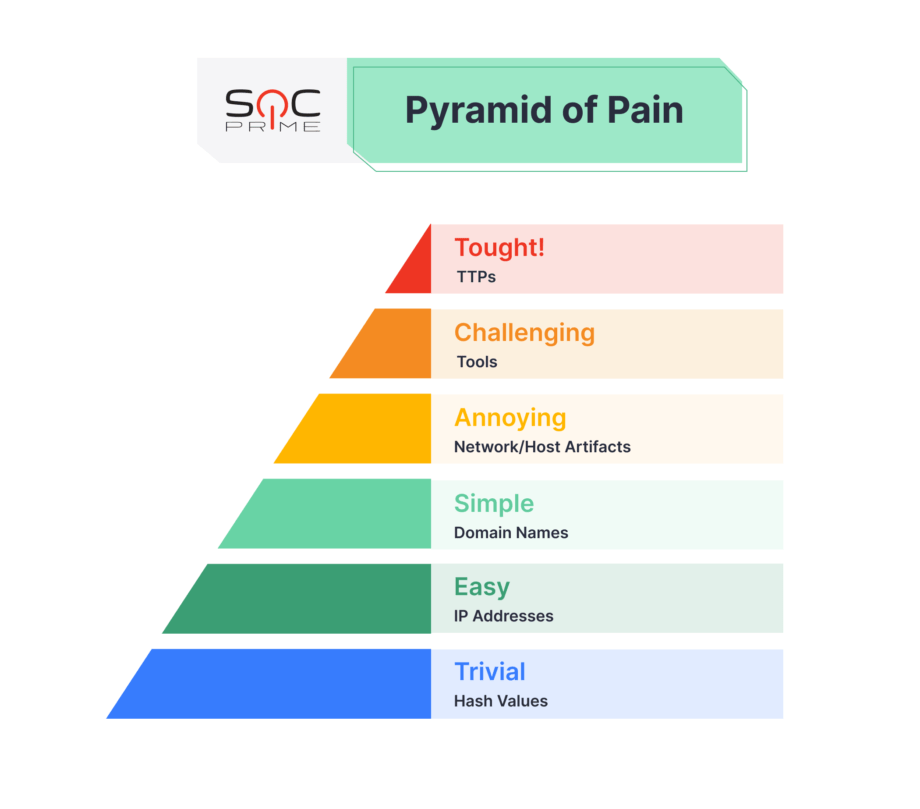
Of course, timely and high-quality IOC-based rules can be handy. Often IOC-based detections are best used retroactively to see if you were targeted in the past instead of detecting current attacks. In the end, you shouldn’t forget about the Pyramid of Pain when approaching threat hunting and incident response.
Step 6: Enrich Your Hunting
Being a Cyber Threat Hunter is probably one of the most creative roles in cybersecurity, even though it is based on analysis. To keep on with the pace of the industry, you should always get additional knowledge, insights, and inspiration. Here are a few ideas that could enrich your threat hunting process:
- Malware analysis is a great way to learn. You can borrow some ideas and rebuild the code of adversaries.
- Don’t neglect Digital Forensics and the Threat Intel context. The more you know, the more prepared you are. You can always find a compilation of context for emerging threats in the Cyber Threats Search Engine.
- Utilize MITRE ATT&CK, OSSEM, and other frameworks or documentation to broaden your knowledge and improve your hard skills.
- Use additional tools to find more inspiration, context, and ideas for your detections. First, check the free and open-source projects. For example:
- LOLBAS for binaries
- MalwareBazaar for malware samples
- ANY.RUN for malware analysis
- Uncoder.IO for Sigma rules translation
- Uncoder CTI for IOC-based queries generation
- If you run out of ideas for your hunts, check what Quick Hunt in the SOC Prime Platform has to offer.
Threat Hunting might be overwhelming and challenging, but it’s worth it. Learn, practice, and be curious. And we’ll try to make your path smoother with our guides on Threat Hunting Basics.


