Since the onset of the Russia-Ukraine war in 2022, there has been a significant rise in offensive operations, highlighting the profound impact of geopolitical tensions on global enterprises. Multiple hacking groups continue to use Ukraine as a testing ground to extend their attack surface into European and U.S. political arenas. CERT-UA has been lately reported about a new surge in targeted cyber attacks against government entities, the military, and defense agencies using the DarkCrystal RAT malware, which is spread through the Signal messenger.
UAC-0200 Attack Analysis
On June 4, 2024, CERT-UA released a novel CERT-UA#9918 heads-up of a new phishing campaign leveraging the Signal messenger. The hacking collective tracked as UAC-0200 is behind a new wave of malicious operations targeting Ukrainian state bodies, including public officials, military personnel, and the representatives of the defense sector who largely rely on Signal as a trusted means of communication.
Notably, hackers try to entice victims into opening the malicious file sent via Signal that contains DarkCrystal RAT by using a sender who might be from the recipient’s contact list or shared groups. This tactic aims to increase the trust level of these messages, posing greater threats to potential victims of such sophisticated phishing attacks.
Attackers send an archive, a password, and a message emphasizing the need to open the harmful file with malware on a computer. Typically, the above-referenced archive contains an executable file (with extensions such as “.pif” or “.exe”), which is a RARSFX archive that includes a VBE file, a BAT file, and an EXE file. Once executed, the latter will infect the targeted computer with the DarkCrystal RAT malware, enabling hidden unauthorized access to the system.
Defenders point to the escalating trend of cyber attacks that exploit popular messengers as a common initial attack vector and leverage compromised legitimate accounts. In all cases, the victim is lured into opening the file on a computer, which should be considered a specific warning for users to avoid the risks of intrusions.
Detecting UAC-0200 Intrusions Covered in the CERT-UA#9918 Alert
The continuously increasing pattern of cyber attacks that abuse trusted messaging applications to spread malware poses escalating risks for organizations that might fall prey to tricky adversary intentions. In response to the latest CERT-UA#9918 alert, warning defenders of UAC-0200 attacks that exploit Signal to spread DarkCrystal RAT, SOC Prime has instantly curated a relevant set of detection algorithms.
Click the Explore Detections button to get to the list of Sigma rules for UAC-0200 activity detection covered in the corresponding CERT-UA#9918 alert. All detections are filtered by the custom tag based on the CERT-UA research identifier to help security teams accelerate their content search and selection. The TTP-based Sigma rules provided in this detection stack are linked to MITRE ATT&CK® and compatible with the market-leading on-prem and cloud-native SIEM, EDR, and Data Lake solutions to streamline detection engineering operations for organizations that work in dispersed ecosystems. Alternatively, security teams can also access relevant detections using the “UAC-0200” tag based on the adversary attribution.
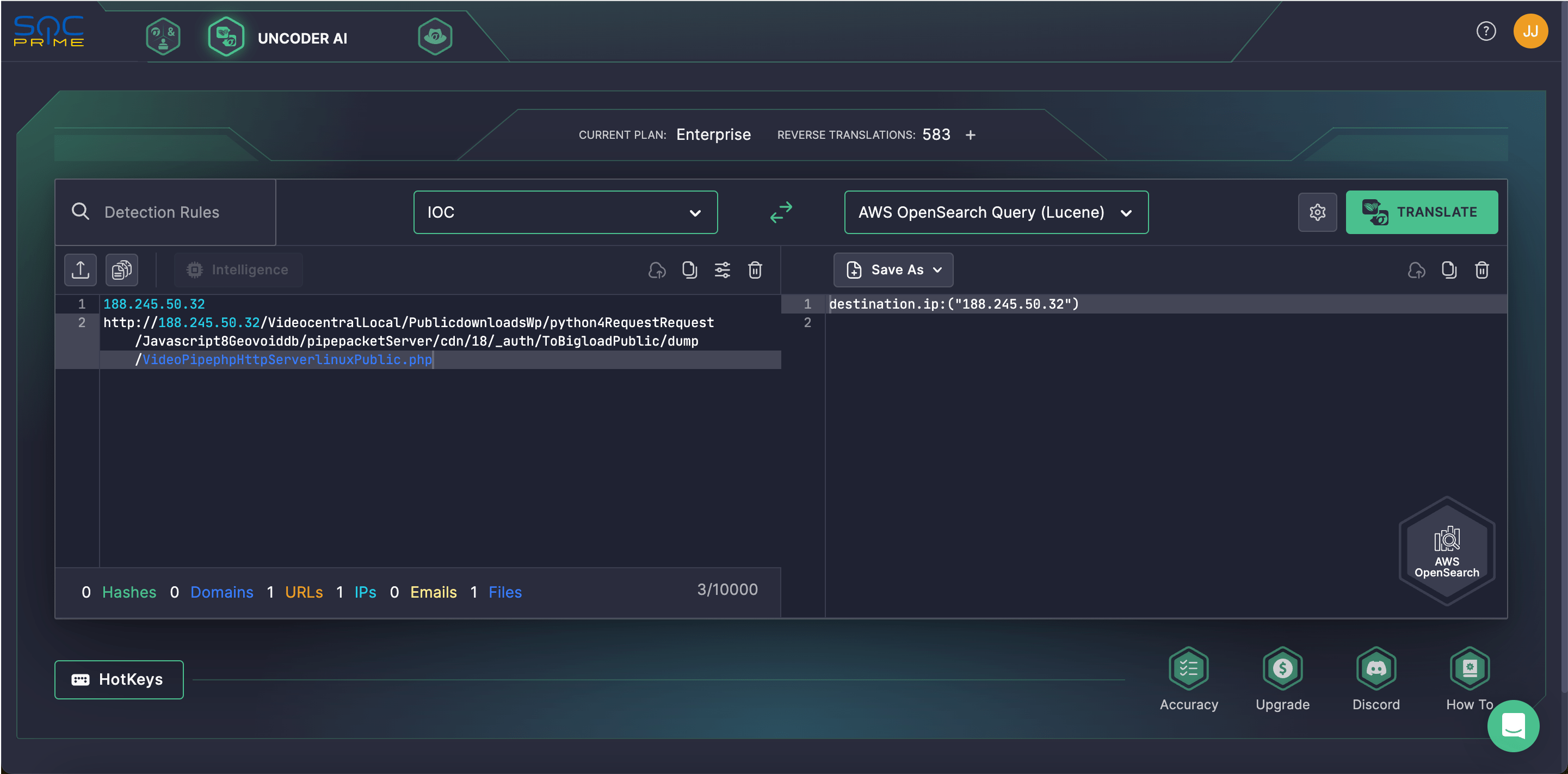
To simplify the search for the file, host, or network-based IOCs offered in the CERT-UA#9918 report, security engineers can rely on SOC Prime’s Uncoder AI using the built-in IOC packager. The solution enables automatically converting threat intel into performance-optimized IOC queries compatible with the SIEM or EDR format of your choice.
MITRE ATT&CK Context
By leveraging MITRE ATT&CK, cyber defenders might obtain detailed insights into the context of the latest offensive operation and TTPs linked to UAC-0200. Check out the table below to view the comprehensive list of specific Sigma rules that correspond to the relevant ATT&CK tactics, techniques, and sub-techniques.




