Threat actors frequently leverage remote management tools in cyber attacks via the phishing attack vector. For instance, the Remote Utilities software has been largely exploited in offensive campaigns against Ukraine. CERT-UA, in conjunction with CSIRT-NB, has recently identified a targeted cyber attack attributed to the UAC-0188 employing remote management software. Adversaries were observed gaining unauthorized access to the computers of Ukrainian organizations exploiting a popular SuperOps RMM tool.
Detect UAC-0188 Activity Covered in the CERT-UA#9797 Research
The increasing exposure and impact of phishing attacks abusing legitimate software, including remote management tools, underscores the need for enhancing proactive cyber defenses. SOC Prime Platform provides a collection of Sigma rules to detect the latest malicious activity that leverages SuperOps RMM for offensive purposes, targets Ukraine, and potentially expands the attack scope to Europe and the USA. For ease of search, the detection algorithms can be filtered by the custom tags “UAC-0188” or “CERT-UA#9797” based on either the group or research identifiers.
Log into SOC Prime Platform and click the Explore Detections button to instantly drill down to the relevant detection stack enriched with actionable metadata, aligned with the MITRE ATT&CK® framework, and ready to deploy to multiple security analytics solutions in use.
To proactively defend against similar attacks that exploit legitimate remote management tools, security engineers can also take advantage of more SOC content added to the relevant detection stack available via this link.
CERT-UA has also provided the list of IOCs to hunt for threats related to the UAC-0188 most recent activity. By leveraging SOC Prime’s Uncoder AI, Detection Engineers, Threat Hunters, and SOC Analysts can streamline IOC matching by instantly converting relevant threat intel into custom IOC queries ready to hunt in the language format matching the SIEM or EDR in use.
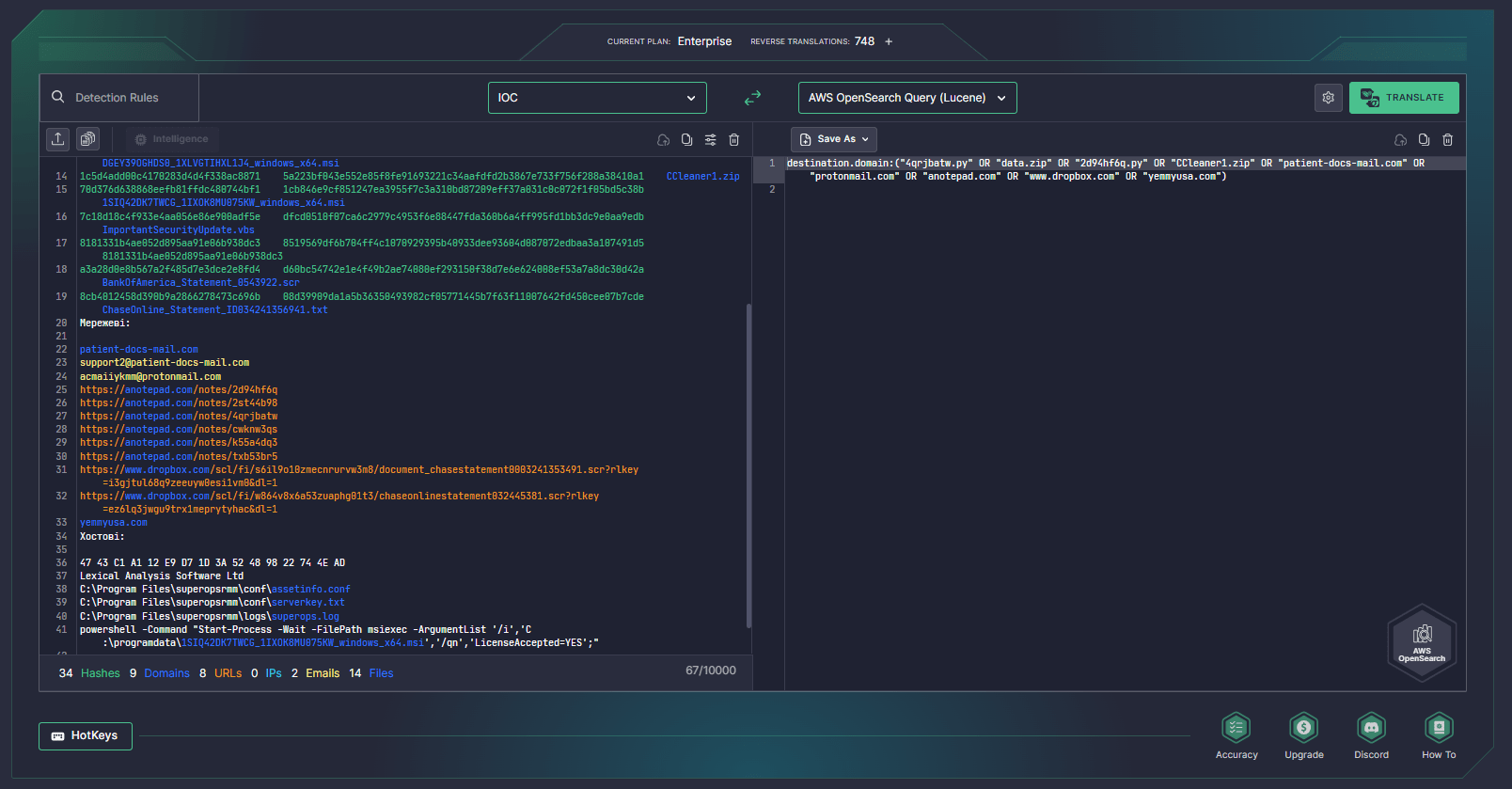
UAC-0188 Attack Analysis
On May 23, 2024, CSIRT-NBU and CERT-UA issued a new CERT-UA#9797 alert warning the global cyber defender community of a phishing attack against Ukraine weaponizing a legitimate remote management SuperOps RMM tool. The malicious activity has been linked to the UAC-0188 hacking collective.
The infection flow is triggered by a phishing email with a link to Dropbox, which leads to downloading an executable SCR file. The latter is created using PyInstaller and contains the legitimate Python code for the “Minesweeper” game along with a 28MB base64-encoded string. The rest of the program code downloads, decodes, and executes the Python code. The primary function of the downloaded Python code is to call the “create_license_ver” function from “Minesweeper,” with the argument being a combination of the base64-encoded string from the downloaded script and the 28MB base64 string contained in the initial SCR file.
Concatenating and decoding the string leads to obtaining a ZIP archive, which extracts and executes an MSI file representing the legitimate SuperOps RMM software. Running this program on the computer enables adversaries to gain unauthorized remote access to third parties
CERT-UA conducted further research into the adversary TTPs. Using the features of the SCR file, five similar files were found, named after financial and insurance institutions in Europe and the USA. According to the research, the uncovered cyber attacks are likely to have been launched no later than February-March 2024, with adversaries expanding the geographic scope of impact.
Defenders recommend organizations not using legitimate SuperOps RMM should ensure there is no network activity related to the domains *.superops.com and *.superops.ai to preempt attacks associated with the latest UAC-0188 operations.
MITRE ATT&CK Context
By leveraging MITRE ATT&CK, cyber defenders might obtain detailed insights into the context of offensive operations and TTPs linked to UAC-0188. Check out the table below to view the comprehensive list of specific Sigma rules that correspond to the relevant ATT&CK tactics, techniques, and sub-techniques.




