The UAC-0184 hacking collective is back, once again setting its eyes on the Armed Forces of Ukraine. Adversaries attempt to gain access to the targeted computers to steal files and messaging data, according to the latest CERT-UA research.
UAC-0184 Latest Attack Description
Defenders have been observing a significant surge in the malicious activity of the UAC-0184 group throughout 2024. At the turn of the year, hackers launched a phishing campaign against Ukraine, using military-related phishing lures and Remcos RAT malware as part of their offensive toolkit.
On April 16, CERT-UA released a novel heads-up focused on a new wave of the group’s offensive operations. In the latest malicious campaign attributed to the UAC-0184 group, adversaries are targeting the computers of the Armed Forces of Ukraine attempting to steal sensitive data. As the initial attack vector, the group applies social engineering, such as lure messages about the opening of an executive investigation or a criminal case, combat action videos, or requests for acquaintance through popular dating platforms. Subsequent chatting with a military serviceman may involve transferring a file or archive with a request for assistance in opening or processing it.
Adversaries leverage multiple offensive tools, including commercial software and open-source utilities. For instance, UAC-0184 applies IDAT (HijackLoader, SHADOWLADDER, GHOSTPULSE) malware in the initial stage of intrusion. Other malicious strains involve REMCOSRAT, VIOTTOKEYLOGGER, and XWORM. The group also leverages SIGTOP and TUSC utilities, which are publicly accessible from GitHub, to steal and extract data from targeted computers, including messages and contact details from Signal, a popular platform among military personnel.
To minimize adversary intrusions, defenders recommend remaining cyber vigilant when using popular messengers that are not properly controlled channels for information exchange and are at risk of being weaponized by attackers.
Detect UAC-0184 Activity Addressed in the CERT-UA#9474 Alert
The increasing number of cyber attacks against Ukraine linked to the UAC-0184 group underscores the need for enhancing defenses to timely identify the intrusions. Log in to SOC Prime Platform to gain access to the entire collection of detection algorithms for UAC-0184 attacks weaponizing popular messengers and dating websites according to the most recent CERT-UA#9474 heads-up. Browse for the relevant detection stack by applying the custom tag based on the CERT-UA alert ID:
Sigma rules to detect UAC-0184 activity covered in the CERT-UA#9474 report
All detection algorithms are aligned with the MITRE ATT&CK® framework v.14.1, enriched with relevant threat intel and actionable metadata, and are instantly convertible to diverse SIEM, EDR, and Data Lake language formats to hyperscale your Detection Engineering operations.
If you are looking for the complete rule set for UAC-0184 attack detection, click the Explore Detections button below, and access more content items addressing the group’s TTPs and reflecting their common behavior patterns.
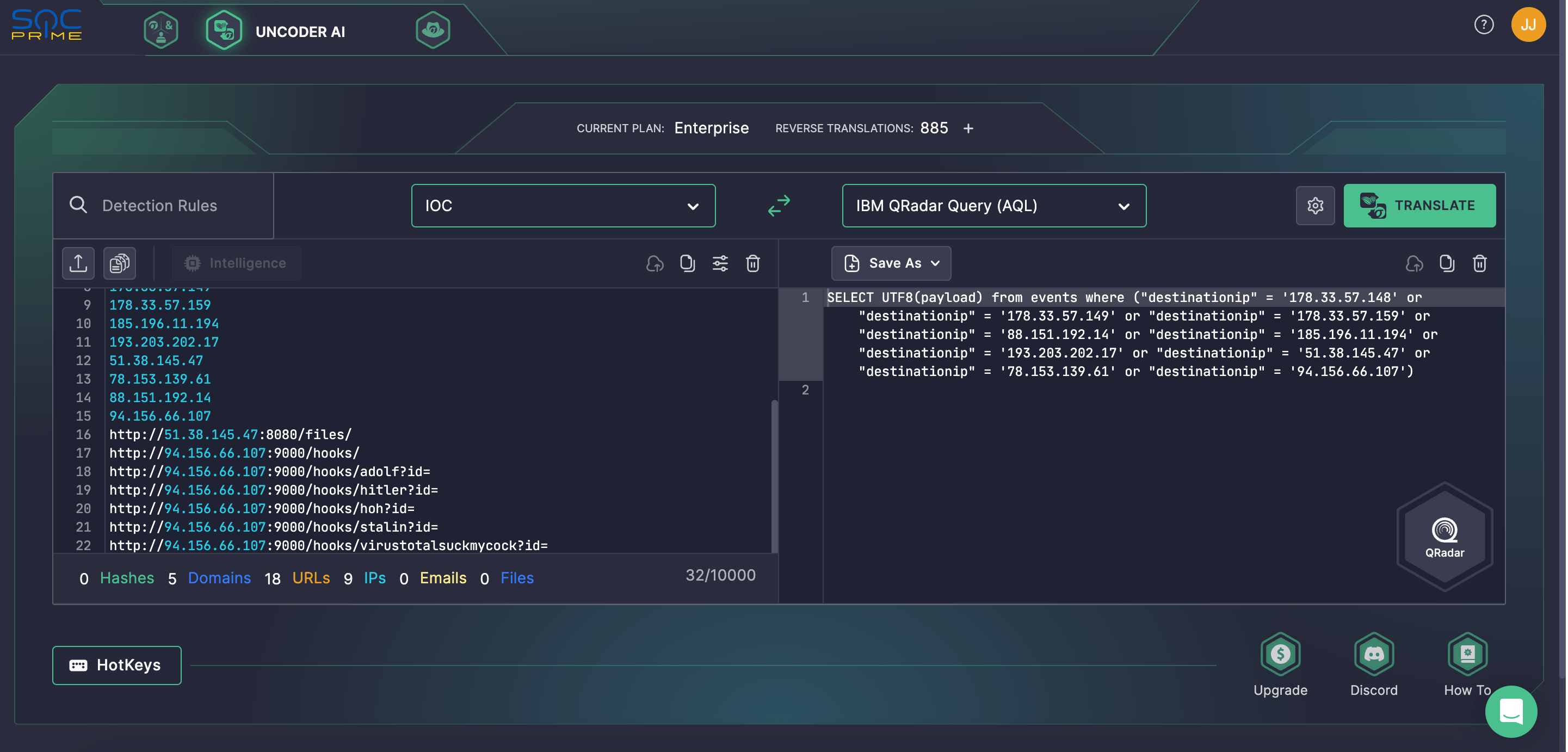
To streamline your IOC matching, rely on Uncoder AI, the industry-first AI co-pilot for Detection Engineering, and instantly hunt for indicators of compromise provided in the CERT-UA#9474 alert. Uncoder AI acts as an IOC packager, letting CTI and SOC analysts and Threat Hunters seamlessly parse IOCs and convert them into custom hunting queries ready to run in the SIEM or EDR of their choice.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides granular visibility into the context of offensive operations attributed to UAC-0184. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | User Execution: Malicious File (T1204.002) | |
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) | ||
Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | |
Defense Evasion | Masquerading (T1036) | |
Subvert Trust Controls: Mark-of-the-Web Bypass (T1553.005) | ||
Hide Artifacts: Hidden Window (T1564.003) | ||
Deobfuscated/Decode Files or Information (T1140) | ||
Command and Control | Ingress Tool Transfer (T1105) |




