The UAC-0149 threat actor repeatedly targets Ukrainian governments and military organizations using COOKBOX malware. The latest research by CERT-UA details the new attack leveraging phishing Signal messages and CVE-2023-38831 exploits to deploy COOKBOX on the targeted instances.
UAC-0149 Attack Details
UAC-0149 hacking collective has been performing malicious operations against Ukraine since at least autumn 2023. At the turn of 2024, CERT-UA revealed a targeted attack against the Armed Forces of Ukraine involving the infamous COOKBOX malware delivered via fake Signal messages.
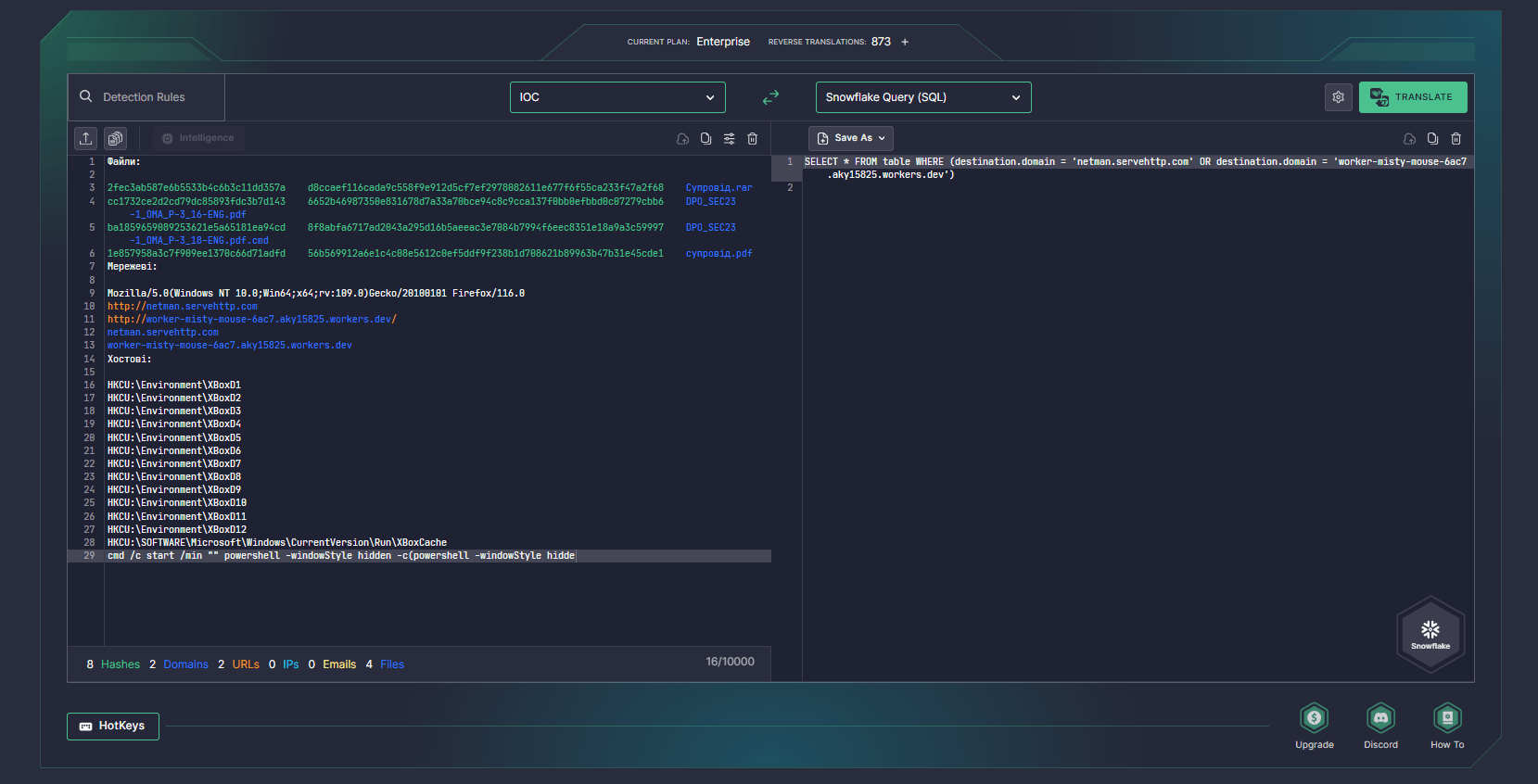
On April 18, CERT-UA issued a new alert warning of a new wave of intrusions leveraging COOKBOX. In the latest operation attributed to UAC-0149, hackers are targeting representatives of the Ukrainian Defense Forces with malicious Signal messages having malware-laced documents attached. The fake documents referred to applying for a position in the United Nations Department of Peace Operations are delivered via “Супровід.rar” archive which contains a CVE-2023-38831 exploit for WinRAR software. In case opened, the malicious RAR archive executes CMD-file “супровід.pdf. cmd” which in turn opens a phishing document “DPO_SEC23-1_OMA_P-3_16-ENG.pdf” and triggers PowerShell scripts associated with COOKBOX malware.
Notably, the COOKBOX command-and-control server leverages NoIP dynamic DNS service. In cooperation with NoIP representatives the corresponding domain name has been already blocked.
Following this attack, CERT-UA strongly recommends system administrators limit users in running utilities such as powershell.exe, wscript.exe, cscript.exe, mshta.exe, and others. It is advised to use standard mechanisms such as SRP, AppLocker, and registry settings.
Detect UAC-0149 Attack Covered in CERT-UA#9522 Alert
With the escalating wave of UAC-0149 attacks leveraging COOKBOX malware, security professionals are seeking a reliable way to spot intrusions on time and defend proactively. SOC Prime Platform for collective cyber defense aggregates a curated set of Sigma rules to detect the latest UAC-0149 activity accompanied by advanced threat detection and hunting solutions. Additionally, cyber defenders can browse for the relevant detection stack by applying the custom tag based on the CERT-UA alert ID “CERT-UA#9522”:
Sigma Rules to Detect UAC-0149 Activity Covered in CERT-UA#9522 Alert
All detection algorithms are aligned with the MITRE ATT&CK® framework v.14.1, enriched with relevant threat intel and actionable metadata, and are instantly convertible to diverse SIEM, EDR, and Data Lake language formats to hyperscale your Detection Engineering operations.
Cybersecurity experts looking for broader coverage of UAC-0149 attacks might click the Explore Detections button below to immediately access an extensive rule collection addressing the group’s TTPs and behavior patterns.
To streamline your threat investigation, rely on Uncoder AI, the industry-first AI co-pilot for Detection Engineering, and instantly hunt for indicators of compromise provided in the CERT-UA#9522 alert. Uncoder AI acts as an IOC packager, letting CTI and SOC analysts and Threat Hunters seamlessly parse IOCs and convert them into custom hunting queries ready to run in the SIEM or EDR of their choice.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides extensive visibility into the behavior patterns related to the latest UAC-0149 attack. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques. Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment Execution User Execution: Malicious File (T1204.002) Command and Scripting Interpreter: PowerShell (T1059.001) Persistence Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) Defense Evasion Obfuscated Files or Information (T1027) Masquerading: Double File Extension (T1036.007) Hide Artifacts: Hidden Window (T1564.003) Command and Control Proxy: Domain Fronting (T1090.004)




