Hard on the heels of the cyber-espionage campaign by UAC-0099 via the phishing attack vector, another hacking collective has evolved in the cyber threat arena to target Ukrainian organizations. CERT-UA notifies defenders about the discovery of fake websites that mimic the official page of the “Army+” application and are hosted using the Cloudflare Workers service. The malicious activity is linked to the UAC-0125 group, which is highly likely associated with the nefarious russia-backed hacking collective tracked as UAC-0002 (aka APT44 aka Sandworm).
Detect UAC-0125 Attacks Covered in the CERT-UA#12559 Alert
The increasing number of cyber-attacks targeting government bodies, military and defense agencies, and the critical infrastructure sector has been causing a stir on the cyber front line since russia’s full-fledged war against Ukraine. The release of a novel CERT-UA#12559 heads-up amplifies the growing concern over the UAC-0125 adversary activity, with strong indications of its connection to russia’s UAC-0002 group (aka Sandworm APT) and the need for increased cybersecurity vigilance. SOC Prime Platform for collective cyber defense equips security teams with a relevant detection stack to proactively thwart attacks covered in the CERT-UA#12559 alert.
Click Explore Detections to access the dedicated SOC content or use the corresponding custom tags when searching Threat Detection Marketplace based on the cluster identifier or the CERT-UA alert ID. The detection algorithms are aligned with the MITRE ATT&CK® framework and offer actionable cyber threat context, including CTI and operational metadata. Security engineers can also translate the detection code in an automated fashion for one of 30+ chosen SIEM, EDR, or Data Lake formats.
Teams can also investigate the TTPs associated with the actor’s offensive operations by accessing the full collection of Sigma rules via the corresponding “UAC-0125” tag. Additionally, security experts can apply the “Sandworm” tag to search for detections linked to the adversary cluster, which is highly likely associated with the latest UAC-0125 activity.
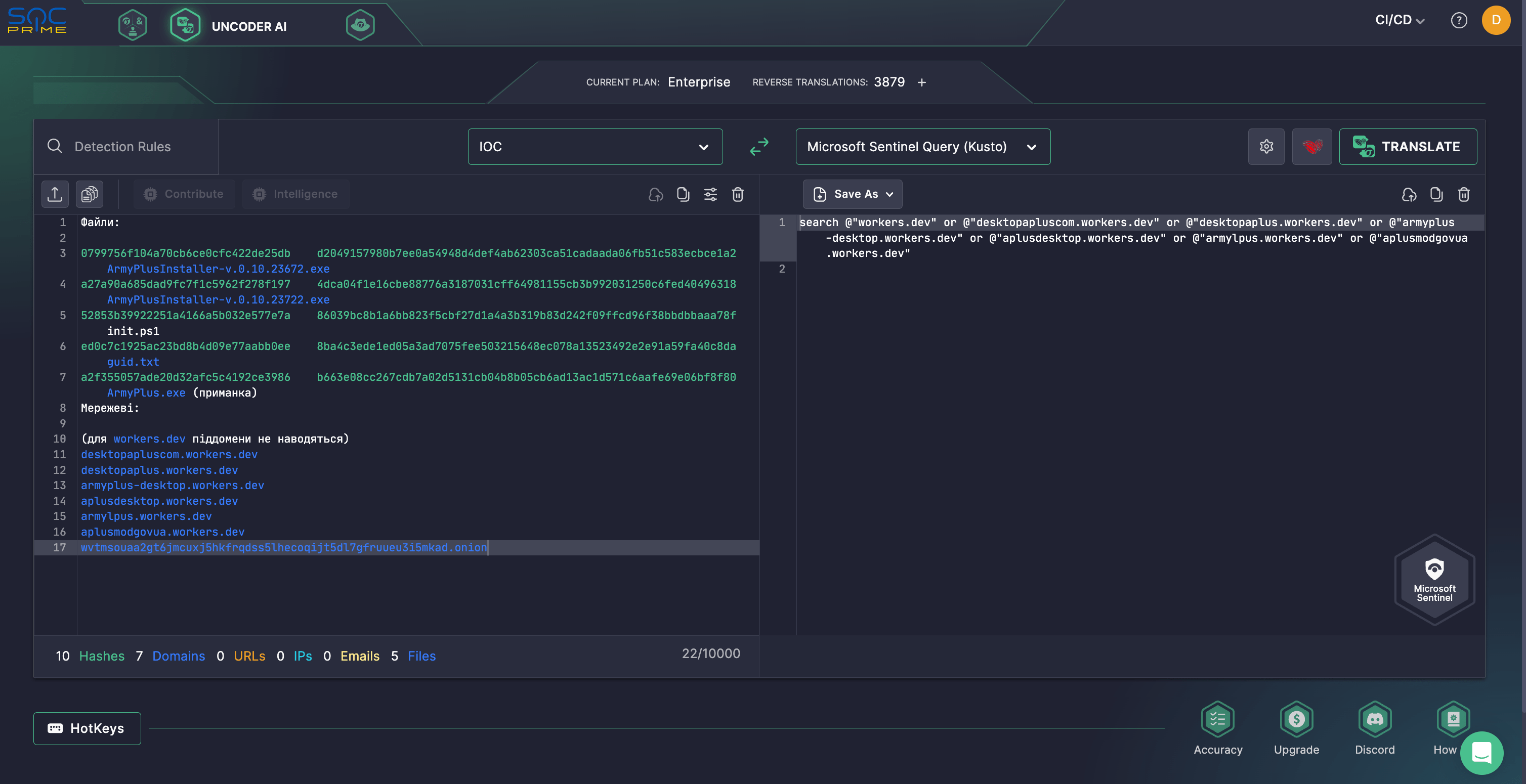
By leveraging SOC Prime’s Uncoder AI, organizations can accelerate IOC matching related to the UAC-0125 offensive operations observed in the latest CERT-UA alert while seamlessly converting IOCs into custom hunting queries matching the language format in use.
UAC-0125 Attack Analysis
On December 17, 2024, CERT-UA received information from MIL.CERT-UA experts related to the discovery of several fraudulent websites that masquerade as the official page of the “Army+” application and are hosted through the Cloudflare Workers service. Army+ was created by the Ministry of Defense together with the General Staff of the Armed Forces of Ukraine to transform the Ukrainian army exosystem and help solve the requests of military personnel.
According to the corresponding CERT-UA#12559 alert, when visiting these fake websites, users are prompted to download the executable file “ArmyPlusInstaller-v.0.10.23722.exe”, with the file name potentially changed.
The executable file is an installer created using NSIS (Nullsoft Scriptable Install System), which, in addition to the .NET bait file “ArmyPlus.exe,” contains Python interpreter files, a Tor program archive, and a PowerShell script “init.ps1.”
When the “ArmyPlusInstaller-v.0.10.23722.exe” file is opened, it runs the lure file and a PowerShell script. The latter is designed to install OpenSSH on the compromised system, generate an RSA key pair, add the public key for authentication, send the private key to the attacker via “curl,” and expose a hidden SSH service through Tor. All these operations give attackers the green light to gain remote access to the victim’s computer, facilitating further system compromise.The adversary activity is tracked under the UAC-0125 identifier and, with high confidence, has ties with the russia-linked UAC-0002 cluster (aka UAC-0133, APT44, UAC-0082, or Sandworm). The notorious Sandworm APT group has been targeting Ukrainian state bodies and critical infrastructure organizations for over a decade. They are responsible for the 2015-2016 BlackEnergy-induced blackouts, the global NotPetya campaign in 2017, and the 2022 attacks on Ukrainian power facilities using Industroyer 2 and different data-wiping malware. In the first half of 2024, the attackers’ initial compromise vector was a Microsoft Office package containing a trojanized component, which included the “CommunicatorContentBinApp.cmd” file with a PowerShell command.
MITRE ATT&CK Context
By applying ATT&CK, security teams can gain valuable insights into the UAC-0125 TTPs involved in the latest malicious campaign against Ukraine, as detailed in the latest CERT-UA report. The table below provides a comprehensive collection of Sigma rules that address the associated ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing (T1566) | |
Execution | Command and Scripting Interpreter: PowerShell (T1059.001) | |
Command and Scripting Interpreter: Windows Command Shell | ||
Defense Evasion | Hide Artifacts: Hidden Window (T1564.003) | |
Discovery | System Information Discovery (T1082) | |
Collection | Archive Collected Data (T1560) | |
Command and Control | Proxy: Multi-hop Proxy (T1090.003) | |
Protocol Tunneling (T1572) | ||
Encrypted Channel: Asymmetric Cryptography (T1573.002) | ||
Exfiltration | Exfiltration Over C2 Channel (T1041) |




