UAC-0050 Activity Detection: Hackers Impersonate SSSCIP and State Emergency Service of Ukraine Using Remote Utilities

Table of contents:
Just slightly over a week after the UAC-0050 group’s attack against Ukraine leveraging Remcos RAT, Quasar RAT, and Remote Utilities, adversaries reemerge in the cyber threat arena. CERT-UA has recently notified defenders of the ongoing group’s campaign involving mass email distribution and masquerading the senders as State Service of Special Communications and Information Protection of Ukraine (SSSCIP) and State Emergency Service of Ukraine.
UAC-0050 Phishing Attack Description: Novel Offensive Activity Against Ukraine Using Remote Utilities
On January 22, 2024, the CERT-UA team once again arrested the attention of cyber defenders to the increasing activity of the UAC-0050 threat actors. A new security heads-up highlights the mass distribution of phishing emails impersonating the SSSCIP and the State Emergency Service of Ukraine. The identified phishing emails include lure topics like “virus removal” or “evacuation” and contain RAR archives along with links to the Bitbucket web service.
Once opened, any of the above-referenced files, including those downloaded from the Bitbucket, will launch an MSI installer. The latter installs the Remote Utilities remote control program on the compromised system. Notably, the software configuration file contains 15 different IP addresses of adversary C2 servers.
According to Bitbucket statistics, the malicious files have already been downloaded more than 3,000 times. The number of successfully infected computers may reach several dozens, however, due to urgent cybersecurity measures, defenders managed to thwart attacks.
Detect UAC-0050 Phishing Attacks Covered in the CERT-UA#8654 Alert
As offensive operations against Ukraine attributed to the UAC-0050 group continuously increase, defenders are looking for more sophisticated measures to preempt these attacks. SOC Prime’s industry-first platform for collective cyber defense equips security teams with vendor-agnostic and future-proof detection algorithms against emerging cyber threats, including adversary operations linked to the UAC-0050 activity. Log in to SOC Prime Platform and access the list of relevant ready-to-deploy Sigma rules filtered by the “CERT-UA#8654” tag matching the alert ID by following the link below:
Sigma rules for UAC-0050 attack detection addressed in the CERT-UA#8654 alert
To boost defenses against existing and emerging threats attributed to the UAC-0050 hackers, it’s worth taking advantage of the entire collection of relevant detection algorithms available in the SOC Prime Platform. Press Explore Detections to obtain these Sigma rules aligned with MITRE ATT&CK®, enriched with in-depth CTI, and automatically convertible to the language formats of multiple security analytics platforms.
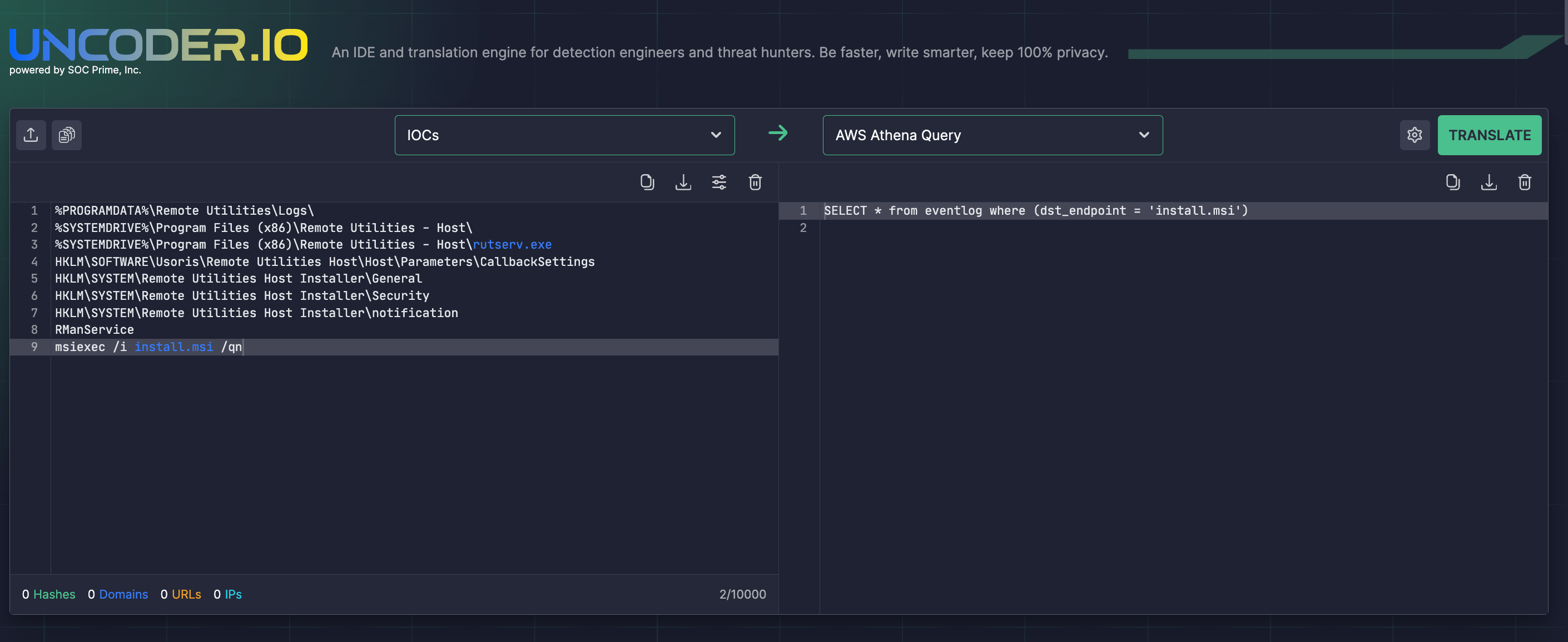
Uncoder IO enables security engineers to seamlessly hunt for IOCs provided by CERT-UA by automatically converting threat intel linked to the UAC-0050 malicious activity into custom hunting queries tailored for the SIEM or EDR environment in use.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK gains detailed insight into the context of the most recent offensive campaign associated with UAC-0050. Refer to the table below to view the comprehensive set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | Exploitation for Client Execution (T1203) | |
User Execution: Malicious File (T1204.002) | ||
Software Deployment Tools (T1072) | ||
Defense Evasion | Obfuscated Files or Information (T1027) | |
Lateral Movement | Remote Services (T1021) | |
Command and Control | Remote Access Software (T1219) | |