The Vermin hacking collective, also tracked as UAC-0020, resurfaces, targeting Ukraine using a novel offensive tool dubbed FIRMACHAGENT. In the latest attack, adversaries leverage the phishing attack vector to spread emails with the lure subject related to the prisoners of war at the Kursk front.
UAC-0020 aka Vermin Attack Analysis Using FIRMACHAGENT
On August 19, 2024, the CERT-UA team released a new cybersecurity heads-up CERT-UA#10742, covering the reemergence of the UAC-0020 hacking group, also known as Vermin, in the cyber threat arena. Notably, a couple of months ago, Vermin launched a “SickSync” campaign against the Armed Forces of Ukraine using SPECTR malware, which was also one of the key tools from the group’s adversary arsenal in mid-March 2022 targeting Ukrainian government and military agencies. In the latest campaign, in addition to the common SPECTR malware from the offensive toolkit, attackers take advantage of a novel offensive tool known as FIRMACHAGENT malware.
The infection flow starts with phishing emails leveraging the subject of war prisoners at the Kursk front embedded with a link to a malicious ZIP archive. The archive contains a CHM file named “list_of_inactive_vice_chairs_kursk.chm,” which includes an HTML file with JavaScript code that triggers the execution of an obfuscated PowerShell script. The latter is designed to download components of the SPECTR malware, which steals sensitive data like documents, screenshots, or browser data, and the new FIRMACHAGENT malware. The major function of the new offensive tool is to upload stolen data to a command server. It is also used to set up scheduled tasks to run the orchestrator “IDCLIPNET_x86.dll”, which manages the SPECTR plugins and FIRMACHAGENT.
To reduce the attack surface, organizations are recommended to limit user account privileges, such as removing them from the Admin group and implementing relevant policies to prevent users from executing CHM files and powershell.exe.
Detect UAC-0020 Attack Covered in CERT-UA#10742 Alert
As the UAC-0020 (also known as Vermin) hacking group continues to enhance its malicious toolset to target the Ukrainian government and military organizations, security professionals are in search of reliable ways to detect and counter these threats in real time. SOC Prime Platform for collective cyber defense offers a dedicated set of Sigma rules to identify the latest UAC-0020 attacks, accompanied by a complete product suite for automated threat hunting, AI-powered detection engineering, and advanced threat detection.
Sigma Rules to Detect UAC-0020 Attacks Covered in CERT-UA#10742 Alert
All the rules are compatible with 30+ SIEM, EDR, and Data Lake solutions and mapped to the MITRE ATT&CK® framework v.14.1. Also, to streamline threat investigation, detections are enriched with detailed CTI and operational metadata, including threat intel references, attack timelines and triage recommendation. Just access the detection stack via the link above or simply browse Threat Detection Marketplace using the custom “CERT-UA#10742” tag based on the CERT-UA alert identifier.
Cybersecurity experts looking for broader UAC-0020 detection coverage to analyze adversary attacks retrospectively might click the Explore Detections button and immediately drill down to a rule collection addressing the adversary TTPs and behavior patterns.
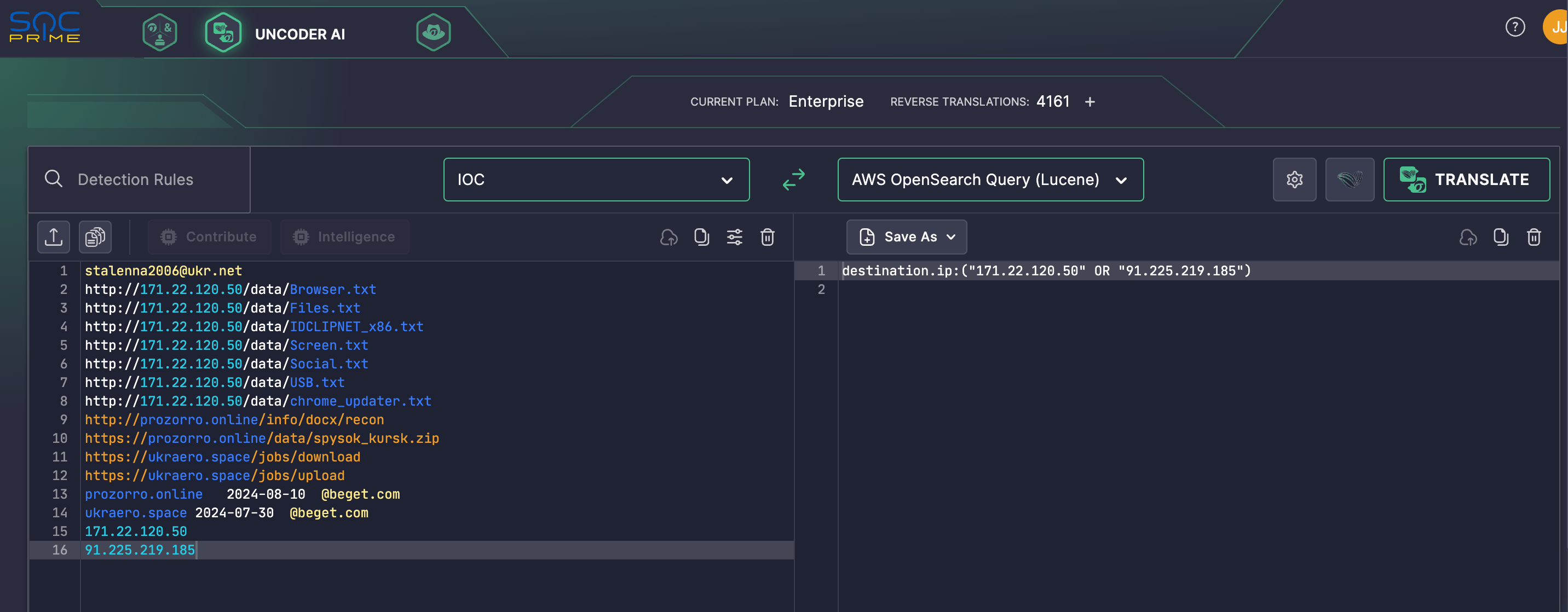
Additionally, to smooth out the investigation, cyber defenders can rely on Uncoder AI, the industry-first AI co-pilot for Detection Engineering, and instantly hunt for IOCs provided in the CERT-UA#10742 alert. Just paste IOCs to Uncoder AI and seamlessly parse them to covert into custom hunting queries matching your SIEM or EDR in use.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides extensive visibility into the behavior patterns related to the latest UAC-0020 attack. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Phishing: Spearphishing Link (T1566.002) | ||
Execution | User Execution (T1204) | |
Scheduled Task/Job: Scheduled Task (T1053.005) | ||
Command and Scripting Interpreter: PowerShell (T1059.001) | ||
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Defense Evasion | System Binary Proxy Execution: Compiled HTML File (T1218.001) | |
Hide Artifacts: Hidden Window (T1564.003) | ||
Command and Control | Ingress Tool Transfer (T1105) | |
Application Layer Protocol: Web Protocols (T1071.001) |




