The Vermin hacking group, also known as UAC-0020, resurfaces, targeting the Armed Forces of Ukraine. In the latest “SickSync” campaign uncovered by CERT-UA in collaboration with the Cybersecurity Center of the Armed Forces of Ukraine, adversaries once again employ SPECTR malware, which has been part of their adversary toolkit since 2019.
SickSync Campaign Targeting the Armed Forces of Ukraine: Attack Analysis
On June 6, 2024, CERT-UA, in conjunction with the Center for Cybersecurity of the Armed Forces of Ukraine, discovered and investigated the malicious activity of the UAC-0020 group, also tracked as Vermin. The group was active over two years ago, in mid-March 2022, at the early stages of russia’s full-scale evasion of Ukraine, when they were spotted behind a massive spear-phishing campaign targeting the Ukrainian state bodies and attempting to spread SPECTR malware. Notably, the hacking collective is linked to the self-proclaimed Luhansk People’s Republic and is believed to operate under the direction of the Moscow government as part of russia’s cyber warfare efforts against Ukraine.
In the latest campaign CERT-UA#9934 alert, UAC-0020 targets the Armed Forces of Ukraine, leveraging the nefarious SPECTR malware accompanied by the SyncThing utility. The group has been relying on the SPECTR malware for half a decade, implementing it as a means of cyber threat implementation. As for the exploitation of the SyncThing software, which is commonly used for legitimate purposes to establish peer-to-peer connections between computers, hackers use the tool to extract data from the targeted computer.
The infection flow starts with a phishing email that contains a password-protected archive attachment. The latter includes another RARSFX archive containing a decoy file named “Wowchok.pdf,” an executable file “sync.exe” created via the InnoSetup installer, and a BAT file “run_user.bat” intended for initial execution.
The “sync.exe” file contains both legitimate components of the SyncThing software and harmful SPECTR malware files, including auxiliary libraries and scripts. Additionally, SyncThing files have been partially modified to change directory names, schedule tasks, or disable user notification functionality.
The SPECTR modules include SpecMon, which executes DLL files containing the “IPlugin” class; Screengrabber for capturing screenshots; FileGrabber and Usb modules used to copy files with specified extensions from certain directories and USB drives via robocopy.exe; and Social and Browsers modules used for stealing authentication and browser data from various messengers and Internet browsers.
Notably, the stolen data is copied to subfolders in the directory %APPDATA%\sync\Slave_Sync. Subsequently, via the SyncThing synchronization capabilities, the contents of these folders are sent to the attacker’s computer, thus facilitating data exfiltration.
Detect Vermin (UAC-0020) Attacks as Part of SickSync Espionage Campaign
The re-emergence of the Vermin (UAC-0020) hacking group in the Ukrainian cyber threat arena highlights the urgent need to enhance cyber resilience and proactive defense measures to counter attacks, which primarily target public sector agencies and are highly likely connected to russia’s offensive operations. In view of the novel security heads-up issued by CERT-UA and the Cybersecurity Center of the Armed Forces of Ukraine, SOC Prime has recently released a set of curated Sigma rules to detect the latest Vermin’s activity as part of an espionage campaign called SickSync against the Armed Forces of Ukraine
Security engineers can easily search for relevant detection content using the custom tag based on the CERT-UA#9934 alert ID or the SickSync campaign name. All the rules are compatible with 30+ SIEM, EDR, and Data Lake solutions and mapped to the MITRE ATT&CK® framework. Click the Explore Detections button to instantly drill down to the dedicated content collection.
For additional rules and context to perform a retrospective analysis of Vermin TTPs, cyber defenders might also leverage “UAC-0020” and “Vermin” tags.
To streamline the search for the file, host, or network IOCs mentioned in the CERT-UA#9934 alert, security engineers can take advantage of SOC Prime’s Uncoder AI with its built-in IOC packager. It enables automatically converting threat intelligence into custom IOC queries that are instantly compatible with your preferred SIEM or EDR format.
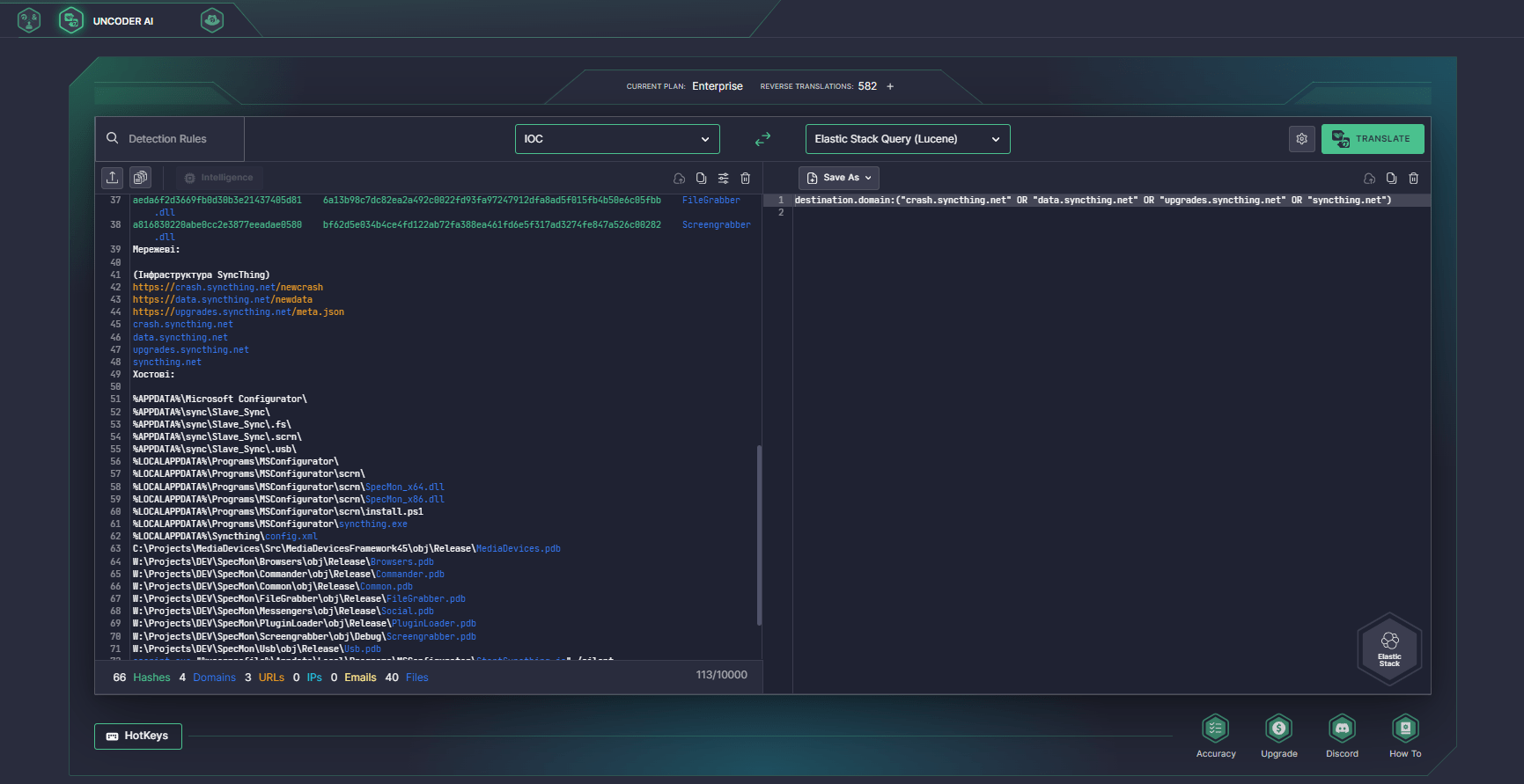
MITRE ATT&CK Context
By leveraging MITRE ATT&CK, cyber defenders might obtain detailed insights into the context of the latest offensive operation by UAC-0020, targeting the Armed Forces of Ukraine. Check out the table below to view the comprehensive list of specific Sigma rules that correspond to the relevant ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Initial Access | Spearphishing Attachment (T1566.001) | |
Execution | Command and Scripting Interpreter: Visual Basic (T1059.005) | |
User Execution: Malicious File (T1204.002) | ||
Collection | Data From Local System (T1005) | |
Exfiltration | Automated Exfiltration (T1020) | |
Exfiltration Over Alternative Protocol (T1048) | ||




