SOC Prime Threat Detection Marketplace – Getting Ready to Explore
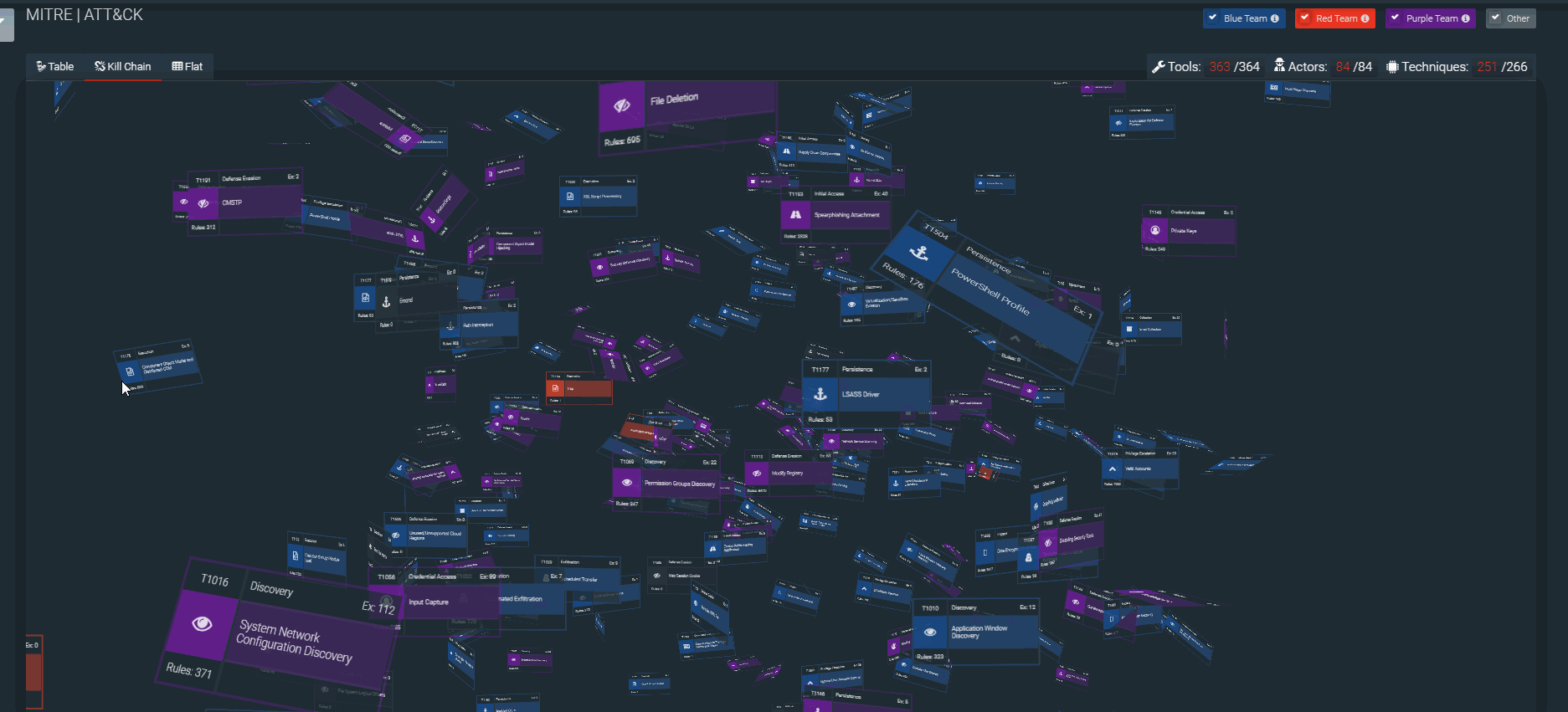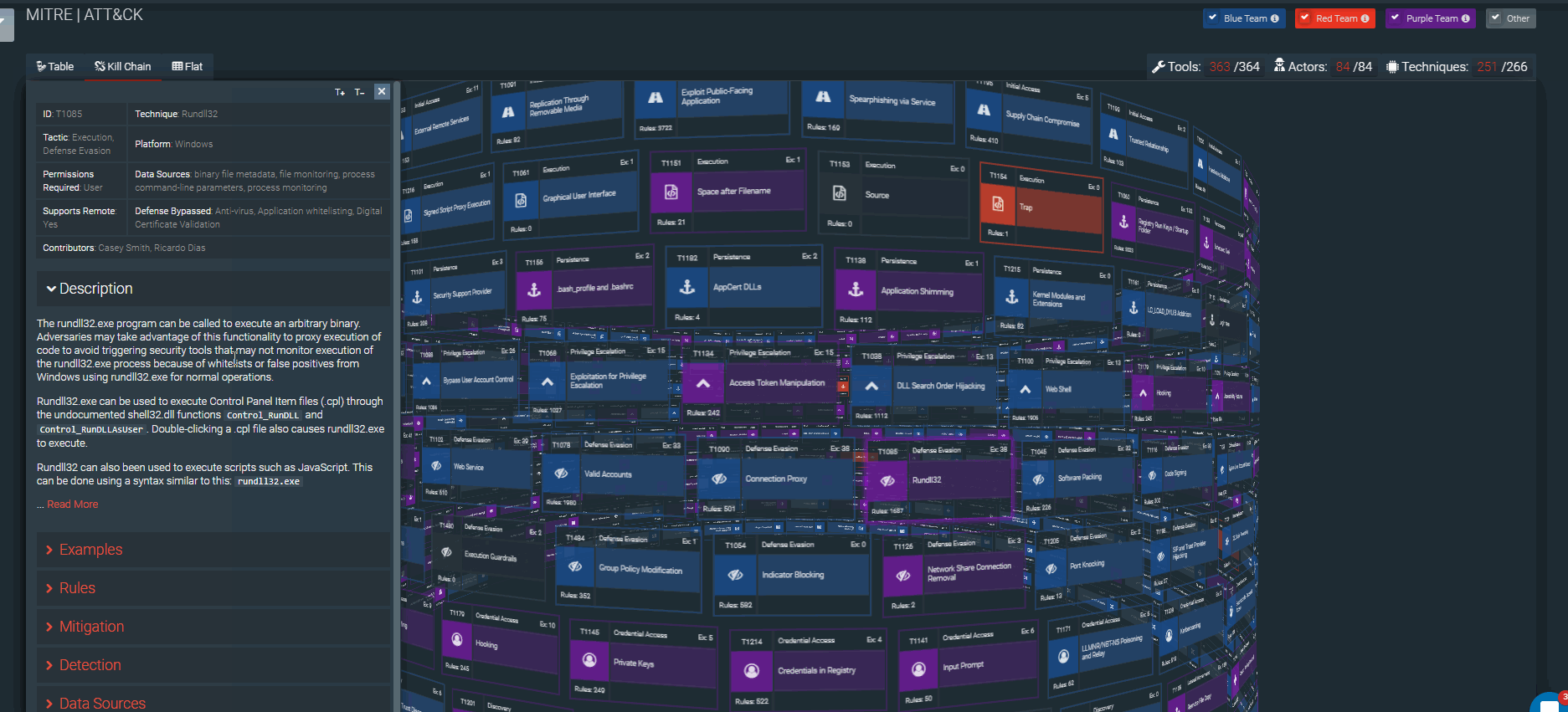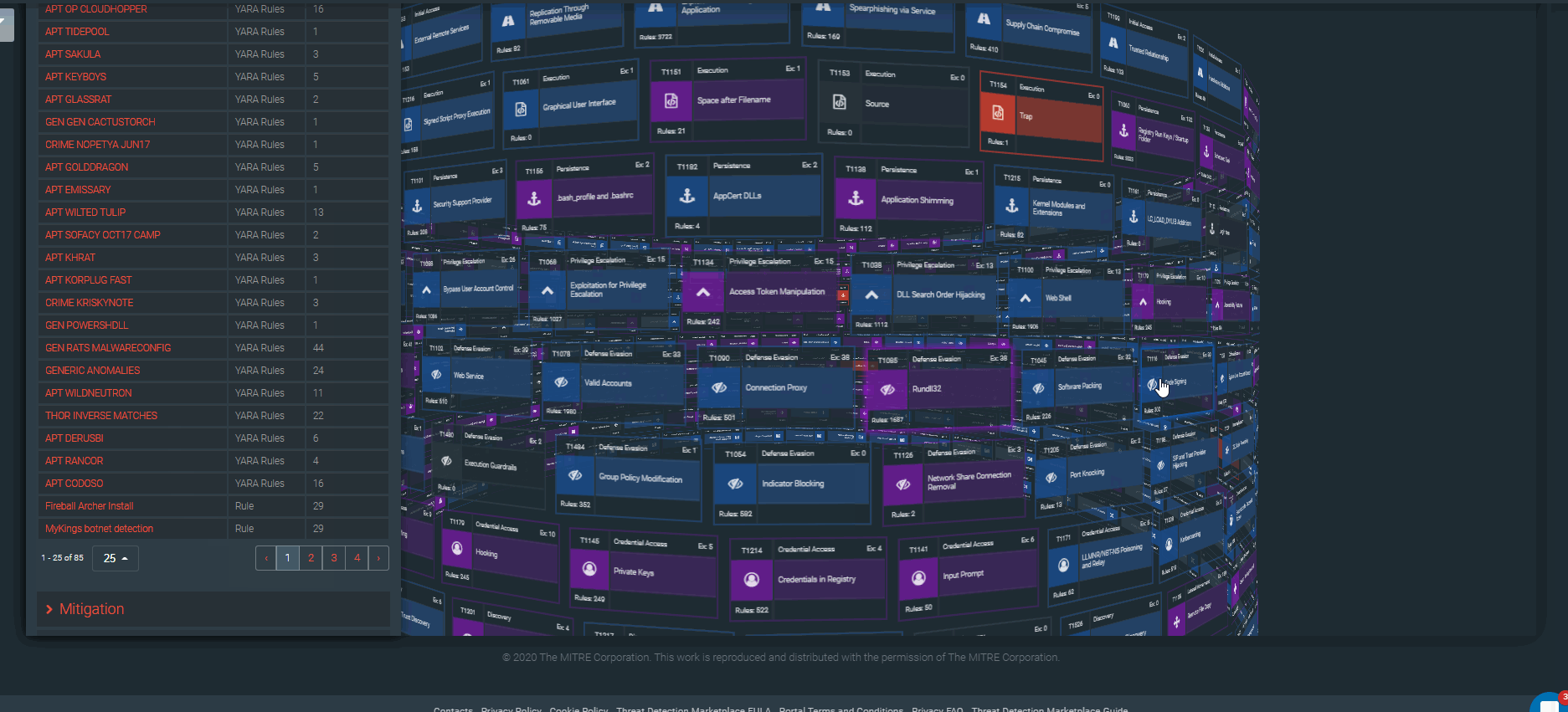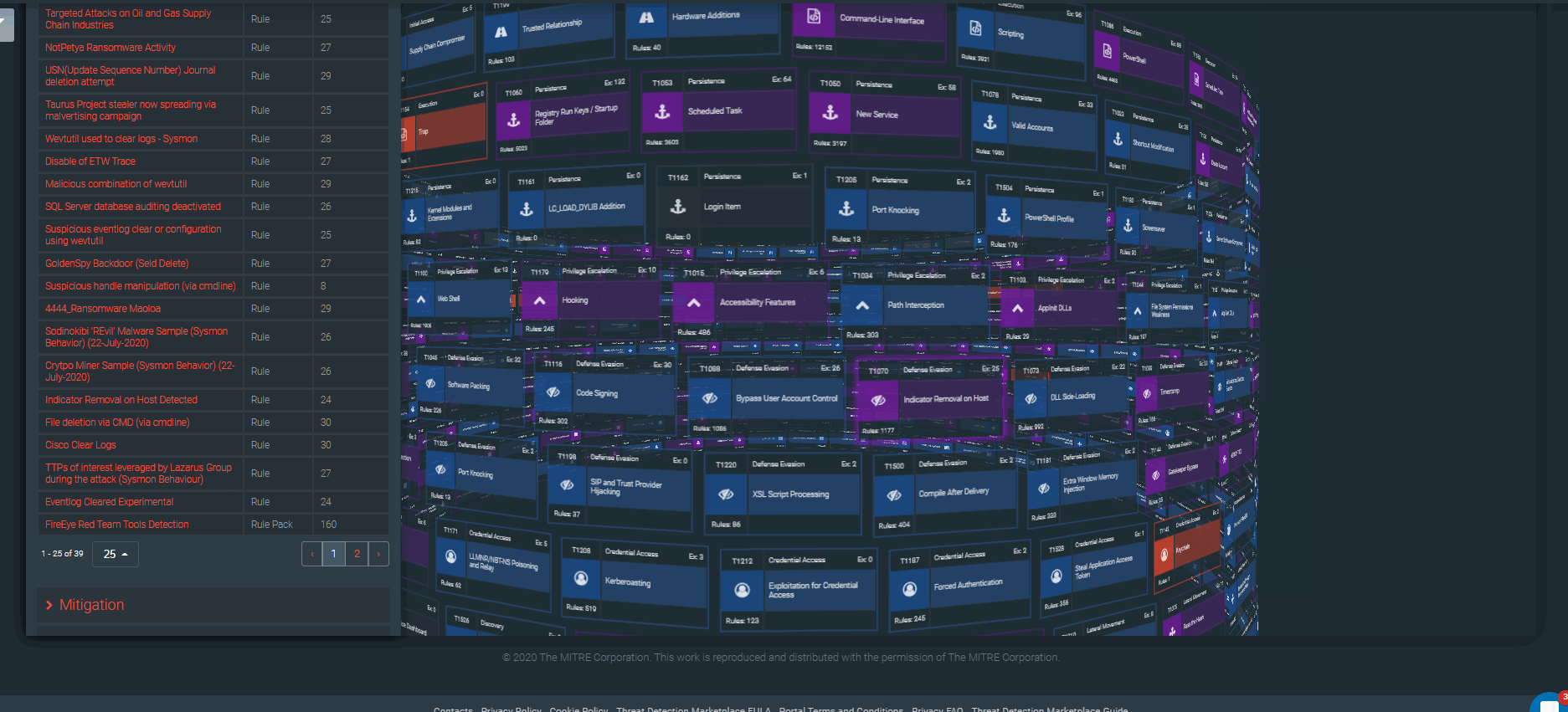
SOC Prime Threat Detection Marketplace (SOC Prime TDM) is a community-based library of relevant and actionable threat detection content that has been uniting cybersecurity content authors to stand on the defensive of cyberspace to deliver the best content to the community for more than five years already. SOC Prime TDM provides ready-made tested Rule Packs, SIGMA rules, YARA rules, RED tests, Snort rules, parsers, natively integrating applications as well as support services for the most used SIEM, EDR, and NTDR solutions. More than 94% of Threat Detection Marketplace content is mapped against the MITRE ATT&CK® matrix. Each technique has a list of security-sensitive platforms, examples of known attacks, detection instructions that along with the number of rules that are aimed at spotting suspicious behavior and protecting the company’s infrastructure.
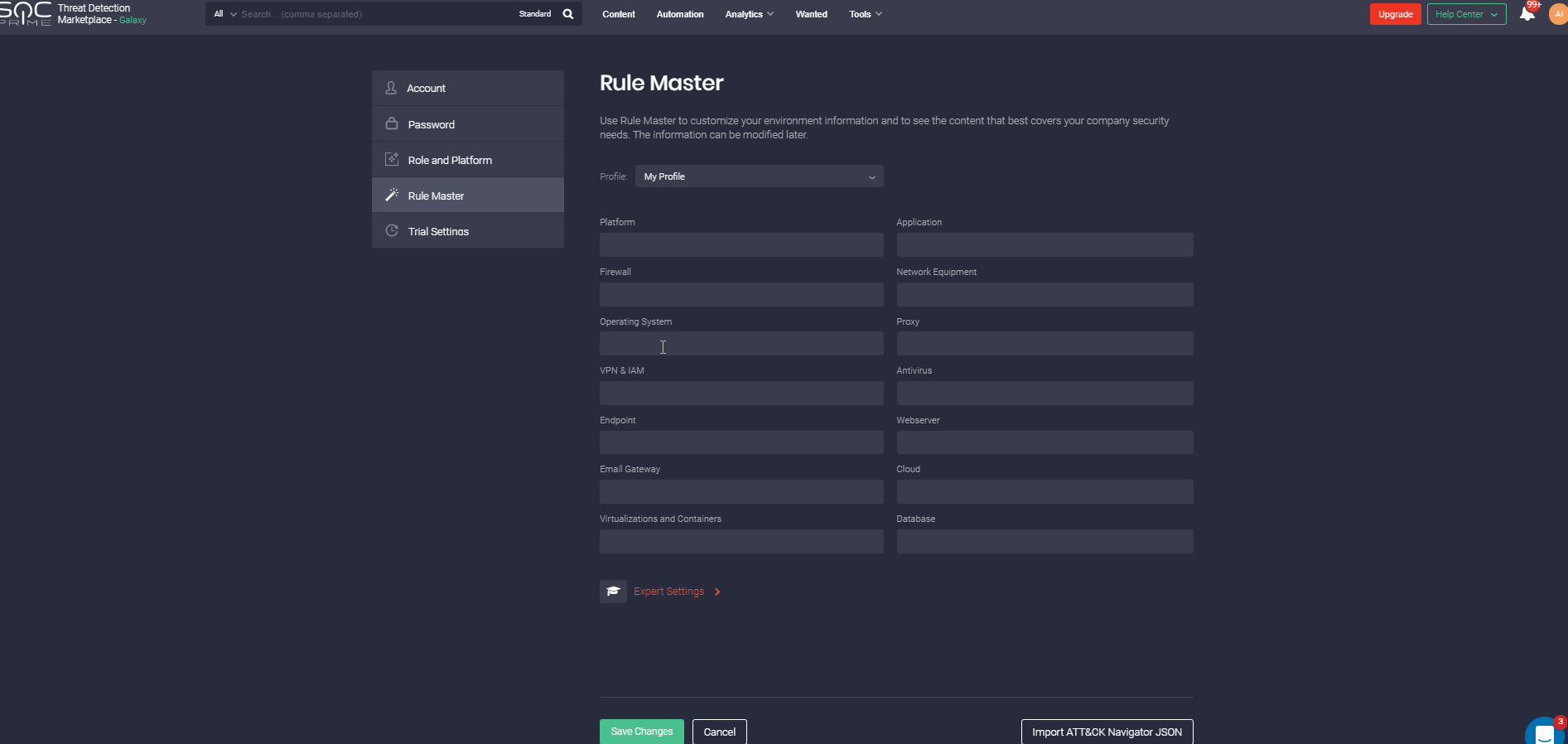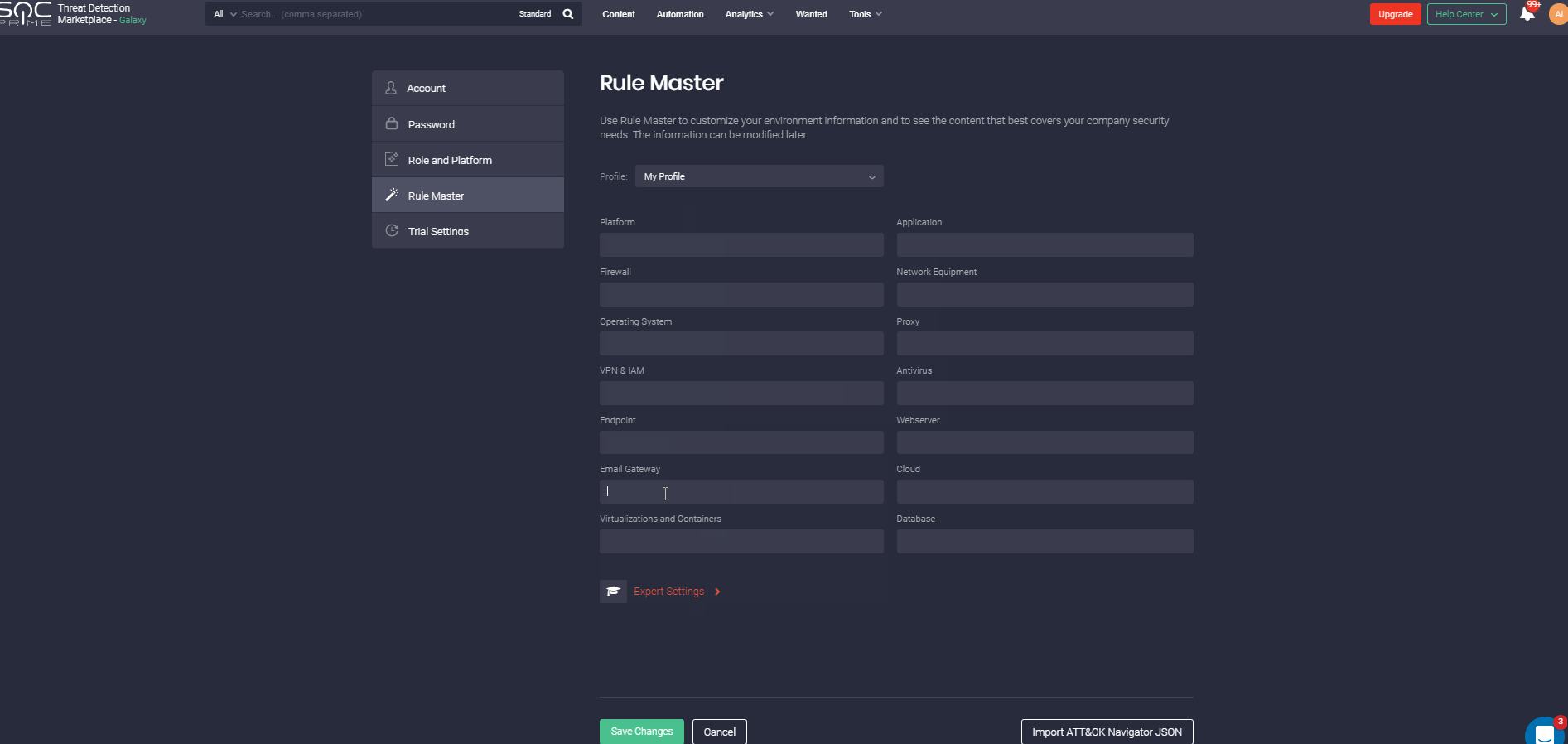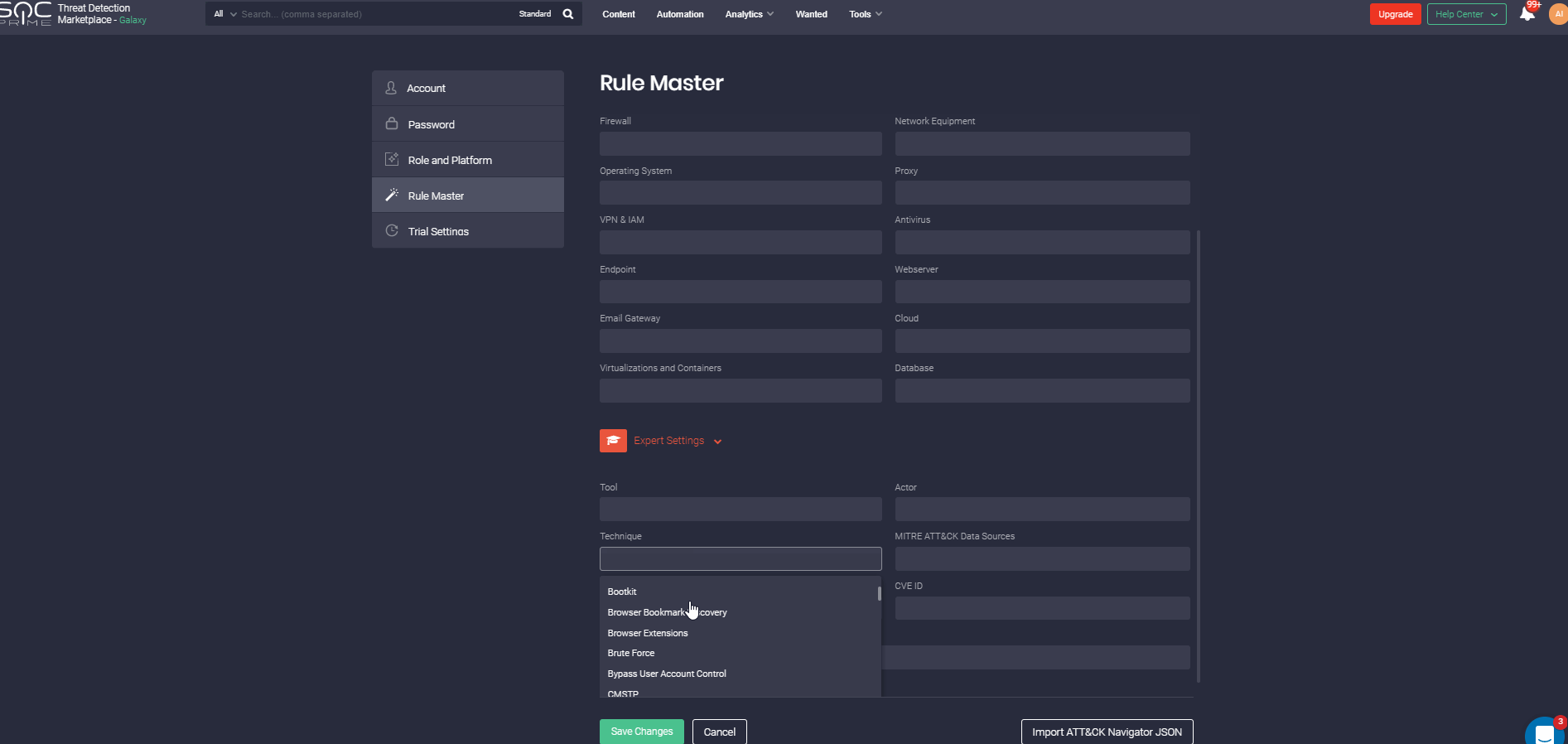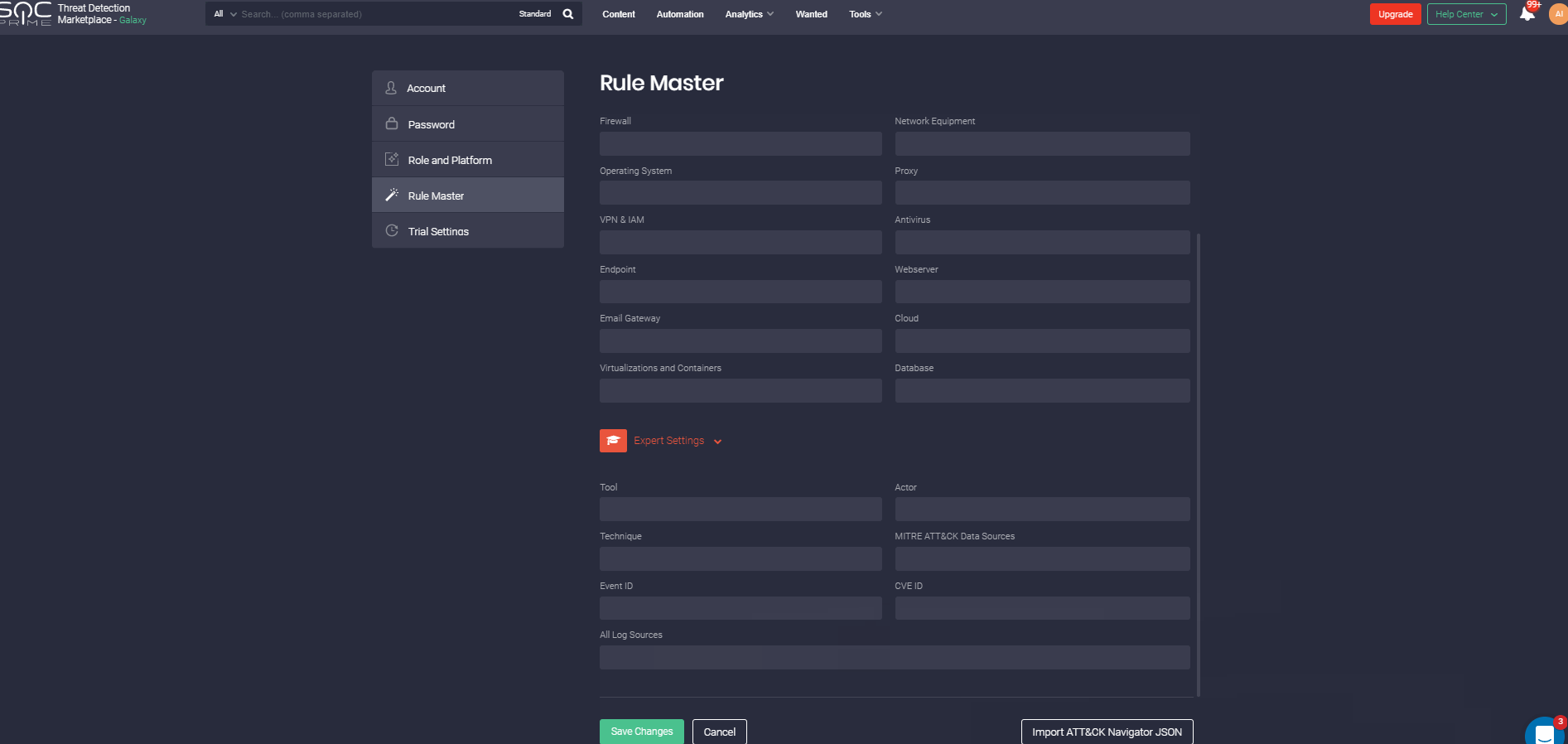
Looking for threat detecting content at SOC Prime TDM with more than 100k rules is much easier than picking a needle out of the haystack, though it may not seem so. We’ve garnished the searching capabilities with the profile configuration option. Rule Master allows flexible customization to display the content that best meets your company’s security requirements by specifying information about the environment so that you will be informed about the most suitable, recommendable, and up-to-day content first. However, the Rule Master doesn’t oblige you to look through the Rules that only meet your profile configuration. You can easily switch on/off this option in the Filter panel.
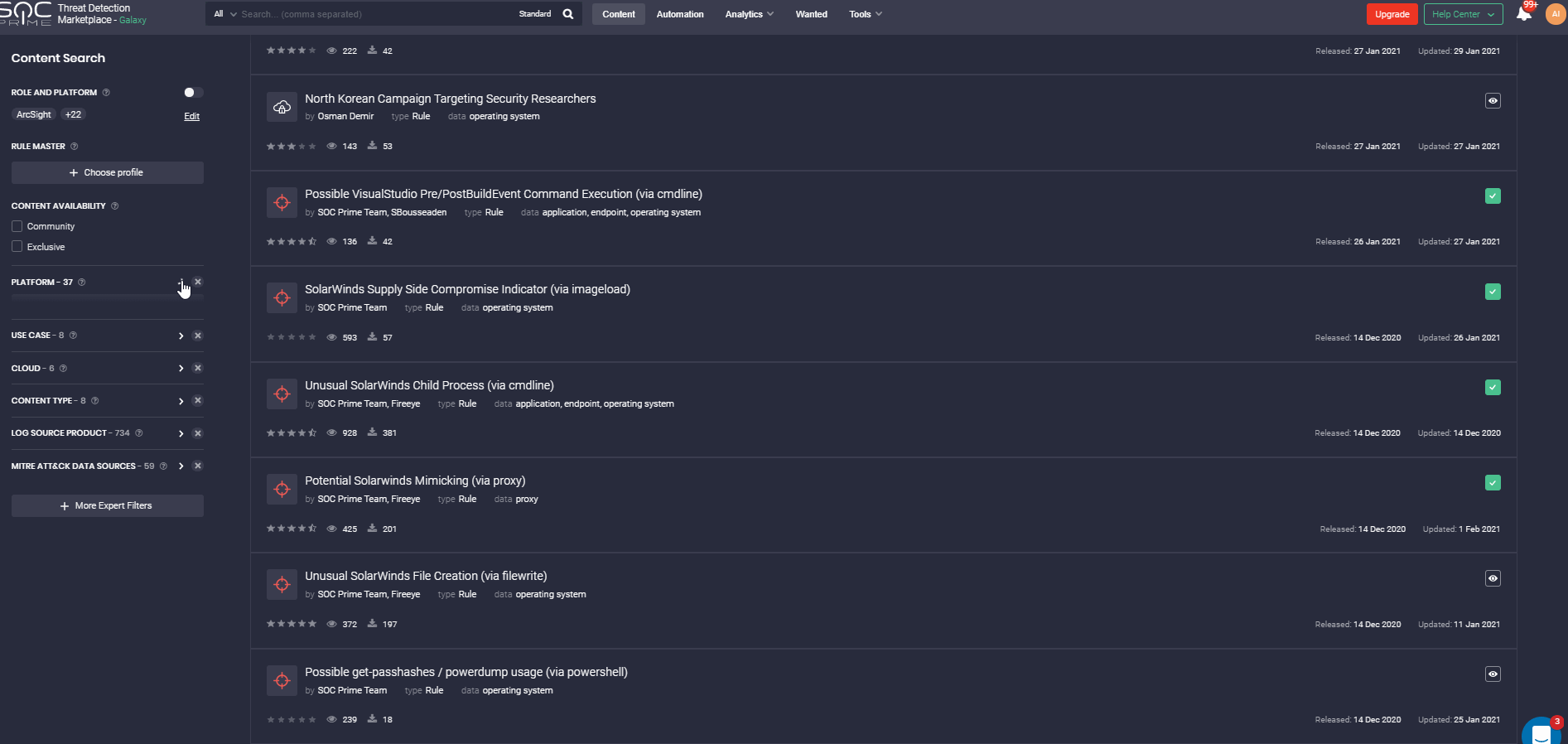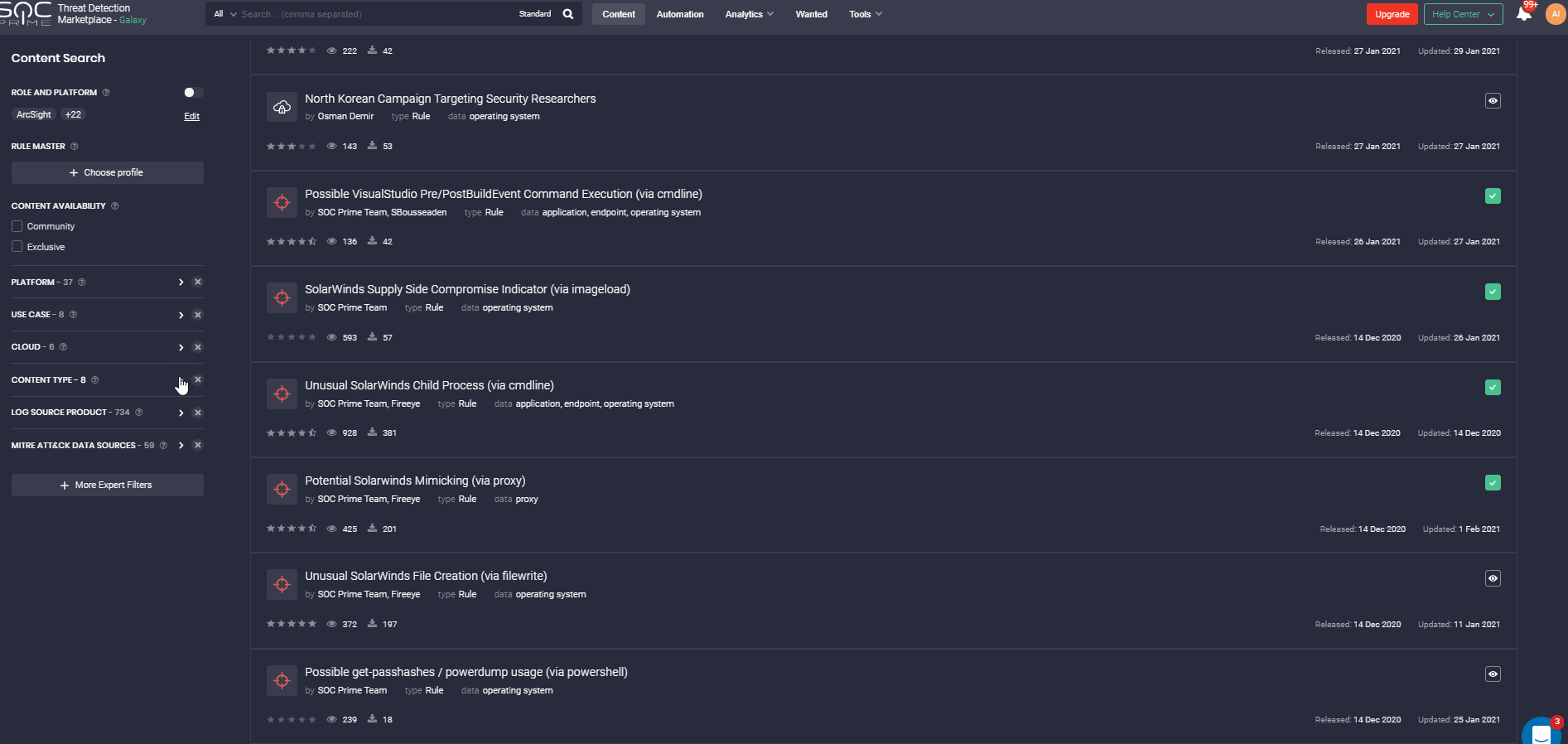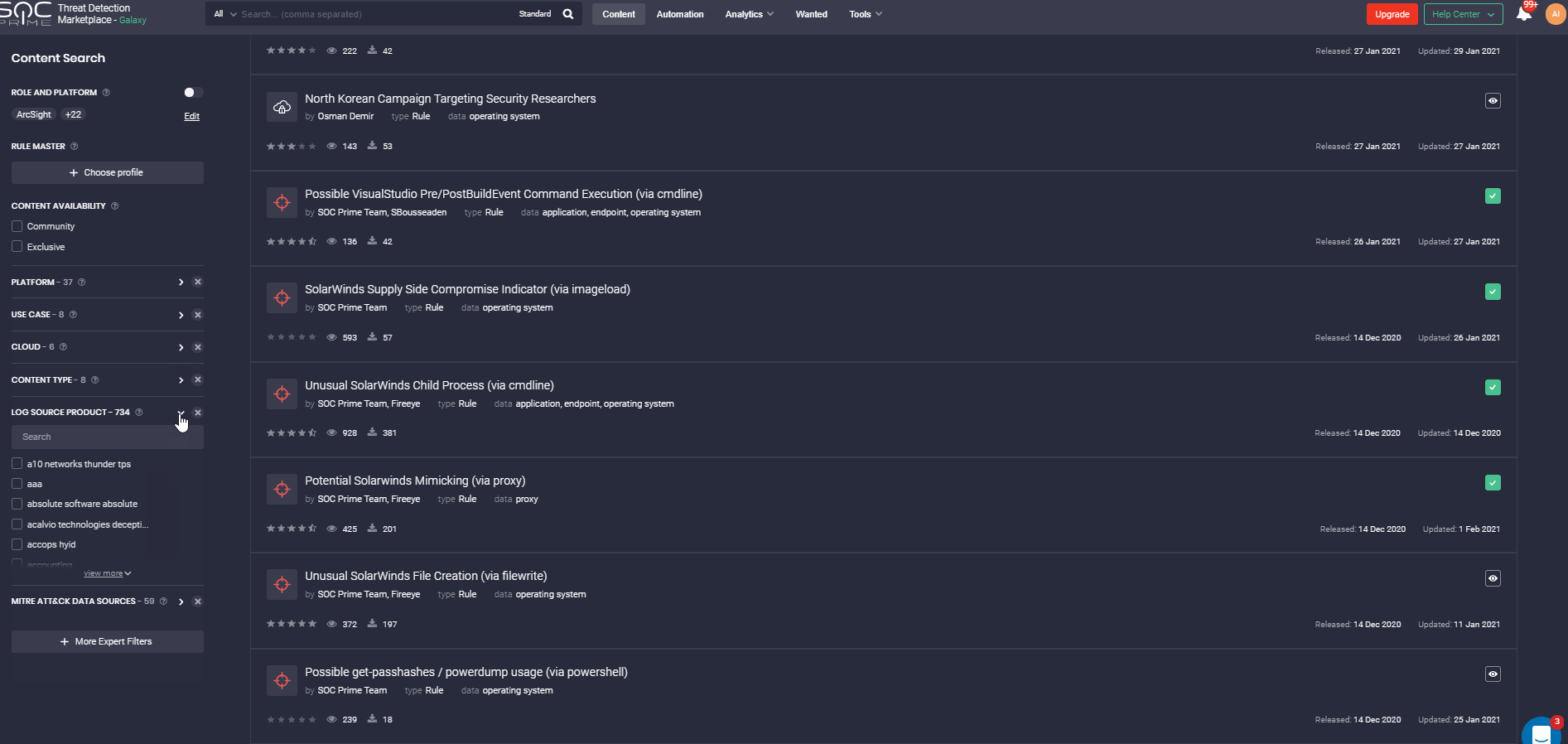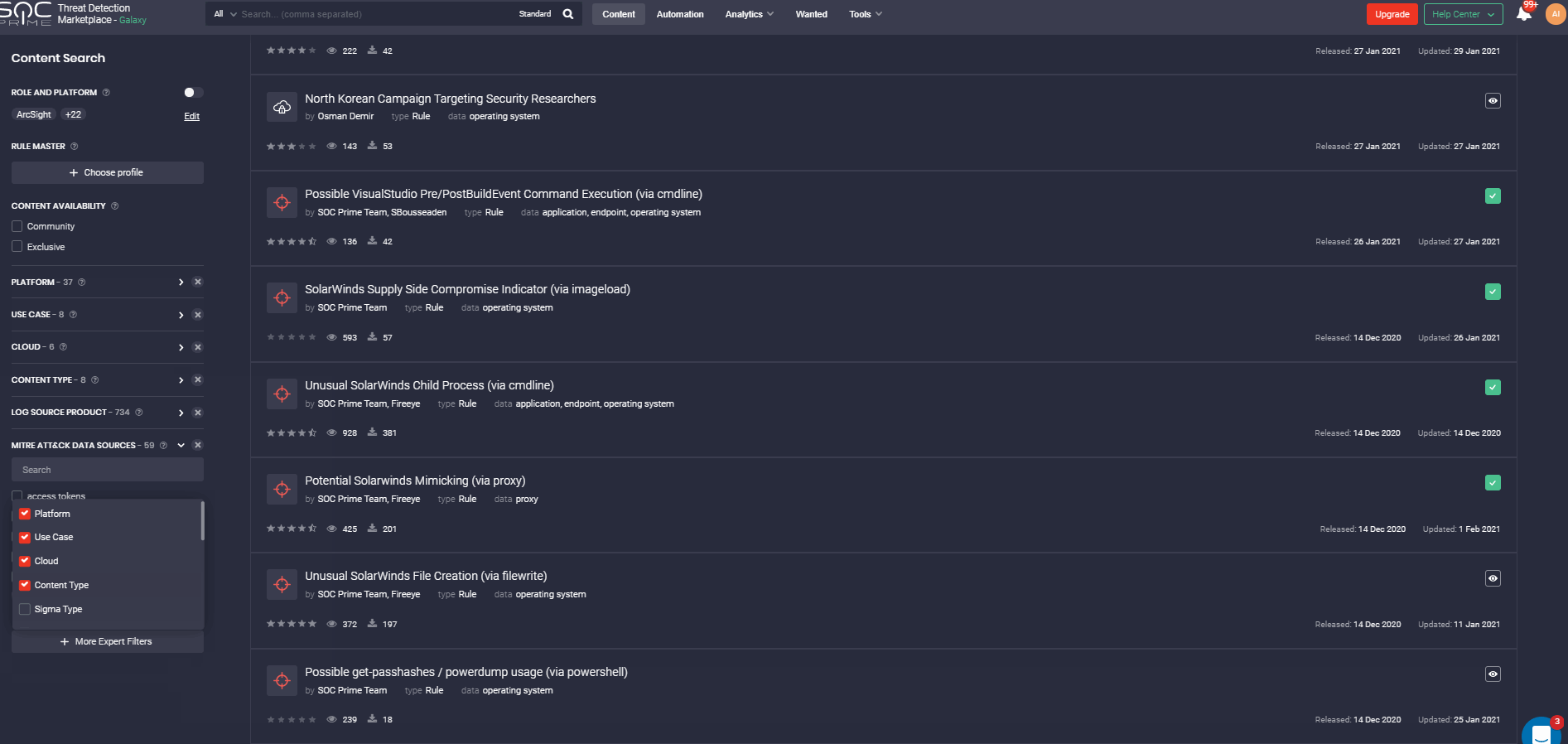
Also, the Filter panel allows displaying content that meets certain criteria: platforms, OS, log sources, data sources, executor, content authors, etc. You may indicate the required content type, content availability type, or even specify the type of Sigma rule – IOC, Threat hunting, or Compliance. If you looking for content focusing on MITRE methodology, you can filter out the content that is mapped against certain Actors, Tools, Tactics, or Techniques.
Not least of all available search tools at SOC Prime is the Search panel. On the surface, it seems to be pretty simple and obvious – you can type whatever you are looking for and it suggests the TMD content color-marking its category. But we’ve brightened up the Search panel with Elastic stack search capabilities, namely the Lucene query syntax option, making it possible to specify the field names, run wildcards, embed regular expressions, use the “fuzzy” operator, specify the edit distance of specified words with proximity searches, use the boost operator, grouping, reserved characters, etc. Read more about Lucene query syntax here: https://tdm.socprime.com/search/how-to-use-lucene/
Have you already got an account at Threat Detection Marketplace? Tell us about your experience with looking for the threat detection content at SOC Prime. Join the world’s largest Threat Detection Marketplace now or publish your own content with SOC Prime Threat Bounty Program!