Why Short-Cut The Threat Hunting Process?
As with any security operations endeavor, we want to balance efficacy and efficiency to produce the best results with the smallest amount of resources.
Unfortunately, Threat Hunting is often seen as a ‘luxury’, reserved only for the most advanced sec-ops teams with ample budgets to fund expert resources and time to spend on hunting exercises with fuzzy deliverables and business value. The Threat Hunting process is undoubtedly more complex than the typical Tier I/II SOC Analyst workflow. It is also true that, historically, the outcomes of Threat Hunting have been hard to meaningfully demonstrate to stakeholders.
However, at SOC Prime, our goal is to change the status quo through better technology, tools, and community collaboration. In this article, we will review what the current Threat Hunting process looks like and how we can short-cut this process to enable teams of all sizes, levels, and maturities to start catching threats proactively.
What Does The Threat Hunting Process Look Like?
Let’s begin by establishing a highly generic framework for Threat Hunting.
- Identify a Research Subject or Topic
- Conduct Research
- Form a Hypothesis
- Test Hypothesis
- Record and Take Action on Findings
You’ll probably notice that I’ve intentionally left out detail. The corpus of expert opinion on this topic; while not extremely large, should be the primary resource for truly understanding what Threat Hunting looks like. However, in general, most Threat Hunters agree that the above bullet points are a fair summation of the general process.
*Note – SOC Prime does not claim to own this video or claim to be affiliated with Insomni’hack or the presenters. The video referenced above is to provide further context for common approaches to Threat Hunting.
This presentation by Roberto Rodriguez and Jose Luis Rordiguez is one of my favorites. Both presenters are well known thought leaders and contributors to the open-source threat hunting development community. I highly recommend watching the full length video and also checking out their respective blogs.
How To Shortcut The Threat Hunting Process
When balancing efficacy and efficiency, we’re really talking about tackling the following problems.
- Technology
Speed is key when executing complex searches over periods of time. Without getting too specific and bashing certain platforms, it is important to note that some log storage and SIEM technologies are capable of executing searches more quickly than others. The difference between a search that takes 30 seconds and 3 minutes, multiplied across hundreds of exercises a year, start to add up to real efficiency gains.
- Information
I’m intentionally casting a wide net by using the term ‘information’. Within a Threat Hunting practice, information can and should come from multiple places internally and externally to drive focus and enrich exercises. Simply put, more informed and strategic Threat hunting is more effective than hunting blindly with random searches and dashboards.
- Threat Intelligence Feeds
- Internal Honey Net
- External Honey Net
- Threat Modeling (Ideally, mapped to the MITRE ATT&CK Framework and informed by both technical and business stakeholders.)
- OSINT
- Malware Reverse Engineering
- Ideally, mapped to the MITRE ATT&CK Framework and informed by both technical and business stakeholders.
- People
We could pontificate on why having the right people is important; however, we also know that this type of conversation is less impactful given the current skills gap in the industry. Meaningful conversation in this realm is more about automating or augmenting the existing workforce.
- Processes
This is the glue that holds everything together and brings both effectiveness and efficacy to Technology, Information, and People.
I. Understanding Deliverables/Impact
- How does Threat Hunting improve your overall security posture?
- GRC
- Protection
- Detection
- Response
II. Quantifying Progress/Value
- How do you measure the progress of your Threat Hunting program?
- Does an increase or decrease in deliverables correlate with business value?
Admittedly, all of these factors are deeply related and difficult to consolidate into distinct entities. In short, in order to short-cut the threat-hunting process, we need a solution that (a) works with the best technologies, (b) provides advanced and relevant information, (c) reduces workload through automation or enrichment, and (d) provides some type of procedural structure for understanding and quantifying value.
SOC Prime’s Detection as Code platform
For the last five years, SOC Prime has been helping organizations realize Threat Hunting operations through the Detection as Code platform.
The platform is an arsenal of over 100,000 cross-platform threat-specific rules designed to solve for the technology, information, people, and processes problem in Threat Hunting.
Item (a), SOC Prime’s Detection as Code platform content is compatible with all of the top SIEM platforms.
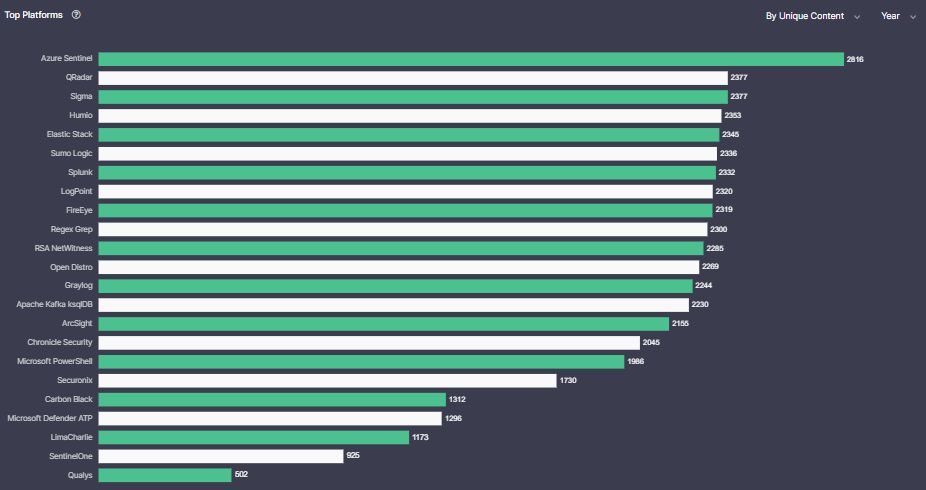
We develop content for the top SIEM platforms in the industry. Whichever platform you currently use, or are considering potentially migrating to, we’ll be ready to supply you with the right detections.
Item (b), our detection content is advanced and relevant to emerging threats.
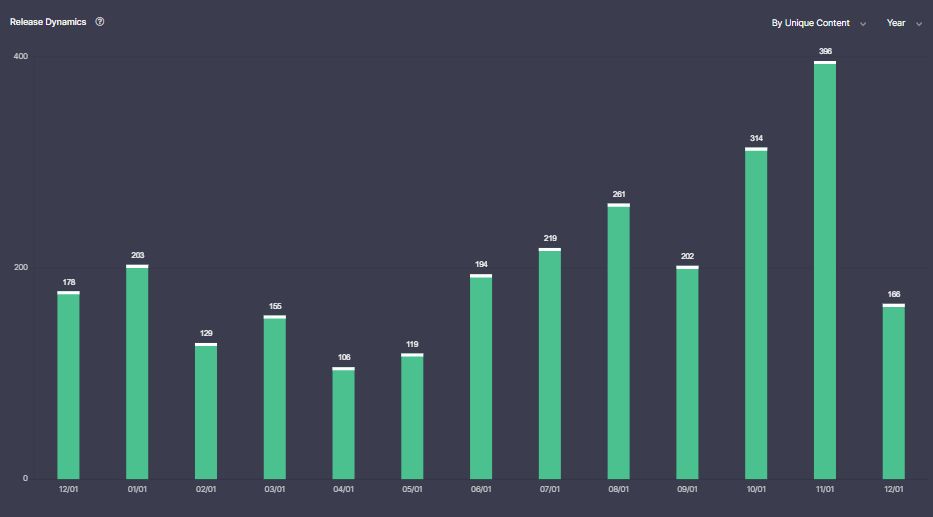
As a community platform, SOC Prime’s Detection as Code platform acts as an aggregator of new detection content created by SOC Prime’s R&D team, independent Threat Bounty Hunters, and community developers. We release and update new content daily, helping teams respond to the quickly evolving threat landscape.
Item (c), the Platform integrates with Elastic and comes with our SOC Workflow application for case/incident management, enrichment, and automation.
With over 30,000+ rules available, operationalizing content quickly is the key to success. Our SOC Workflow app is included with most paid tiers and provides native case management and SOAR-like functionality right from the stack.
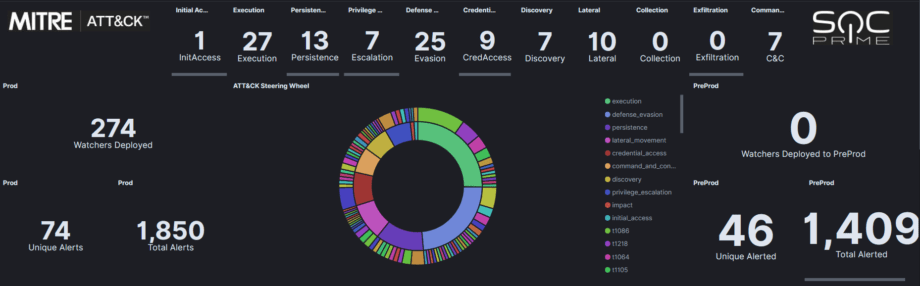
Item (d), our detection content is mapped to the MITRE ATT&CK framework to provide conceptual structure and act as a tool for communicating value and progress to stakeholders.
We map over 95% of our detection content against the MITRE ATT&CK Framework. This enables organizations to enhance their own capability by relying on the specialized expertise of our community.
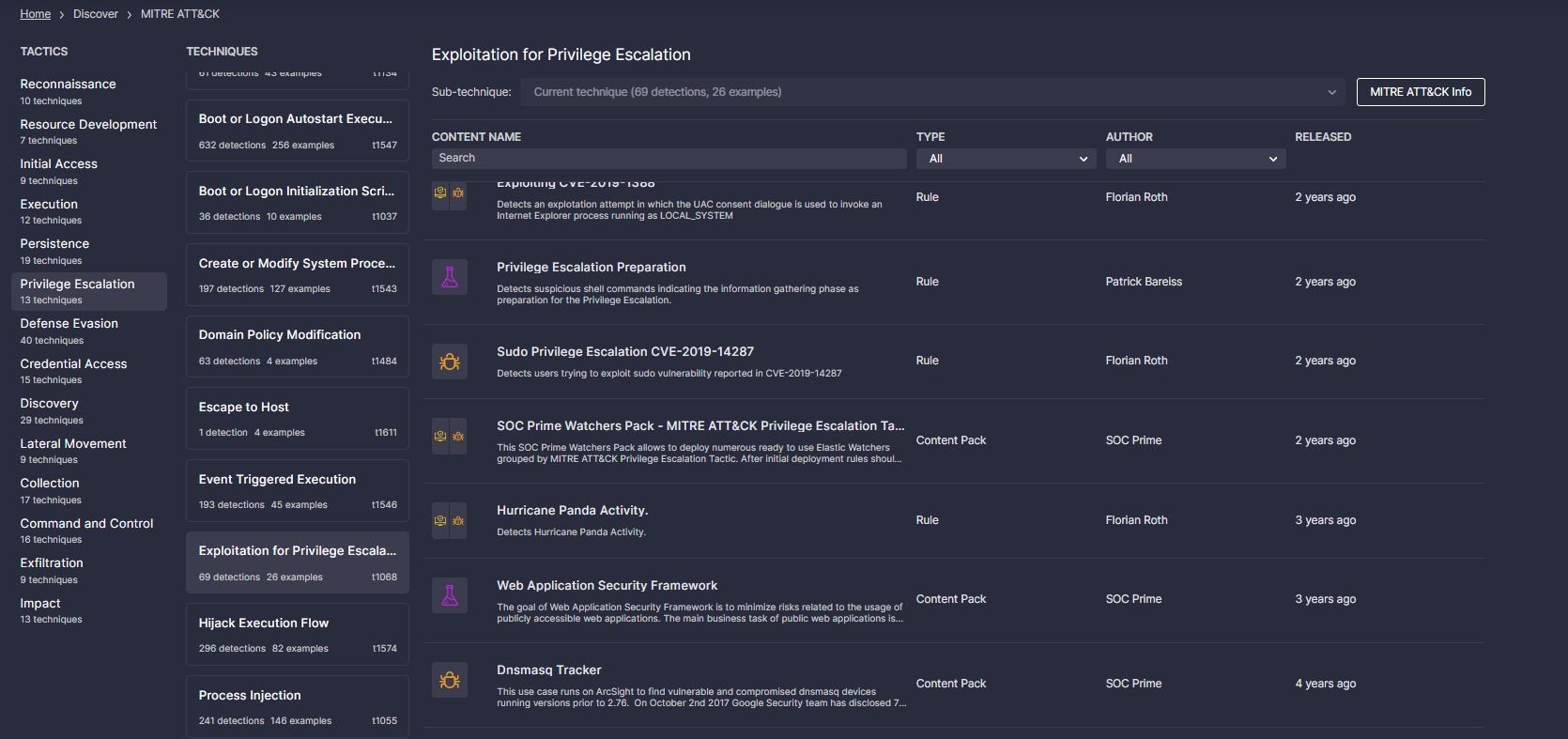 From here, teams can quickly identify hunt targets, perform additional research on relevant threat actors and TTPs, and access threat-specific queries and rules that can be used to start hunting within just a few clicks.
From here, teams can quickly identify hunt targets, perform additional research on relevant threat actors and TTPs, and access threat-specific queries and rules that can be used to start hunting within just a few clicks.
Because we map our rules to the ATT&CK framework; we can measure detection coverage across an environment and benchmark progress over time.
For example; we could be able to say that 6 months ago, you had coverage for 20/144 techniques. Today, after systematically implementing additional rules for missing techniques, you now have coverage for 60/144 techniques. That’s triple the detection coverage! Additionally, you now have a security operations roadmap that defines:
- Current Detection Gaps
- Tactics
- Techniques
- Threat Actors
- Log Sources to Acquire/Onboard
- Event Types to Configure
Example:
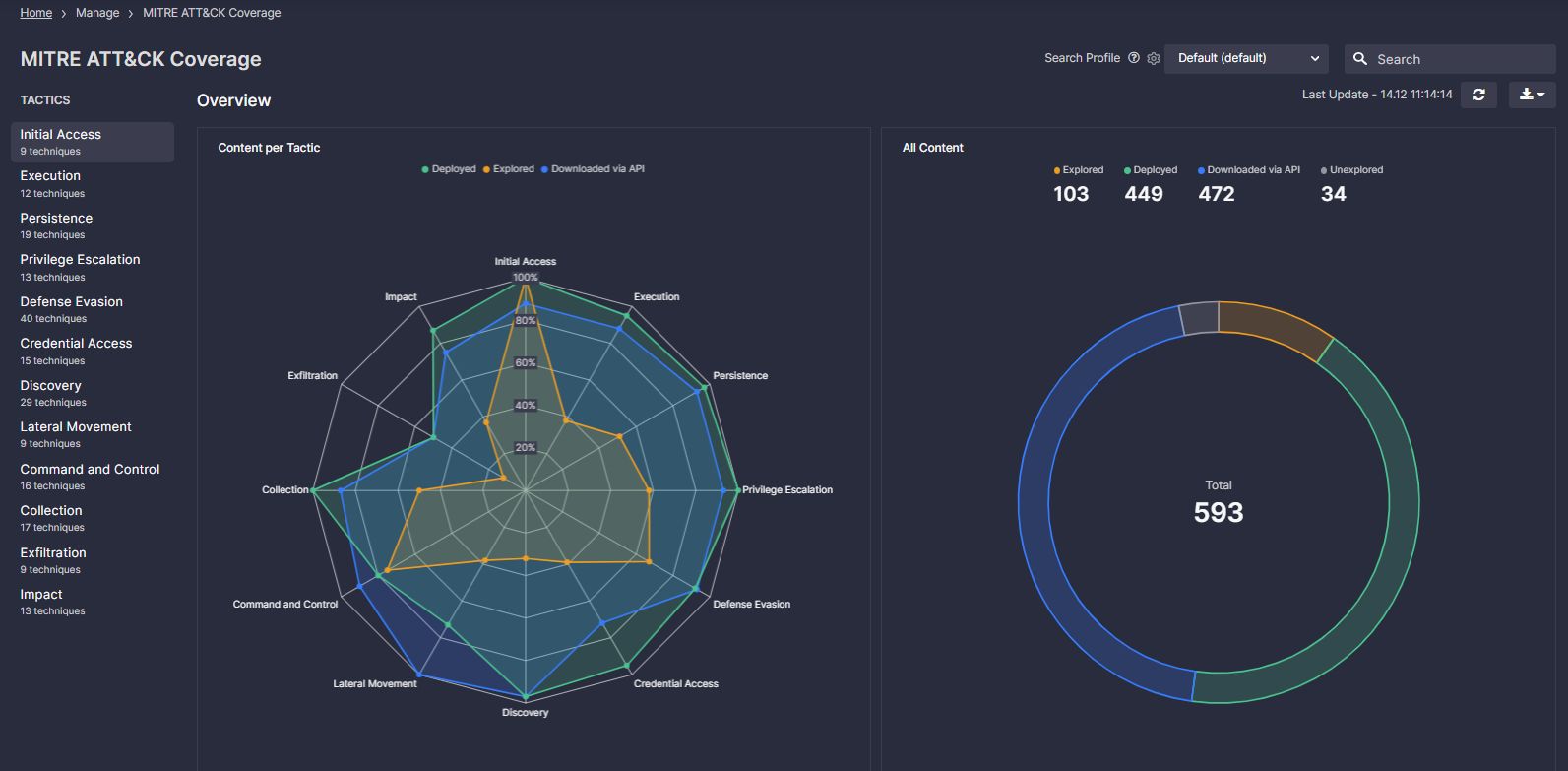
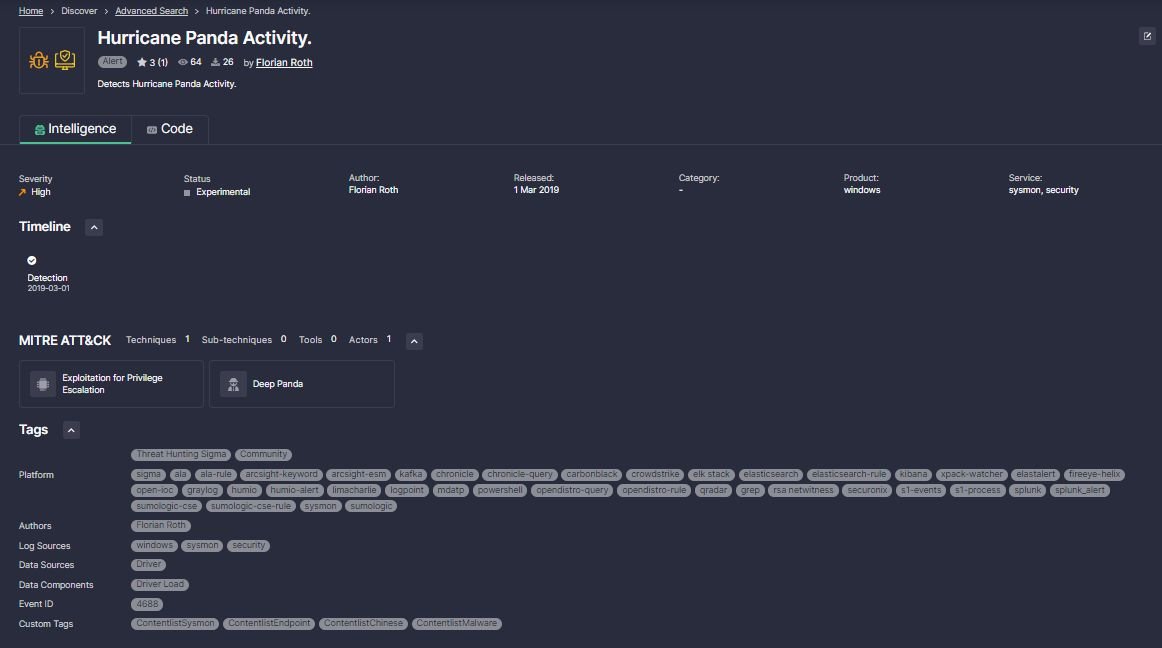
https://tdm.socprime.com/tdm/info/FHh5xhYB3zlf/
As an example, we’ve selected the “Exploitation for Privilege Escalation” Technique under the “Privilege Escalation” Tactic. From here, we were able to find the “Hurricane Panda Activity” Sigma Rule, which contains a direct reference to the research article it was based on and conditions specific to the techniques and commands that this Threat Actor users. With a rule ready to go, a Threat Hunter could quickly kick off an exercise, skipping the longest and most resource intensive phases of research and hypothesis forming.
Summary:
As a product, SOC Prime’s Detection as Code platform fulfills all four of the requirements we laid out for turbocharging the threat hunting process. Of course, we also have an entire catalog of professional services designed to also help teams deliver on these values in the all too frequent case where they are short-handed.
Community access to the Platform is free! Sign up and start exploring our detection content today at “TDM.SOCPRIME.COM”. As always, feel free to reach out to us directly with questions or for a meeting.