Hot on the heels of russia-linked BlueAlpha’s exploitation of Cloudflare Tunneling services to spread GammaDrop malware, another russia-backed state-sponsored APT group comes to the spotlight. The nefarious actor tracked as Secret Blizzard (aka Turla) APT group has been observed leveraging offensive tools and infrastructure of other hacking collectives. The group’s campaigns also focus on deploying custom malware, with the Tavdig backdoor establishing initial access to install the updated version of the backdoor called Kazuar.
Detect Secret Blizzard Attacks Spreading KazuarV2 Malware
russia-linked hacking groups remain a serious challenge for cybersecurity teams, constantly changing their tactics to attack organizations worldwide. Since the start of the war in Ukraine, these groups have increased their activity, using the conflict to test advanced malicious strategies. To help defenders stay ahead, the SOC Prime Platform offers the world’s largest collection of CTI-enriched detections backed by a complete product suite for advanced threat detection, automated threat hunting, and AI-powered detection engineering.
Hit the Explore Detections button below to access a relevant detection stack addressing TTPs used in the latest Secret Blizzard attacks. All the rules are mapped to MITRE ATT&CK, enriched with extensive metadata, and compatible with 30+ SIEM, EDR, and Data Lake technologies.
Alternatively, cyber defenders might search for relevant detection content right in the Threat Detection Marketplace by using a “Secret Blizzard” tag.
Also, to proceed with the investigation, security professionals might launch instant hunts using IOCs provided in the corresponding Microsoft Threat Intelligence research. Rely on SOC Prime’s Uncoder AI to create custom IOC-based queries in a matter of seconds and automatically work with them in your chosen SIEM or EDR environment.
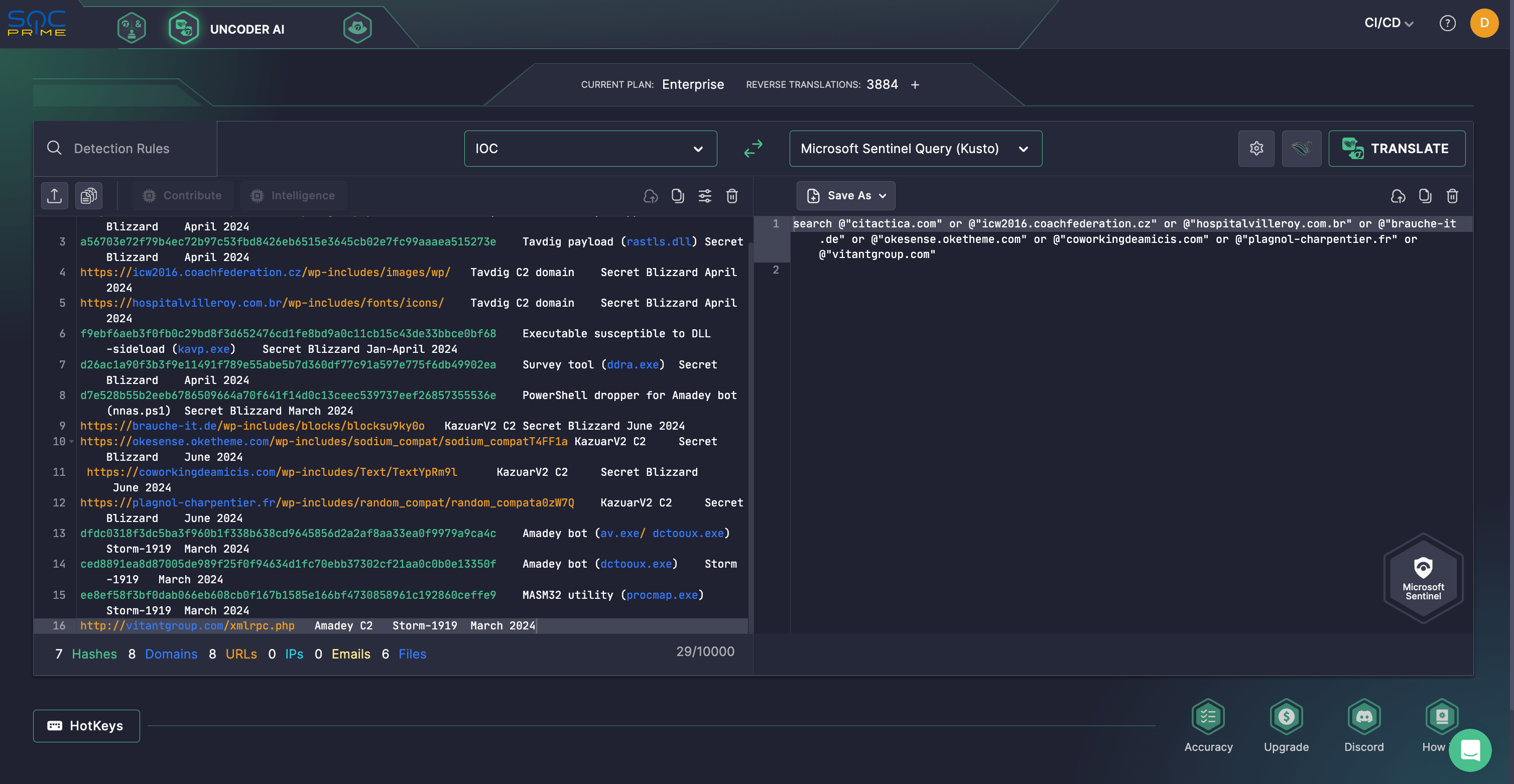
Secret Blizzard Activity Analysis: Attacks Spreading KazuarV2 Malware
Since russia’s full-scale invasion of Ukraine, cyber defenders have been overwhelmed by the sheer number of destructive attacks launched by the aggressors’s cyber-offensive forces targeting Ukraine and its allies. Defenders have recently observed an increasing activity by the russian state-backed group known as Secret Blizzard, which has been actively using malware linked to other threat actors to install the updated version of Kazuar backdoor on targeted devices in Ukraine.
According to recent findings by the Microsoft threat intelligence team, Secret Blizzard used Amadey bot malware from the offensive toolkit linked to Storm-1919 to download its own malicious samples onto compromised systems connected to the Ukrainian military in the spring of 2024. Researchers highlight that this is the second instance since 2022 that Secret Blizzard has launched a cybercriminal campaign to spread its custom malware targeting Ukrainian organizations. In January 2024, Secret Blizzard employed the backdoor of Storm-1837 (aka UAC-0149 or Flying Yeti), another russia-based actor targeting Ukrainian military drone operators, to install the Tavdig and KazuarV2 backdoors on a Ukrainian compromised instance.
Secret Blizzard is associated with the same threat actor tracked by other security vendors under the monikers Turla, Waterbug, Venomous Bear, Snake, Iron Hunter, Krypton, or Venomous Bear. It primarily focuses on government, diplomatic, and military organizations, employing various reconnaissance tools and custom malware. Notably, CISA has linked Secret Blizzard to Center 16 of russia’s FSB.
Since February 2022, Turla has been heavily involved in cyberespionage campaigns aimed at Ukraine, concentrating on reconnaissance and exploiting phishing attacks to steal credentials and other sensitive information. At the turn of 2023, Turla APT used legacy Andromeda USB-delivered malware to deploy new backdoors and custom reconnaissance tools in their adversary campaign targeting Ukraine.
Researchers are unsure if Turla hijacked or purchased access to the Amadey botnet, but the latest campaign highlights the group’s tendency to hide behind other hacker collectives. It is believed Secret Blizzard either used Amadey MaaS or secretly accessed its C2 panels to deploy a PowerShell dropper on impacted devices.
The investigation didn’t uncover the two DLLs typically used by Amadey bots on devices accessed by Secret Blizzard, but they were likely used to collect clipboard data and browser credentials. Secret Blizzard also deployed a custom reconnaissance tool to target systems linked to STARLINK IPs, often associated with Ukrainian military devices. This tool decrypted a batch script or cmdlets using a custom RC4 algorithm.
The batch script collected details about the victim device and checked if Microsoft Defender was active or flagged the Amadey bot’s activity. The custom reconnaissance tool in use also helped Secret Blizzard to identify high-value targets, deploying a PowerShell dropper with the Tavdig backdoor and a vulnerable Symantec binary for DLL sideloading. Tavdig malware enabled further reconnaissance, gathering user data, network stats, and patch information while also installing registry keys for KazuarV2 backdoor persistence.
Secret Blizzard’s operations rely on third-party footholds to establish valuable espionage access. The group has adapted its own adversary toolkit for espionage in large domain environments and tailored it for Ukrainian military targets. Additionally, the group might be striving to escalate access toward strategic ministry-level systems.
The increasing attacks by Secret Blizzard against Ukraine, combined with the group’s tactic of concealing itself behind other hacking groups, demand swift and proactive responses from defenders. SOC Prime Platform for collective cyber defense equips security teams with cutting-edge solutions to elevate threat detection and hunting capabilities, significantly reduce the attack surface, and build a robust cybersecurity posture.




