Since a full-fledged war in Ukraine, russia-backed hacking collectives have intensified their malicious activity against Ukraine and its allies in the cyber front line to conduct espionage operations and cripple the critical systems. For instance, a nefarious Sandworm APT group (aka UAC-0082, UAC-0145, APT44) has been attacking Ukrainian organizations for over a decade, primarily targeting government agencies and the critical infrastructure sector.
The Symantec and Carbon Black researchers have recently uncovered a two-month-long campaign targeting a major business services company in Ukraine and a separate week-long attack against a local state body. Notably, attackers primarily relied on Living-off-the-Land (LotL) techniques and dual-use tools to achieve persistent access.
Detect Latest Attacks Against Ukraine by russian Hackers
Cyber defenders are facing growing pressure as russian threat actors evolve their tactics and sharpen their stealth capabilities. Since the beginning of the war in Ukraine, these state-backed APT groups have intensified operations, exploiting the conflict to experiment with and refine cutting-edge cyberattack strategies. And this activity has a global impact as russia-linked actors now rank second worldwide among APT attack sources, according to ESET APT Activity Report for Q4 2024–Q1 2025.
Register for the SOC Prime Platform to detect potential russian APT attacks at the earliest stage possible. Click the Explore Detections button below to access a curated stack of detection rules designed to identify and respond to the most recent campaign leveraging LotL tactics, dual-use tools, and a custom Sandworm-linked webshell to target Ukrainian organizations.
Alternatively, cyber defenders might search for relevant detection content right in the Threat Detection Marketplace by using “Sandworm” or “Seashell Blizzard” tags.
All the rules in the SOC Prime Platform are compatible with multiple SIEM, EDR, and Data Lake solutions and are mapped to the MITRE ATT&CK® framework. Additionally, each rule is packed with detailed metadata, including threat intel references, attack timelines, triage recommendations, and more.
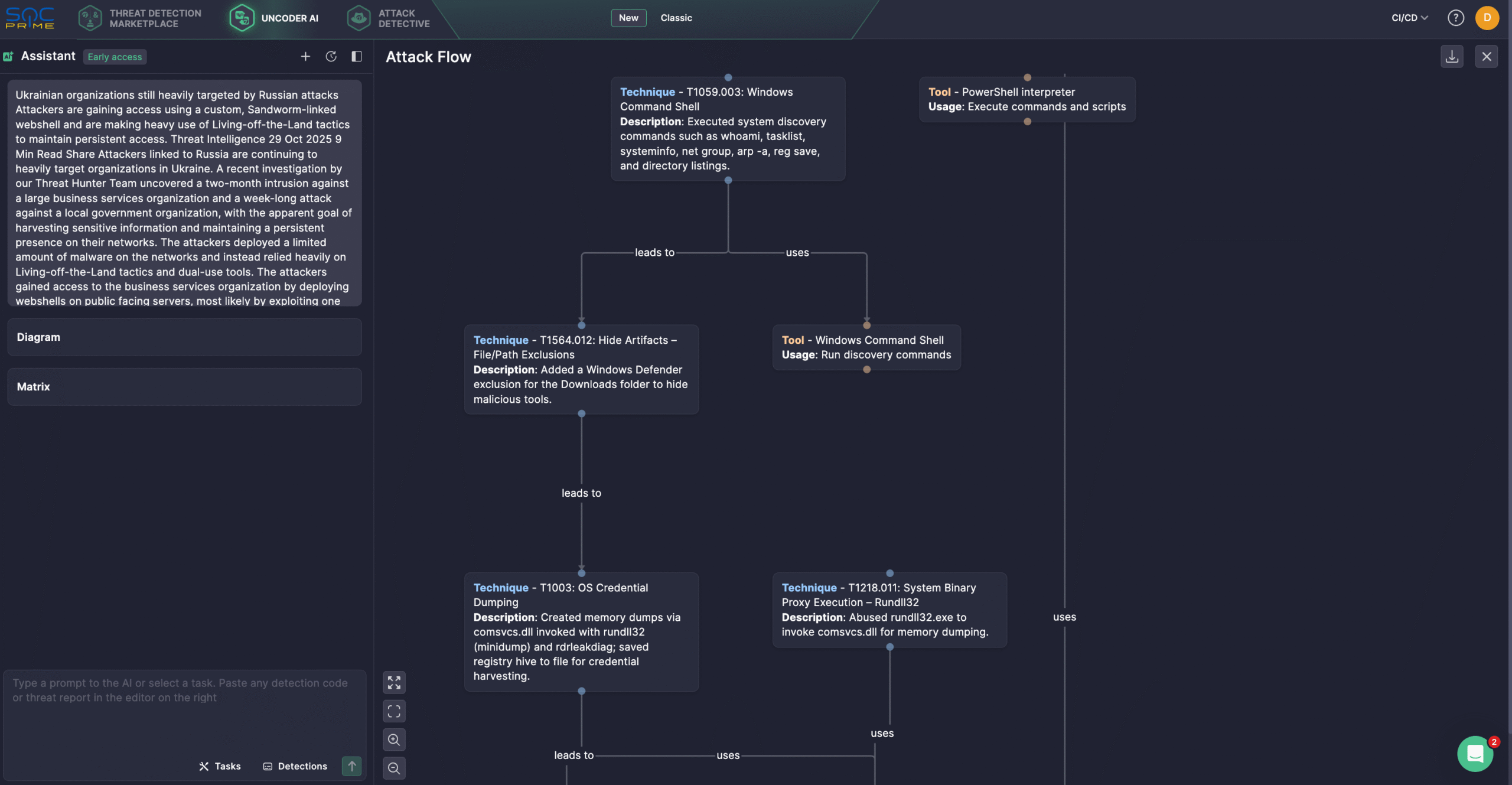
Additionally, security experts might streamline threat investigation using Uncoder AI, a private IDE & co-pilot for threat-informed detection engineering. Generate detection algorithms from raw threat reports, enable fast IOC sweeps, predict ATT&CK tags, optimize query code with AI tips, and translate it across multiple SIEM, EDR, and Data Lake languages. For instance, security professionals can use Symantec and Carbon Black most recent report to generate an Attack Flow diagram in several clicks.
Ukraine Attacked by russian Hackers: The Latest Campaign Analysis
The russia-linked threat actors have been launching intensive attacks on Ukrainian organizations since the onset of russia’s full-scale invasion. The Symantec and Carbon Black Threat Hunting team has recently identified a persistent two-month-long campaign compromising a major business services company and a week-long intrusion into a local state entity. Both campaigns apparently intended to collect sensitive data and maintain persistent network access. Instead of deploying large-scale malware, the adversaries primarily used LotL techniques and dual-use tools to operate stealthily within the environments.
Adversaries infiltrated the business services company by installing webshells on publicly accessible servers, likely by exploiting unpatched vulnerabilities. Among the tools used was Localolive, a custom webshell previously linked by Microsoft to a Sandworm subgroup (also known as Seashell Blizzard) and observed in an earlier long-running Sandworm intrusion campaign codenamed BadPilot to establish initial access.
Sandworm APT associated with Russia’s GRU military intelligence is notorious for espionage and destructive operations. The group has been linked to malicious operations targeting Ukraine’s power grid, the VPNFilter attacks against routers, and the AcidRain wiper campaign against Viasat satellite modems, and is also known for targeting IoT devices. In February 2025, the group was behind another long-term campaign active since 2023, in which adversaries employed trojanized Microsoft Key Management Service (KMS) activators and fake Windows updates to compromise Ukrainian systems.
Malicious activity at the targeted organization began in late June 2025, when attackers attempted to install a webshell from a remote IP address. After gaining access, they executed a series of reconnaissance commands (whoami, systeminfo, tasklist, net group) to map the environment. They then disabled Windows Defender scans for the Downloads folder, suggesting admin-level privileges, and created a scheduled task to perform periodic memory dumps, likely to extract credentials.
Two days later, a second webshell was deployed, followed by additional network reconnaissance. Activity later spread to other systems. On the second computer, adversaries searched for Symantec software, listed files, and checked for KeePass processes, indicating an attempt to access stored passwords. Subsequent actions included more memory dumps (using rdrleakdiag), reconfiguration of Windows Defender, and the execution of suspicious binaries, such as service.exe and cloud.exe, whose names resembled webshells used elsewhere in the intrusion. Another notable aspect of the intrusion was the use of a legitimate MikroTik router management tool (winbox64.exe), which the attackers placed in the Downloads folder of the affected systems. Notably, CERT-UA also reported the use of winbox64.exe in April 2024, linking it to a Sandworm campaign aimed to disrupt the information and communication technology (ICT) systems of the energy, water, and heat supply sector across 20 organizations in Ukraine.
While defenders found no direct evidence linking the recent intrusions to Sandworm, they assumed that the operations appeared to originate from russia. The investigation further revealed the use of multiple PowerShell backdoors and suspicious executables likely representing malware, though none of these samples have yet been recovered for analysis.
Adversaries displayed deep expertise with native Windows tools, proving how a skilled operator can escalate activity and exfiltrate sensitive information, including credentials, while remaining on the network with almost no visible traces. As potential mitigation measures to reduce the risks of russian-backed attacks, defenders recommend applying the Symantec Protection Bulletin.
With the increasing attempts of russia-backed hacking collectives to compromise Ukraine and its allies, organizations should be ready to thwart such stealthy threats before they escalate into attacks. By relying on SOC Prime’s complete product suite backed by AI, automation, and real-time threat intelligence, security teams can preempt cyber-attacks of any sophistication and fortify the organization’s defenses. Exclusively for MDE customers, SOC Prime also curates a Bear Fence pack to enable automated threat hunting for APT28 and 48 more russia’s state-sponsored actors, letting teams automatically hunt for Fancy Bear and its siblings through an exclusive Attack Detective scenario using 242 hand-picked behavior rules, over 1 million IOCs, and a dynamic AI-driven TTP feed.




