We are pleased to present to you the latest Rule Digest, which, unlike the previous digest, consists of rules developed by the SOC Prime Team only. This is a kind of thematic selection since all of these rules helps to find malicious activity via cmdline by analyzing sysmon logs.
But before moving directly to the Rule Digest, let’s recall what the rules of the SOC Prime Threat Bounty Program members were published on our blog this week.
Rule of the Week: Turla Group by Ariel Millahuel: https://socprime.com/blog/rule-of-the-week-turla-group/
Detection Content: Scarab Ransomware by Ariel Millahuel: https://socprime.com/blog/detection-content-scarab-ransomware/
Threat Hunting Content: PipeMon malware detection by Ariel Millahuel: https://socprime.com/blog/threat-hunting-content-pipemon-malware-detection/
IOC Sigma: GreenBug APT Group Activities by Emir Erdogan: https://socprime.com/blog/ioc-sigma-greenbug-apt-group-activities/
Detection Content: Malspam Downloads Zloader Malware by Emir Erdogan: https://socprime.com/blog/detection-content-malspam-downloads-zloader-malware/
Now let’s see what rules got into the digest this week.
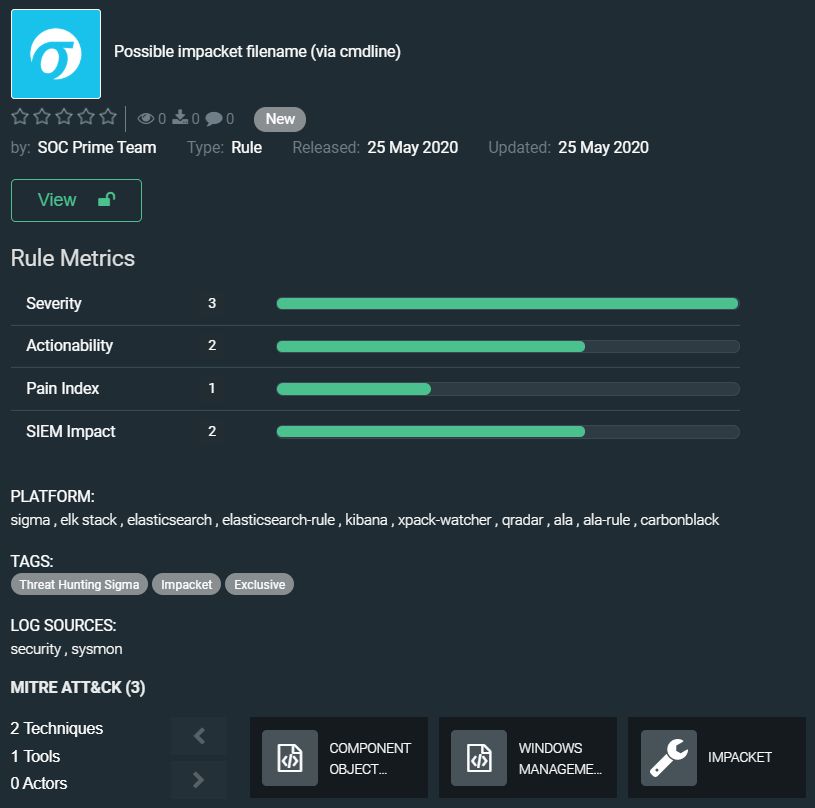
Possible impacket filename (via cmdline) by SOC Prime Team
https://tdm.socprime.com/tdm/info/BPKo7b7xyKlM/0QphTHIBAq_xcQY4IElg/?p=1
Impacket is an open source collection of modules written in Python for programmatically constructing and manipulating network protocols. Impacket contains several tools for remote service execution, Kerberos manipulation, Windows credential dumping, packet sniffing, and relay attacks. Default file names exist in the Windows directory (i.e C:windows) and contain the pattern __##### as a result of ‘__’ + str(time.time()). Hits may be empty or contain command output (i.e. such as the output of discovery commands like net/ipconfig/etc)
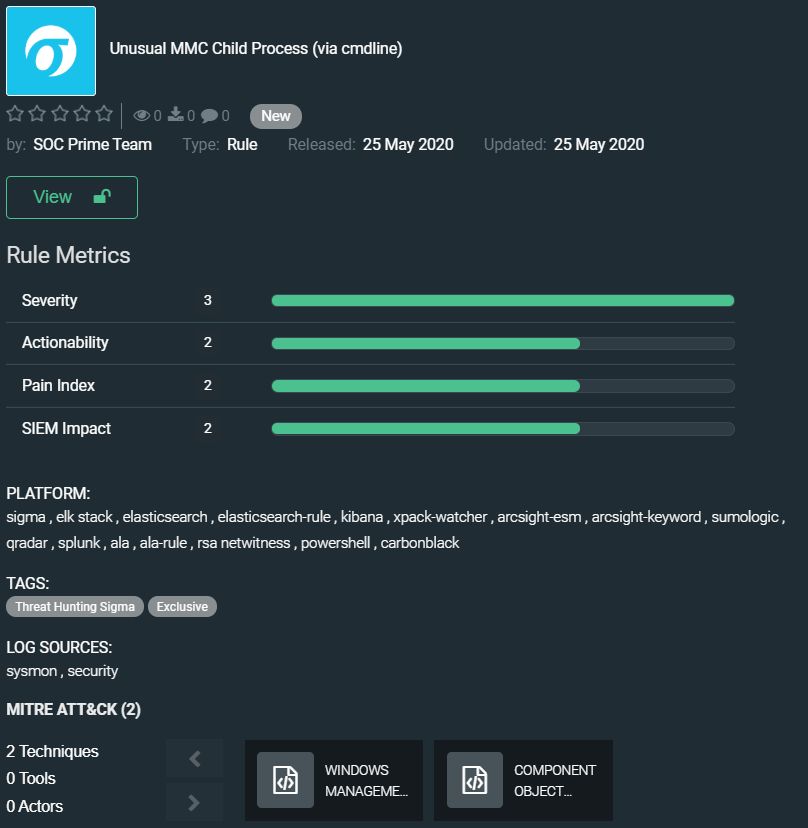
Unusual MMC Child Process (via cmdline) by SOC Prime Team
https://tdm.socprime.com/tdm/info/x37MWadchVPb/M-ZlTHIBv8lhbg_iteTp/?p=1
Microsoft Management Console (MMC) is a component of Windows operating system that provides system administrators and advanced users an interface for configuring and monitoring the system. MMC can be abused via com/dcom for lateral movement or to disguise process chains.
Using Certutil for Data Encoding (via cmdline) by SOC Prime Team
https://tdm.socprime.com/tdm/info/NzzfJwxMu0xj/XeZvTHIBv8lhbg_iF-QM/?p=1
CertUtil.exe is an admin command line tool intended by Microsoft to be used for manipulating certification authority (CA) data and components. This includes verifying certificates and certificate chains, dumping and displaying CA configuration information and configuring Certificate Services. Running CertUtil always requires at least one command option to specify the type of operation to perform, usually on a certificate. The rule detects use of certutil as a living off the land technique.
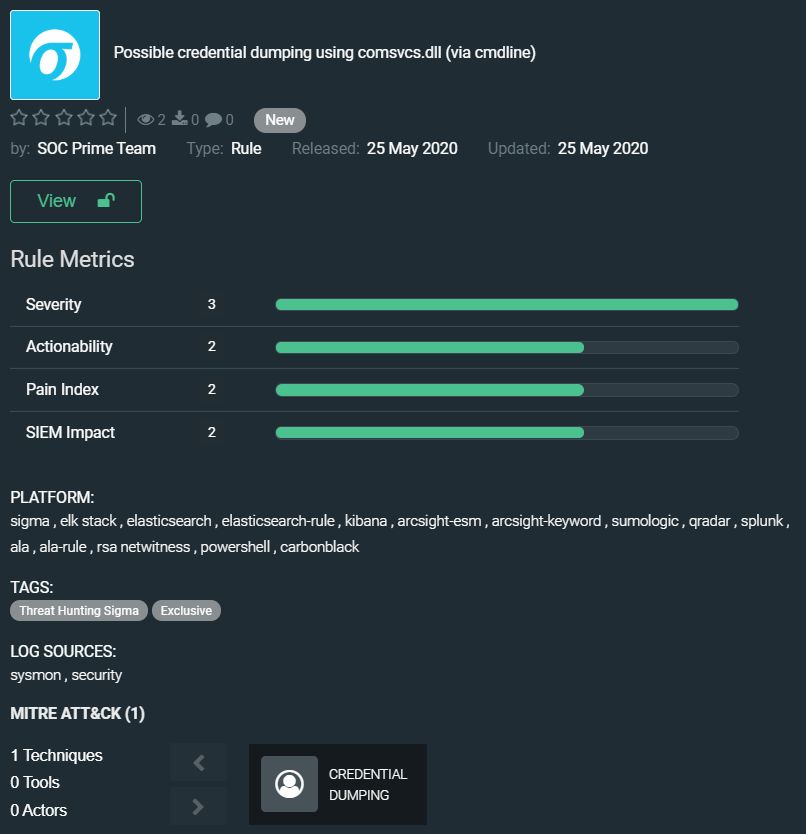
Possible credential dumping using comsvcs.dll (via cmdline) by SOC Prime Team
https://tdm.socprime.com/tdm/info/CrWJtnD4DfNE/ZeZwTHIBv8lhbg_iGeRr/?p=1
The comsvcs.dll is part of Microsoft Windows operating system. Adversaries can misuse this native Windows DLL that exports a function called MiniDumpW. Because of this, it’s possible to invoke this function with rundll32.exe to create a MiniDump of any process, including LSASS. The rule discovers when library ‘comsvcs.dll’ is used to dump credentials on a compromised host.
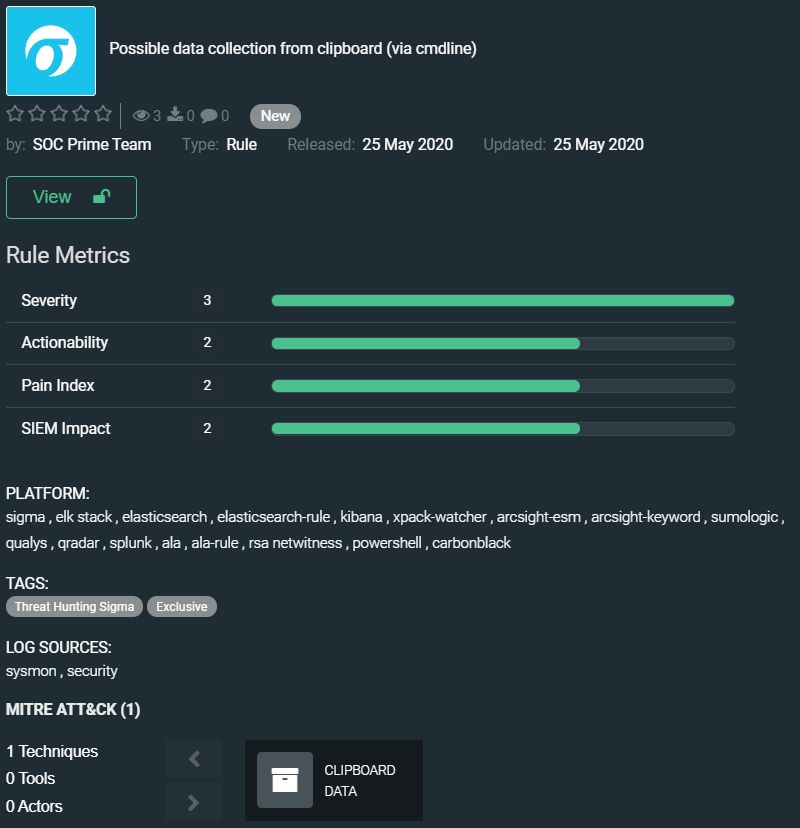
Possible data collection from clipboard (via cmdline) by SOC Prime Team
https://tdm.socprime.com/tdm/info/Kh2BQYb5fTAC/ciFwTHIBjwDfaYjKlKIR/?p=1
Adversaries can use powershell cmdlet to grab data within the clipboard on the target host. The rule detects such malicious activity indicating the compromised system.
The rules from this collection have translations for the following platforms:
SIEM: Azure Sentinel, ArcSight, QRadar, Splunk, Graylog, Sumo Logic, ELK Stack, RSA NetWitness, Logpoint, Humio
EDR: Carbon Black, Elastic Endpoint
MITRE ATT&CK:
Tactics: Defense Evasion, Execution, Persistence, Privilege Escalation, Discovery, Lateral Movement, Exfiltration, Credential Access
Techniques: Regsvr32 (T1117), Rundll32 (T1085), Software Packing (T1027.002), Scripting (T1064), Command-Line Interface (T1059), Registry Run Keys / Startup Folder (T1060), Process Injection (1055), Install Root Certificate (T1130), Modify Registry (T1112), Query Registry (T1012), Component Object Model and Distributed COM (T1175), Windows Management Instrumentation (T1047), Deobfuscate/Decode Files or Information (T1140), Data Encrypted (T1022), Credential Dumping (T1003)
Wait for the next digest in a week.
PS
Don’t miss our next webinar USING MITRE ATT&CK™ AND SIGMA RULES TO ENABLE PROACTIVE THREAT-HUNTING: https://my.socprime.com/en/webinar-using-mitre-att/
Stay safe!