Hot on the heels of the joint cybersecurity advisory warning defenders of the Iran-backed Pioneer Kitten’s collaboration with multiple ransomware groups, another spike in ransomware activity is causing a stir in the cyber threat landscape. The FBI, CISA, and partners recently issued a joint alert covering the increased offensive activity of the RansomHub RaaS operators, who have breached at least 210 organizations in only half a year since the group’s emergence in the cyber threat arena.
Detect RansomHub Attacks
With the ransomware outbreak remaining as rampant as ever in 2024 and ransom demands increasing five-fold over the last year, ransomware attacks are proving to be an escalating threat to global organizations. The release of the latest joint alert AA24-242A by the co-authoring organizations underscores the need to proactively thwart attacks by RansomHub ransomware affiliates. SOC Prime Platform for collective cyber defense equips security teams with context-enriched detection algorithms to help them timely identify RansomHub intrusions.
Click the Explore Detections button below to access the list of relevant SOC content filtered by the custom tag based on the alert identifier. All Sigma rules in the provided detection stack are aligned with the MITRE ATT&CK® framework, enriched with actionable metadata & tailored CTI, and are ready to use across multiple SIEM, EDR, and Data Lake solutions.
Security engineers can also search for additional detections using the custom tag “RansomHub” or explore relevant Sigma rules to detect exploitation attempts related to the known vulnerabilities that are commonly used as initial access vectors by RansomHub adversaries:
- Sigma rules to detect CVE-2023-3519 exploitation attempts
- Sigma rules to detect CVE-2023-27997 exploitation attempts
- Sigma rules to detect CVE-2023-46604 exploitation attempts
- Sigma rules to detect CVE-2023-22515 exploitation attempts
- Sigma rules to detect CVE-2023-46747 exploitation attempts
- Sigma rules to detect CVE-2023-48788 exploitation attempts
- Sigma rules to detect CVE-2020-1472 exploitation attempts
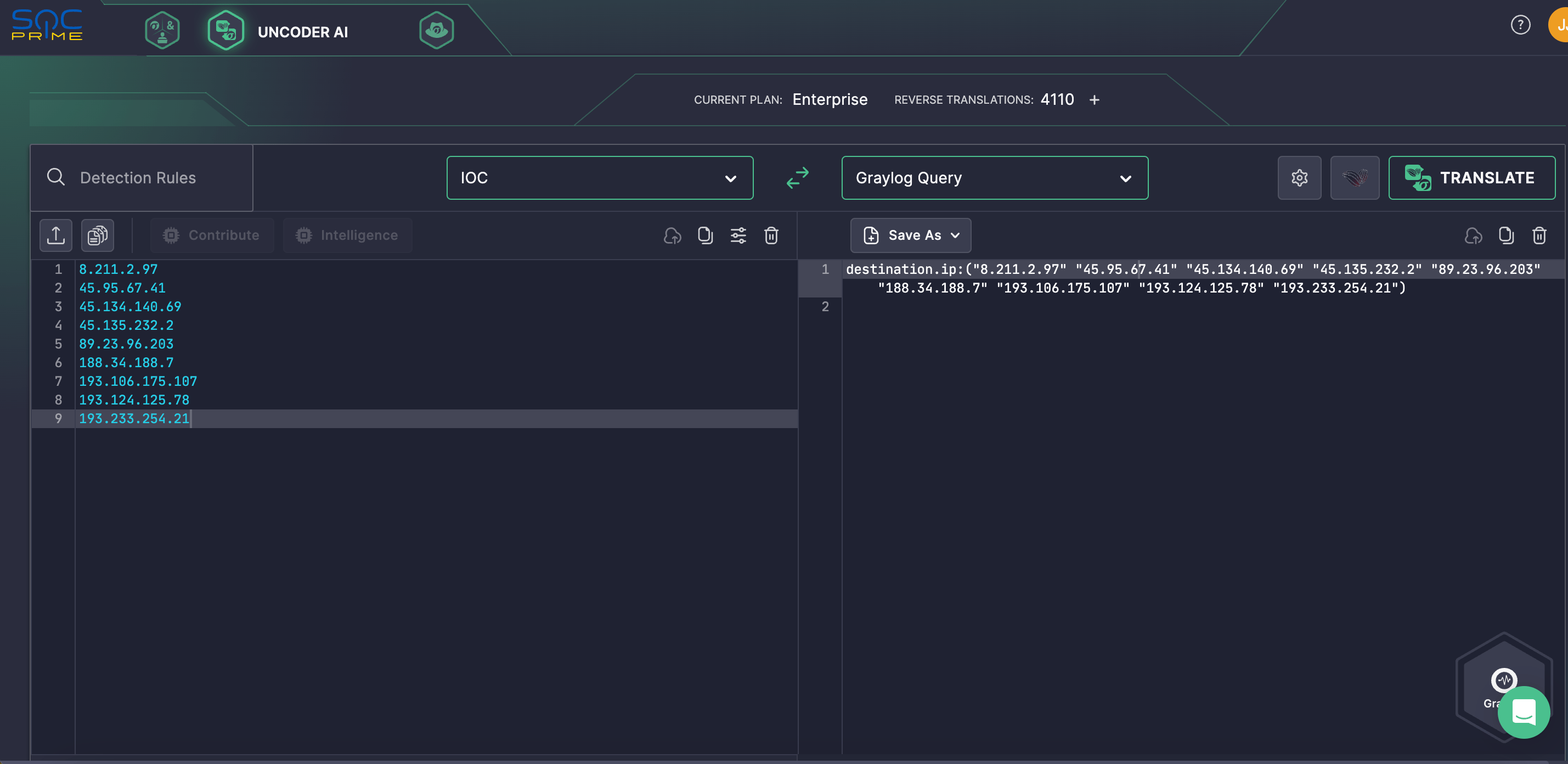
Security teams can also leverage SOC Prime’s AI co-pilot for detection engineering to simplify threat research and IOC matching. With Uncoder AI, it’s easier to search for IOCs from the corresponding advisory AA24-242A and linked to the RansomHub activity. Defenders can seamlessly convert relevant IOCs into hunting queries that are ready to run in their chosen SIEM or EDR instance.
RansomHub Attack Analysis
On August 29, 2024, the FBI and CISA, in conjunction with other authoring agencies, released the AA24-242A alert focused on the growing attacks against the state bodies and critical infrastructure organizations, including water and wastewater, IT, healthcare, financial services, and communications. The RansomHub group behind these attacks has already hit over 210 organizations since its emergence in February 2024. RansomHub, once known as Cyclops or Knight, has become an effective and successful model, recently drawing in top ransomware affiliates from other notorious variants like LockBit and ALPHV.
The ransomware maintainers operate under the RaaS model and employ a double-extortion approach, encrypting systems and extracting data to coerce victims into paying the demanded ransom. The ransom note left during encryption usually lacks a specific demand or payment instructions. Instead, it provides a client ID and directs victims to contact the ransomware group via a unique .onion URL on the Tor network. Victims are typically given up to 90 days to pay before their data is published on the adversary leak site.
As the initial attack vector, RansomHub maintainers commonly rely on phishing emails, vulnerability exploitation, including weaponizing the critical flaws and zero-days like CVE-2023-3519, CVE-2023-46604, CVE-2023-22515, or CVE-2020-1472, and password spraying, which targets accounts compromised in data breaches. Adversaries gain PoC exploits from public resources like ExploitDB or GitHub.
RansomHub actors scan networks using tools like AngryIPScanner, Nmap, and PowerShell. Attackers also apply a set of techniques to evade detection, like renaming ransomware executables to benign names, clearing system logs, and using Windows Management Instrumentation to disable antivirus software. In some cases, they also disable EDR tools with their custom utilities. For persistence, they create or reactivate user accounts, use Mimikatz to collect credentials and escalate privileges, and move laterally through the network using methods such as RDP, PsExec, Anydesk, and various C2 tools like Cobalt Strike and Metasploit. RansomHub also leverages sophisticated methods to encrypt files on the system, like the Curve 25519 encryption algorithm, which employs a unique public/private key pair for each targeted organization.
To minimize the risks of RansomHub attacks, the authoring agencies advise adhering to the recommendations provided in the #StopRansomware Guide, strengthening cyber hygiene, and continuously testing and validating the organization’s existing security controls. By relying on SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection, organizations can proactively defend against ransomware attacks and other current or emerging threats of any scale and sophistication to build a robust cybersecurity posture.




