What are IOCs, and what is their role in cybersecurity?
In cybersecurity operations, Indicators of Compromise — such as IP addresses, file hashes, domains, and URLs — serve as crucial forensic evidence for identifying malicious activities within the organization’s network. These artifacts are essential to enabling security teams to detect potential cyber threats.
To leverage effective IOCs, teams should adhere to reliable and up-to-date channels to ensure that the provided information enables them to detect the latest tactics, techniques, and procedures (TTPs) used by threat actors. Different security teams use various sources of IOCs, and these are the most common ones:
Open-source intelligence (OSINT) resources, like Virus Total, abuse.ch, and AlienVault OTX, provide publicly available IOCs collected from security researchers, government reposts, and community platforms.
Threat intelligence feeds and platforms offered by vendors like Recorded Future, FireEye, and CrowdStrike, aggregate and curate IOCs from global data sources, such as malware analysis, attack data, and darknet monitoring.
Industry and sharing communities, such as information sharing and analysis centers (ISACs) or the Cyber Threat Alliance, allow participants to share IOCs in real-time, increasing the response speed against industry-specific threats.
Incident response and forensic investigations provide IOCs identified through log analysis, malware reverse-engineering, and network forensics that add context to specific attacks. Such information as file hashes of malicious executables or IP addresses of command-and-control servers is documented and often shared to prevent similar attacks.
However, turning raw IOCs into actionable intelligence by converting them into SIEM-specific queries for threat detection and threat hunting is a challenge for cybersecurity teams. As each SIEM system requires a unique query language and data structure, manual translation of IOCs is a resource-intensive and error-prone process, especially for teams dealing with multiple environments and in high-pressure incident response situations.
Uncoder AI automates this conversion of IOCs into ready-to-deploy SIEM queries, enhancing both accuracy and operational efficiency.
Step-by-Step Guide to Converting IOCs with Uncoder AI
Converting Indicators of Compromise into actionable SIEM queries is a crucial step in operationalizing threat intelligence for rapid response. While IOCs provide accurate and valuable insights, manually converting them into formats supported by various security solutions can slow down threat detection and increase the risk of errors. Uncoder AI simplifies this process enabling SOC analysts, threat hunters, and detection engineers to convert IOCs into SIEM-specific queries in just a few steps. Besides, Uncoder AI provides broad customization options so that teams can automatically generate SIEM queries and adapt them to their specific setting or technology stack in use.
The following types of Indicators of Compromise are supported:
- Hash
- Domain
- URL
- IP
- File
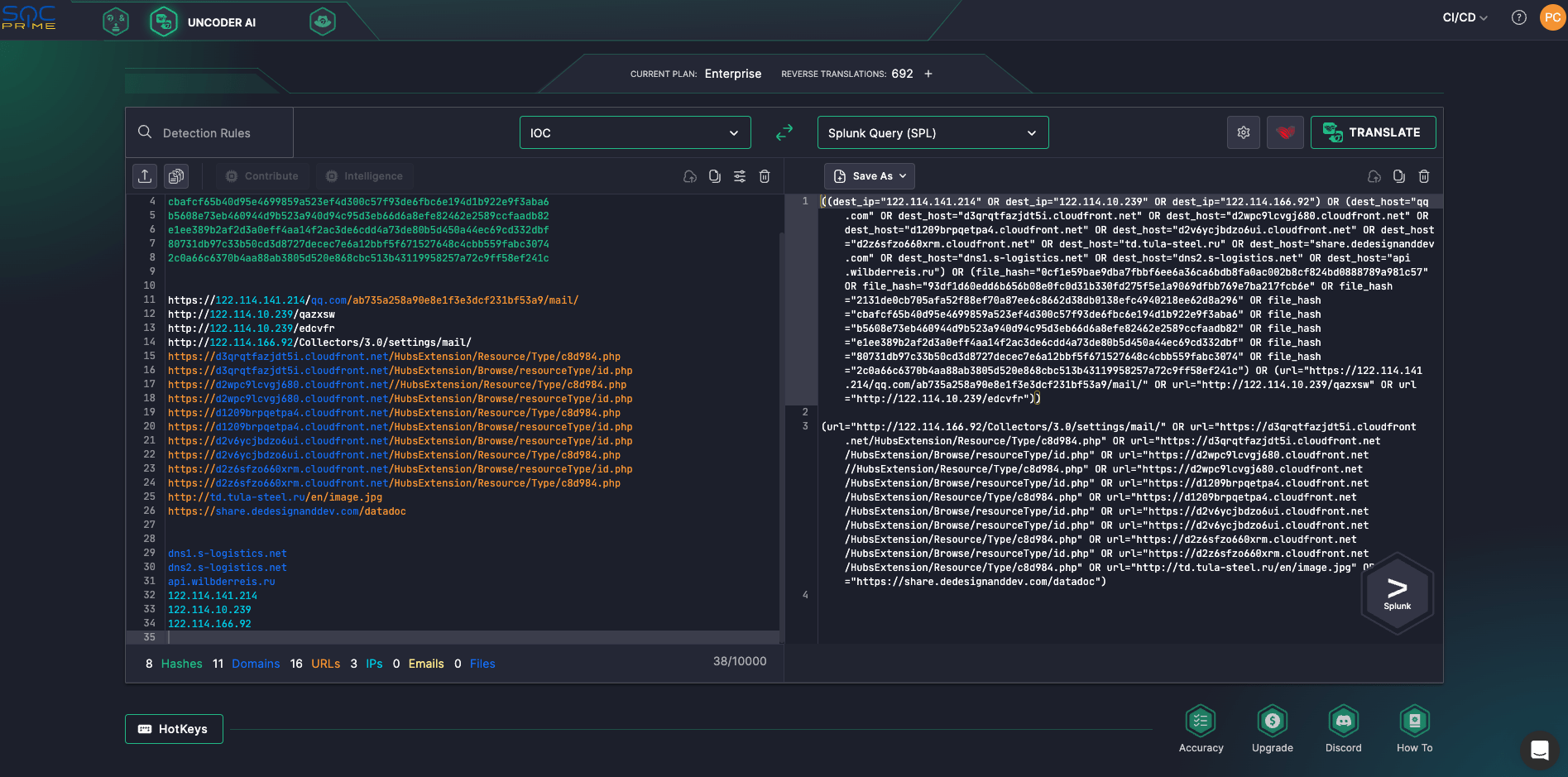
Converting IOCs into Splunk Query
This is how you can convert IOCs from the source of your choice to a SIEM query:
- Go to Uncoder AI. Log in using your SOC Prime Platform account, or register an account for free using your personal or work email address.
- Copy the IOCs from your information source and paste them into the input panel of Uncoder AI.
- Select IOC as your format to translate from if it has not been identified automatically.
- Select Splunk query (SPL) as a format to translate to.
- Click Translate and see your IOC query generated in the output panel.
Alternatively, you can use Uncoder IO, but remember that this version does not provide all the functionalities of Uncoder AI.
How to Customize IOC Translation with Uncoder AI
Customization is key when translating IOCs into SIEM queries to maximize the accuracy and effectiveness of your detection rule. Uncoder AI offers several options of settings and customization that enable security teams to optimize threat hunting while eliminating extensive manual adjustments.
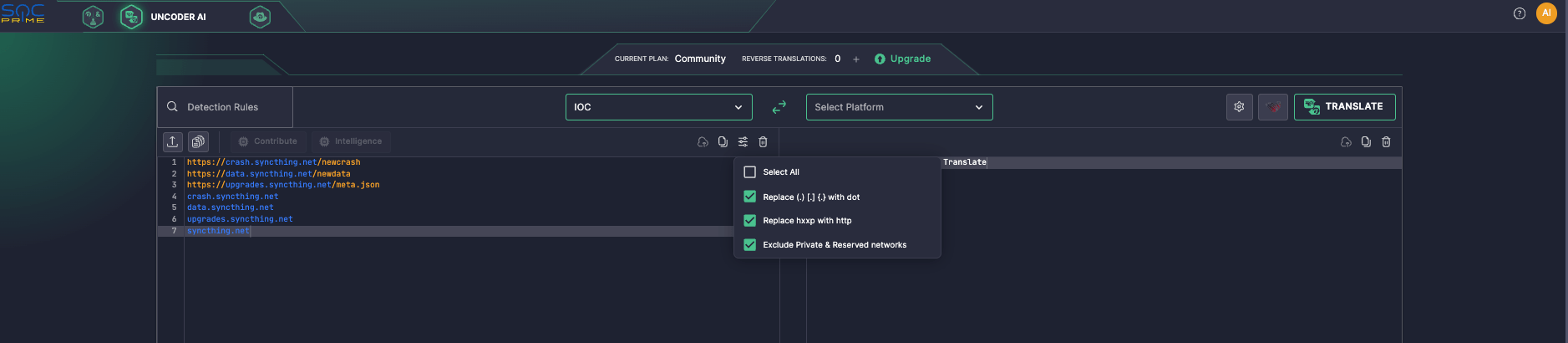
Apply additional parsing settings. Click the Settings icon in the input panel to see that additional parsing settings are enabled by default:
- Replace (.) [.] {.} with dot.
- Replace hxxp with http — this setting is case insensitive, so hXXp, HXXP, HXXp, and hXXP are replaced in this case as well.
- Exclude Private & Reserved Networks — private and reserved IP addresses like 224.0.0.0/4 or 127.0.0.0/8 are ignored.
By default, all the options are enabled:
Fine-tune your query. Here, you can select what IOC types to use for queries and set the number of IOCs per query to take into account the performance of your platform. If you have hash enabled as an IOC type, you can also select what hash types to use for queries. Additionally, here you can define exceptions by specifying hashes, domains, IPs, emails, files, or URLs (in whole or only partially) you want to exclude from your queries.
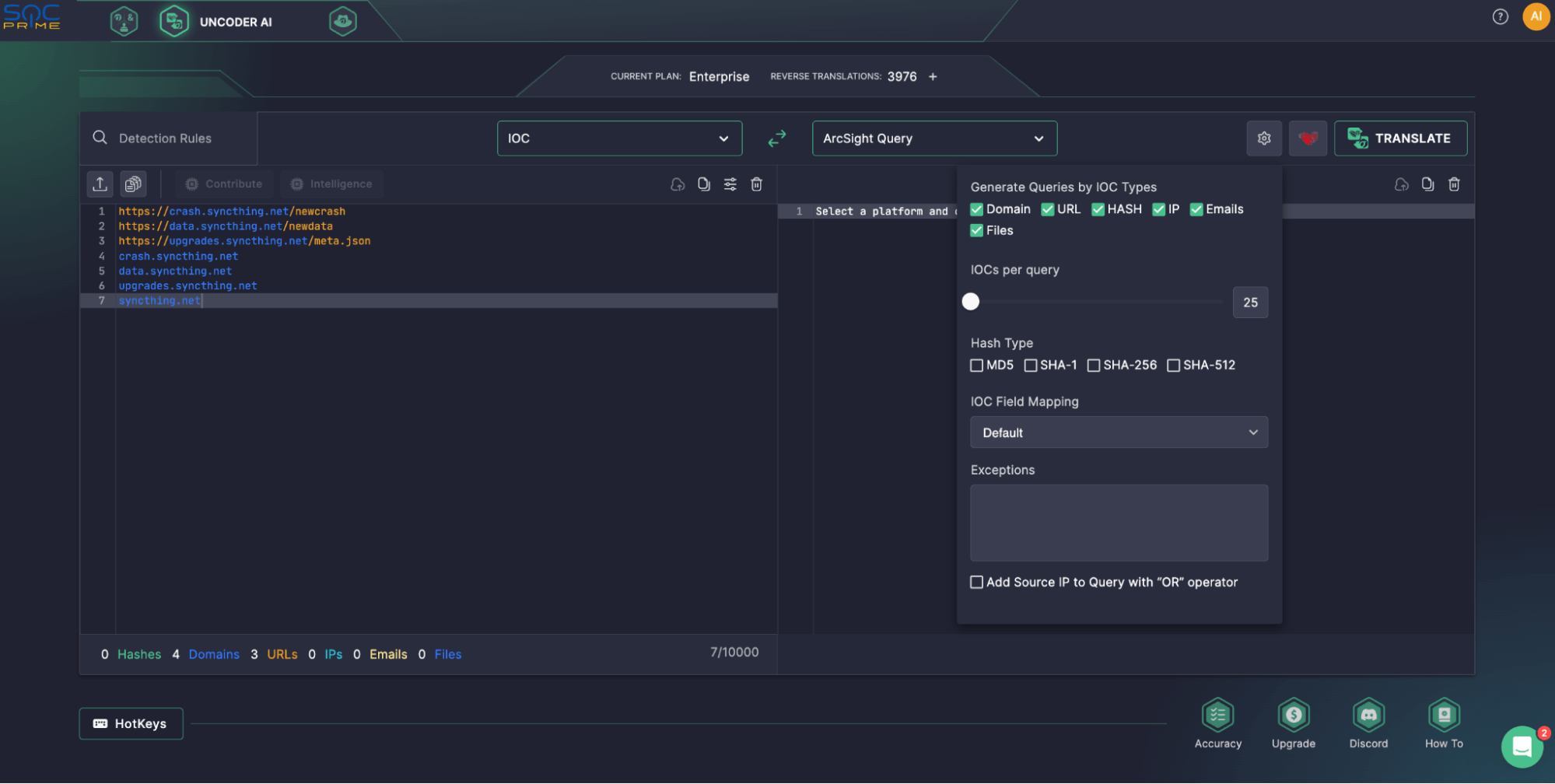
Set up IOC field mapping profiles. Use this feature if your data schema has non-standard field names for:
- Destination IP
- Source IP
- Domain
- URL
- Emails
- Files
- Md5
- Sha1
- Sha256
- Sha512
Advantages of Using Uncoder AI
Utilizing Uncoder AI to convert Indicators of Compromise into SIEM-specific queries provides significant advantages for cybersecurity teams seeking accurate threat detection by streamlining the part of the daily routine that has traditionally been a manual and time-consuming task. By automating the translation of IOCs across formats for various security solutions, Uncoder AI allows teams to generate accurate and platform-compatible queries for various security solutions without the need for in-depth familiarity with the syntax.
Uncoder AI enables teams to significantly reduce manual input from personnel with specialized knowledge of SIEM query languages, formats, and data structures. This efficiency allows organizations to increase the maturity level of their security operations by reallocating high-skilled specialists to more strategic tasks such as threat hunting, advanced analysis, and long-term security planning, making Uncoder AI a valuable asset in any proactive threat detection strategy.




