Threat Hunting Maturity Model Explained With Examples

Table of contents:
In our series of guides on Threat Hunting Basics, we’ve already covered multiple topics, from techniques and tools threat hunting teams use to the certifications for professionals and beginners. But what makes good Cyber Hunting, and how can you evaluate it? One of the ways to measure the effectiveness of the hunting procedures is by using the Threat Hunting Maturity Model (HMM). It comes in helpful to assess the proficiency of the threat hunting process and define the opportunities for improvement.
In this blog, we’ll see how you can evaluate your organization’s maturity level and what can be modified to strengthen the security posture. Whether you are new to threat hunting or looking to boost your current setup, equipping yourself with the behavior-based detections from the SOC Prime Platform is never a bad idea.
Detect & Hunt Explore Threat Context
Threat Hunting Maturity Model Introduction
Referring to Threat Hunting Maturity Model is a great way to keep your organization’s cyber hunting in place. Of course, there are no universal hunting models as they vary for different companies. However, when assessing an organization’s capacity for threat hunting, you should always consider the following elements:
- What are the quality and volume of the data gathered by an organization?
- How well can an organization interpret and analyze different kinds of data?
- Which automated analytical techniques can an organization use to improve Analyst’s insights?
When was Threat Hunting Maturity Model Developed?
The current Threat Hunting Maturity Model was created by Sqrrl in 2017 to assess the hunting capacity of an organization. In particular, the Sqrrl Threat Hunting Model was developed by David J. Bianco (@DavidJBianco), a Hunter and Security Architect. The main idea of this threat hunting framework is to outline different stages of organizational cyber hunting competence.
What is Threat Hunting Maturity Model?
Threat Hunting Maturity Model is a five-level evaluation system of how efficient an organization is in terms of cyber hunting. The Sqrrl threat hunting model assesses the following criteria:
- Data Collection (the volume and the quality of data a company extracts from its environment)
- Hypotheses Creation (what is taken into account when creating hypotheses)
- Tools and Techniques for Hypothesis Testing
- Pattern and Tactics, Techniques, and Procedures (TTPs) Detection
- Analytics Automation (to what extent the threat hunting procedures are automated)
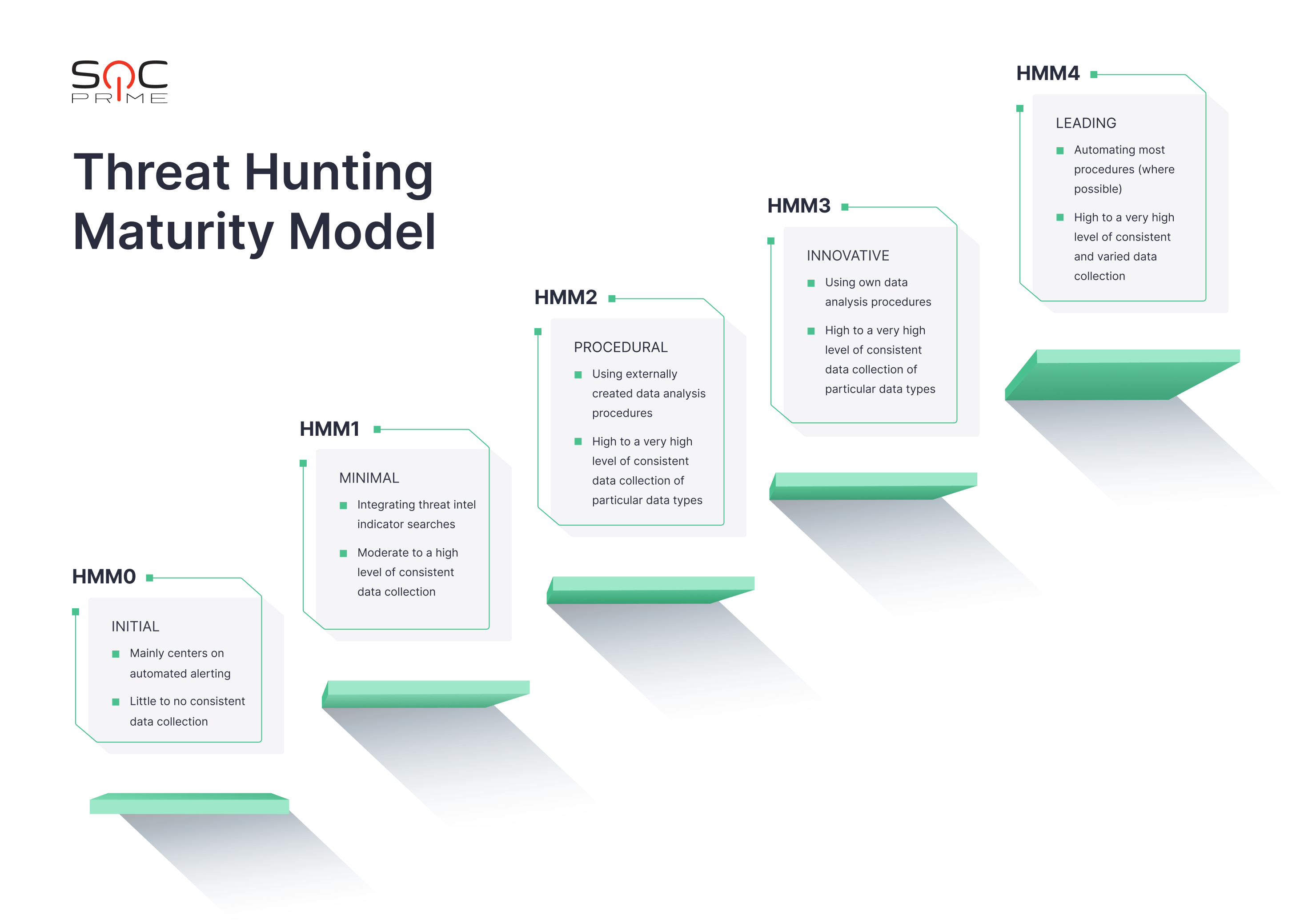
The Threat Hunting Maturity Model defines the organizations’ capabilities of effective cyber hunting and threat response. The more capable the business is, the higher the Hunting Maturity Model (HMM) level is, where the HMM0 is the least capable and the HMM4 is the most efficient. Now, let’s look at each level in detail.
HMM0 – Initial Level of Threat Hunting Maturity Model
At HMM0, organizations generally use automated alerting systems like IDS, SIEM, or antivirus to identify harmful behavior. The majority of the human work at HMM0 is focused on alert resolution.
These companies presumably utilize threat intelligence indicators and threat feeds from open-source services. These indicators mostly correspond to the lower levels of the Pyramid of Pain, trivial data that is unlikely to be reused (domains, hashes, URLs, IP addresses). HMM0 organizations tend to lack actual threat intelligence capability.
At HMM0, businesses typically utilize a platform like SIEM for log aggregation. It most likely uses the vendor’s basic default configuration (e.g., correlative rules for alerts.) Additionally, HMM0 companies do not gather much data from their systems, which greatly restricts their capacity to discover threats proactively. As a result, there is little to no visibility of the environment for these organizations. All this makes HMM0 organizations incapable of threat hunting.
What does HMM0 cyber hunting look like?
- Data Collection: Minimal or no data collection at all.
- Hypothesis Creation: The process comes down to resolving alerts produced by antivirus, firewall, SIEM, IDS, etc., without creating hypotheses.
- Tools and Techniques for Hypothesis Testing: The procedures don’t involve any proactive investigation. The tools would generally include SIEM searches or alert consoles.
- Pattern and TTP Detection: None.
- Analytics Automation: None.
HMM1 – Minimal Level of Threat Hunting Maturity Model
HMM1 means that organizations still mostly use automated alerting to guide their incident response process. However, at this stage, the visibility of the environment gets better, mainly thanks to collecting a greater variety of logs.
At HMM1, businesses keep using SIEM platforms for analysis, but at this maturity level, the SIEM content is diversified beyond basic correlations. The gathering of various data allows creating reports for further analysis. As a result, Analysts can pull indicators from these reports when new threats emerge and check historical data for any relevant traces.
At the minimal level of the threat hunting framework, organizations also aim to gain threat intelligence capability by integrating a threat intel platform that enriches their individually-generated IOCs. These companies frequently follow up on the most recent threat reports as they strive for intelligence-driven detection.
HMM1 is the first level of the Sqrrl threat hunting model where some form of cyber hunting takes place, despite being limited.
What does HMM1 cyber hunting look like?
- Data Collection: Basic data collection from the key infrastructure points.
- Hypothesis Creation: New hypotheses are created based on the threat intel review.
- Tools and Techniques for Hypothesis Testing: Basic query search using log analytics tools or SIEMs.
- Pattern and TTP Detection: Identification of the simplest IOCs, such as domains, hashes, and URLs.
- Analytics Automation: Basic threat intelligence capability is integrated into automated alerting.
HMM2 – Procedural Level of Threat Hunting Maturity Model
HMM2 is believed to be the most prevalent level of threat hunting maturity among companies. Organizations at HMM2 use analytical and hunting processes produced by others on a nearly regular basis. While they can make minor alterations to the techniques taken from elsewhere, they are not yet able to develop their custom procedures.
HMM2 businesses typically gather large (often very large) volumes of data from across the company because most of their methods rely on least-frequency analysis.
What does HMM2 cyber hunting look like?
- Data Collection: High and consistent data collection of particular data types.
- Hypothesis Creation: Threat intelligence review for hypotheses creation.
- Tools and Techniques for Hypothesis Testing: Using basic tools and histograms for search and data analysis.
- Pattern and TTP Detection: Identification of the IOCs that correspond to the lower and middle levels of the Pyramid of Pain. The hunting processes might involve the mapping of the IOCs trends.
- Analytics Automation: Building a library of effective cyber hunting procedures and performing them regularly.
HMM3 – Innovative Level of Threat Hunting Maturity Model
HMM3 organizations have at least a few Threat Hunters who understand several types of data analysis techniques and can apply them to detect malicious behavior. These organizations are typically the ones developing and releasing hunting methods, unlike the HMM2 businesses, which rely on third-party procedures. Analytical abilities can range from elementary statistics to more complex subjects like linked data analysis, data visualization, or machine learning. At this point, it’s crucial for Analysts to develop repeatable procedures that are recorded and regularly carried out.
At HMM3, data collection is at least equally common as at HMM 2, if not more. When it comes to identifying and combating adversary activity, HMM3 organizations are quite effective. However, they may have scalability issues as the volume of cyber hunting processes expands. Performing all the procedures timely might get overwhelming unless the threat hunting team grows correspondingly.
What does HMM3 cyber hunting look like?
- Data Collection: High and consistent data collection of particular data types.
- Hypothesis Creation: Constant threat intelligence review and manual cyber risk scoring for the new hypotheses development.
- Tools and Techniques for Hypothesis Testing: Leveraging graph searches and visualizations while developing new hunting procedures.
- Pattern and TTP Detection: Ability to detect a wide range of IOCs, including those at the top of the Pyramid of Pain.
- Analytics Automation: Conducting basic data science activities and building a library of effective cyber hunting procedures.
HMM4 – Leading Level of Threat Hunting Maturity Model
The main distinction between the HMM4 and HMM3 organizations is automation. At HMM4, most hunting techniques are operationalized and transformed into automatic detection where possible. It frees Analysts from running the same processes repeatedly and enables them to focus on enhancing existing operations or developing new ones.
Organizations at the HMM4 level are effective at stopping and detecting adversary activity. Due to the high level of automation, hunting teams can concentrate their efforts on constantly improving their hunting methodologies, which results in continuous development.
What does HMM4 cyber hunting look like?
- Data Collection: High level of consistent and varied data collection.
- Hypothesis Creation: Constant threat intelligence review and automated cyber risk scoring for the new hypotheses development.
- Tools and Techniques for Hypothesis Testing: Advanced graph searches and visualizations with automated hunting procedures.
- Pattern and TTP Detection: Automated TTP discovery and possible sharing of IOCs with the relevant organizations that gather reports.
- Analytics Automation: Automation is applied wherever possible; active usage of Machine Learning (ML) and other advanced technologies.
Conclusion on Threat Hunting Maturity Model
While companies keep improving various types of threat hunting procedures, it is critical to establish a precise roadmap. Threat Hunting Maturity Model is a great place to start for both mature organizations and those who are only starting to check different hunting models. Organizations may use this approach to determine not only where they are but also where they need to be and how to get there.
To boost your threat hunting processes, join SOC Prime’s Detection as Code platform that gives you access to the world’s largest collection of curated Sigma rules suited to 25+ SIEM, EDR, and XDR solutions.