This blog post describes the custom data schema mapping feature that is available on SOC Prime Threat Detection Marketplace for Premium Subscription plans.
The custom data schema mapping allows users to build a custom mapping configuration for most log sources and platforms that can be automatically applied to rules on Threat Detection Marketplace to make them more compatible with your platform so that you don’t have to manually go back to the SIEM and modify the field names to match the schema you are using.
Apparently, there are a lot of differences between different environments and automatical changing of default field names with custom field names allows you to automatically rewrite all rules to the specifics of your Data Quality and avoid parsing issues.
The obvious reason why this feature is necessary is that the field names that you are using are most likely not the same that everyone else is using, whichever platform you are running – Elastic with the Elastic Common Schema (ECS), or Splunk with its Common Information Model (CIM), or you are using ArcSight Common Event Format (CEF), or the QRadar Log Event Extended Format (LEEF).
Data Schema Profiles
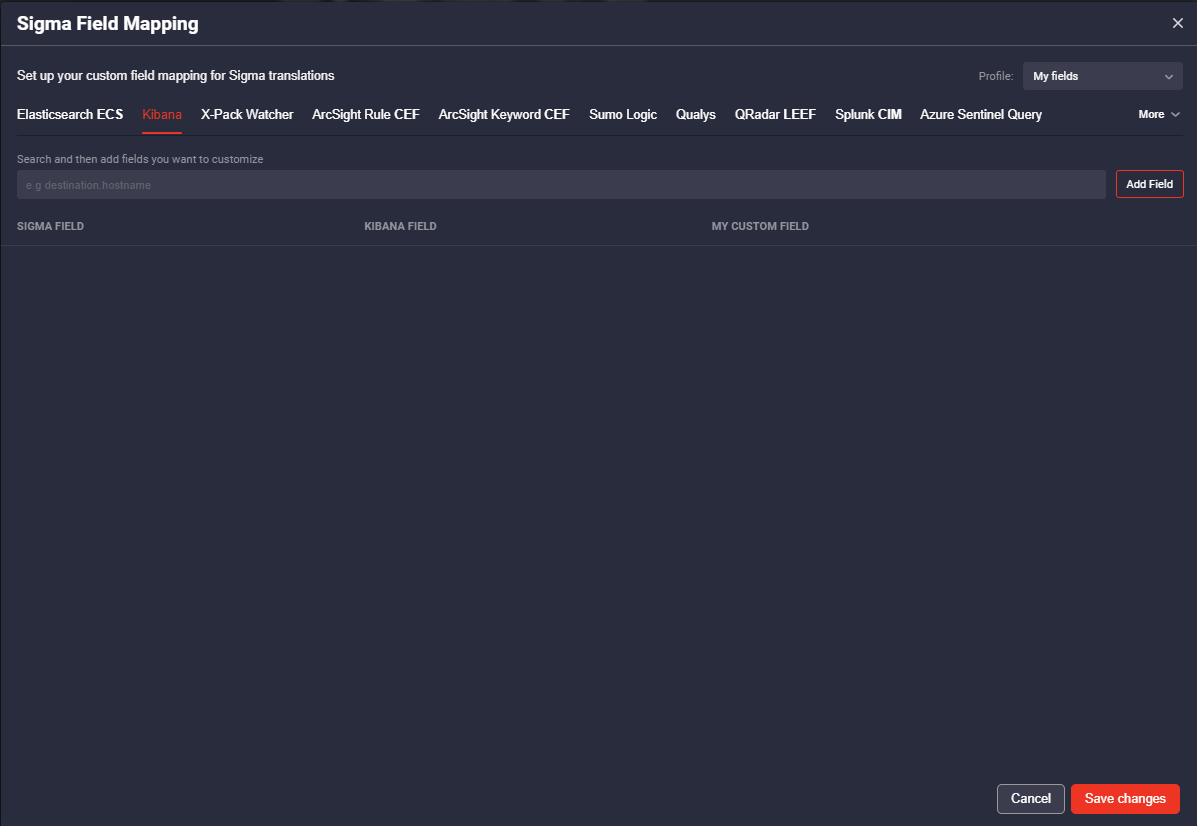
You can access the configuration either by clicking on the platform that you want to tune-up on the selected Rule page and click the gear icon to configure Sigma Field Mapping, or you can go to the User Menu on the top right and select the Sigma Field Mapping menu item.
In the opened settings window, you can see the number of Platforms that you can configure field mapping for.
Besides, you can create different Mapping Profiles and switch between them if you are using several SIEMs with different field names. Having multiple Mapping Groups is essential for Managed Security Service Providers (MSSP) to manage multiple SIEM instances.
Fields Customization
Detection rules that you can find on Threat Detection Marketplace are Sigma rules of generic and open signature format with standard field names https://github.com/Neo23x0/sigma
When making a rule translation with the default Sigma translator, the SIEM default field names are used for destination platform fields, for example, Sigma EventID field corresponds to the event.code field in the Elasticsearch, and the EventCode field in Splunk.
In the Sigma Field Mapping section, you can customize the filed names so that all further Rules translations could be run in your SIEM instance without any additional manual customization. Select the Sigma fields form the drop-down list and save the customized filed names to the Profile. Also, you can manually add fields to the to be further customized for your SIEM instance.
You can specify all the available field names used in your SIEM instance and save the settings for a Field Mapping Group, also you can create a Mapping Group for several platforms, so that you could copy to the clipboard a translation for your platform with customized field names after just selecting a preset Group.
As fixing parsing issues requires time, expertise and following the Change Management process, adopting rules on the fly eliminates blockers to proactive threat detection.