CVE-2023-23397 is a critical elevation of privilege (EoP) vulnerability in Microsoft Outlook with a CVSS base score of 9.8. It was first disclosed on March 14, 2023, and attributed to APT28, also known as Fancy Bear or Strontium – a threat actor associated with the Russian General Staff Main Intelligence Directorate (GRU). The vulnerability is mainly targeting the European government, military, and energy sectors.
The severity of CVE-2023-23397 is mainly credited to its nature of a zero-touch exploit, meaning that no user intersection is needed for a threat actor to exploit the vulnerability via a specific email or a calendar item sent to a user. As a result of a successful CVE-2023-23397 exploit, an attacker can access the Net-NTLMv2 hash that contains the encrypted user’s credentials. This allows adversaries to move laterally within the network to get more sensitive information.
Today, we’ll analyze this Outlook vulnerability and check several options for mitigating and detecting CVE-2023-23397.
Detecting Exploits for a CVE-2023-23397
To help organizations proactively detect CVE-2023-23397 exploitation attempts, SOC Prime Platform for collective cyber defense curates a set of verified context-enriched Sigma rules. y clicking the Explore Detections button, you can instantly reach relevant Sigma rules for CVE-2023-23397 detection via registry_event, powershell, process_creation, and cmdline. The rules are aligned with the latest MITRE ATT&CK® framework and supported by extensive metadata and relevant threat intelligence links.
Microsoft recommends using their Exchange scanning script as the first step of the threat-hunting process for the potential compromise. It audits the Exchange server for malicious messages, including emails, tasks, and calendar items.
CVE-2023-23397 IOCs
If you don’t identify any suspicious values through the scanning script, you can hunt for the indicators of compromise. Examine the following anomalous behavior:
- Observe the telemetry of Microsoft Defender for Endpoint and Microsoft Defender Identity, as well as the Exchange Server logging for any NTLM authentication that involves external or untrusted resources.
- Track process execution events for the attempts of WebDAV connection.
- Check SMBClient events for log entries.
- Look for abnormal outbound SMB connections in the firewall logs.
As for the data sources, you can review the following:
- Firewall logs
- Proxy logs
- VPN logs
- Azure AD sign-in logs for Exchange Online
- IIS logs for Exchange Server
- RDP Gateway logs
- Endpoint data ( e.g., windows event logs for end users)
- EDR telemetry (if available)
Below, you can find the IP addresses associated with the CVE-2023-23397 exploit. You can access a more extensive list on Virustotal.
- 24.142.165[.]2
- 85.195.206[.]7
- 101.255.119[.]42
- 113.160.234[.]229
- 168.205.200[.]55
- 181.209.99[.]204
- 185.132.17[.]160
- 213.32.252[.]221
To seamlessly hunt for indicators of compromise related to the CVE-2023-23397 exploitation attempts, rely on Uncoder AI and instantly generate custom IOC queries ready to run in the selected SIEM or EDR environment.
CVE-2023-23397 PoC
By now, you can find many CVE-2023-23397 PoCs, but what you should know is how straightforward the exploit is. The creation of a malicious calendar appointment, for instance, comes down to the following:
- Creating an Outlook MSG file,
- Extending the Appointment class as it has a defined number of properties,
- Adding PidLidReminderOverride and PidLidReminderFileParameter properties.
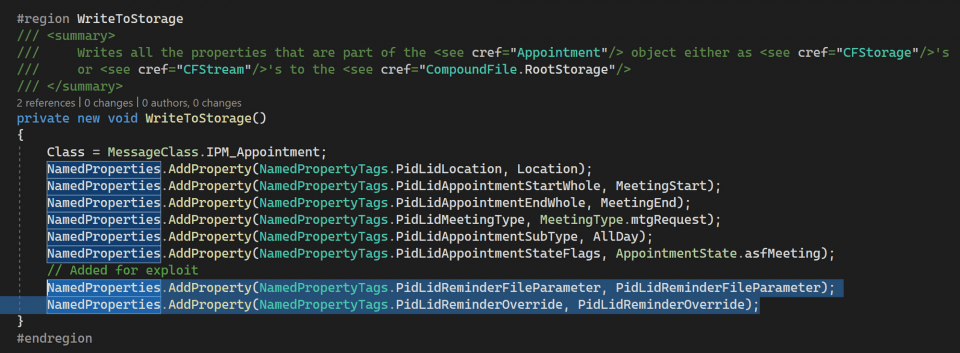
Source: MDSec
Microsoft Outlook Vulnerability Analysis
CVE-2023-23397 is a vulnerability that specifically targets Microsoft Outlook on Windows operating systems. Exploiting this vulnerability requires the delivery of a specially crafted message (email, event, or task) to a user. The main vulnerability is located in the PidLidReminderFileParameter extended MAPI property. PidLidReminderFileParameter is a filename of a reminder sound. To exploit the vulnerability, threat actors change the PidLidReminderFileParameter property, pointing a UNC path to a server controlled by adversaries via the Server Message Block (SMB) or TCP port 445.
Further, a reminder appears on a user’s device triggering New Technology LAN Manager (NTLM) authentication. The process requires no interaction from the recipients and goes unnoticed behind the scenes. After connecting to the remote SMB server, the user’s Net-NTLMv2 hash leaks. With the NTLMv2, adversaries can either use a lateral movement tactic (TA0008) to navigate through the network or crack the encrypted form of the user’s password.
According to Microsoft’s guidance, adversaries can only exploit the Outlook vulnerability using the SMB protocol. At the same time, the WebDAV protocol interaction doesn’t pose a risk of credential leak to external IP addresses when using the CVE-2023-23397 exploit technique. Even if there is a Net-NTLMv2 authentication request, Windows won’t send hashes.
In any scenario, with the proper CVE-2023-23397 mitigation, you can minimize the risks of vulnerability exploitation. For the mitigation measures, Microsoft recommends the following in their security update:
- Disable NTML usage as an authentication method. The easiest way of doing it is by creating a Protected Users Security Group and adding your users there. Especially focus on accounts with higher levels of permissions (e.g., domain admins). This action might disrupt work with the NTLM-required apps. Therefore, you would have to remove a user from the group to reverse these settings.
- Block SMB (TCP 445) outbound in your network. You can do that with the help of a perimeter/local firewall or through the VPN settings. By using those, the NTLM authentication messages won’t be sent to the remote file shares.
Rely on SOC Prime to be fully equipped with detection content against any exploitable CVE or any TTP used in the ongoing cyber attacks. Obtain access to 800+ detection algorithms for existing CVEs to proactively defend against threats tailored to your security needs. Instantly reach 140+ Sigma rules for free at https://socprime.com/ or get all relevant detections with premium subscriptions to SOC Prime Platform at https://my.socprime.com/pricing/.



