Following the investigation into UAC-0212’s increasing activity against multiple organizations in Ukraine’s critical infrastructure sector, CERT-UA notifies the global cyber defender community of the reemergence of another hacking group in the Ukrainian cyber threat arena. The organized criminal group tracked as UAC-0173 has been conducting a series of phishing attacks against notaries impersonating the sender as a representative of the Ministry of Justice of Ukraine.
Detect UAC-0173 Attacks Covered in the CERT-UA#13738 Alert
Phishing attacks still account for over 80% of security events in the modern cyber threat landscape. There is also a sharp increase in malicious activity targeting Ukrainian organizations in multiple industry verticals, leveraging the phishing attack vector to gain initial access.
SOC Prime Platform for collective cyber defense offers curated Sigma rules to help organizations proactively thwart UAC-0173 attacks against Ukrainian notaries covered in the latest CERT-UA#13738 alert. Click Explore Detections to find relevant Sigma rules compatible with dozens of SIEM, EDR, and Data Lake solutions, mapped to MITRE ATT&CK®, and enriched with in-depth threat intel.
Organizations can also apply the “UAC-0173” tag based on the group identifier to search SOC Prime Platform for more detection content related to the threat actor’s offensive operations.
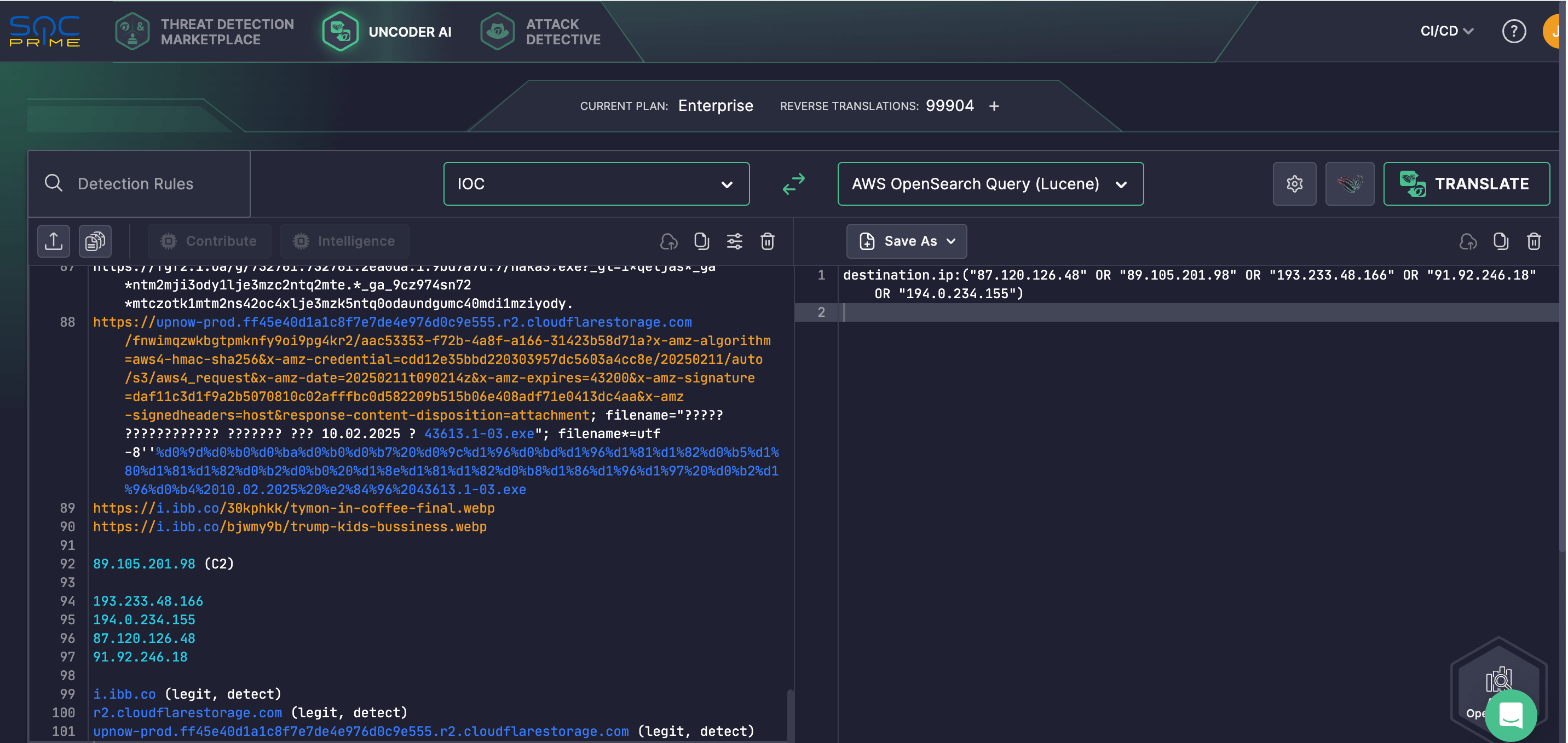
SOC Prime Platform users can also use Uncoder AI to accelerate IOC matching and help defenders perform retrospective hunts. The private IDE and AI co-pilot enables converting IOCs related to the UAC-0173 activity from the relevant CERT-UA report to custom queries ready to search for potential threats in your SIEM or EDR environment.
UAC-0173 Attack Analysis
On February 25, 2025, CERT-UA published a new CERT-UA#13738 heads-up focused on the increasing activity of the financially motivated UAC-0173 hacking collective. The group has been conducting cyber-attacks for financial gain by targeting notaries’ computers to gain covert remote access and later make unauthorized changes to state registries.
Notably, in the summer of 2023, adversaries chose similar targets and offensive techniques by setting eyes on Ukraine’s judicial bodies and notaries through massive email distribution containing malicious attachments disguised as official documents.
On February 11, 2025, another round of phishing emails was sent, masquerading the sender as a territorial branch of the Ministry of Justice of Ukraine. These emails contained links to download executable files, which were aimed at infecting the computer with the DARKCRYSTALRAT (DCRAT) malware upon execution.
After gaining initial access to a notary’s workstation, attackers install additional tools, including RDPWRAPPER, which enables parallel RDP sessions. When used in conjunction with the BORE utility, this setup allows them to establish RDP connections directly from the Internet to the compromised computer.
The group has also been observed leveraging detection evasion utilities to bypass User Account Control and tools like the NMAP network scanner, the FIDDLER proxy/sniffer to capture authentication data entered on state registry web interfaces, and the XWORM keylogger for credential theft. In some cases, exposed computers were later used to generate and send malicious emails via the SENDEMAIL console utility.
In response to the growing threat, CERT-UA, together with partners, promptly implemented cybersecurity measures to quickly identify infected computers in six regions and thwarted the attackers’ intentions even at the final stages of unauthorized notarial actions. By leveraging SOC Prime’s Platform for collective cyber defense, organizations can significantly reduce the attack surface while staying ahead of emerging threats linked to sophisticated hacking groups.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides granular visibility into the context of the latest UAC-0173 operation targeting Ukrainian notaries with the DARKCRYSTAL malware. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Tactics | Techniques | Sigma Rule |
Execution | Command and Scripting Interpreter: PowerShell (T1059.001) | |
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Command and Scripting Interpreter: Python (T1059.006) | ||
Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | |
Defense Evasion | Masquerading (T1036) | |
Masquerading: Match Legitimate Name or Location (T1036.005) | ||
Process Injection: Process Hollowing (T1055.012) | ||
Impair Defenses: Disable or Modify Tools (T1562.001) | ||
Hide Artifacts (T1564) | ||
Hide Artifacts: Hidden Window (T1564.003) | ||
System Binary Proxy Execution (T1218) | ||
System Binary Proxy Execution: Mshta (T1218.005) | ||
Discovery | Network Service Discovery (T1046) |




