The UAC-0057 hacking collective, aka GhostWriter, reemerges in the cyber threat arena by abusing a WinRAR zero-day tracked as CVE-2023-38831 that has been exploited in the wild since April through August 2023. The successful exploitation of CVE-2023-38831 enables attackers to infect the targeted systems with a PicassoLoader variant and Cobalt Strike Beacon malware. Notably, both malicious strains were leveraged by UAC-0057 in earlier attacks in the summer of 2023 targeting the Ukrainian government and educational sector.
CVE-2023-38831 Analysis: UAC-0057 Attack Against Ukraine Exploiting a WinRAR Zero-Day
On the last day of summer 2023, the CERT-UA team released a novel heads-up notifying defenders of an ongoing attack against Ukraine launched by the UAC-0057 hackers, also known under the moniker GhostWriter. In the latest malicious campaign, adversaries abuse CVE-2023-38831, a zero-day affecting WinRAR software versions prior to 6.23. The vulnerability exploitation allows threat actors to execute arbitrary code once users attempt to view a benign file from the corresponding ZIP archive. CVE-2023-38831 has been observed in real-world incidents with the PoC exploit publicly available on GitHub. In August 2023, defenders observed escalating numbers of CVE-2023-38831 exploitation attempts posing risks to stock brokers and traders across the globe.
In the latest campaign against Ukraine weaponizing the WinRAR security bug, the infection chain is triggered by an archive file with the CVE-2023-38831 exploit. Successful exploitation attempts allow attackers to execute a CMD file, which in turn, launches an LNK file. The latter runs an HTA file via the mshta.exe utility. This leads to generating a PDF lure with the file name related to the russia-Ukraine war and further running malicious JavaScript code on the compromised instances. The latter is another variant of PicassoLoader, earlier leveraged by the UAC-0057 group in offensive campaigns targeting Ukraine, and is intended to download the SVG lure image along with decrypting a malicious .NET file leveraging the Rabbit encryption algorithm. The above-referenced .NET file leads to the distribution of Cobalt Strike Beacon on vulnerable devices.
Detect CVE-2023-38831 Exploitation Attempts Linked to UAC-0057 Attacks Againt Ukrainian Entities
In light of the escalating cyber war, the need for proactive cyber defense measures has never been more crucial. SOC Prime Platform equips cybersecurity professionals with advanced and cost-efficient tools to enhance the capacity of security teams and optimize the ROI of SOC investments.
To help cyber defenders identify possible exploitation attempts for CVE-2023-38831 WinRAR flaw linked to the latest UAC-0057 campaign, SOC Prime’s Threat Detection Marketplace offers a relevant selection of curated Sigma rules. All the detection algorithms come enriched with CTI and are mapped to the MITRE ATT&CK framework. Furthermore, the rules are compatible with multiple SIEM, EDR, XDR, and Data Lake formats, with support for automated conversion from Sigma to native technology format.
To facilitate the content search, all the detections are categorized and tagged with relevant identifiers such as “UAC-0057” and “CERT-UA#7435” based on the group and CERT-UA security heads-up identifiers. For comprehensive access to the entire collection of Sigma rules covering the latest UAC-0057 attacks, enriched with valuable cyber threat context, simply press the Explore Detections button below.
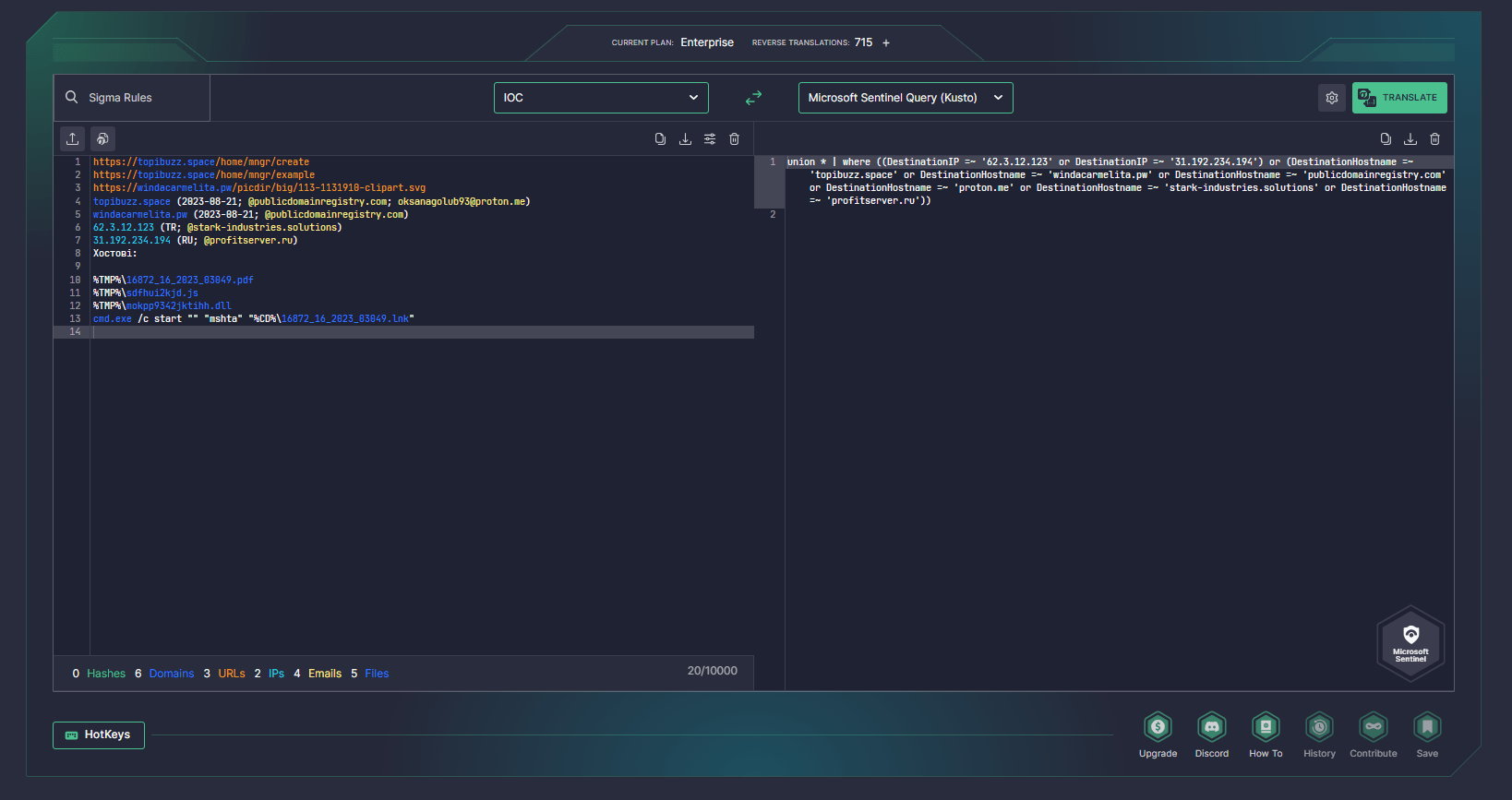
Security professionals are also welcome to take advantage of Uncoder AI, SOC Prime’s augmented intelligence framework, to accelerate threat research with instant IOC query generation based on indicators of compromise suggested in the latest CERT-UA alert.
MITRE ATT&CK Context
SOC team members can also explore the attack details covered in the CERT-UA#7435 alert. Dive into the table below to find the list of all applicable adversary tactics, techniques, and sub-techniques linked to the above-mentioned Sigma rules for in-depth analysis:
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Defense Evasion | System Script Proxy Execution (T1216) | |
System Binary Proxy Execution (T1218) | ||
System Binary Proxy Execution: Mshta (T1218.005) | ||
System Binary Proxy Execution: Rundll32 (T1218.011) | ||
Execution | Command and Scripting Interpreter (T1059) | |
Exploitation for Client Execution (T1203) | ||
Command and Scripting Interpreter: JavaScript | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) |




