The notorious Microsoft Office zero-day vulnerability tracked as CVE-2022-30190 aka Follina is still being actively exploited by multiple hacking organizations across the world. On June 10, 2022, CERT-UA released a new alert warning of ongoing cyber-attacks targeting Ukrainian media organizations. Threat actors continue to leverage the CVE-2022-30190 vulnerability in the latest malicious email campaign aimed to deliver the malware variant called CrescentImp and infect the targeted systems. The malicious activity is identified as UAC-0113, which, according to researchers, can be attributed to the russian hacking group Sandworm earlier observed in cyber-attacks on Ukrainian organizations.
Detect CrescentImp Malware Used in the Latest Attack by Sandworm APT Group aka UAC-0113
Cyber-attacks abusing the newly discovered CVE-2022-30190 vulnerability, which is actively exploited in the wild, are growing in scale and impact, thus, exposing global organizations in various industry sectors to severe risks. Leveraging email attachments in malicious email campaigns remains one of the most popular attack vectors, which has gained momentum in the latest cyber-attack targeting the Ukrainian media sector.
To help organizations timely spot CrescentImp infections in their infrastructure and proactively defend against the malicious activity of the related Sandworm APT, explore the comprehensive list of detection content crafted by SOC Prime Team and Threat Bounty Program content contributors:
Sigma rules to detect the malicious activity of the Sandworm APT group (UAC-0113)
All Sigma rules above available in the SOC Prime’s platform are aligned with the MITRE ATT&CK® framework for enhanced threat visibility and are compatible with the industry-leading SIEM, EDR, and XDR solutions. For a streamlined search experience, cybersecurity practitioners can also instantly browse the detection content library by the corresponding tag #UAC-0113 associated with the group activity.
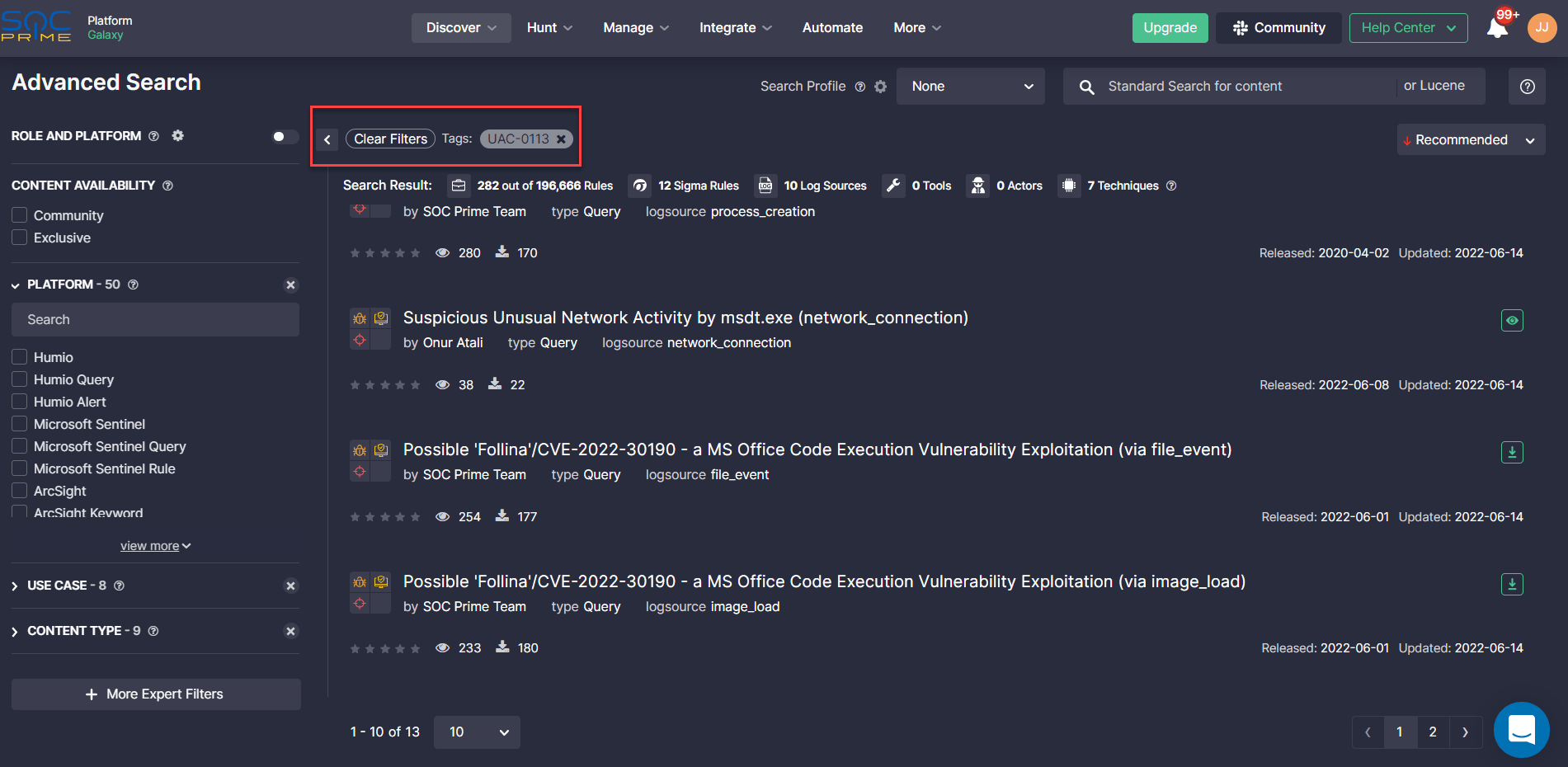
Alternatively, cyber defenders can also use a set of IOCs provided by the CERT-UA researchers to detect CrescentImp infections. Leveraging SOC Prime’s Uncoder CTI module, threat hunters and cyber threat intelligence specialists can instantly generate related IOC queries ready to run in their SIEM or XDR environment.
Registered SOC Prime users can instantly reach the full list of detection and hunting content for the CVE-2022-30190 vulnerability aka Follina by clicking the Detect & Hunt button. Looking for the latest trends in the cyber threat arena and the newly released Sigma rules available even without registration? Explore SOC Prime’s Cyber Threat Search Engine to instantly search for a particular APT, exploit, or CVE accompanied by relevant Sigma rules and comprehensive contextual information.
Detect & Hunt Explore Threat Context
CrescentImp Description: Attack Analysis Attributed to Sandworm APT/UAC-0113 Using CVE-2022-30190
In early June 2022, the global cyber threat arena was brimming with news about ongoing in-the-wild attacks exploiting CVE-2022-30190 aka Follina, with cyber-attacks on Ukraine being no exception. Just two weeks before the latest malware campaign, CERT-UA warned of ongoing phishing attacks on Ukrainian state bodies spreading Cobalt Strike Beacon malware by exploiting Windows CVE-2021-40444 and CVE-2022-30190 zero-day flaws.
In a new wave of cyber-attacks using the CVE-2022-30190 vulnerability and attributed to the Sandworm APT group, malicious emails targeting media organizations, including radio stations and news agencies, are massively spread from the compromised email addresses of the Ukrainian state bodies. These emails contain a lure attachment that, once opened, triggers an infection chain by downloading an HTML file and further executing malicious JavaScript code, which delivers CrescentImp malware to the compromised system. CrescentImp belongs to the Trojan viruses, still, the details of its origin are currently under investigation.
The malicious activity of the russia-linked Sandworm hacking collective targeting Ukrainian organizations since russia’s full-scale invasion of Ukraine traces back to April 2022, when the group was involved in the second power outage cyber-attack in human history leveraging Industroyer2 and CaddyWiper malware strains.
To constantly stay ahead of emerging threats regardless of their scale and level of sophistication, join SOC Prime’s Detection as Code platform and be ready to drive immediate value from enhanced threat detection and hunting capabilities. Looking for ways to make your own contribution and monetize your professional expertise? Join the ranks of SOC Prime’s crowdsourcing initiative, Threat Bounty Program, and see in action how to turn your threat hunting skills into recurrent financial benefits.




