Results of initial investigation and malware reverse analysis of Fire Sale Ukraine

Hello again, as promised, today we bring up some more detailed information (Research Intel) of what we believe was Phase 1 of Fire Sale Cyber Attack that hit entire media industry in Ukraine during elections. Good news first, there is already an incident recap by local Ukrainian CERT you may find it here: http://cert.gov.ua/?p=2370.
We now have proof that the attack was executed using 2 main components: a backdoor for delivery and payload/(cyber) weapon and it indeed hit the entire industry (as previously discussed) but did not interrupt the elections broadcast – perhaps it was never meant to do that. This is a bit troubling as either it was a test of something worse to come or we where faster at detecting than they thought was possible, or lucky or a mixture of multiple factors.
The Backdoor part of “Fire Sale”
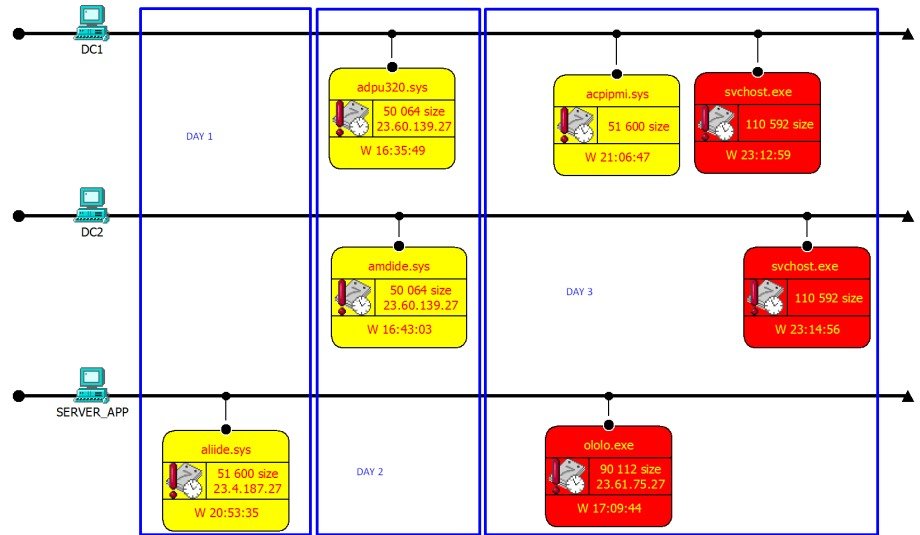
Backdoor files are called: aliide.sys, amdide.sys
and as research progressed we later discovered more files: acpipmi.sys, adpu320.sys
or any random driver name .sys. The malicious *.sys files are the files located in Windows/System32/drivers directory, pretending to be legit drivers, the most common being aliide.sys and amdide.sys.
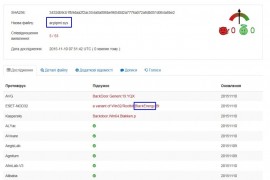
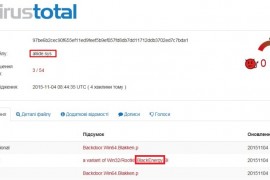
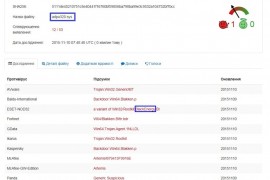
A simple way to tell the difference from a legit driver is to compare size: legit driver is < 20 KB, while virus is > 20KB, typically up to 50 KB. Initially we uploaded the files to VirusTotal and no antivirus flagged them as malicious.
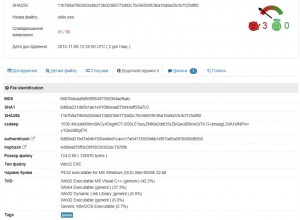
We then started contacting AV vendors directly and one by one they released signatures and confirmed the malware origin (so your welcome world!!). Here are the fresh VirusTotal results on the samples that got into my hands:
While detection is still on the early stage, make no mistake – we are dealing with a previously famous BlackEnergy malware, that was already used in 2015 for targeting ICS systems, as reported by CyberX.
In this scenario, BlackEnergy was planted through the fake IDE controller and CPU drivers months ahead before the elections date (October 25th).I will let you folks think about that and if it was planned or not…
There is one very plausible hypothesis regarding the backdoor published by CERT-UA basically telling that original drivers have a valid certificate signature, while replaced ones (backdoors / rootkits, etc.) are self-signed (that’s good news, right?!).
Conclusion 1: BlackEnergy has resurrected and is acting as a stealthy transportation system to deliver advanced cyber weaponry, it is installed to pretend to be a legit Windows driver, having a random name but a self-signed certificate signature. I think there is something more sinister coming up…. But hey that’s just an 1D10t’s opinion 😉
The Payload
Payload/weapon files that were discovered are called ololo.exe or an infected svchost.exe (which is classically placed to c:\Windows\ instead of correct location at c:\Windows\System32) file as a malicious payload.
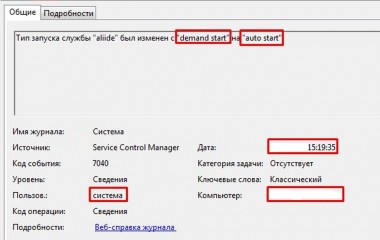
Firstly, what happens during the attack day exactly? The backdoor activates itself and even changes the process start-up parameters from “demand start” to “auto start” on all backdoored / infected machines in a matter of few seconds. That’s what allowed attack to happen across an entire industry at the same time – imagine someone has just pressed a remote control or trigger, except actually having a need to initiate a network connection to the targets!
ololo.exe/svchost.exe .
This is the most dangerous part of this targeted attack is as the BlackEnergy backdoor is constructed for each attack individually (think about that for a sec…) and is distributed very selectively (again think about that…).
We yet again can confirm and conclude that the BlackEnergy botnet is far from being dead, it has resurfaced in a new and very advanced form, and it is (spoiler alert!) not found in any public blacklists or intel feeds.
Coming back to the payload/weapon details, just having file names of ololo.exe/svchost.exe is not enough to serve as full IOC (Indicator Of Compromise), but here are the hashes from VirusTotal that now became available as we sent out malware samples to AV vendors.
The study(and full reverse) of the payload/weapon is still ongoing, but it is already clear that it is really a work of art – it has over 309 functions now and over 140 variables that it checks, sets, works with. Major part of code is written in Visual C++ and the code looks nice and very professional.
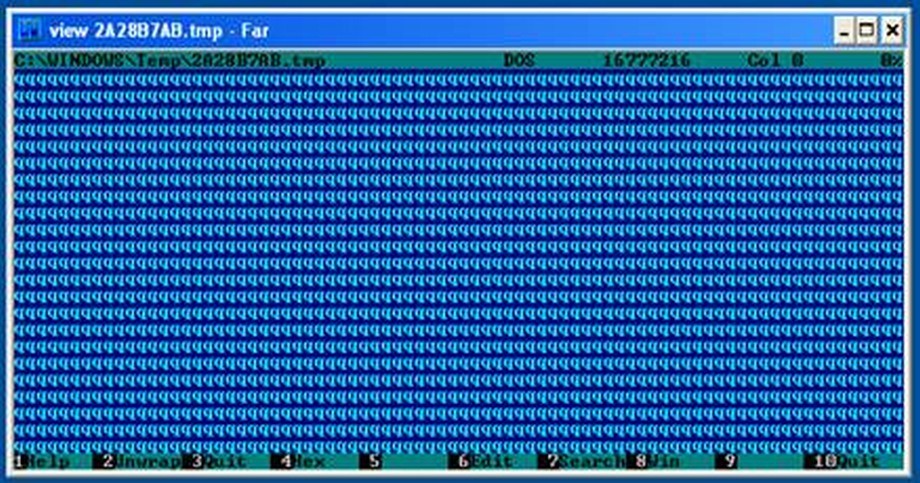
These are NOT some $Random people who created this, these are the guys know exactly what they are doing. This .exe file has multiple functions/inputs and steps that look at user context, environment, etc. Behavior also depends on which user it managed to run from. Running from non-admin account, ololo.exe/svchost.exe creates an event that fills up the hard drive (Windows\Temp\_random_name.tmp) with 16 MB files that contain one random ASCII character that repeats itself until 16 MB size is reached.
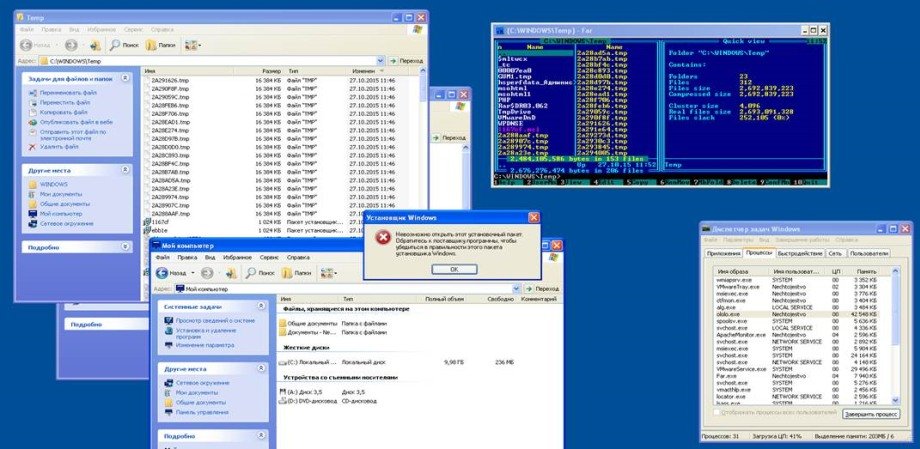
Here are some screens from infected host where you can spot ololo.exe as a process and creates a popup for you to call the admin! (pretty cool in my opinion as far work goes)
This event (we assume) is used to force any users on a windows based client that are not local admins to ask an admin to help resolve the issue on their respective laptop / desktop. Once malware noticed that the admin account (context change, it acts completely differently. Firstly, the payload conducts a full reconnaissance of the environment of the target for some time, up to 40 minutes as one of the victims observed. Malicious actions initially start as modifying the boot record / loader of the infected pc/laptop.
And then it starts to look for files on the infected computer.
After the virus finds what it is looking for it starts to erase any trail or evidence of it’s existence from the infected computer by writing zeroes to all files it was looking for (and in media industry it meant to look for any .avi, .mpeg, .mjpeg and anything else that may be found on video-editing workstations).
By the way, total number of file types by extension that malware is examining reaches over 2830 – this includes every possible document, multimedia, archive, database, executable, source code or anything you can think of, maybe this is intellectually selected by C&C payload? It is unclear at this stage what exactly is being searched for 40 minutes, or is 40 minutes relevant at all – this is VERY LOW chance this is a timer, but rather an indicator how fast search was performed on a particular infected machines, so further reverse engineering of malware samples is required… The interesting thing here is also that it acts like other spyware from attacks I have seen in the past, again you make up your mind on who the attacker really was and what the end game is…
Now just think for a second on other threats can this cause? Well, as malware varies behavior based on what it finds, it can do pretty much anything the attack wants, such as retrieval SAM file from domain controller, for example for further upload of the password hashes at “home location”, it further distributes backdoor and payload around the network, opens up tunnels etc. This also establishes the persistence of the threat (hello APT) since target of the attack will need a lot of time and resources to clean the mess up, and while company would clean up backdoors, tunnels will still be open, while cleaning up the tunnels they already would pre-load new weaponry undetectable by AV, rinse, repeat…
Additionally we discovered that virus is also location or time aware. We sent out a malware sample to multiple sandboxes across the globe and all of them did not find malware, except one. That one sandbox was in US and it indicated a connection: a command / function starts to connect to a server in Cambridge, Mass at the NTT Americas Data Center and with the server IP 23.61.75.27. 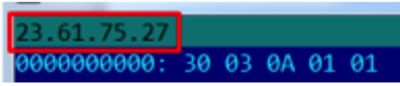
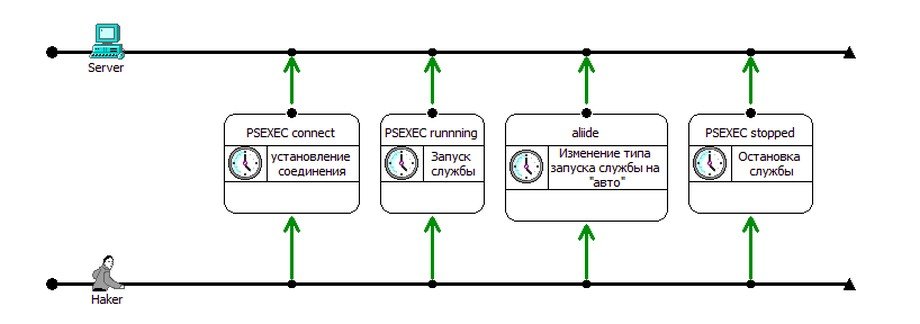
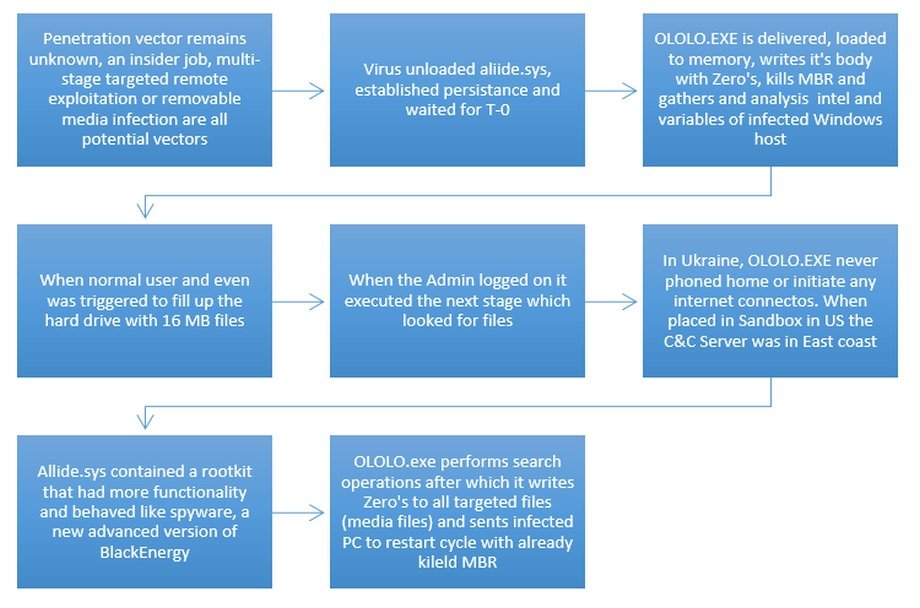
Now we can summarize the attack stages and make first conclusions:
- External Recon (Lack of info? OSINT on election campaign maybe?)
- Penetration – injection of BlackEnergy backdoor.
- Internal Recon – malware is studying environment, running 140+ variable checks similar to primitive AI and changes it’s further actions based on the findings
- Establishing persistence – tunnels, various backdoors to become hard to clean-up and resistant to AV’s.
- Timed and synced execution of attack purpose – delivering and running OLOLO.exe/SVCHOST.exe or other weaponry.
Attack stages map
Once the malware/payload has finished its dirty business it deletes itself, along with all media files (or other files that it is after) and delivery files (backdoor, what backdoor?) and 0’s out the space that it occupied to eliminate its signature and evidence of its existence. It is important to note that BlackEnergy itself is acting very stealthy and then just gets erased (covering tracks, eh?).
While we now have a clear understanding how to spot infection, we still known little about the C&C and distribution network. Having the IP address and malware hashes we ran it through all known Open Threat Intelligence feeds, including Zeus tracker, OTX, VxVault, IPvoid, VirusTotal and 100+ feeds but came out with 0 hits. We also checked hashes and IP vs 10 commercial sources, including very good feeds but yet again without result. This means that BlackEnergy has a new botnet that is used very secretly and currently goes around most of Threat Intelligence solutions out there. Another important point is that backdoor did not initiate any internet communication, so things like protocol tunneling (i.e. DNS, DHCP, ICMP) were not discovered (YET!). I am not saying Threat Intelligence is not effective, on the contrary it is fastest way to build out defense on global scale, but it was first time the attack (or proof of concept of the attack?) was seen.
I am providing different CERTs with details of the attack that are relevant as well as talking to companies about how the attack and future attacks can be stopped using ours and partners technology. As of now SOC Prime has released attack detection signatures that work with QUALYS (fastest way to detect if you have backdoor or not); SNORT, OSSEC, ARCSIGHT, SPLUNK and QRADAR. Please contact SOC Prime directly for the detection tools that are provided for free to all who need them. I’ll be posting up updates as investigation progresses and full reverse engineering of malware samples become available.