Hello, today we will talk about detection methods for the new version of BlackEnergy (4.0?) using QualysGuard Policy Compliance module.
According to the results of our research as well as some other reports that will be published later, we found some common signs of attack, known as IOC (Indicator Of Compromise) and we managed to test them using the abovementioned module.
IOCs were based on the analysis of the infected systems’ behavior and the fact that malware was configured for each attack individually. IOCs were divided into 5 groups according to the following criteria:
- Group 1 – suspicious behavior – further need for manual testing (we are grateful for the correct sample files which triggered false positives – we will be able to expand the controls and reduce the number of false positives, please send them to us via email.)
- Group 2 – confirmed infection;
- Group 3 – a very high probability of compromise
- Group 4 – a very high probability of compromise
- Group 5 – high probability of compromise
We can state that the presence of two or more controls from the Groups 3, 4, 5 is a proof of system compromise. We checked which files and system settings were changed and based on this analysis we created User Defined Control (UDC) for Qualys Policy Compliance.
The controls can be divided into 5 groups:
- The first group includes controls that check specific file hashes for compliance with the reference values;
- The second group of controls checks files for the known malware hashes;
- The third group looks for svchost.exe file in the locations that are not typical for it;
- The fourth group of controls checks for the existence of the known non-reference registry settings;
- The fifth group checks starting parameters of the known services that can indicate an infection.
- Let’s take a closer look at the results of the control checks from each group.
- If you notice inconsistencies in Group 1, you must double-check file signature or just its existence.
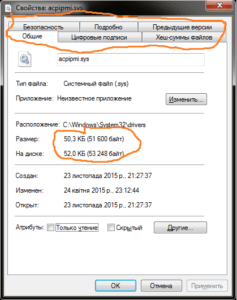
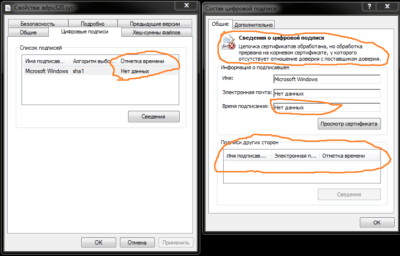
The malware’s acpipme.sys signature looks like this:
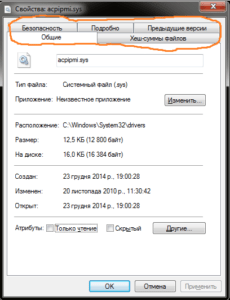
While there is usually no signature for reference file acpipmi.sys:
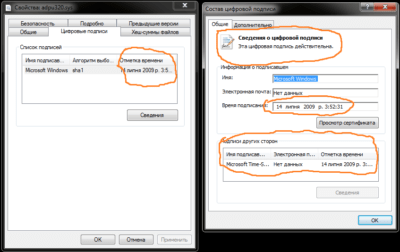
The other reference files have signature like this:
And this is typical driver with BE backdoor with self-signed certificate:
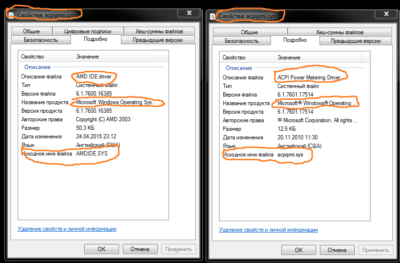
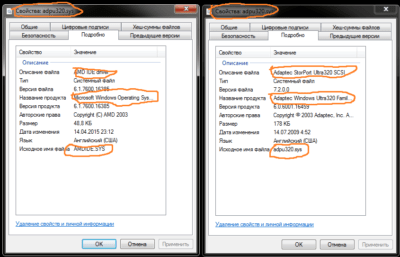
Also pay attention to the file details description for any inconsistencies or mismatches, for example on the left you can see a screenshot of the infected file and on the right a reference:
And here is another comparison, infected file is on the left and reference is on the right
- If you notice inconsistencies in Group 2, you have one of the known samples of BlackEnergy dropper.
- If you notice inconsistencies in file location from Group 3, there is a high probability your system is under attack and you need to follow our recommendations.
- If you find the registry key in question (Group 4), there is a high probability your system is infected, it is necessary to take urgent countermeasures.
- If you find incompliance to the policy in Group 5, please check with the system administrators for the causes of the atypical behavior of the services.
In order to analyze the suspected systems (and these can be any Windows machines) you need to download controls listed in the end of the article, create a policy and run a scan by QualysGuard Policy Compliance. Here is a step-by-step guide:
- Import the CID (named in the documents as User Defined Control (UDC)).
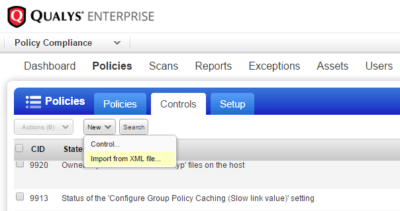
New controls will be added to the list of controls, their numbers will proceed in direct sequence, in order to see them you can sort the CID list by the column Created. - Create a policy that includes previously imported CID.
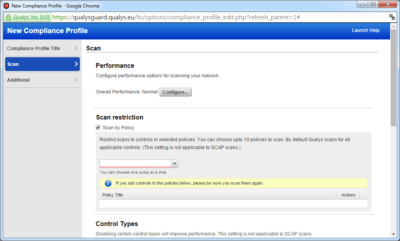
- Configure the scan profile settings as shown on the screenshot.
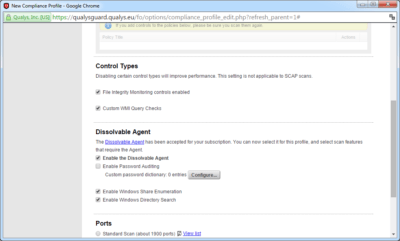
- For a quick scan of the entire infrastructure you can select Scan by Policy and carry out only the relevant tests, it will speed up scanning considerably. But it is always worth remembering that it will not be possible to build other reports from the results of the scan, in such cases we recommend running a full scan, considering that it takes about 5 minutes for each host at normal network workload and without consideration of scanner multi-threading.
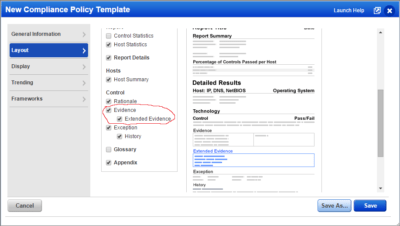
- When you create a report template is necessary to check this box to see the file size in the report.
- When viewing the report pay attention not only to the hash matching but also to the size of the files and all of the above control specifics.
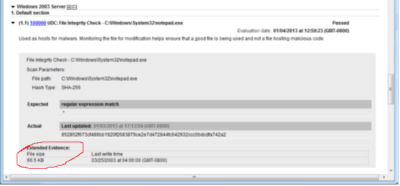 If the file is greater than 25 KB (or for some files > 150KB) it is a reason for concern.
If the file is greater than 25 KB (or for some files > 150KB) it is a reason for concern.
We will be grateful to receive your feedback, good hunting!
Take care of yourself.
P.S. You can download all the mentioned UDCs in zip archive below. Trial QualysGuard Policy Compliance account can be requested here.
SPID_0004_QUALYS_ adpu320_Correct.xml control checks the standard hash value.
SPID_0003_QUALYS_acpipmi_Correct.xml control checks the standard hash value.
SPID_0007_QUALYS_aliide_Correct.xml control checks the standard hash value.
SPID_0010_QUALYS_amdide_Correct.xml control checks the standard hash value.
SPID_0006_QUALYS_aliide_Compromised.xml control checks the hash of the file, uses two hashes of available malware, and you can also view the file size.
SPID_0009_QUALYS_amdide_Compromised.xml control checks the hash of the file, uses two hashes of available malware, and you can also view the file size.
SPID_0004_QUALYS_adpu320_Compromised.xml control checks the hash of the file, uses two hashes of available malware, and you can also view the file size.
SPID_0002_QUALYS_acpipmi_Compromised.xml control checks the hash of the file, uses two hashes of available malware, and you can also view the file size.
SPID_0012_QUALYS_svchost_Location.xml control looks for svchost.exe file in the wrong locations.
SPID_0001_QUALYS_ Registry_IOC_MicrosoftSecurity.xml control checks for suspicious registry key.
SPID_0008_QUALYS_aliideStart.xml checks the status of services and whether they are run as default.
SPID_0011_QUALYS_amdideStart.xml checks the status of services and whether they are run as default.