APT28 Adversary Activity Detection: New Phishing Attacks Targeting Ukrainian and Polish Organizations

Table of contents:
Throughout the second half of December 2023, cybersecurity researchers uncovered a series of phishing attacks against Ukrainian government agencies and Polish organizations attributed to the infamous russian nation-backed APT28 hacking collective. CERT-UA has recently issued a heads-up covering the in-depth overview of the latest APT28 attacks, from the initial compromise to posing a threat to the domain controller within an hour.
APT28 Phishing Attack Description
On December 28, 2023, CERT-UA released a security alert covering a wave of new phishing attacks by the russia-linked state-sponsored APT28 group (aka Fancy Bear APT or UAC-0028) against Ukrainian government agencies and several organizations in Poland. Phishing emails sent by adversaries contain links to harmful files aimed to infect the targeted systems with malware samples.
The above-mentioned malicious links redirect targeted users to a website that leads to downloading a shortcut file via JavaScript and the “search” (“ms-search”) application protocol. Opening the shortcut file executes a PowerShell command designed to download from a remote (SMB) resource and further launch a decoy document, as well as the Python programming language interpreter and the Python-based MASEPIE malware. The latter downloads and launches OPENSSH for tunneling, STEELHOOK, a PowerShell script designed for data theft from Internet browsers, and the backdoor OCEANMAP. Additionally, within an hour from the moment of the initial compromise, IMPACKET, SMBEXEC, and other offensive tools are created, facilitating network reconnaissance and attempts at further lateral movement.
MASEPIE from the group’s adversary toolkit is a Python-based malware with core capabilities designed for file transfer and command execution using TCP protocol. Data is encrypted via the AES-128-CBC algorithm. The backdoor achieves persistence by creating a “SysUpdate” key in the OS registry’s “Run” branch and an LNK file in the startup directory.
The applied OCEANMAP backdoor is a C#-based malware that uses IMAP for command execution. Commands are encoded in base64 within email drafts. The malware includes a configuration update mechanism, patching the backdoor executable files, and then restarting the process. OCEANMAP achieves persistence by creating a “VMSearch.url” file in the startup directory.
The observed TTPs are common for the APT28 group that has launched spear-phishing campaigns against Ukraine since at least June 2021, leveraging cyber-espionage malware to infect the targeted networks.
Notably, the latest offensive campaigns reveal that threat actors have been striving to expand the scope of attacks and infect the entire information and communication system organization-wide. Thus, compromising any workstation can pose a threat to the entire network.
Detect APT28 Attacks Covered in the CERT-UA#8399 Alert
The russia-backed APT28 group is continuously exploring fresh offensive strategies to target Ukraine and its allies in the cyber domain. With the release of the new CERT-UA#8399 alert focused on the latest adversary activity against Ukrainian and Polish organizations, SOC Prime Platform offers a curated list of relevant behavior-based detection algorithms. Follow the link below to drill down to all dedicated Sigma rules filtered by the “CERT-UA#8399” custom tag, explore their cross-platform translations, and delve into the MITRE ATT&CK® context for faster attack attribution.
Sigma rules to detect APT28 attacks based on the CERT-UA#8399 alert
To strengthen proactive cyber defense capabilities, progressive organizations can take advantage of the entire detection stack related to the APT28 offensive operations. Hit Explore Detections to reach 70+ context-enriched Sigma rules addressing existing and emerging threats attributed to the group’s adversary activity.
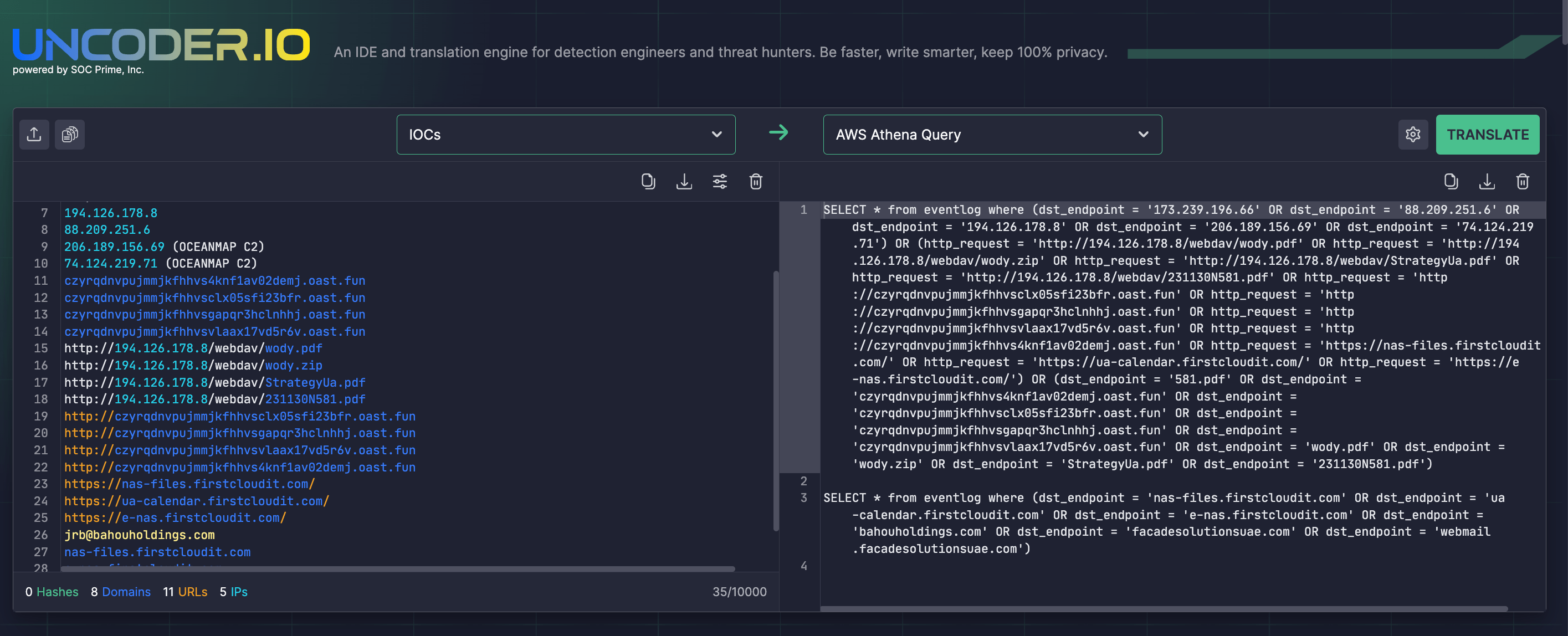
Security engineers can also streamline retrospective IOC matching based on indicators of compromise from the relevant CERT-UA report by leveraging Uncoder IO. With the open-source IDE for Detection Engineering, teams can parse threat intel from the CERT-UA alert and convert it into custom IOC queries tailored for the cybersecurity language in use.
MITRE ATT&CK Context
Leveraging MITRE ATT&CK provides granular visibility into the context of offensive operations attributed to APT28. Explore the table below to see the full list of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques used in the latest campaign against the Ukrainian public sector and Polish organizations.
Tactics | Techniques | Sigma Rule |
Initial Access | Phishing: Spearphishing Attachment | |
Execution | Command and Scripting Interpreter: PowerShell (T1059.001) | |
Command and Scripting Interpreter: Windows Command Shell (T1059.003) | ||
Command and Scripting Interpreter: Visual Basic (T1059.005) | ||
Command and Scripting Interpreter: Python (T1059.006) | ||
Command and Scripting Interpreter: JavaScript (T1059.007) | ||
User Execution: Malicious Link (T1204.001) | ||
User Execution: Malicious File (T1204.002) | ||
Persistence | Boot or Logon Autostart Execution (T1547) | |
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | ||
Defense Evasion | System Binary Proxy Execution: Regsvr32 (T1218.010) | |
Hide Artifacts: Hidden Windows (T1564.003) | ||
Masquerading (T1036) | ||
Lateral Movement | Remote Services: SMB / Windows Admin Shares (T1021.002) | |
Collection | Archive Collected Data (T1560) | |
Command and Control | Protocol Tunneling (T1572) |